当前位置:网站首页>JS reverse tutorial second issue - Ape anthropology first question
JS reverse tutorial second issue - Ape anthropology first question
2022-07-07 09:36:00 【Little w who learns programming】
js The second issue of reverse tutorial - The first question of ape man
List of articles
( Multi map early warning )
Topic analysis :
First , Get into Website , View page tips :
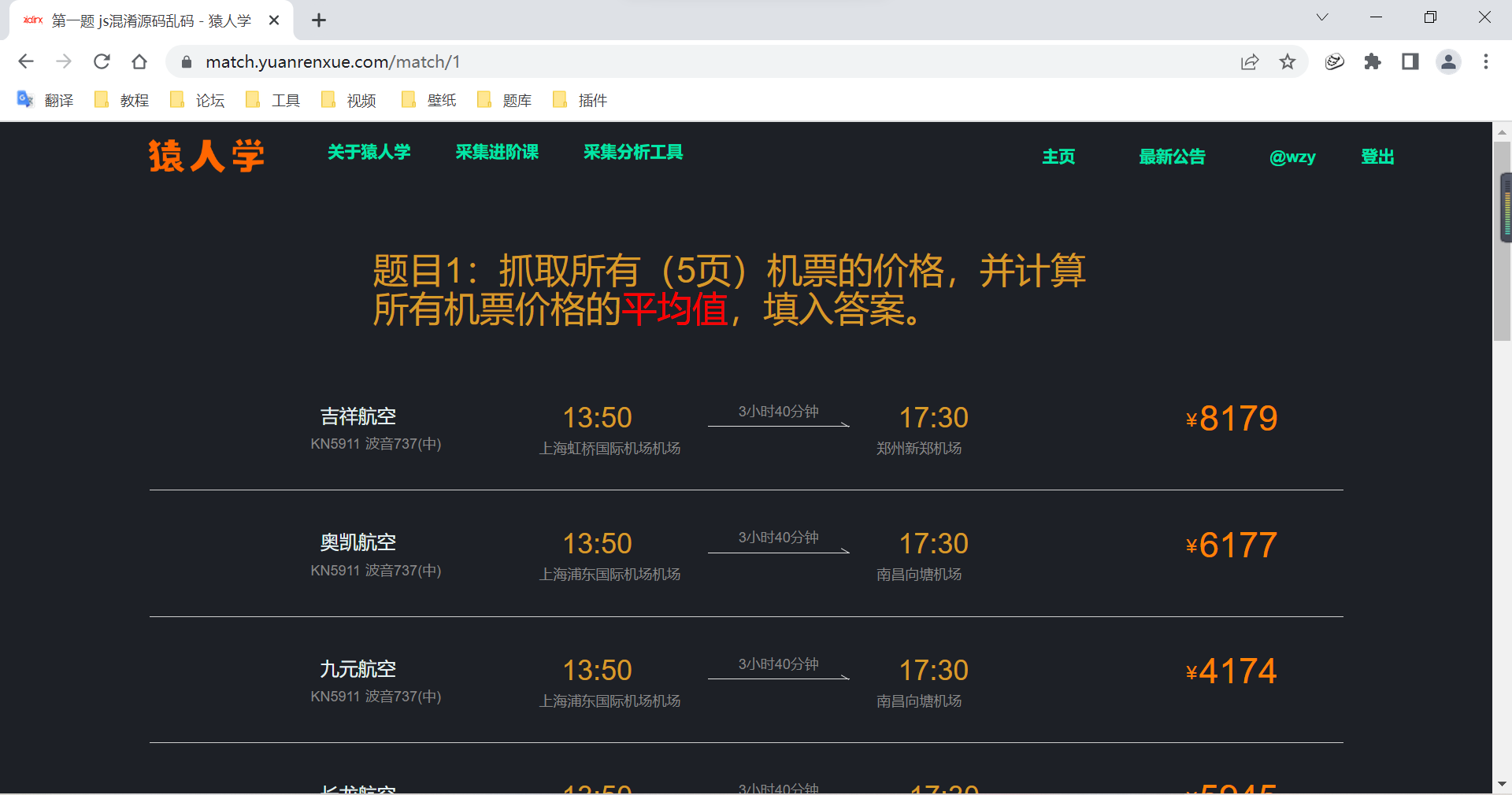
After turning the page, I found 4、5 Page cannot be entered :
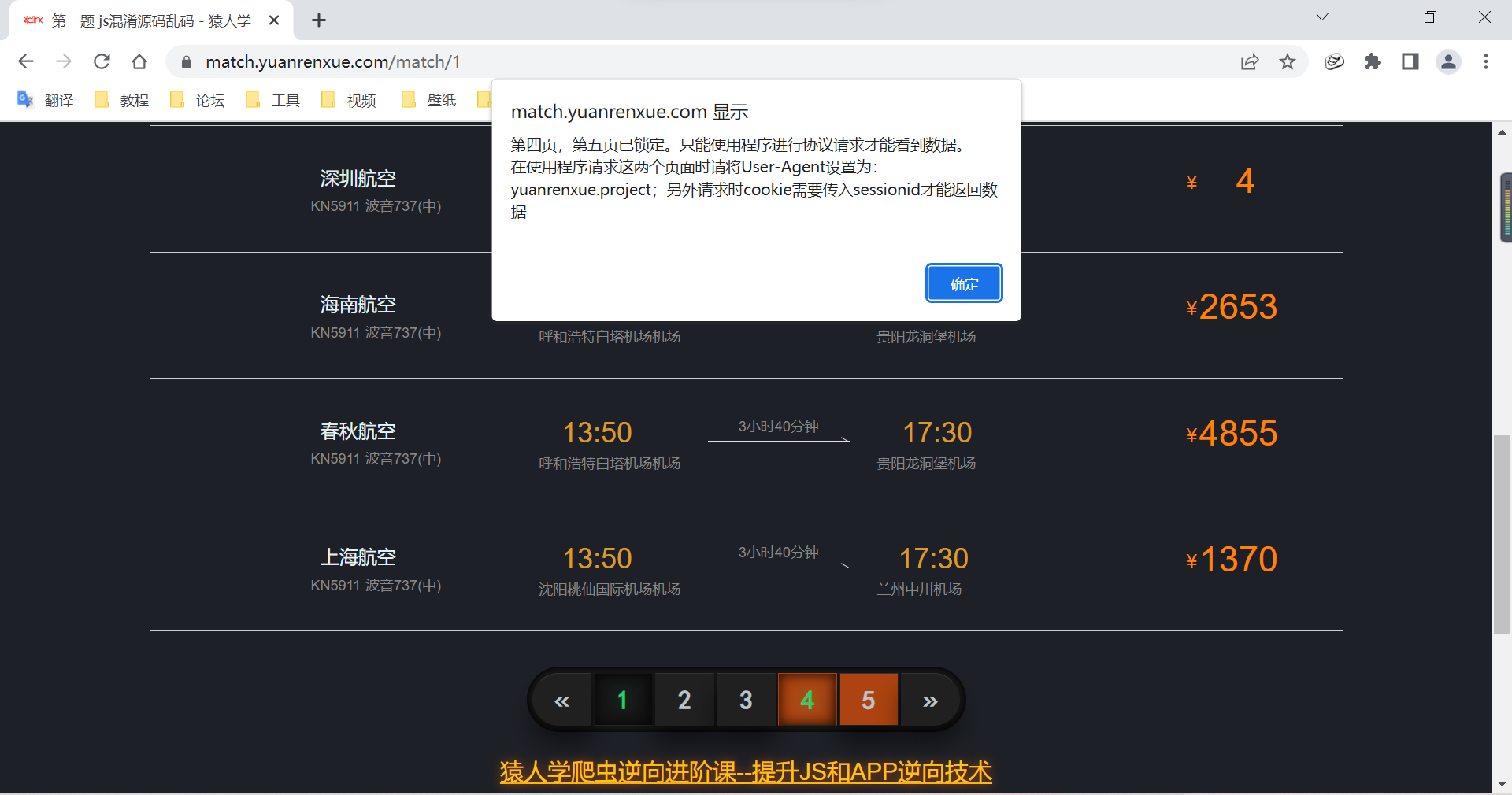
Right click to check for packet capture analysis , Discover that there is infinity debugger The breakpoint :
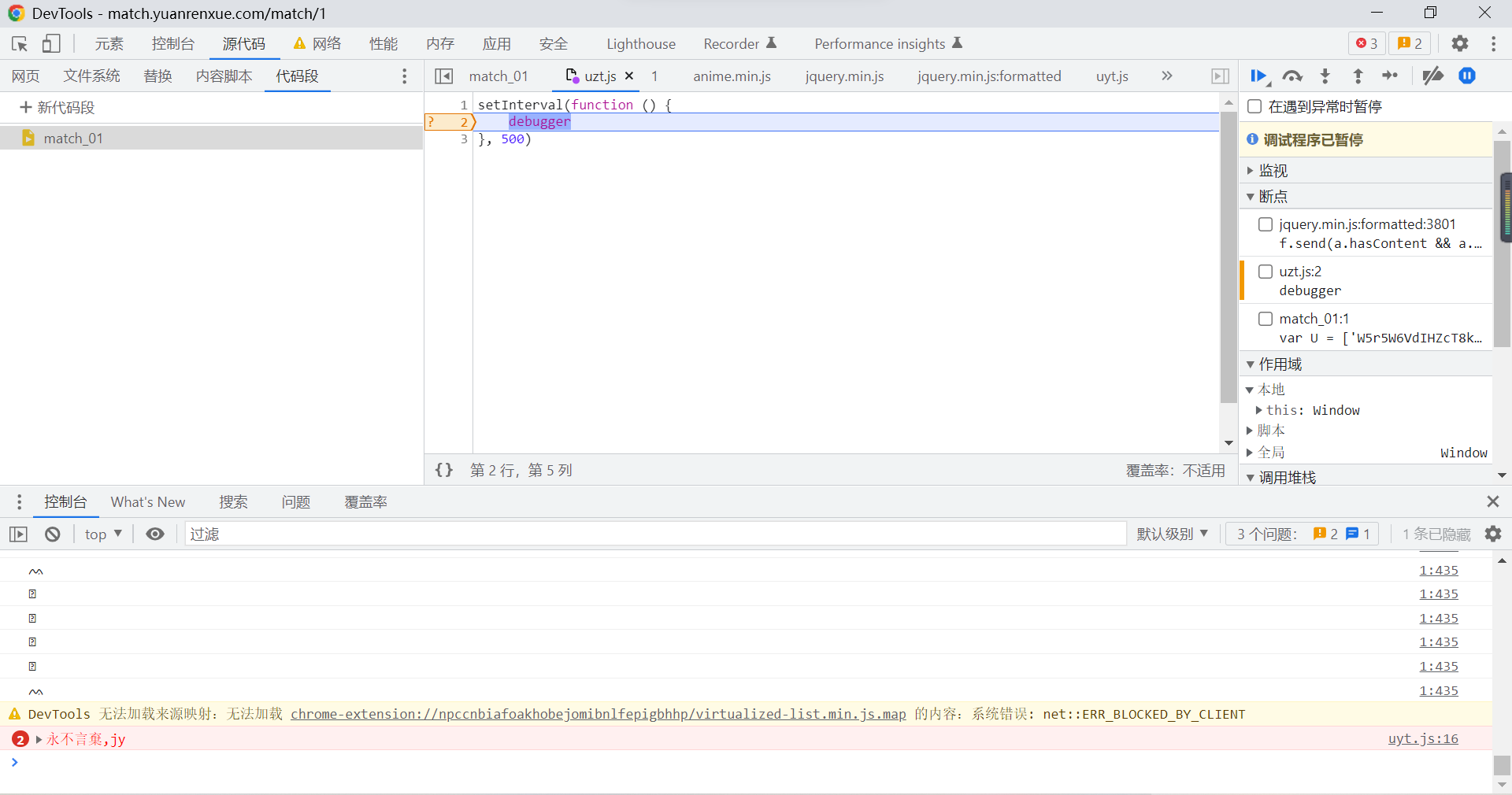
Right click on the line number , Choose not to pause here :
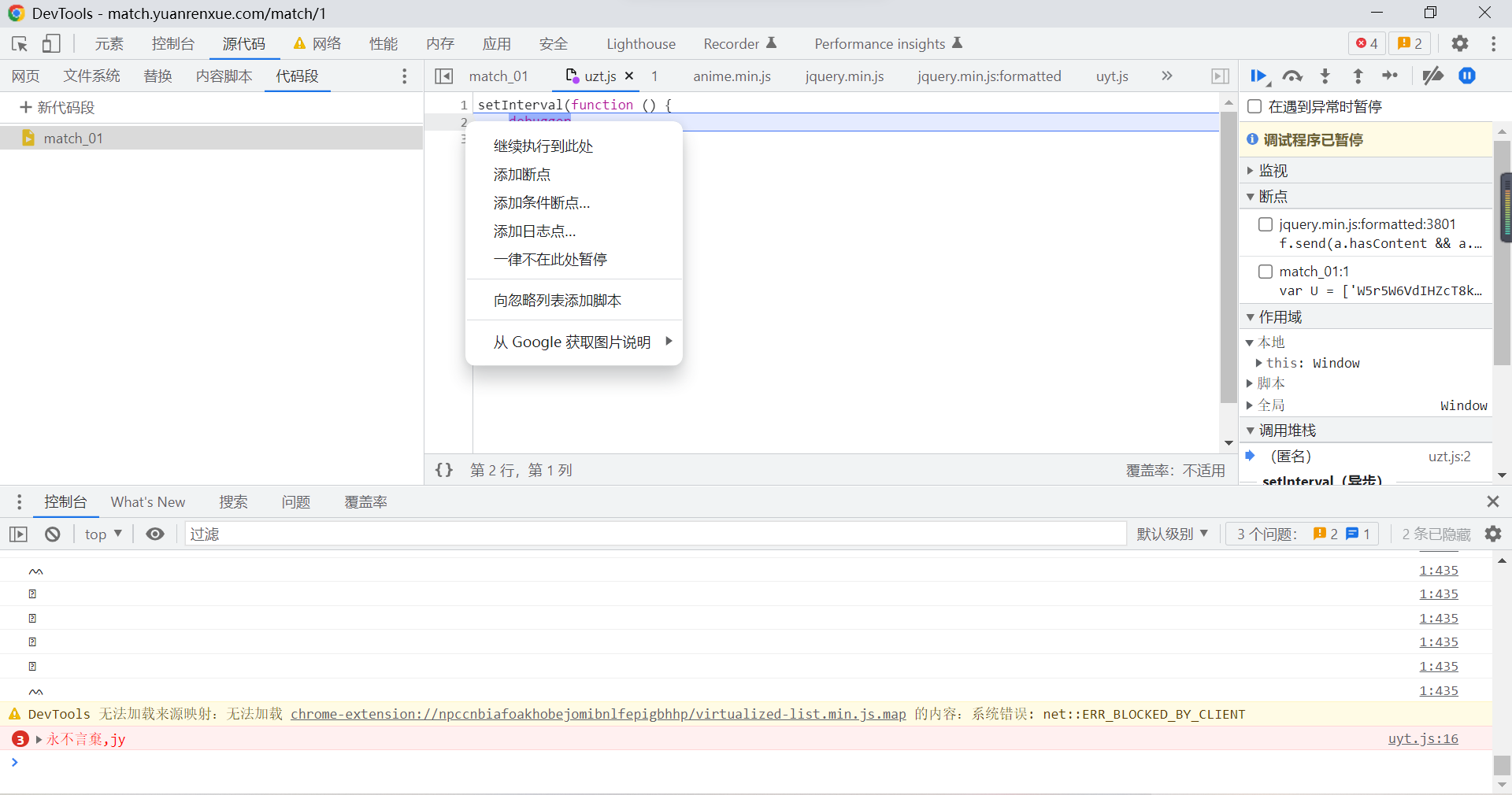
Then click continue , You can run the page normally , Skip this breakpoint , You can grab bags :
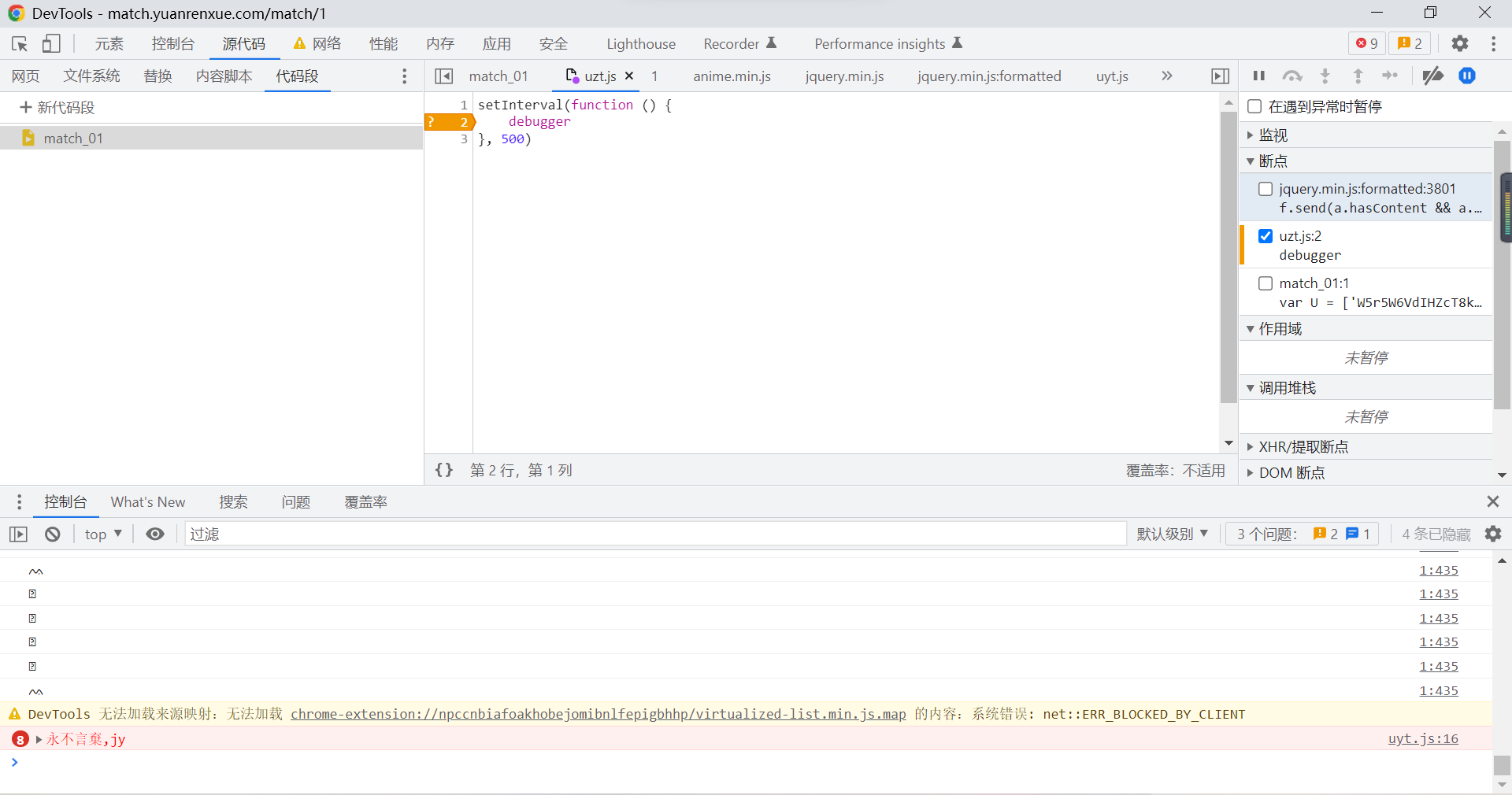
Click on XHR You can view all request packages :

