当前位置:网站首页>Kirk borne's selection of learning resources this week [click the title to download directly]
Kirk borne's selection of learning resources this week [click the title to download directly]
2022-07-07 18:36:00 【Zhiyuan community】
边栏推荐
- 国内的软件测试会受到偏见吗
- 元宇宙带来的创意性改变
- Chapter 3 business function development (to remember account and password)
- Nunjuks template engine
- Tips for this week 131: special member functions and ` = Default`
- 财富证券证券怎么开户?通过链接办理股票开户安全吗
- 标准ACL与扩展ACL
- Yearning-SQL审核平台
- [principle and technology of network attack and Defense] Chapter 6: Trojan horse
- Discuss | what preparations should be made before ar application is launched?
猜你喜欢
List selection JS effect with animation
Introduction to OTA technology of Internet of things

讨论 | AR 应用落地前,要做好哪些准备?
小试牛刀之NunJucks模板引擎
JS pull down the curtain JS special effect display layer
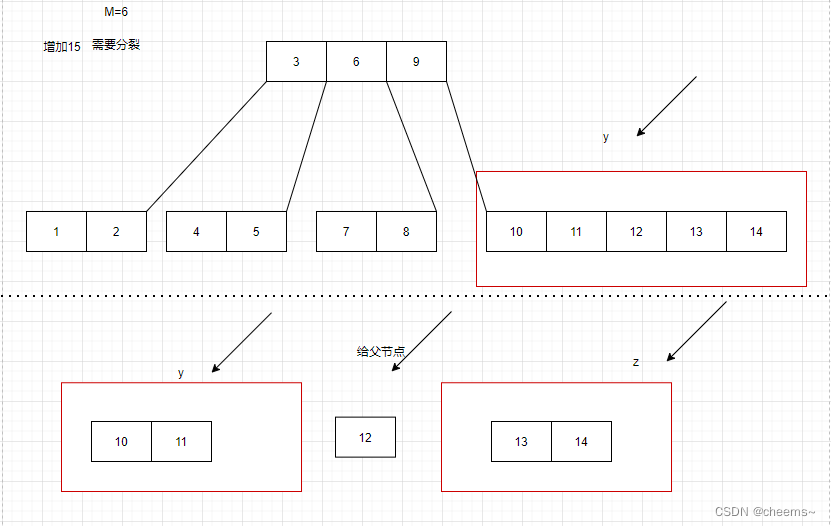
磁盘存储链式的B树与B+树

Native JS verification code
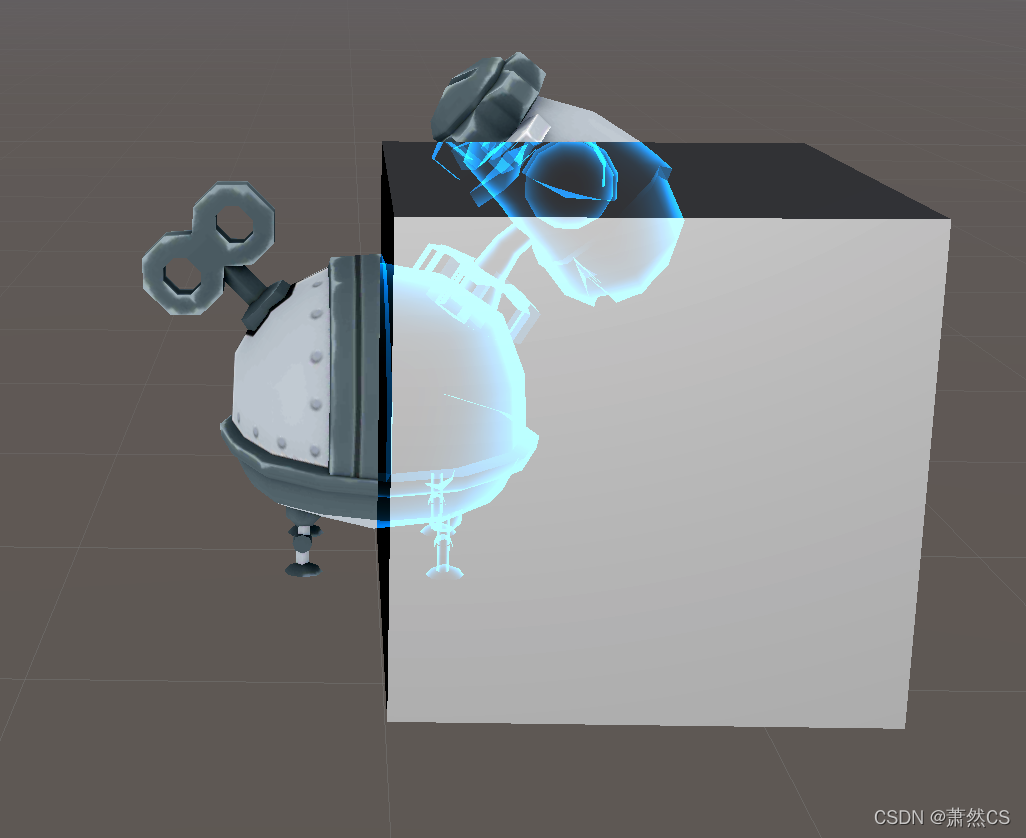
【Unity Shader】插入Pass实现模型遮挡X光透视效果

Tips for short-term operation of spot silver that cannot be ignored

RIP和OSPF的区别和配置命令
随机推荐
Improve application security through nonce field of play integrity API
『HarmonyOS』DevEco的下载安装与开发环境搭建
单臂路由和三层交换的简单配置
Five simple ways to troubleshoot with Stace
gsap动画库
通过 Play Integrity API 的 nonce 字段提高应用安全性
回归测试的分类
Some key points in the analysis of spot Silver
Mui side navigation anchor positioning JS special effect
同消费互联网的较为短暂的产业链不同,产业互联网的产业链是相当漫长的
云景网络科技面试题【杭州多测师】【杭州多测师_王sir】
golang 客户端服务端登录
Industry case | digital operation base helps the transformation of life insurance industry
[paddleseg source code reading] add boundary IOU calculation in paddleseg validation (1) -- val.py file details tips
Tips of the week 136: unordered containers
[tpm2.0 principle and Application guide] Chapter 5, 7 and 8
科学家首次观察到“电子漩涡” 有助于设计出更高效的电子产品
【demo】循环队列及条件锁实现goroutine间的通信
Cf:c. factors and powers of two [DP + sort + Select Board + select several numbers equal to the minimum number of known sums]
Backup Alibaba cloud instance OSS browser




