当前位置:网站首页>Two stage locking protocol for concurrency control
Two stage locking protocol for concurrency control
2022-07-05 21:59:00 【Short section senior】
The database management system generally adopts the method of two-stage lock protocol to realize the serializability of concurrent scheduling , So as to ensure the correctness of scheduling
Two stage lock protocol
It means that all transactions must be divided into two phases to lock and unlock data items
Reading any data 、 Before writing operations , The first thing a transaction needs to do is get a block on that data
After releasing a blockade , The transaction no longer applies for and obtains any other blockages
“ Two paragraphs ” The meaning of lock
The transaction is divided into two stages
The first stage is to get the blockade , Also known as the extension phase
Transactions can apply for any type of lock on any data item , But you can't release any locks
The second stage is to release the blockade , Also known as the contraction phase
A transaction can release any type of lock on any data item , But you can't apply for any more locks
example
Business Ti Comply with the two-stage lock protocol , The blocking sequence is :
Slock A Slock B Xlock C Unlock B Unlock A Unlock C;
|← Expansion stage →| |← Contraction stage →|
Business Tj Failure to comply with the two-stage lock agreement , The blocking sequence is :
Slock A Unlock A Slock B Xlock C Unlock C Unlock B;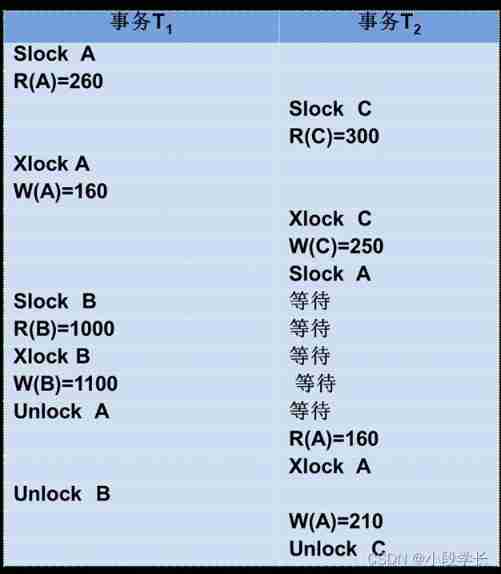
The scheduling of graph follows the two-stage locking protocol , Therefore, it must be a feasible scheduling .
How to validate ?
It is a sufficient condition for serializable scheduling that transactions obey two-stage locking protocol , It's not necessary .
If both concurrent transactions follow the two-stage locking protocol , Any concurrent scheduling strategy for these transactions is serializable
If a schedule of concurrent transactions is serializable , Not all transactions are subject to the two-stage locking protocol
Two stage locking protocol and one-time blocking method to prevent deadlock
One time blocking requires every transaction to lock all data to be used at one time , Otherwise, we can't carry on , Therefore, the one-time blocking law abides by the two-stage locking agreement
However, the two-stage locking protocol does not require the transaction to lock all data to be used at one time , Therefore, transactions complying with the two-stage locking protocol may deadlock
[ example ] A transaction that abides by the two-stage lock protocol has a deadlock 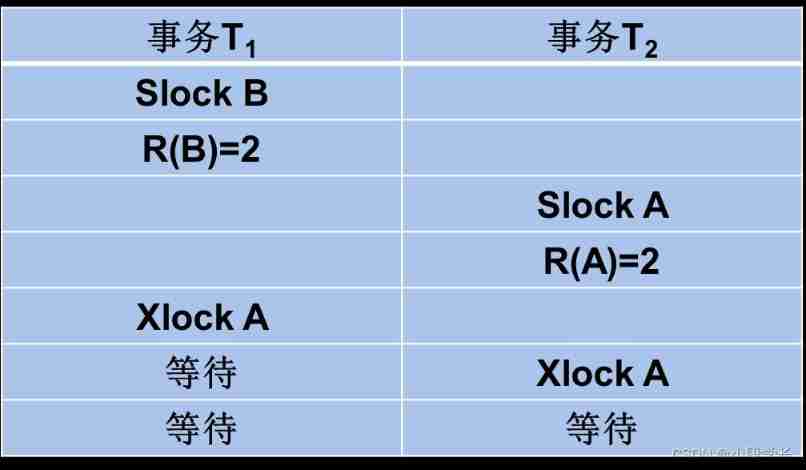
Welcome to join me for wechat exchange and discussion ( Please note csdn Add )
边栏推荐
- 极狐公司官方澄清声明
- Yolov5 training custom data set (pycharm ultra detailed version)
- Implementation technology of recovery
- 微服務鏈路風險分析
- Pointer parameter passing vs reference parameter passing vs value parameter passing
- 854. 相似度为 K 的字符串 BFS
- Recursive query of multi-level menu data
- Three components of openpyxl
- ICMP 介绍
- 2.2.5 basic sentences of R language drawing
猜你喜欢
Daily question brushing record (XIV)
Deeply convinced plan X - network protocol basic DNS
Bitbucket installation configuration
从零开始实现lmax-Disruptor队列(四)多线程生产者MultiProducerSequencer原理解析
1.2 download and installation of the help software rstudio

How to view Apache log4j 2 remote code execution vulnerability?
【愚公系列】2022年7月 Go教学课程 004-Go代码注释

database mirroring
Create a virtual machine on VMware (system not installed)

Database tuning solution
随机推荐
Analyse des risques liés aux liaisons de microservices
database mirroring
Codeforces 12D Ball 树形阵列模拟3排序元素
An exception occurred in Huawei game multimedia calling the room switching method internal system error Reason:90000017
Robot operation mechanism
Matlab | app designer · I used Matlab to make a real-time editor of latex formula
Basic grammar of interview (Part 1)
Advantages and disadvantages of the "Chris Richardson microservice series" microservice architecture
EL与JSTL注意事项汇总
Countdown to 92 days, the strategy for the provincial preparation of the Blue Bridge Cup is coming~
Recursive query of multi-level menu data
Shell script, awk condition judgment and logic comparison &||
微服務鏈路風險分析
"Chris Richardson microservices series" uses API gateway to build microservices
Dbeaver executes multiple insert into error processing at the same time
Poj3414 extensive search
Huawei game multimedia service calls the method of shielding the voice of the specified player, and the error code 3010 is returned
HDU 4391 Paint The Wall 段树(水
Emotional analysis of wechat chat records on Valentine's day based on Text Mining
他们主动布局(autolayout)环境的图像编辑器