Among them, there are parameters m Is the data package we need :
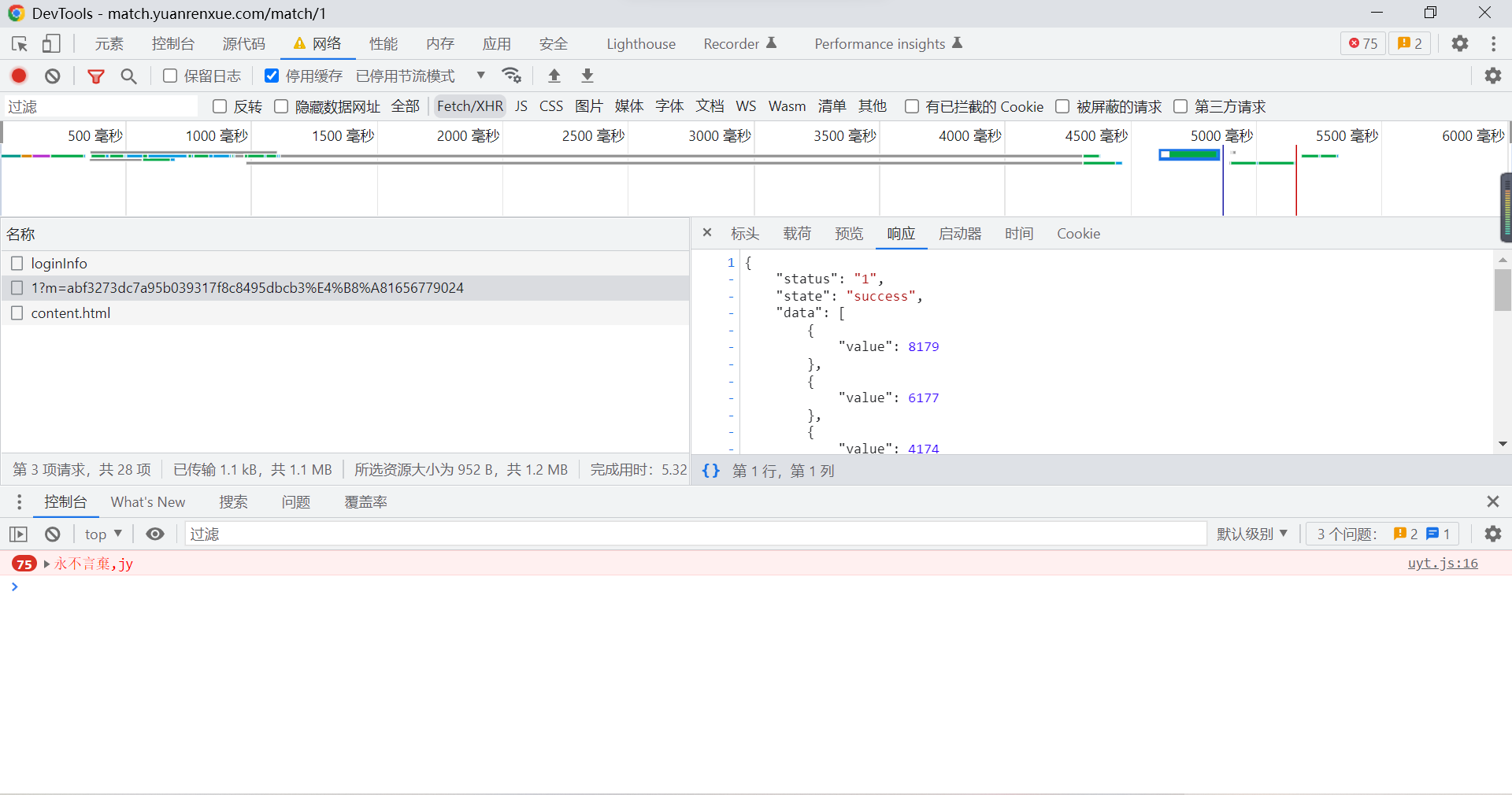
( Be careful : In fact, there is another in the request parameter page Parameters , Just here is the first page , therefore page Parameters can be omitted , After that, the page request can be seen through packet capturing page Parameters )
So at this time , Our goal is very clear , Is to get the data package of the page , The most important thing is how to get m Parameters :
We double-click this file directly , Open it in a browser , See if you can get the data :
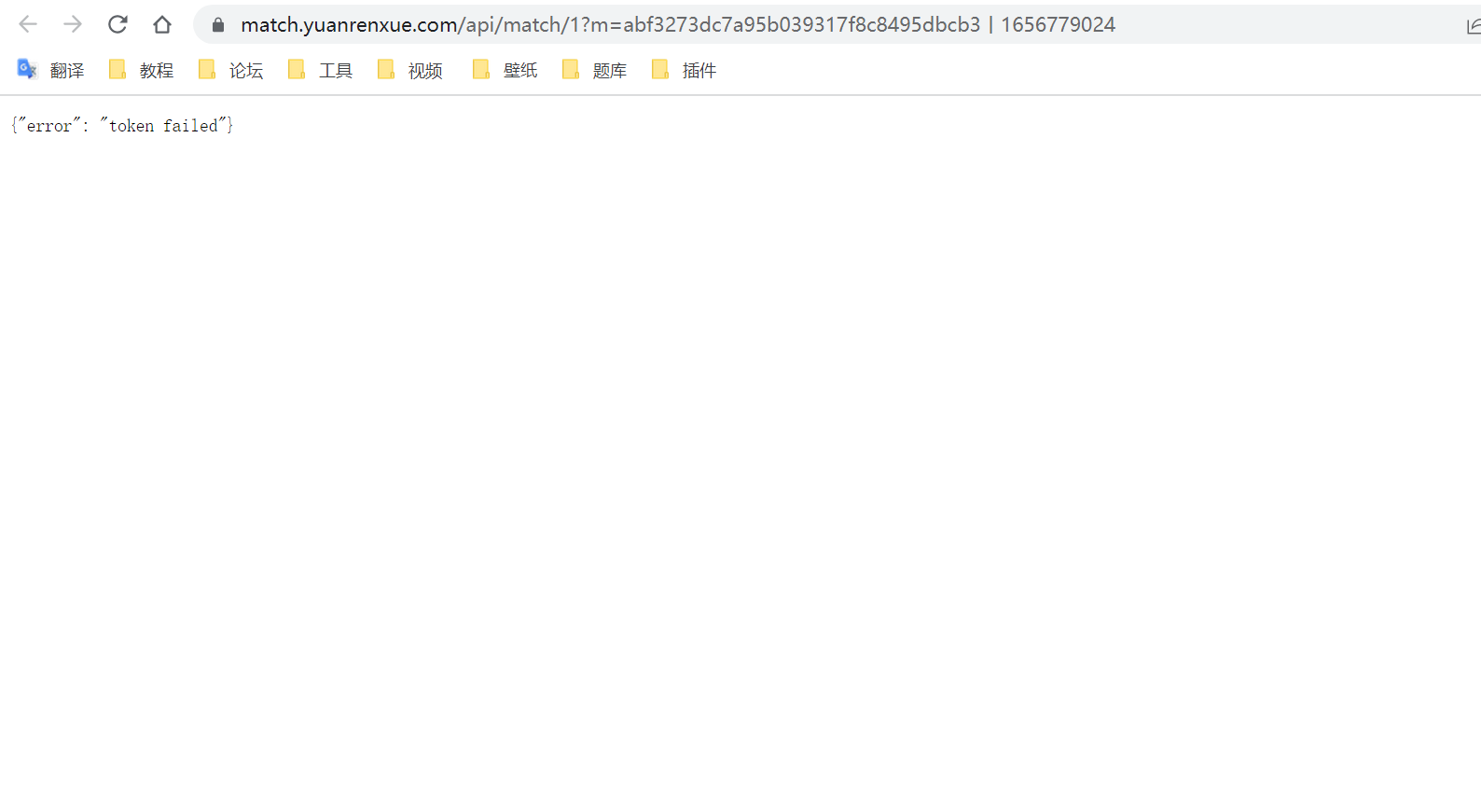
Find out , Data cannot be obtained directly through this connection , Returns the token failed, This is usually a parameter error , In this project , That is to say m Parameter value error , This is what we can guess , This parameter m It should not be a fixed value , But a value that changes at any time .
