当前位置:网站首页>From the perspective of attack surface, see the practice of zero trust scheme of Xinchuang
From the perspective of attack surface, see the practice of zero trust scheme of Xinchuang
2022-07-02 11:12:00 【olga5abl】
Reprint Electronic finance The first 320 period
author Vice president of Beijing anbotong Technology Co., Ltd Li Yuan
Understand zero trust from the perspective of attack surface
Gartner stay 2022 Published in 《2022 Key trends of network security in (Top Trends in Cybersecurity 2022)》 In the report , hold “ The attack area expanded ” As an important item .
《2022 Key trends of network security in (Top Trends in Cybersecurity 2022)》 The report
According to the report : In order to manage the exposure of a series of expanded security attacks , Organizations need to pay attention to more than patching vulnerabilities . Changes brought about by the application of a series of digital schemes , For example, the new hybrid network architecture 、 Accelerated application of public cloud 、 More interconnected supply chains 、 More externally accessible digital assets and more applications of IOT Technology , Leading to a significant expansion of the attack area . Organizations must start in the traditional “ Safe house ” Think about new strategies based on the plan , Take action as soon as possible to improve safety visualization and risk prevention level of key businesses .
The definition of attack surface is : The sum of vulnerabilities that a given computer or network system can be accessed and exploited by malicious people . In order to continuously visualize and reduce the attack surface , The following aspects need to be done well :
- Business access : That is, the process management of people accessing business systems .
- Vulnerability management : Prioritization 、 Classification and visual disposal .
- Asset security : Mapping 、 Vulnerability management 、 Compliance construction .
Zero trust is an architecture and methodology , Its focus is to provide a secure application access path . From the perspective of attack surface , Zero trust is mainly aimed at “ Business access ” Some solutions are given , It can be further refined into several key points :
- Permissions and paths : Access rights and paths around people and Applications , Visual presentation 、 Sorting and management , Eliminate violations and unauthorized access , Plan the best path .
- Communication security : Encrypt the communication content , Verify the identity of both sides of the communication , Avoid communication being monitored or destroyed .
- Content audit : Restore the communication content 、 Records and retention .
In terms of protecting data security , Compared with desensitization in the field of data security 、 Leakage protection 、 Database protection and other special technologies , The core role of the zero trust solution is “ Move the gate forward ”. Set reasonable access rights and paths for key data , Achieve efficient management , Raise the difficulty and threshold of illegal access to data from the source , It can effectively help the implementation of the overall data security scheme .
Three levels of zero Trust Practice
For zero trust building , This paper will analyze according to the following three levels :
