当前位置:网站首页>What is MD5
What is MD5
2022-07-07 09:20:00 【Wow, it's a small dish】
What is? md5?
md5 Is an irreversible hash algorithm
- Irreversible : Ciphertext can be obtained from plaintext , But you can't get plaintext from ciphertext .
- hash : Get a mapping value through a function , It could be repetitive ! But the probability of repetition is relatively low , For example, set characters + Case letters + Digital password , The probability of getting the same ciphertext through hashing is very, very low .
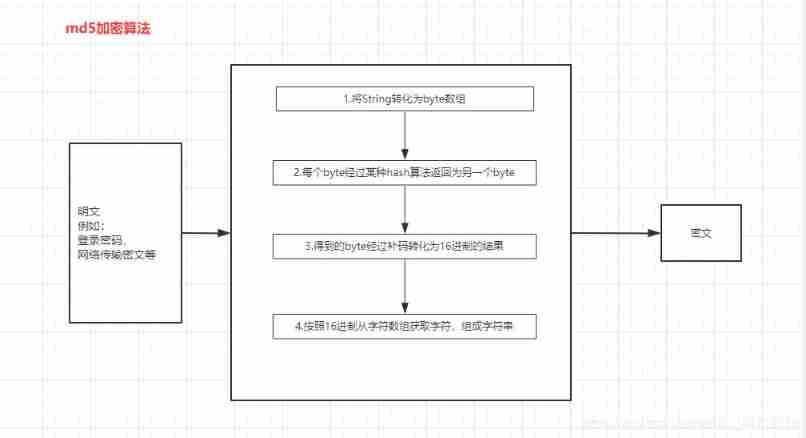
Application scenarios
Password storage :
On safety grounds , Native passwords cannot be stored directly in the database , If the data is leaked, it will cause many problems , therefore , Will pass the password md5 Encrypted and stored in the database , I'm sure you know that .Consistency check :
This is a usage I found when making payment signatures , Not used before . When the client calls the third-party payment , Need is to use http(s) Transmission request , Once the request is blocked , Be modified , For example, payment 1000 element , Intercepted as 1 element , After successful payment , The third party returns the result of successful payment , It will cause serious damage .So people use a ciphertext , Process the request parameters into a string : for example “amount=50&payMethod=native&id=012345”, Then encrypt the string , Send with the request . After receiving the request, make a consistency check with the plaintext parameters , Check the consistency of parameters .
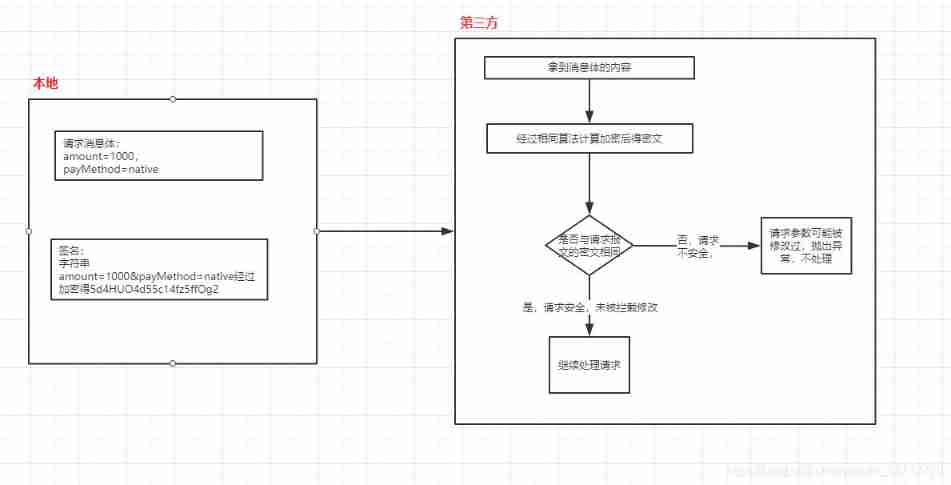
Of course , The real encryption means involving payment will be more complex , For example, certificates and so on , Using this example is just an illustration md5 It can be used as a means to verify the consistency of passwords .
How to improve security
Add salt
Salt value is a meaningless random string , It can be a paragraph uuid, It can also be a random number . Adding salt can prevent hackers from using some comparison tables to crack simple passwords ( such as 123456,password These common passwords , The frequency of use is very high , You can find ).Multiple encryption
Will be encrypted md5 Re encrypt the password , Cycle a few times , The ciphertext thus formed cannot be found through the comparison table .
边栏推荐
- Connecting mobile phone with ADB
- [SVN] what is SVN? How do you use it?
- Why is access to the external network prohibited for internal services of the company?
- Entity of cesium data visualization (Part 1)
- 嵌套(多级)childrn路由,query参数,命名路由,replace属性,路由的props配置,路由的params参数
- MySql数据库-索引-学习笔记
- C语言指针(下篇)
- Postman interface test (I. installation and use)
- Self awakening from a 30-year-old female programmer
- 外部中断实现按键实验
猜你喜欢
MySQL common statements
How to pass the PMP Exam in a short time?
Cesium load vector data

Serial port experiment - simple data sending and receiving
超十万字_超详细SSM整合实践_手动实现权限管理
C language pointer (Part 2)
2021 year end summary
Reflections on the way of enterprise IT architecture transformation (Alibaba's China Taiwan strategic thought and architecture practice)
Jmeters use
【Istio Network CRD VirtualService、Envoyfilter】
随机推荐
Interface test API case, data and interface separation
Yapi test plug-in -- cross request
Port multiplexing and re imaging
Hard core sharing: a common toolkit for hardware engineers
【Istio Network CRD VirtualService、Envoyfilter】
Mysql database lock learning notes
Leetcode question brushing record (array) combination sum, combination sum II
Interview question: general layout and wiring principles of high-speed PCB
JVM 垃圾回收 详细学习笔记(二)
Simulation volume leetcode [general] 1705 The maximum number of apples to eat
浏览器中如何让视频倍速播放
Common operating commands of Linux
JWT certification used in DRF
Unittest simple project
Postman interface test (I. installation and use)
Postman interface test (II. Set global variables \ sets)
信息安全实验四:Ip包监视程序实现
Original collection of hardware bear (updated on June 2022)
Expérience de port série - simple réception et réception de données
What are the suggestions for PMP candidates?