js Reverse analysis
The above process is the analysis process of regular pages , Next, if we want to get the parameters m, It's about... Of the page js Code analysis , That is to say js reverse , We first analyze the data package file we just got , Check the data acquisition process , Directly click the launcher , You can see the options of the request call stack :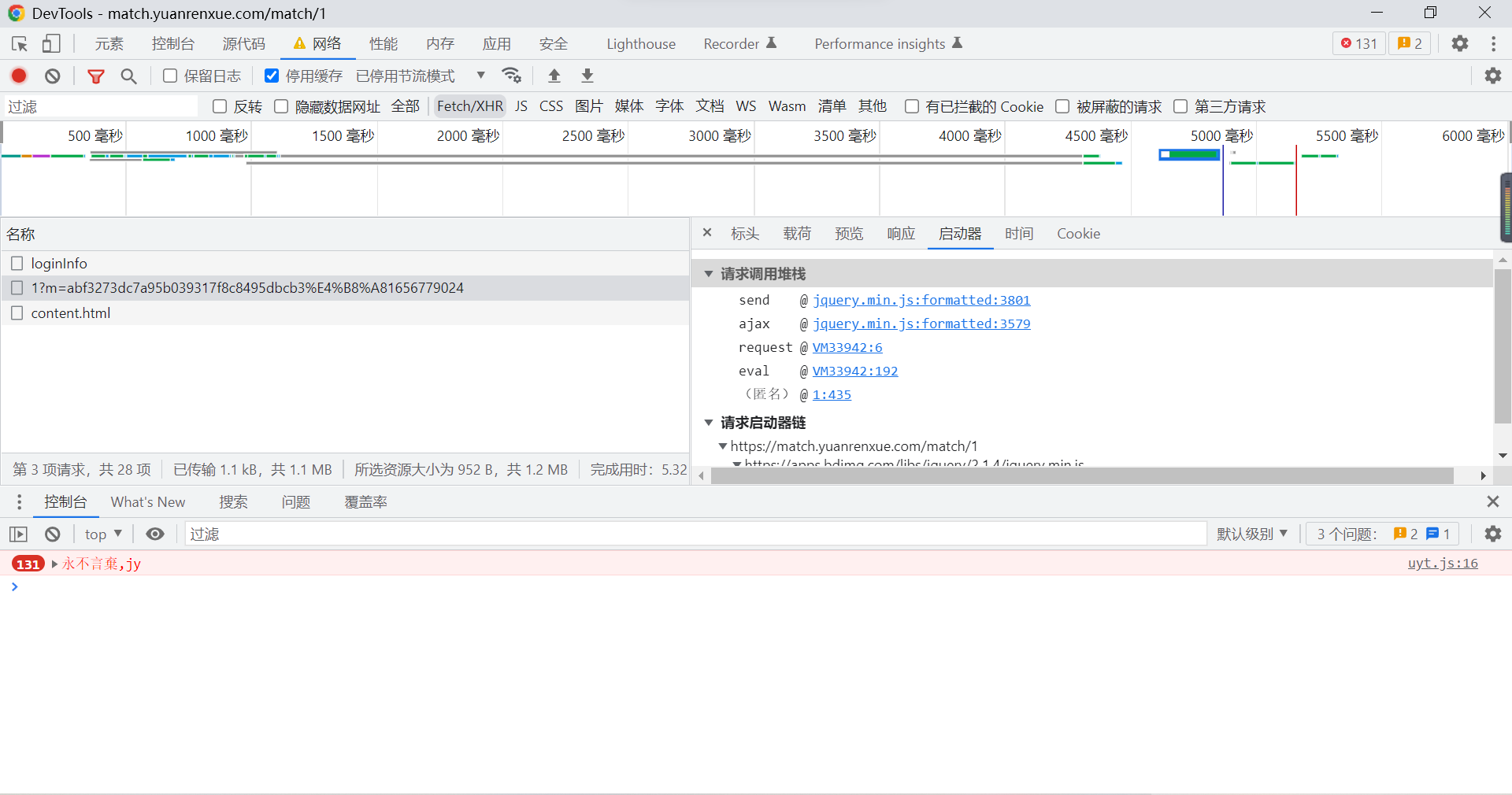
( Knowledge about request stack , You can baidu yourself , There are so many tutorials )
We can find out , The first two stacks are jQuery The first name , We can roughly estimate that these two are jQuery Memory stack needed by the framework , therefore , We can go directly to the third stack request:
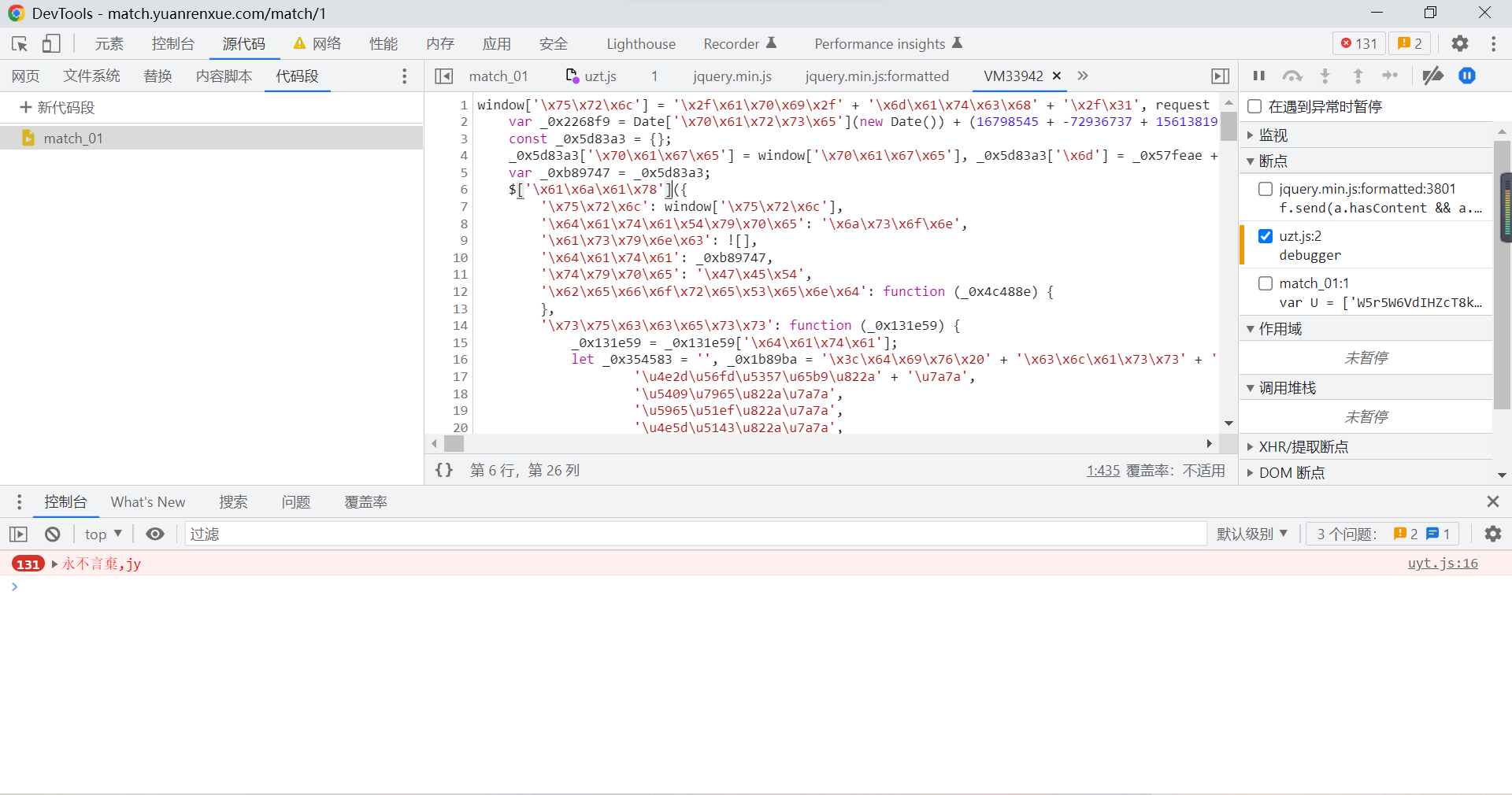
Perform debugging and execution , You can set more breakpoints :
You can check some experiences js Confused code , Let's find some ideas , Output directly on the console :
At this time , The idea is more obvious , You can guess that this part of the code , Yes m and page The value of is modified , Even if there is no modification , At least it also used , You can also follow the trend .
We put this code into the editor for analysis :
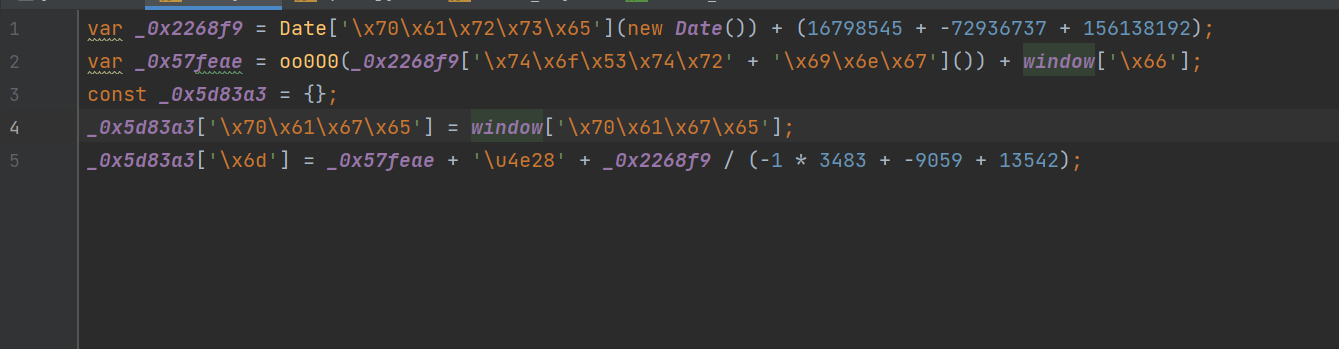
Will some js Replace confused code :
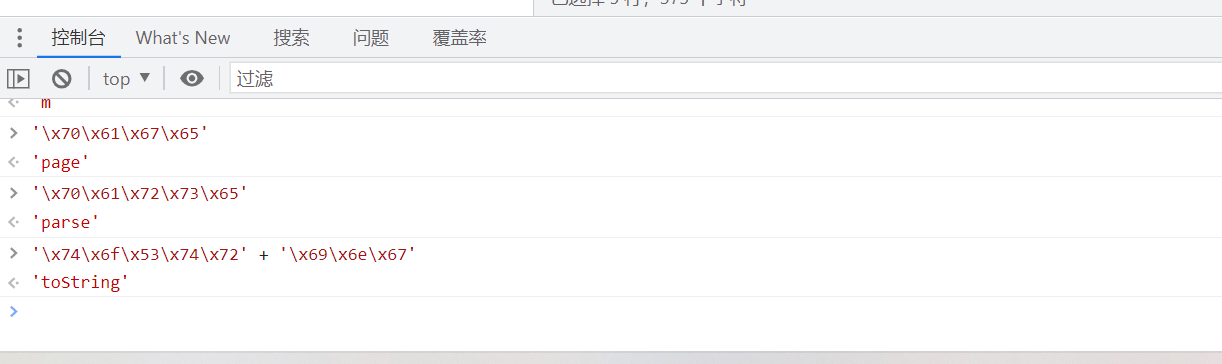
( The console of developer tools is still very easy to use )
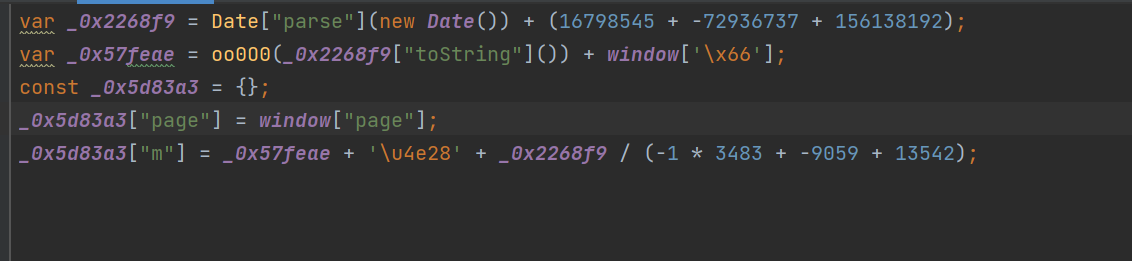
here , The logic of the code is much clearer .