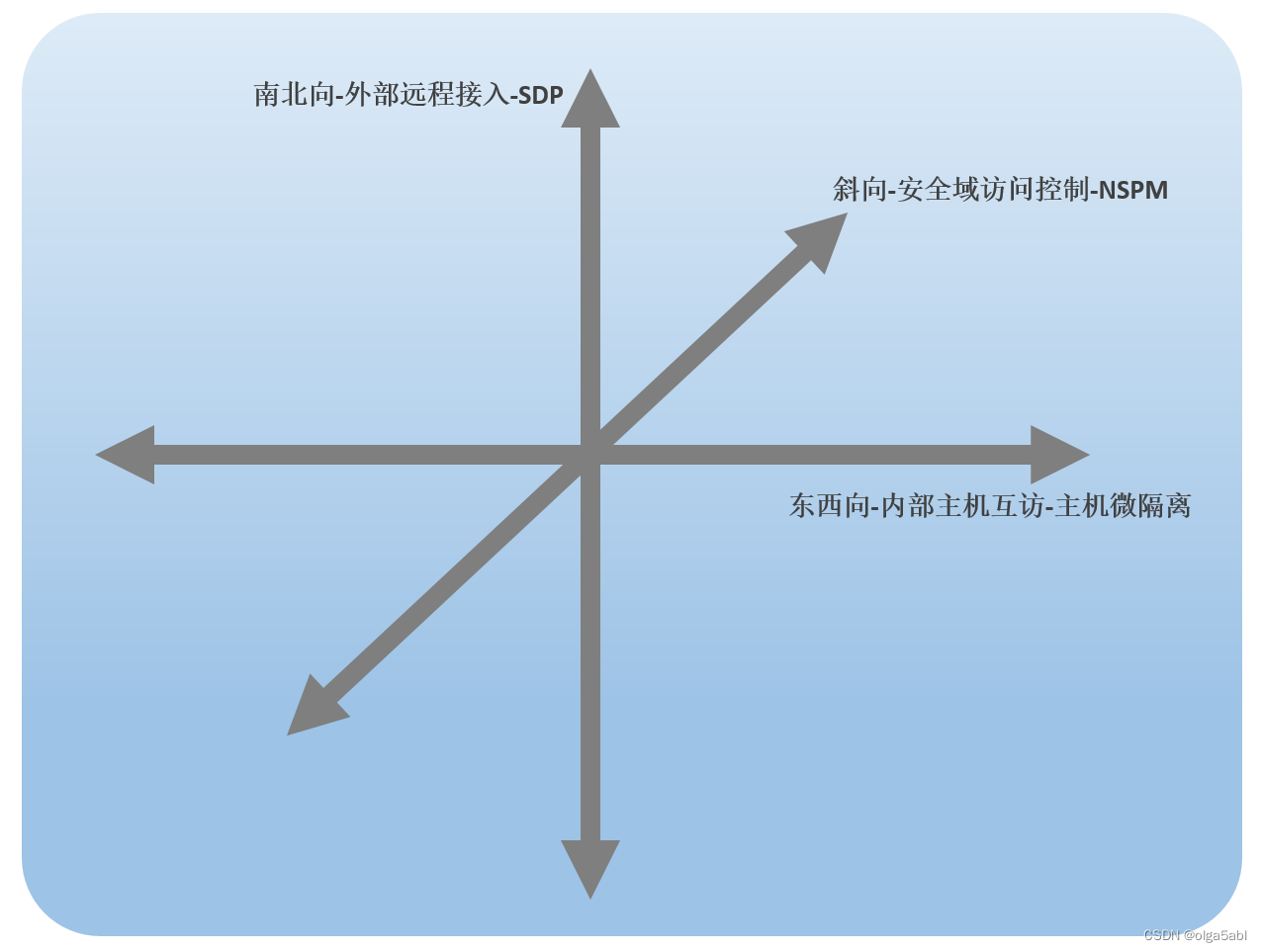
Three levels of zero trust
1、 North-south direction : External remote access
In the north-south direction , The main challenge of access control comes from tradition VPN Several hidden dangers of Technology :
- Open fixed ports for a long time , This leads to the persistence of network layer exposure , This defect has been successfully used by the attacker many times in the attack and defense drill .
- Under the long connection mechanism , Network quality sensitive applications may have performance problems .
- In the multi cloud and hybrid cloud access environment , The authority control is not fine enough or the maintenance cost is too high .
- The terminal security control ability is insufficient .
At present, the mainstream VPN The alternative is software defined boundaries SDP(Software Defined Perimeter), This scheme has been widely used , Its core advantages are as follows :
- Adopt the authentication before connection mode , Avoid exposing fixed ports .
- Use the short connection scheme , Enhance the business performance experience .
- Customize the global strategy based on people and business systems and realize dynamic adaptation , It is more applicable in multi cloud and hybrid cloud access scenarios , And it can reduce the difficulty of maintenance .
- Support a full range of host and mobile terminal operating systems 、SDK And browser environment access , Adopter + End + Access environment three-dimensional verification technology , More executive in terminal identity verification , More suitable for mobile applications and IoT Terminal access scenario .
2、 East West : Internal host exchange
At the level of East-West flow , The main solution of zero trust is micro isolation . Its main security attack means is horizontal proliferation , That is, after the attacker obtains the lost host, he continues to expand the attack in the security domain as a springboard , Ultimately threaten core assets . Micro isolation can be popularly understood as firewall between business systems , In scenarios such as data centers , Large tier-2 environments and virtualized workloads make this technology more popular .
Micro isolation products can generally be classified into three categories , Namely :
- Hyper-V Micro isolation : With VM Isolate the unit .
- Network micro isolation : stay L3/L4 In isolation ( Often with the help of SDN controller ).
- Host micro isolation : Based on the host / Business system isolation .
One of the most popular micro isolation schemes is host micro isolation , One reason is that this solution is relatively easy to deploy , Deploy on the management platform and host Agent You can begin to deploy the policy . Whether it's Windows or Linux operating system ,Agent Can pass iptables And so on , On the management platform, the host mutual access relationship and path can be visualized and managed , And carry out policy adaptive calculation according to the access requirements 、 Exception analysis and distribution , This solution is loaded in the cloud 、 The virtual load is consistent with the physical server , So as to block the East-West threat to security , Reduce business delivery time and maintenance costs .
