当前位置:网站首页>Why is access to the external network prohibited for internal services of the company?
Why is access to the external network prohibited for internal services of the company?
2022-07-07 09:01:00 【bboyzqh】
List of articles
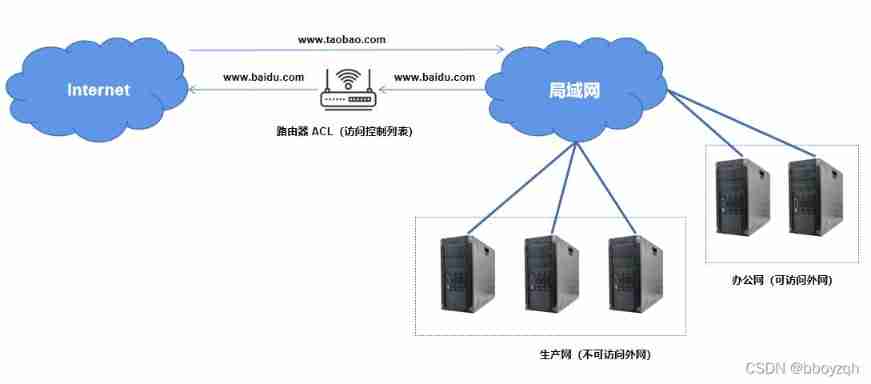
In the above figure, network access is divided into two directions :
- Internet( Extranet ) Access the company network www.taobao.com: The request will be forwarded to the company's load balancing server after routing , The load balancing server will check the request 、 Current limiting and other controls , Generally, there is no safety risk .
- Corporate LAN access Internet( Extranet )www.baidu.com: Corporate LAN access Internet( Extranet )www.baidu.com when , It will also be forwarded by route , If... Is set in the router ACL( Access control list ), Can't access , Otherwise, you can access . here ACL It can be configured separately according to the requests of different network segments in the company's LAN , For example, the production network has a high security level and cannot access the external network , And the office network can access the external network ( For example, Alibaba's internal seven network isolation ). This can not only improve network security , And easy to manage .
A brief introduction ACL,ACL( Access control list ) It's an access control technology based on packet filtering , It can filter the data packets on the interface according to the set conditions , Allow it to pass through or discard . Access control lists are widely used in routers and layer 3 switches , With access control lists , Can effectively control the user's access to the network , So as to ensure the network security to the greatest extent . Now let's introduce what is accessing the Internet 、 The risk of accessing the Internet , And what scenarios need to apply for external Internet .
What is access to the Internet ?
Accessing the Internet refers to The application server deployed in the company actively connects to the public network , For example, a server of the production network in the above figure accesses www.baidu.com.
The risk of accessing the Internet
If the internal application server of the company has the ability to actively connect to the public network, there are the following risks :
- Attackers can download malicious backdoors from the public network 、 Mining Trojan horse, etc , Then invade the internal server of the company
- Attackers can obtain internal data of the company , Thus causing data leakage
- Convenient for attackers XXE、SSRF Etc
What business scenarios need to apply for external Internet ?
Connect with external open platforms , Need to use open api Equal demand . Such as visiting Alipay open platform
Reptile demand .
Ants have had security incidents before , An internal application of ant has patrol function , Will visit the domain name provided by the user ( The domain name provided by the user is uncertain , For example, the State Council Government website ), The application has visited a large number of State Council government websites , Because all applications of ant production network share the external network outlet ip, Cause all ants to exit ip Supplement the ban on government websites , It affects the operation of a large number of core businesses of ant , It had a great impact .
…
So , By default, the application baseline does not allow access to the Internet ( Try on the server ping command , Such as ping www.baidu.com To verify ), For the above business scenarios , If you need to open Internet access , After the security assessment, the operation and maintenance department can release the restriction of accessing the external network .
Welcome to reprint , Please indicate the source ! Welcome to WeChat official account. : Fang Chen's blog
边栏推荐
- Find the original code, inverse code and complement of signed numbers [C language]
- Reflections on the way of enterprise IT architecture transformation (Alibaba's China Taiwan strategic thought and architecture practice)
- xray的简单使用
- 【ChaosBlade:根据标签删除POD、Pod 域名访问异常场景、Pod 文件系统 I/O 故障场景】
- cmake命令行使用
- Hard core sharing: a common toolkit for hardware engineers
- OpenGL 3D graphics rendering
- Digital triangle model acwing 275 Pass a note
- LeetCode 736. Lisp 语法解析
- Test pits - what test points should be paid attention to when adding fields to existing interfaces (or database tables)?
猜你喜欢
C语言指针(上篇)

Markdown editor Use of MD plug-in

硬核分享:硬件工程师常用工具包
Routing information protocol rip
![[MySQL] detailed explanation of trigger content of database advanced](/img/6c/8aad649e4ba1160db3aea857ecf4a1.png)
[MySQL] detailed explanation of trigger content of database advanced

Hard core sharing: a common toolkit for hardware engineers
C语言指针(下篇)
Screen automatically generates database documents
2022-07-06 unity core 9 - 3D animation
Unityshader introduction essentials personal summary -- Basic chapter (I)
随机推荐
RuntimeError: Calculated padded input size per channel: (1 x 1). Kernel size: (5 x 5). Kernel size c
ESP32-ULP协处理器低功耗模式RTC GPIO中断唤醒
Problems encountered in the use of go micro
Vagrant failed to mount directory mount: unknown filesystem type 'vboxsf'
Personal deduction topic classification record
Greenplum 6.x reinitialization
OpenGL帧缓冲
Chaosblade: introduction to chaos Engineering (I)
Unityshader introduction essentials personal summary -- Basic chapter (I)
C语言指针(上篇)
Three updates to build applications for different types of devices | 2022 i/o key review
xray的简单使用
数据在内存中的存储
2022-07-06 Unity核心9——3D动画
STM32的时钟系统
Implement custom memory allocator
[chaosblade: node disk filling, killing the specified process on the node, suspending the specified process on the node]
数字三角形模型 AcWing 1027. 方格取数
Redis fault handling "can't save in background: fork: cannot allocate memory“
串口实验——简单数据收发