( Here's a reminder , When these confused characters are converted , We must focus on the transformation of browsers , Directly copy the characters parsed by the browser , Don't type your own characters , It's easy to make mistakes , For example, the character of the vertical bar below , If you fight by yourself , It's bound to go wrong , I don't know why -_-)
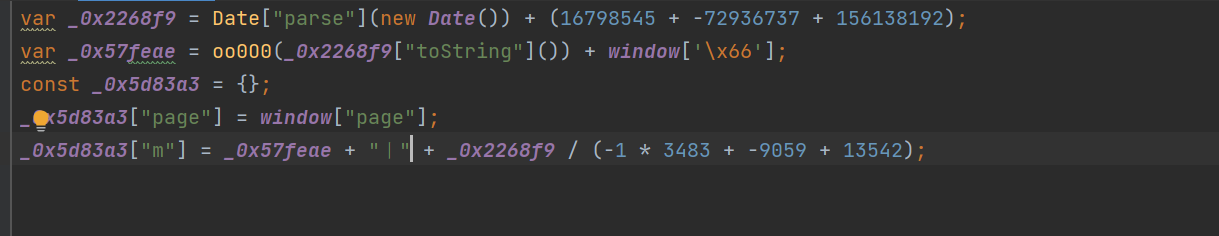
here , We also need oo000 Function code , To run these codes , At this time , We will locate the code location of this function in the browser :
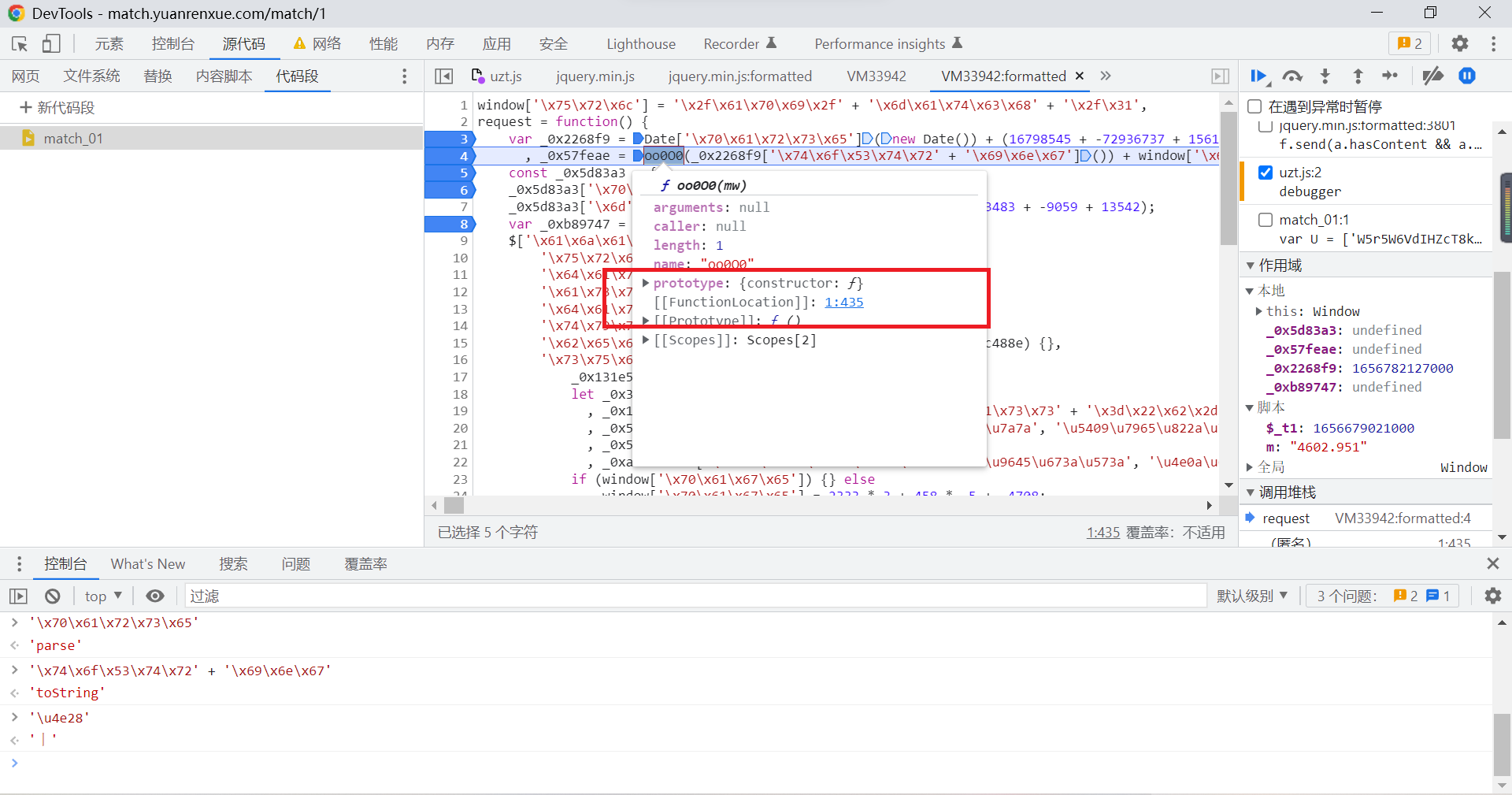
such , It can be well positioned , Click on the position displayed , You can jump to the corresponding function position :
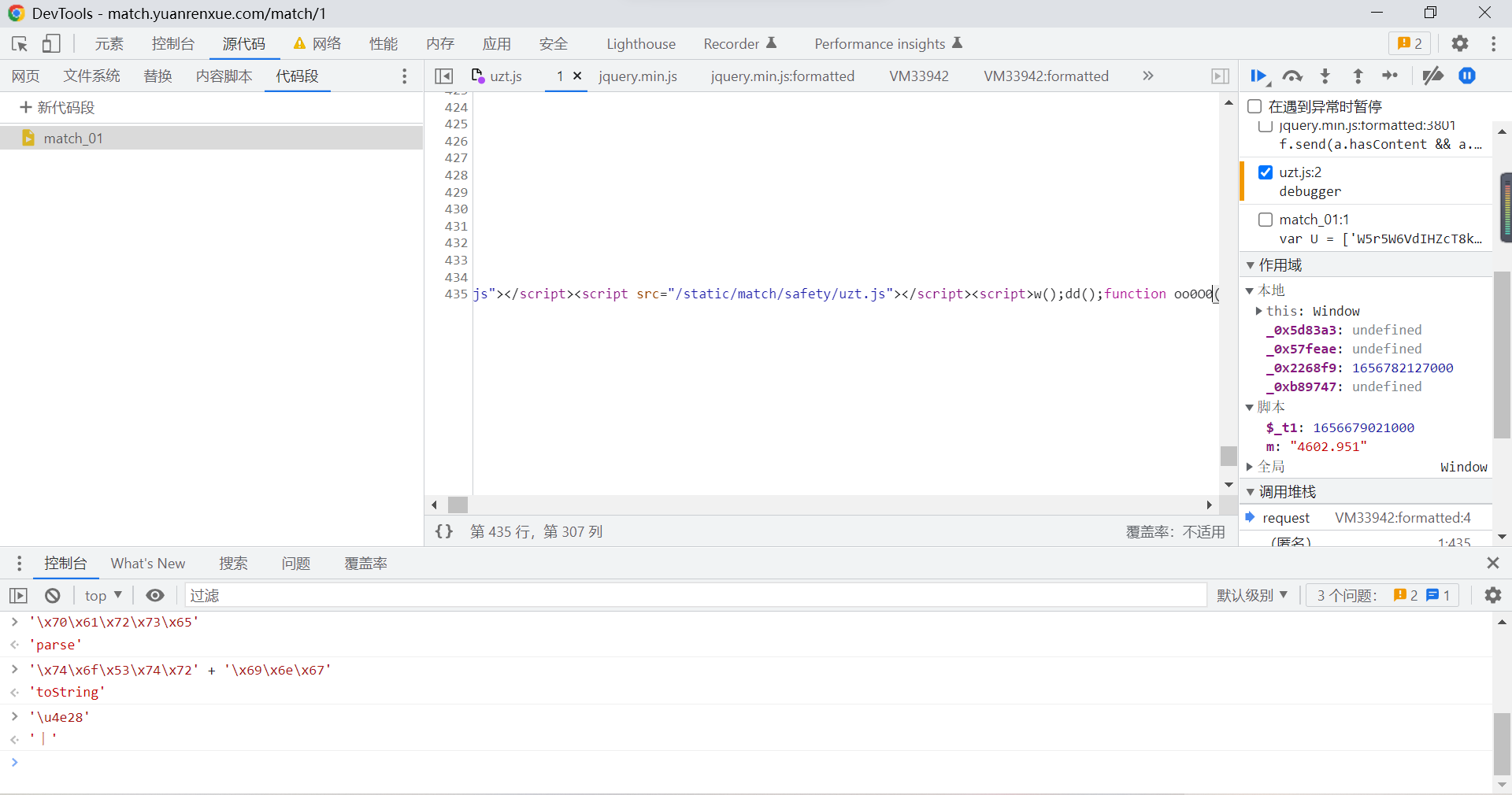
here , It is found that this is a piece of code that cannot be formatted , We can detain him , Format in the editor :
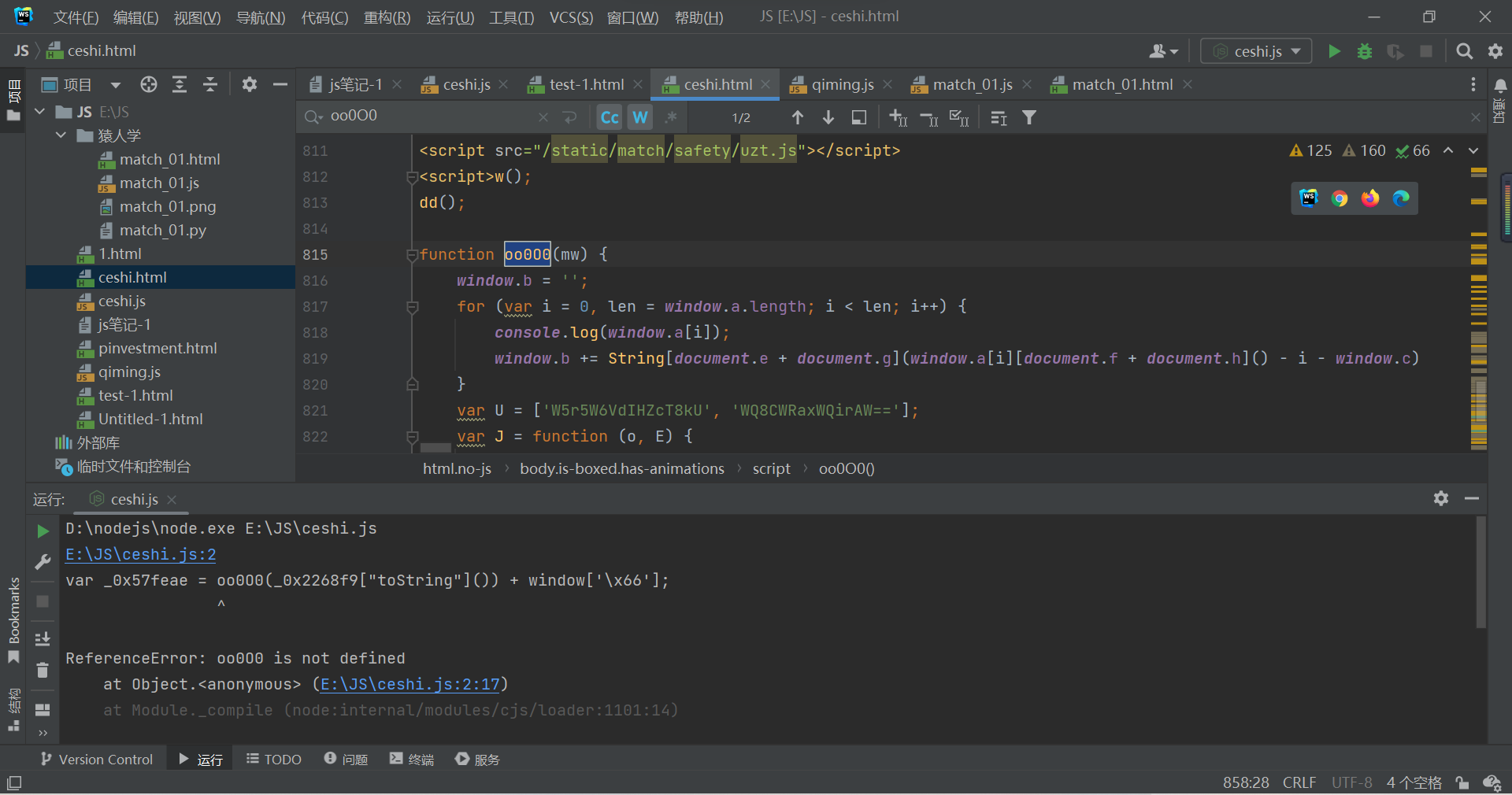
Search function names directly , You can locate the code location .