3、 Oblique : Security domain access control
In addition to the north-south and east-west directions, which are particularly discussed , The so-called “ Oblique ” Often overlooked , Especially when the network scale is large enough and the security access control strategy is complex enough , This direction will be particularly important . In a multi branch network across a wide area network , At the same time, there are many remote access users , Including home office employees 、 Supply chain and third-party partners , At this time, the division of security domain and security policy planning will be more complex . Just imagine , At this time, the access between two hosts may span three layers and security domains , That is to say, it occurs simultaneously in the north-south and east-west directions , The real access control will be based on the access control strategy of security devices , Simple north-south or East-West authority control cannot solve the problem independently .
The oblique corresponding zero trust solution is NSPM(Network security policy management) technology . stay NSPM In the access control baseline management function of , Access control baselines can be set based on business requirements and security domain access rules , The access control baseline information includes at least the source domain 、 source address 、 Destination domain 、 Destination address 、 agreement 、 port 、 Actions and other information , Support black and white list 、 High risk ports 、 Virus port customization , Support the regular inspection of network access control policies according to the access control baseline , Timely discover and eliminate the illegal policies that lead to illegal unauthorized access . Besides ,NSPM The network exposure risk management function of can target a certain host or host group , Automate the analysis of network exposure path and exposure risk , Describe its external exposure from the perspective of network access relationship and security path , It can help users know the size of some important hosts and network exposure in time 、 The level of risk , Assist users in the convergence of exposed surfaces and the security reinforcement of exposed paths .
In order to systematically solve the problem of permission control , We need to turn the north-south direction 、 Organic combination of East-West and oblique solutions . At present , take SDP、 Host micro isolation and NSPM Combined zero trust solutions are not common , Domestic manufacturer anbotong is one of the suppliers , The products have been adapted to the Xinchuang terminal environment , There have been successful cases in the financial and operator industries .
Summary of experience in the implementation of Xinchuang terminal environment
Apply the zero trust technology solution to the information creation environment , The main work is to complete the related software in Xinchuang CPU( Godson / Kun Peng / Feiteng )、 Xinchuang operating system ( kirin 、 Tongxin ) And the adaptation of Xinchuang network card and Xinchuang database . The main technical difficulties to be overcome in this landing process include :
- Degree of hardware independence : When the software is mainly implemented in user mode , There will not be too much driving work involved in the process of migrating to Xinchuang , More smoothly .
- Solve cross platform compilation and various languages 、 The component version is upgraded .
- Adaptation and migration of various localized products .