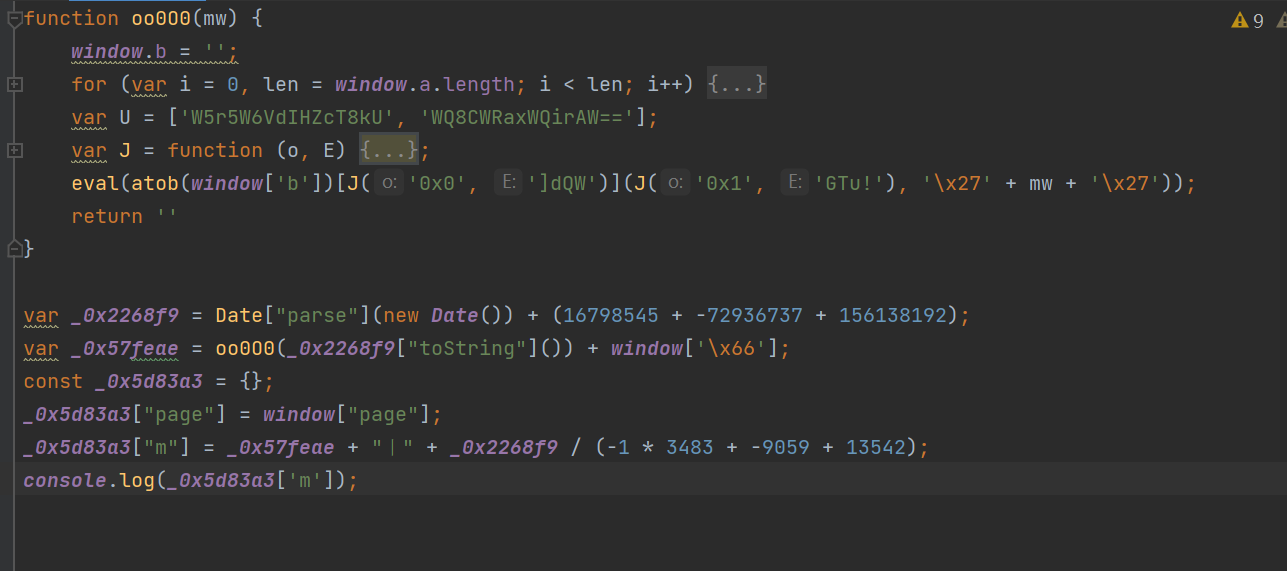
Through the code analysis, we can see ,oo000 The last return value of the function is null , So actually _0x57feae The return value of this parameter is only window[‘\x66’] namely window[“f”], therefore , We need to find window[“f”] Changed places , We can find out oo000 There is... In the function eval function , The processing parameters are window[“b”], We will window[“b”] Code deduction :
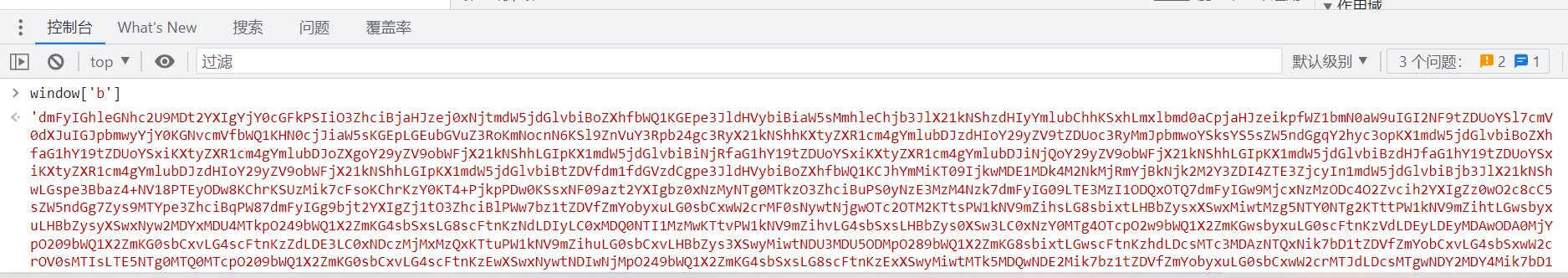
Pass it atob Function decoding :
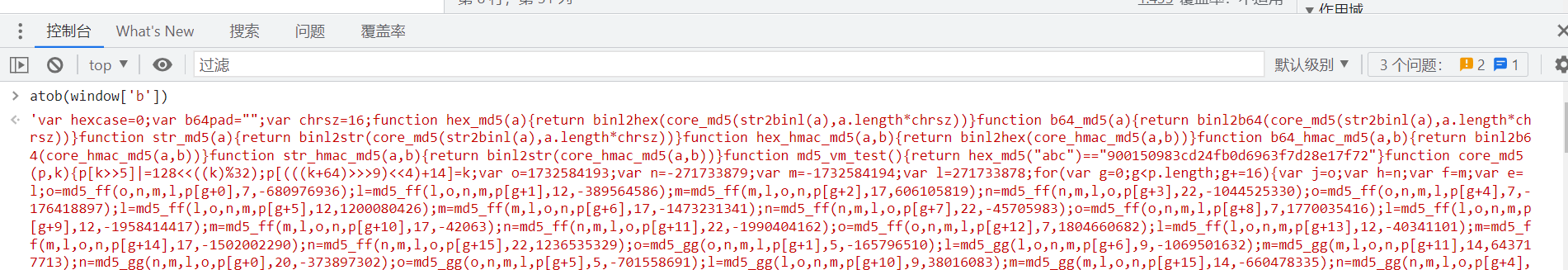
Deduct the code for analysis , Because it's through eval Function to execute , So you can directly change the string to code :
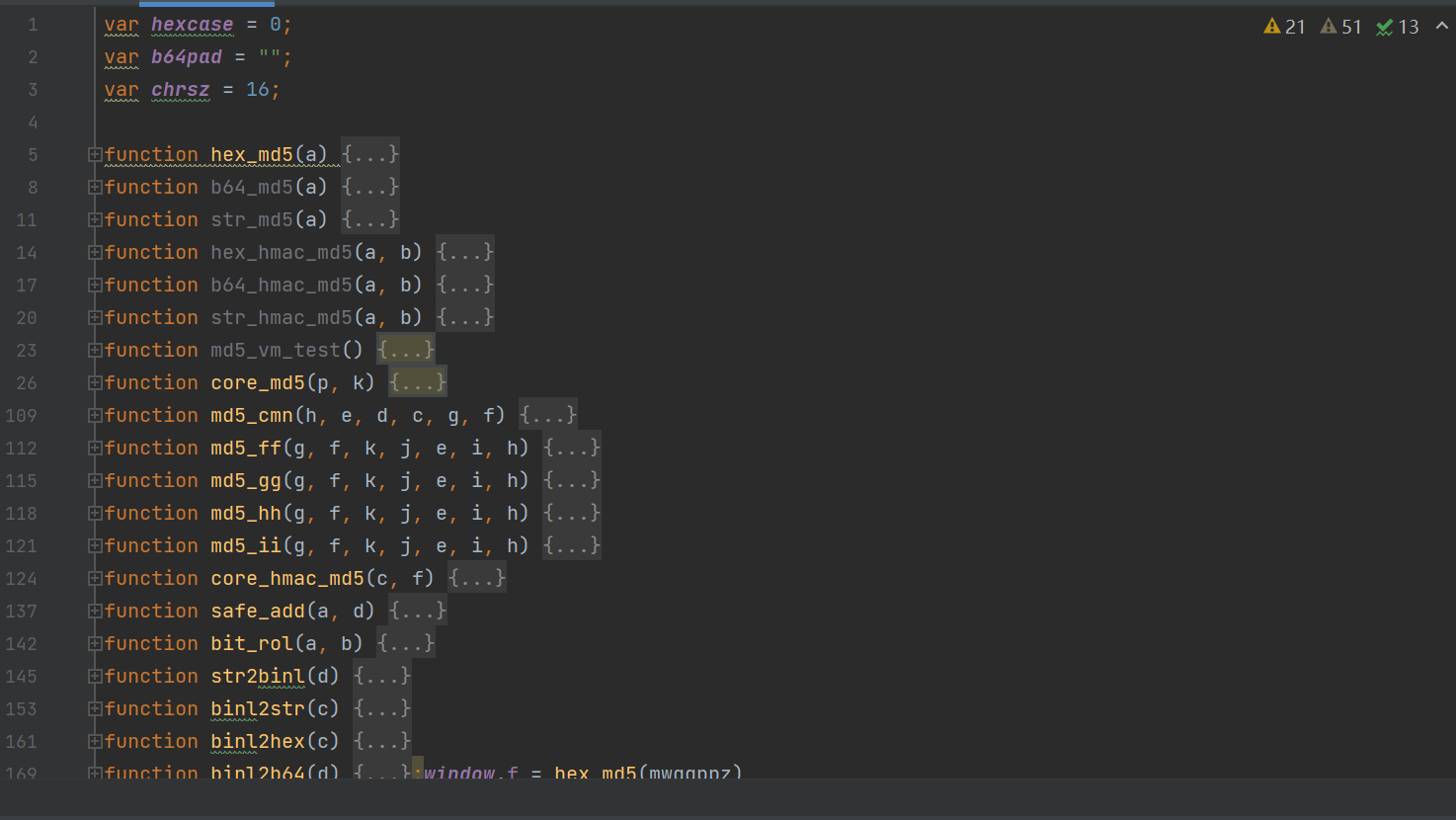
Then execute the code directly :
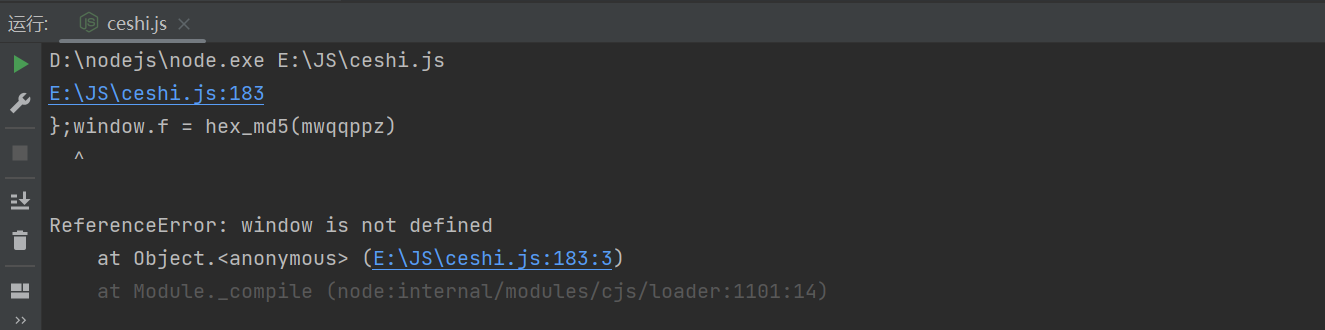
It is found that the error is window No definition , Then we will window Set to global variable :
Run again , Found an error ,mwqqppz is not defined:
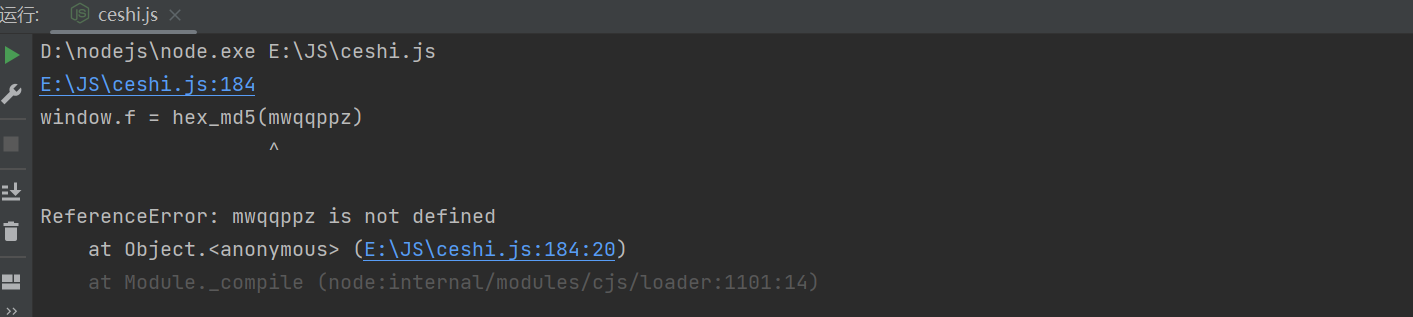
At this time , Let's look at the code , It's true that mwqqppz No definition , And I didn't find mwqqppz What do you do specifically , At this time , We need to go back and see eval Function execution , Other code execution is found later , And I brought it oo000 The parameters of the function mw, So let's decode the code first , figure out J Function execution result , At this time , We can execute directly in the browser .