- Overcome the current situation of relatively weak development tool chain for continuous debugging .
- Architecture related open source software refactoring and migration .
Promote products in the field of information and innovation through several systems , Zero trust related products have been well implemented in the environment of Xinchuang terminal . From the application effect , Although there is still room for optimization in terms of performance and encryption and decryption capabilities , But it has been successfully applied to general environment .
Future outlook
Driven by both policy and Technology , Zero trust security has achieved good results in the field of information innovation , There will be greater opportunities in the future , Especially in the accelerated application of financial markets . During the implementation of the zero trust solution, we need to pay attention to multiple levels , Continue to reduce the attack surface and control access rights , Guard the front pass , Become an important measure of digital transformation and data security .
reference :
《Guide to Network Security Concepts》,Gartner
《Top Trends in Cybersecurity 2022》,Gartner
边栏推荐
- Use of vscode tool
- Special topic of binary tree -- acwing 3540 Binary search tree building (use the board to build a binary search tree and output the pre -, middle -, and post sequence traversal)
- TIPC Cluster5
- TIPC Getting Started6
- PCL projection point cloud
- LVM操作
- 二叉树专题--AcWing 18. 重建二叉树(利用前、中序遍历,构建二叉树)
- Special topic of binary tree -- acwing 18 Rebuild the binary tree (construct the binary tree by traversing the front and middle order)
- JSP webshell free -- the basis of JSP
- One trick to quickly realize custom application titlebar
猜你喜欢
Special topic of binary tree -- acwing 18 Rebuild the binary tree (construct the binary tree by traversing the front and middle order)
Mongodb learning and sorting (condition operator, $type operator, limit() method, skip() method and sort() method)

如何使用IDE自动签名调试鸿蒙应用
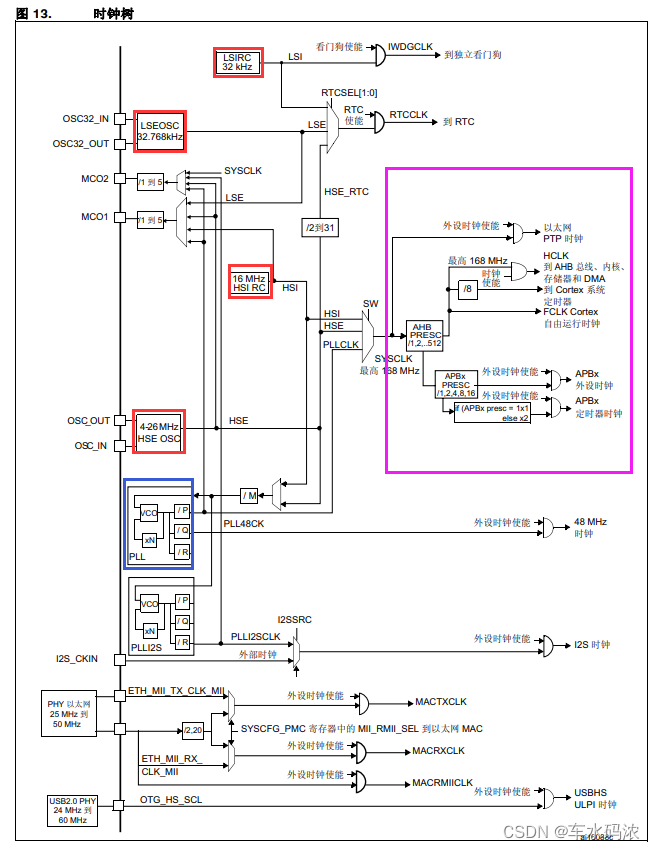
三.芯片启动和时钟系统
![Luogu p5536 [xr-3] core city (greed + tree DP looking for the center of the tree)](/img/dc/2aa55c9b3f23c292820a56ea72fedd.png)
Luogu p5536 [xr-3] core city (greed + tree DP looking for the center of the tree)
![[applinking practical case] share in app pictures through applinking](/img/12/5616f1fa55387b81e25e55a98022b9.png)
[applinking practical case] share in app pictures through applinking

Huawei game failed to initialize init with error code 907135000

From Read and save in bag file Jpg pictures and PCD point cloud
【AGC】构建服务3-认证服务示例
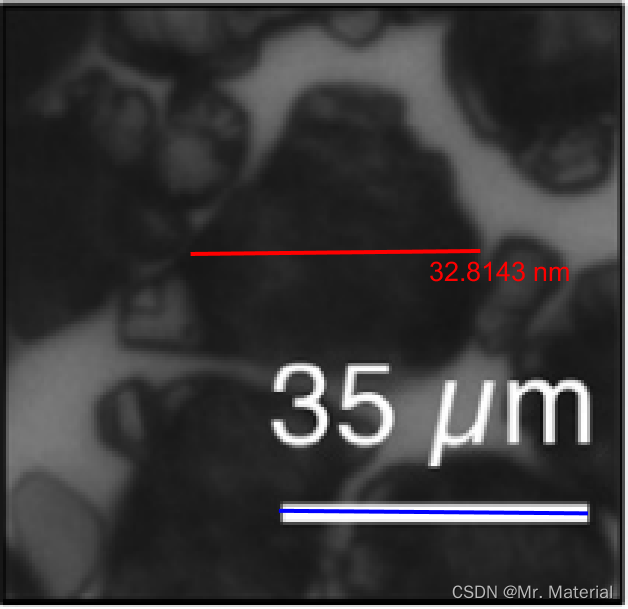
实验电镜距离测量之Matlab处理
随机推荐
Flink two Open, implement Batch Lookup join (attached source)
TIPC Cluster5
Binary tree topic -- p1030 [noip2001 popularization group] find the first order
V2X-Sim数据集(上海交大&纽约大学)
PHP tea sales and shopping online store
Huawei game failed to initialize init with error code 907135000
The first white paper on agile practice in Chinese enterprises was released | complete download is attached
【快应用】Win7系统使用华为IDE无法运行和调试项目
PKG package manager usage instance in FreeBSD
三.芯片啟動和時鐘系統
[AGC] how to solve the problem that the local display of event analysis data is inconsistent with that in AGC panel?
QT学习日记8——资源文件添加
2022-06-17
Overview of integrated learning
[AI application] Hikvision ivms-4200 software installation
【ARK UI】HarmonyOS ETS的启动页的实现
TIPC Getting Started6
Leetcode 182 Find duplicate email (2022.07.01)
flink二开,实现了个 batch lookup join(附源码)
JSP webshell free -- the basis of JSP