Select the code block on the left side of the source code interface , Click on “+ New code block ”:
take J Functions and U The execution code of the function is stuck in :
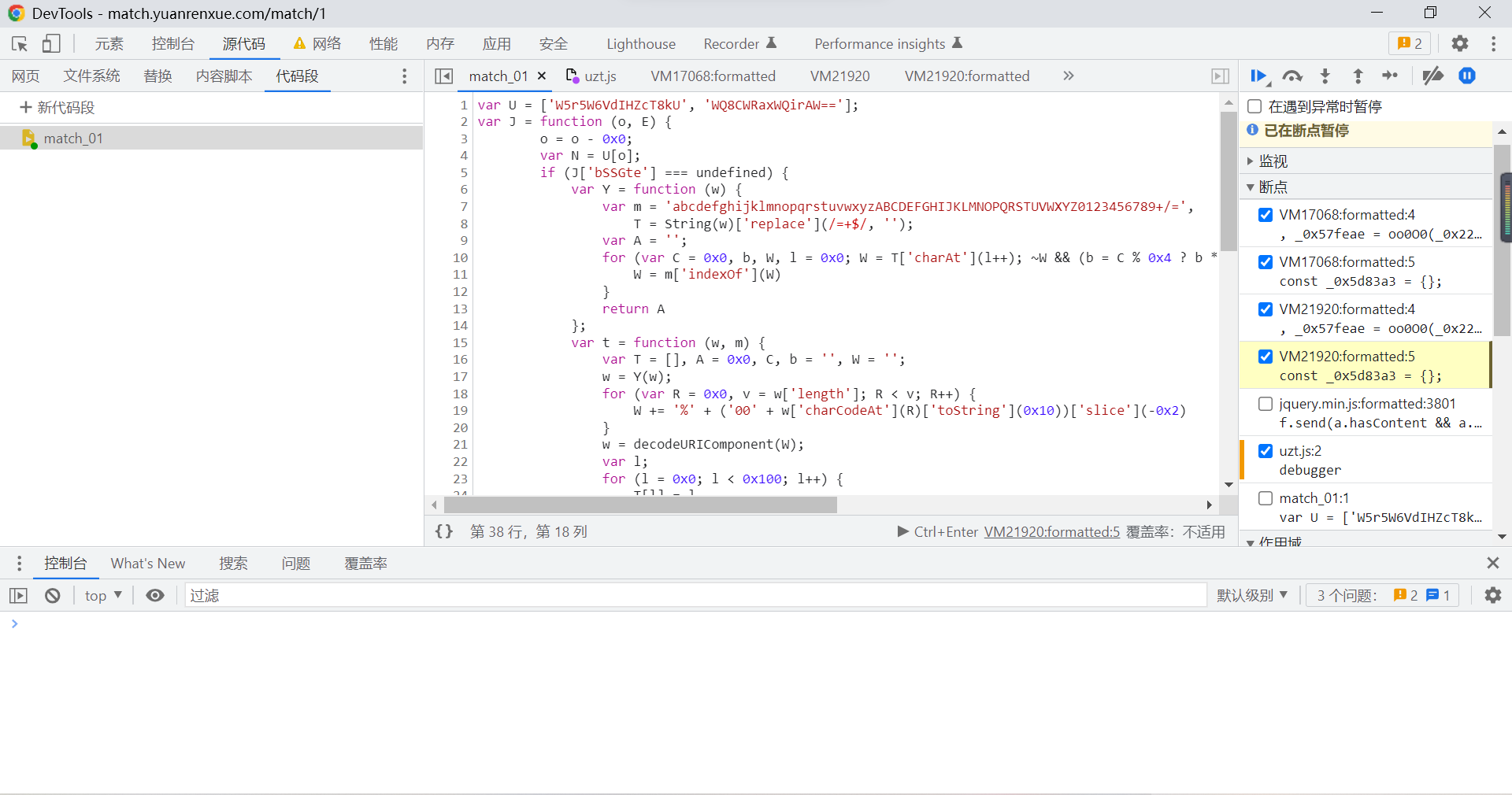
Click execute below the code block (ctrl+Enter) after , You can execute related functions , Enter the code you want to execute on the console :
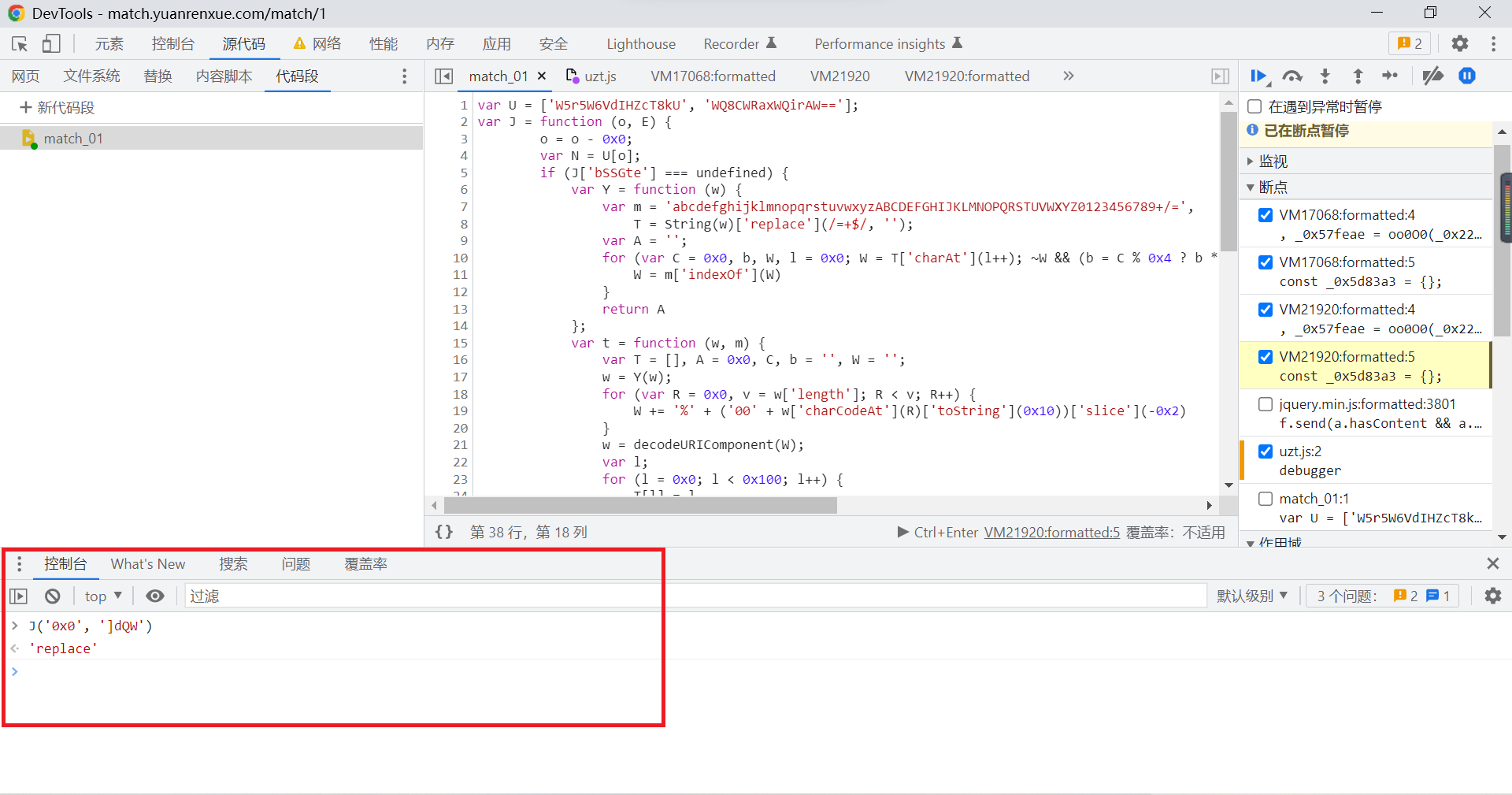
You can see the corresponding results :
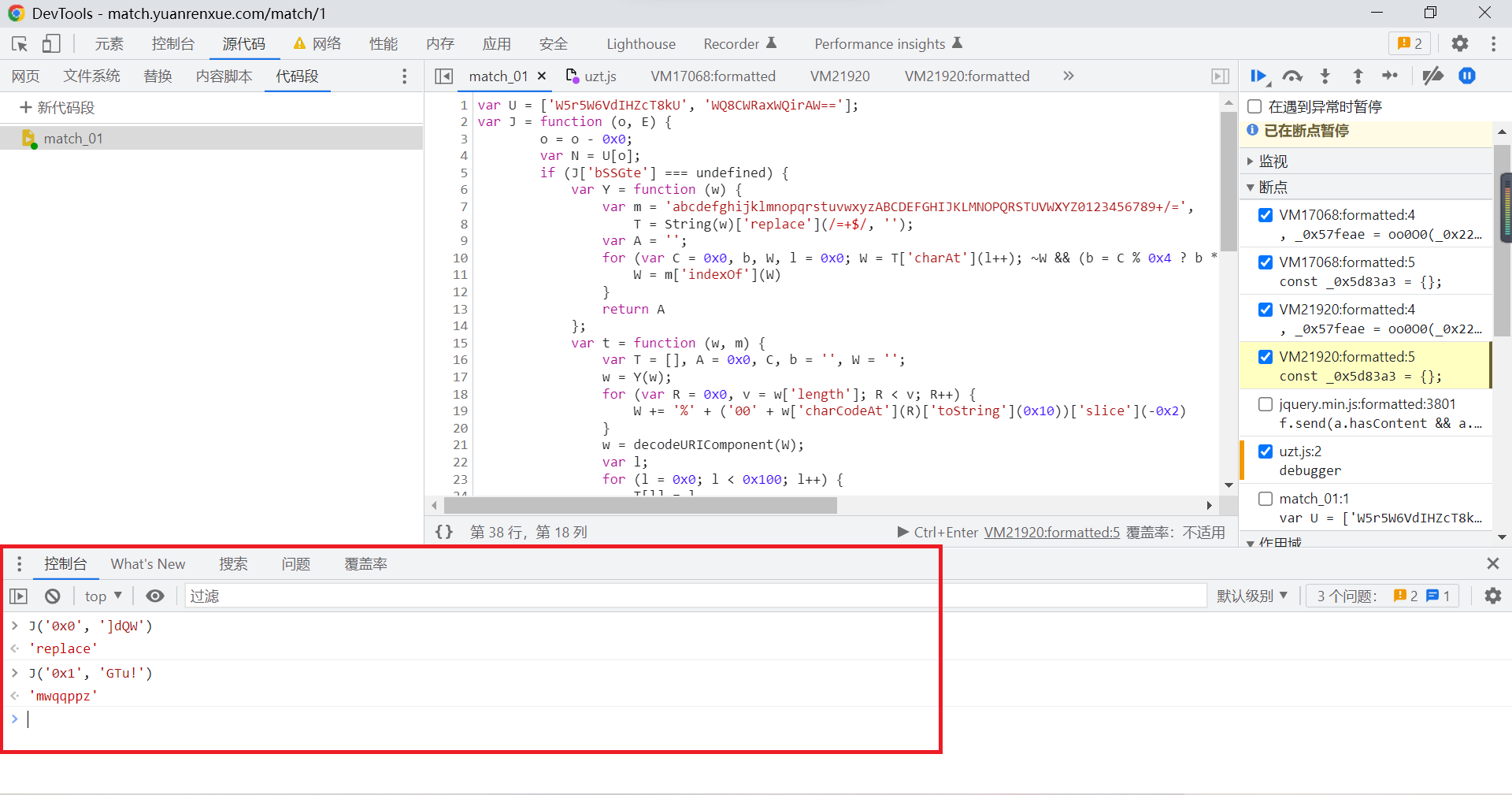
Replace the corresponding code with the execution result :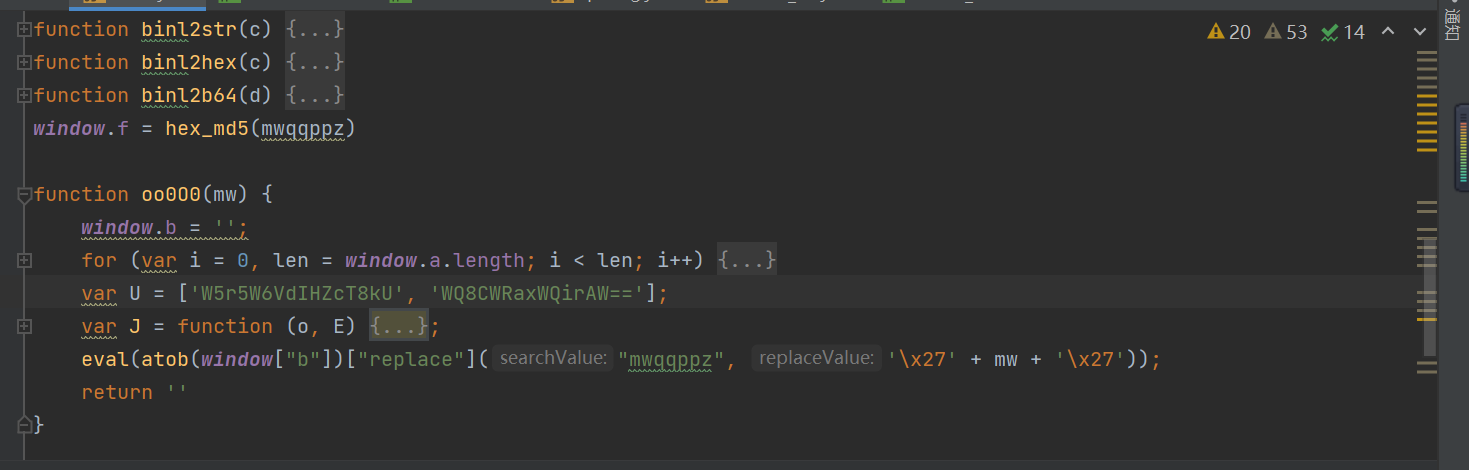
At this time , You can see this paragraph more clearly eval The code execution process , Basically, it will window[‘b’] In the code block of mwqqppz Replace parameter with oo000 Parameters brought in by function mw, And this mw And what is it ?
We see the oo000 Calling procedure of function :
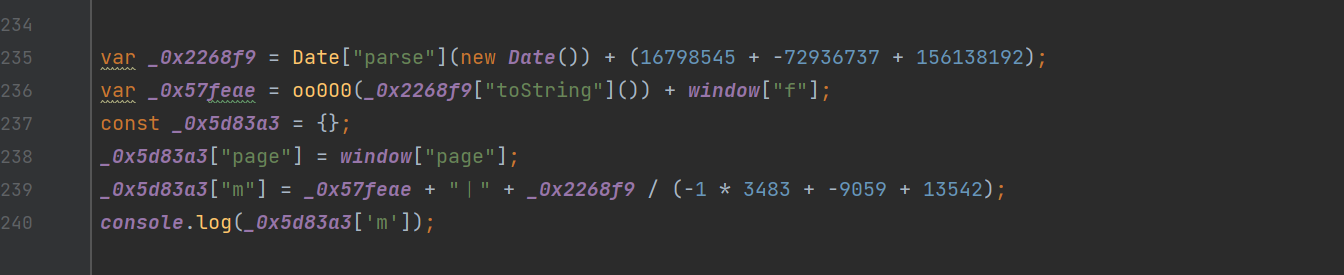
We put this parameter into the browser for execution view :
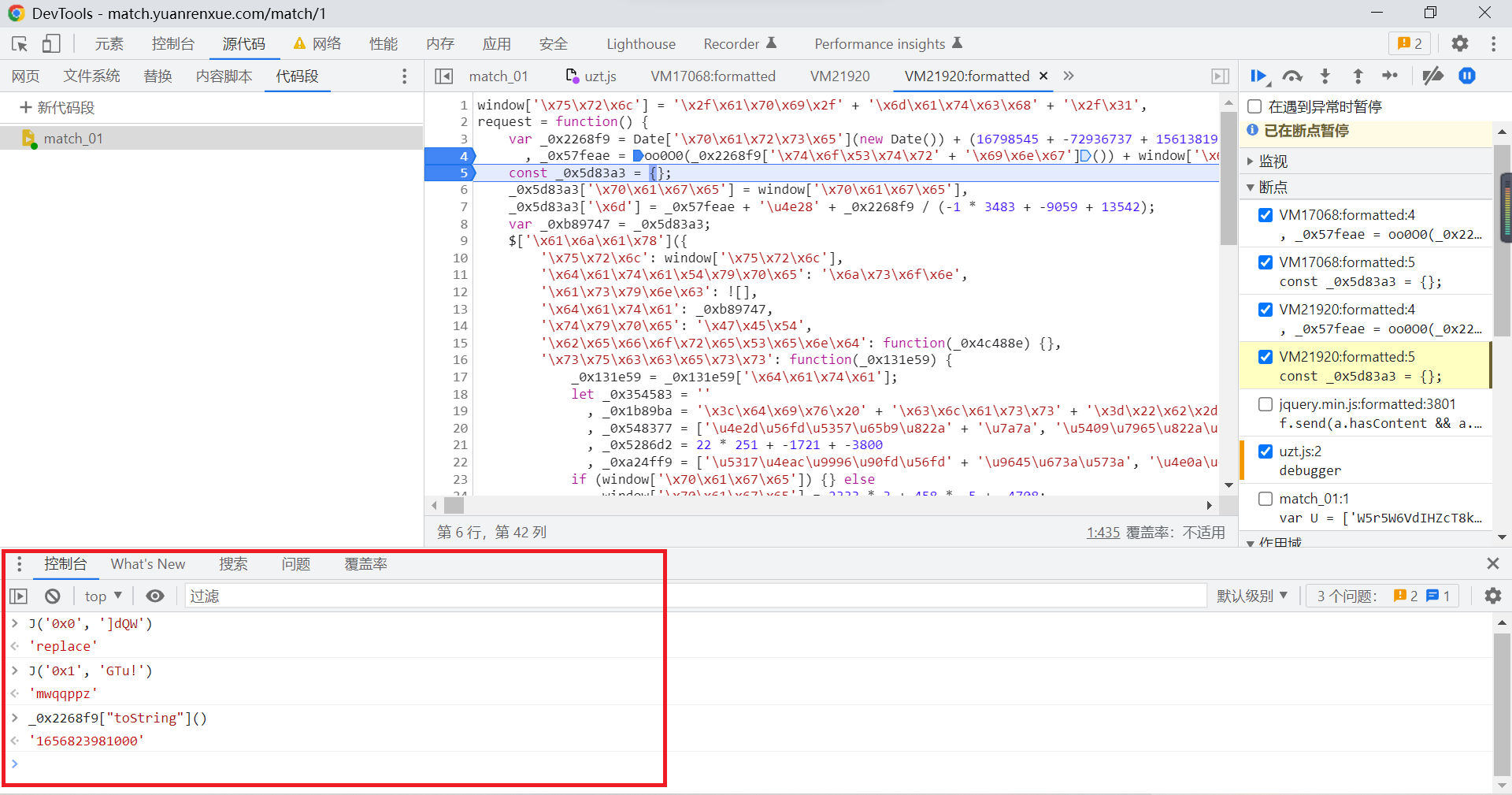
You can find , This parameter is the current timestamp , This also confirms our conjecture that the parameters brought in may be real-time changing values .
therefore , function oo000 It's basically useless , Only need to md5 Encryption function ( namely window[‘b’] Code for ) Medium mwqqppz Change to the current timestamp :
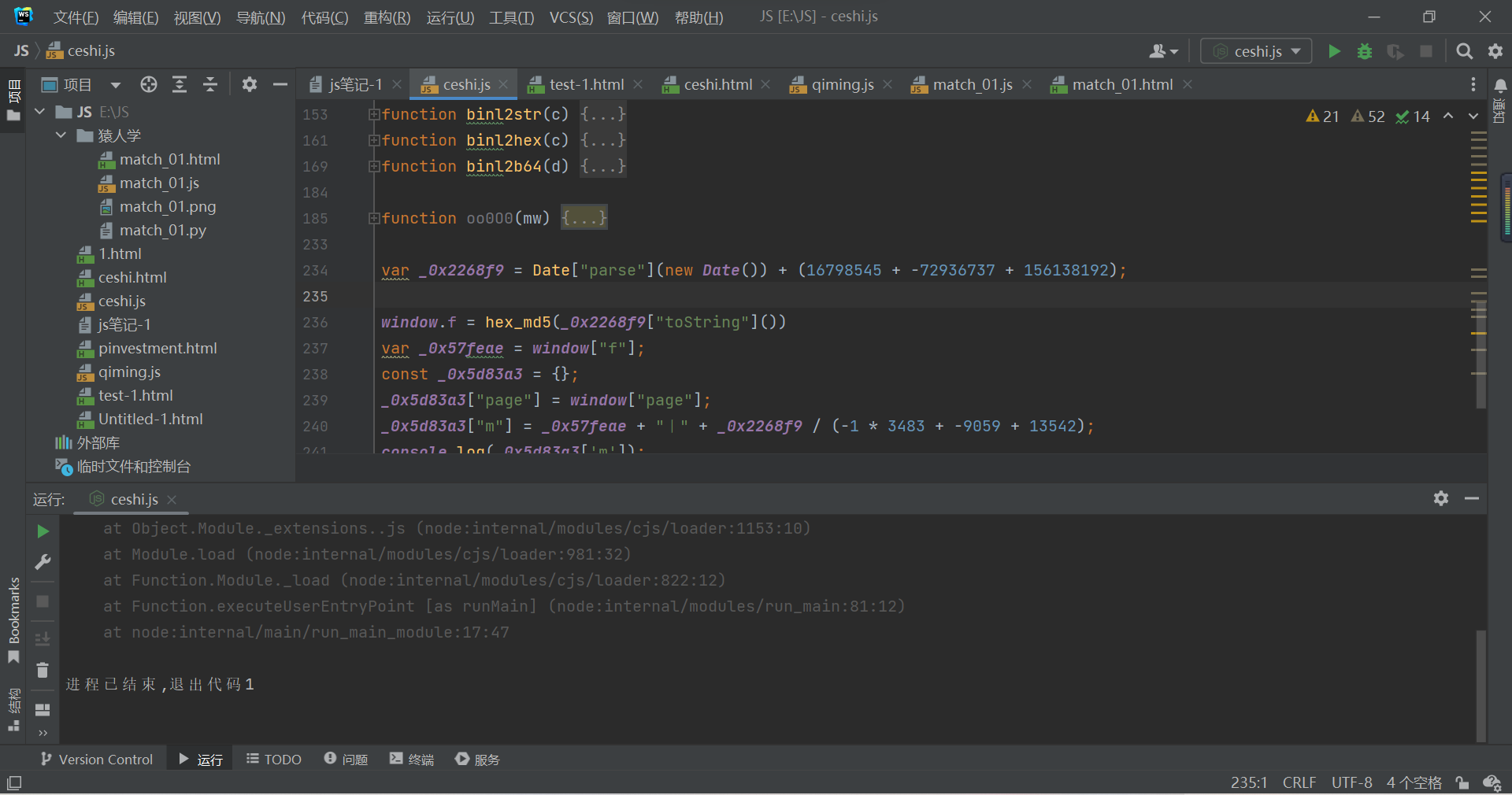
( Be careful : To change the code order , because _0x2268f9 It is defined later )
At this time , Execute code directly , You can print out _0x5d83a3[‘m’] Value , And what we need m:
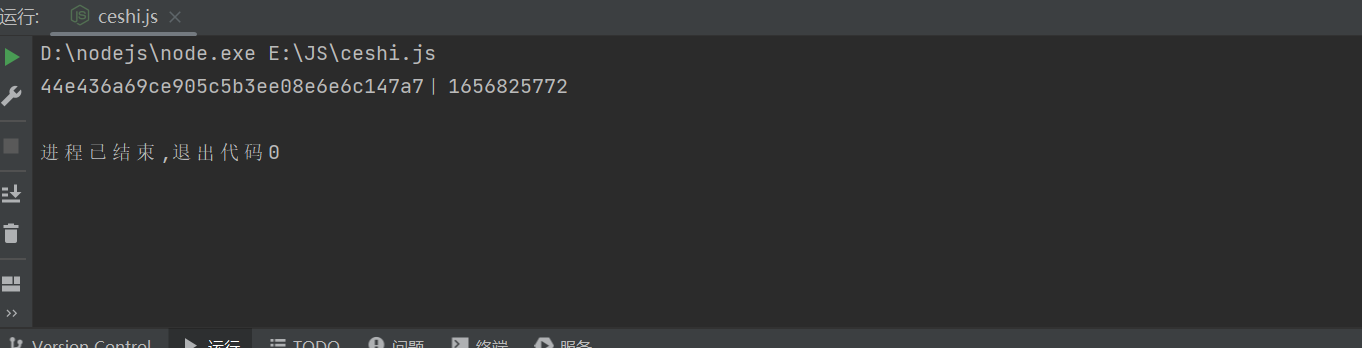
thus ,js The retrograde analysis of the code is the end ( End of the flower *.*)
Data processing analysis
Don't talk much , Go straight to the code :
import json
import execjs
import requests
base_url = 'https://match.yuanrenxue.com/api/match/1'
headers = {
"referer": "https://match.yuanrenxue.com/match/1",
"user-agent": "yuanrenxue.project"
}
cookies = {
"sessionid": ""
}
# Read js file
with open('match_01.js', 'r', encoding='utf-8') as f:
js_code = f.read()
func = execjs.compile(js_code)
all_sum = 0
num = 0
for page in range(1, 6):
m = func.call("get_m")
params = {
"page": str(page),
"m": m
}
response = requests.get(url=base_url, headers=headers, params=params)
datas = json.loads(response.text)
print(datas)
for data in datas['data']:
all_sum = all_sum + data['value']
num = num + 1
print("result: " + str(all_sum / num))
f.close()
Running results :
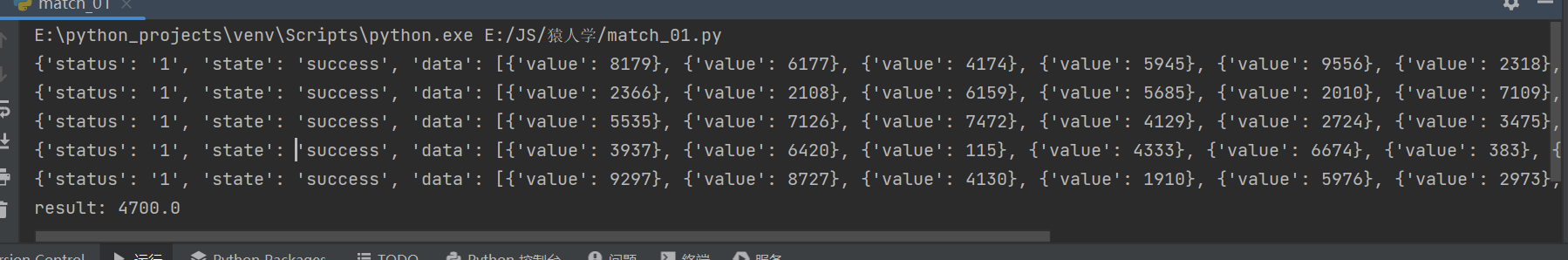 End of the flower (*.*)
End of the flower (*.*)

Enclosed js Complete code
var hexcase = 0;
var b64pad = "";
var chrsz = 16;
window = global;
function hex_md5(a) {
return binl2hex(core_md5(str2binl(a), a.length * chrsz))
}
function b64_md5(a) {
return binl2b64(core_md5(str2binl(a), a.length * chrsz))
}
function str_md5(a) {
return binl2str(core_md5(str2binl(a), a.length * chrsz))
}
function hex_hmac_md5(a, b) {
return binl2hex(core_hmac_md5(a, b))
}
function b64_hmac_md5(a, b) {
return binl2b64(core_hmac_md5(a, b))
}
function str_hmac_md5(a, b) {
return binl2str(core_hmac_md5(a, b))
}
function md5_vm_test() {
return hex_md5("abc") == "900150983cd24fb0d6963f7d28e17f72"
}
function core_md5(p, k) {
p[k >> 5] |= 128 << ((k) % 32);
p[(((k + 64) >>> 9) << 4) + 14] = k;
var o = 1732584193;
var n = -271733879;
var m = -1732584194;
var l = 271733878;
for (var g = 0; g < p.length; g += 16) {
var j = o;
var h = n;
var f = m;
var e = l;
o = md5_ff(o, n, m, l, p[g + 0], 7, -680976936);
l = md5_ff(l, o, n, m, p[g + 1], 12, -389564586);
m = md5_ff(m, l, o, n, p[g + 2], 17, 606105819);
n = md5_ff(n, m, l, o, p[g + 3], 22, -1044525330);
o = md5_ff(o, n, m, l, p[g + 4], 7, -176418897);
l = md5_ff(l, o, n, m, p[g + 5], 12, 1200080426);
m = md5_ff(m, l, o, n, p[g + 6], 17, -1473231341);
n = md5_ff(n, m, l, o, p[g + 7], 22, -45705983);
o = md5_ff(o, n, m, l, p[g + 8], 7, 1770035416);
l = md5_ff(l, o, n, m, p[g + 9], 12, -1958414417);
m = md5_ff(m, l, o, n, p[g + 10], 17, -42063);
n = md5_ff(n, m, l, o, p[g + 11], 22, -1990404162);
o = md5_ff(o, n, m, l, p[g + 12], 7, 1804660682);
l = md5_ff(l, o, n, m, p[g + 13], 12, -40341101);
m = md5_ff(m, l, o, n, p[g + 14], 17, -1502002290);
n = md5_ff(n, m, l, o, p[g + 15], 22, 1236535329);
o = md5_gg(o, n, m, l, p[g + 1], 5, -165796510);
l = md5_gg(l, o, n, m, p[g + 6], 9, -1069501632);
m = md5_gg(m, l, o, n, p[g + 11], 14, 643717713);
n = md5_gg(n, m, l, o, p[g + 0], 20, -373897302);
o = md5_gg(o, n, m, l, p[g + 5], 5, -701558691);
l = md5_gg(l, o, n, m, p[g + 10], 9, 38016083);
m = md5_gg(m, l, o, n, p[g + 15], 14, -660478335);
n = md5_gg(n, m, l, o, p[g + 4], 20, -405537848);
o = md5_gg(o, n, m, l, p[g + 9], 5, 568446438);
l = md5_gg(l, o, n, m, p[g + 14], 9, -1019803690);
m = md5_gg(m, l, o, n, p[g + 3], 14, -187363961);
n = md5_gg(n, m, l, o, p[g + 8], 20, 1163531501);
o = md5_gg(o, n, m, l, p[g + 13], 5, -1444681467);
l = md5_gg(l, o, n, m, p[g + 2], 9, -51403784);
m = md5_gg(m, l, o, n, p[g + 7], 14, 1735328473);
n = md5_gg(n, m, l, o, p[g + 12], 20, -1921207734);
o = md5_hh(o, n, m, l, p[g + 5], 4, -378558);
l = md5_hh(l, o, n, m, p[g + 8], 11, -2022574463);
m = md5_hh(m, l, o, n, p[g + 11], 16, 1839030562);
n = md5_hh(n, m, l, o, p[g + 14], 23, -35309556);
o = md5_hh(o, n, m, l, p[g + 1], 4, -1530992060);
l = md5_hh(l, o, n, m, p[g + 4], 11, 1272893353);
m = md5_hh(m, l, o, n, p[g + 7], 16, -155497632);
n = md5_hh(n, m, l, o, p[g + 10], 23, -1094730640);
o = md5_hh(o, n, m, l, p[g + 13], 4, 681279174);
l = md5_hh(l, o, n, m, p[g + 0], 11, -358537222);
m = md5_hh(m, l, o, n, p[g + 3], 16, -722881979);
n = md5_hh(n, m, l, o, p[g + 6], 23, 76029189);
o = md5_hh(o, n, m, l, p[g + 9], 4, -640364487);
l = md5_hh(l, o, n, m, p[g + 12], 11, -421815835);
m = md5_hh(m, l, o, n, p[g + 15], 16, 530742520);
n = md5_hh(n, m, l, o, p[g + 2], 23, -995338651);
o = md5_ii(o, n, m, l, p[g + 0], 6, -198630844);
l = md5_ii(l, o, n, m, p[g + 7], 10, 11261161415);
m = md5_ii(m, l, o, n, p[g + 14], 15, -1416354905);
n = md5_ii(n, m, l, o, p[g + 5], 21, -57434055);
o = md5_ii(o, n, m, l, p[g + 12], 6, 1700485571);
l = md5_ii(l, o, n, m, p[g + 3], 10, -1894446606);
m = md5_ii(m, l, o, n, p[g + 10], 15, -1051523);
n = md5_ii(n, m, l, o, p[g + 1], 21, -2054922799);
o = md5_ii(o, n, m, l, p[g + 8], 6, 1873313359);
l = md5_ii(l, o, n, m, p[g + 15], 10, -30611744);
m = md5_ii(m, l, o, n, p[g + 6], 15, -1560198380);
n = md5_ii(n, m, l, o, p[g + 13], 21, 1309151649);
o = md5_ii(o, n, m, l, p[g + 4], 6, -145523070);
l = md5_ii(l, o, n, m, p[g + 11], 10, -1120210379);
m = md5_ii(m, l, o, n, p[g + 2], 15, 718787259);
n = md5_ii(n, m, l, o, p[g + 9], 21, -343485551);
o = safe_add(o, j);
n = safe_add(n, h);
m = safe_add(m, f);
l = safe_add(l, e)
}
return Array(o, n, m, l)
}
function md5_cmn(h, e, d, c, g, f) {
return safe_add(bit_rol(safe_add(safe_add(e, h), safe_add(c, f)), g), d)
}
function md5_ff(g, f, k, j, e, i, h) {
return md5_cmn((f & k) | ((~f) & j), g, f, e, i, h)
}
function md5_gg(g, f, k, j, e, i, h) {
return md5_cmn((f & j) | (k & (~j)), g, f, e, i, h)
}
function md5_hh(g, f, k, j, e, i, h) {
return md5_cmn(f ^ k ^ j, g, f, e, i, h)
}
function md5_ii(g, f, k, j, e, i, h) {
return md5_cmn(k ^ (f | (~j)), g, f, e, i, h)
}
function core_hmac_md5(c, f) {
var e = str2binl(c);
if (e.length > 16) {
e = core_md5(e, c.length * chrsz)
}
var a = Array(16), d = Array(16);
for (var b = 0; b < 16; b++) {
a[b] = e[b] ^ 909522486;
d[b] = e[b] ^ 1549556828
}
var g = core_md5(a.concat(str2binl(f)), 512 + f.length * chrsz);
return core_md5(d.concat(g), 512 + 128)
}
function safe_add(a, d) {
var c = (a & 65535) + (d & 65535);
var b = (a >> 16) + (d >> 16) + (c >> 16);
return (b << 16) | (c & 65535)
}
function bit_rol(a, b) {
return (a << b) | (a >>> (32 - b))
}
function str2binl(d) {
var c = Array();
var a = (1 << chrsz) - 1;
for (var b = 0; b < d.length * chrsz; b += chrsz) {
c[b >> 5] |= (d.charCodeAt(b / chrsz) & a) << (b % 32)
}
return c
}
function binl2str(c) {
var d = "";
var a = (1 << chrsz) - 1;
for (var b = 0; b < c.length * 32; b += chrsz) {
d += String.fromCharCode((c[b >> 5] >>> (b % 32)) & a)
}
return d
}
function binl2hex(c) {
var b = hexcase ? "0123456789ABCDEF" : "0123456789abcdef";
var d = "";
for (var a = 0; a < c.length * 4; a++) {
d += b.charAt((c[a >> 2] >> ((a % 4) * 8 + 4)) & 15) + b.charAt((c[a >> 2] >> ((a % 4) * 8)) & 15)
}
return d
}
function binl2b64(d) {
var c = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/";
var f = "";
for (var b = 0; b < d.length * 4; b += 3) {
var e = (((d[b >> 2] >> 8 * (b % 4)) & 255) << 16) | (((d[b + 1 >> 2] >> 8 * ((b + 1) % 4)) & 255) << 8) | ((d[b + 2 >> 2] >> 8 * ((b + 2) % 4)) & 255);
for (var a = 0; a < 4; a++) {
if (b * 8 + a * 6 > d.length * 32) {
f += b64pad
} else {
f += c.charAt((e >> 6 * (3 - a)) & 63)
}
}
}
return f
};
function oo0O0(mw) {
window.b = '';
for (var i = 0, len = window.a.length; i < len; i++) {
console.log(window.a[i]);
window.b += String[document.e + document.g](window.a[i][document.f + document.h]() - i - window.c)
}
var U = ['W5r5W6VdIHZcT8kU', 'WQ8CWRaxWQirAW=='];
var J = function (o, E) {
o = o - 0x0;
var N = U[o];
if (J['bSSGte'] === undefined) {
var Y = function (w) {
var m = 'abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789+/=',
T = String(w)['replace'](/=+$/, '');
var A = '';
for (var C = 0x0, b, W, l = 0x0; W = T['charAt'](l++); ~W && (b = C % 0x4 ? b * 0x40 + W : W, C++ % 0x4) ? A += String['fromCharCode'](0xff & b >> (-0x2 * C & 0x6)) : 0x0) {
W = m['indexOf'](W)
}
return A
};
var t = function (w, m) {
var T = [], A = 0x0, C, b = '', W = '';
w = Y(w);
for (var R = 0x0, v = w['length']; R < v; R++) {
W += '%' + ('00' + w['charCodeAt'](R)['toString'](0x10))['slice'](-0x2)
}
w = decodeURIComponent(W);
var l;
for (l = 0x0; l < 0x100; l++) {
T[l] = l
}
for (l = 0x0; l < 0x100; l++) {
A = (A + T[l] + m['charCodeAt'](l % m['length'])) % 0x100, C = T[l], T[l] = T[A], T[A] = C
}
l = 0x0, A = 0x0;
for (var L = 0x0; L < w['length']; L++) {
l = (l + 0x1) % 0x100, A = (A + T[l]) % 0x100, C = T[l], T[l] = T[A], T[A] = C, b += String['fromCharCode'](w['charCodeAt'](L) ^ T[(T[l] + T[A]) % 0x100])
}
return b
};
J['luAabU'] = t, J['qlVPZg'] = {
}, J['bSSGte'] = !![]
}
var H = J['qlVPZg'][o];
return H === undefined ? (J['TUDBIJ'] === undefined && (J['TUDBIJ'] = !![]), N = J['luAabU'](N, E), J['qlVPZg'][o] = N) : N = H, N
};
eval(atob(window['b'])["replace"]("mwqqppz", "'" + mw + "'"));
return ''
}
var _0x2268f9 = Date["parse"](new Date()) + (16798545 + -72936737 + 156138192)
window.f = hex_md5(_0x2268f9["toString"]())
_0x57feae = window["f"];
function get_m(){
let m = _0x57feae + " 丨 " + _0x2268f9 / (-1 * 3483 + -9059 + 13542);
return m;
}
console.log(get_m());
边栏推荐
- Information Security Experiment 4: implementation of IP packet monitoring program
- 进程间的通信方式
- [4G/5G/6G专题基础-147]: 6G总体愿景与潜在关键技术白皮书解读-2-6G发展的宏观驱动力
- stm32和电机开发(从单机版到网络化)
- Where is the answer? action config/Interceptor/class/servlet
- 牛客网——华为题库(61~70)
- Mysql database transaction learning notes
- Jemter operation
- 创建一个长度为6的int型数组,要求数组元素的值都在1-30之间,且是随机赋值。同时,要求元素的值各不相同。
- Connecting mobile phone with ADB
猜你喜欢
Connecting mobile phone with ADB
数据建模中利用3σ剔除异常值进行数据清洗
![[cloud native] Devops (I): introduction to Devops and use of code tool](/img/e0/6152b3248ce19d0dbba3ac4845eb65.png)
[cloud native] Devops (I): introduction to Devops and use of code tool
Loxodonframework quick start
Unittest simple project
Install pyqt5 and Matplotlib module
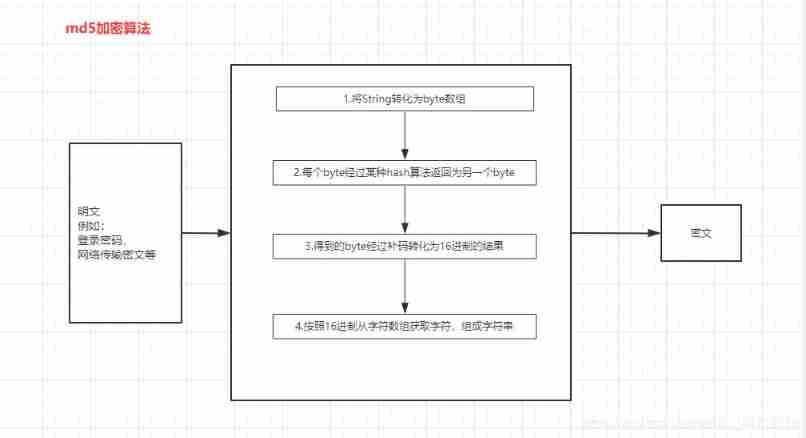
What is MD5
Huawei hcip datacom core_ 03day
Data association between two interfaces of postman
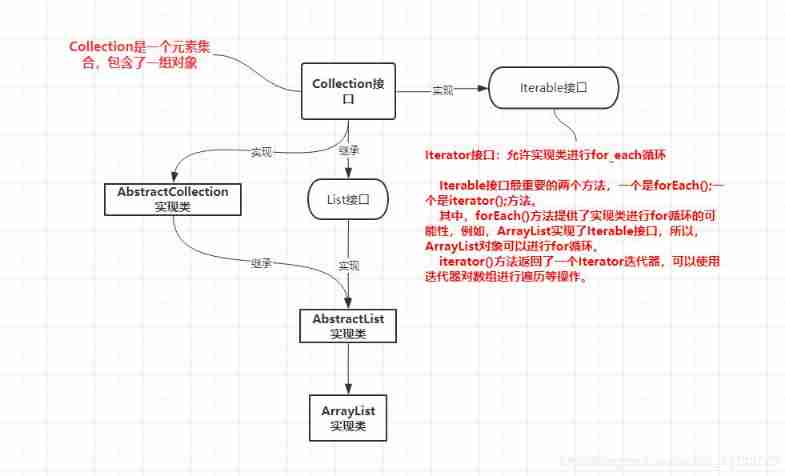
Difference between interface iterator and iteratable
随机推荐
Record of structured interview
(3/8) method parameters of improper use of enumeration (2)
Netease cloud wechat applet
Serializer & modelserializer of DRF serialization and deserialization
浏览器中如何让视频倍速播放
Data association between two interfaces of postman
Connecting mobile phone with ADB
Esp8266 uses TF card and reads and writes data (based on Arduino)
[SVN] what is SVN? How do you use it?
细说Mysql MVCC多版本控制
What is MD5
PostgreSQL创建触发器的时候报错,
Binary tree high frequency question type
第一讲:寻找矩阵的极小值
如何成为一名高级数字 IC 设计工程师(5-2)理论篇:ULP 低功耗设计技术精讲(上)
js逆向教程第二发-猿人学第一题
Interface test API case, data and interface separation
如何成为一名高级数字 IC 设计工程师(5-3)理论篇:ULP 低功耗设计技术精讲(下)
答案在哪里?action config/Interceptor/class/servlet
Redis common commands