当前位置:网站首页>Computer screen splitting method
Computer screen splitting method
2022-06-27 14:22:00 【Derived planet】
There are two simple ways to split a computer screen :
One 、 Drag the mouse to split the screen adaptively
( There is not much here )
Two 、 Split screen by shortcut key
1. Split screen
We open two pages , Then press and hold win Key and left and right direction keys for left and right split screen
win+ Left : Place the selected interface on the left ;
win+ To the right : Place the selected interface on the right .
( Be careful : It seems that the upper and lower parts cannot be operated , The specific reason is unknown , I wonder if it has anything to do with computers , Is there a big guy who can teach shortcut keys to split the screen up and down )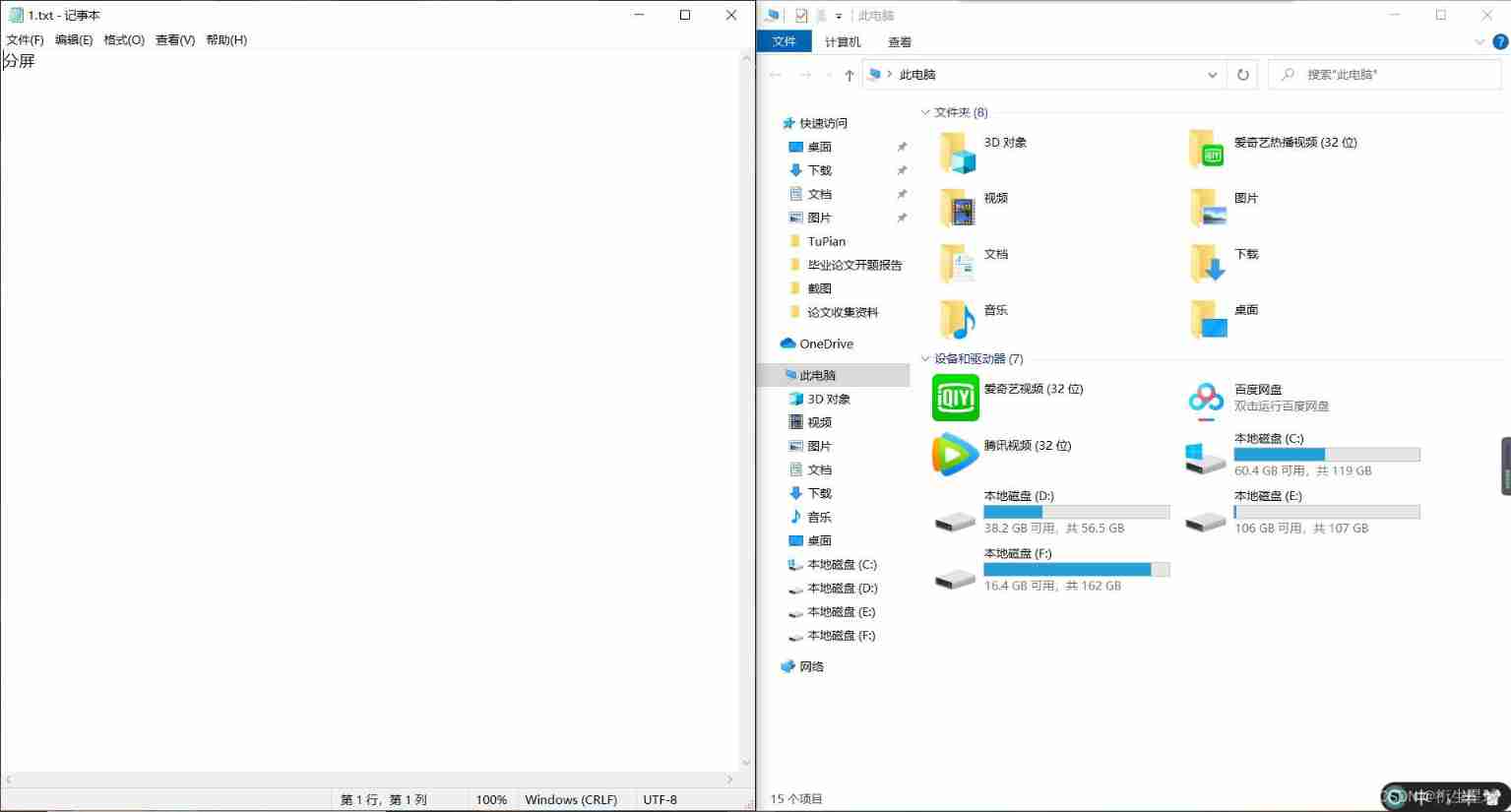
2. Quarter screen
On the basis of split screen , Perform up and down key operations :
win+ Up : Set the selected interface to the top of this side ;
win+ Down the road : Set the selected interface to the bottom of the current side ;
边栏推荐
- In the past, domestic mobile phones were arrogant in pricing and threatened that consumers would like to buy or not, but now they have plummeted by 2000 for sale
- Buuctf Misc
- Implementing springboard agent through SSH port forwarding configuration
- 阅读别人的代码,是一种怎样的体验
- Pycharm安装与设置
- 海量数据!秒级分析!Flink+Doris构建实时数仓方案
- [WUSTCTF2020]girlfriend
- Tsinghua & Shangtang & Shanghai AI & CUHK proposed Siamese image modeling, which has both linear probing and intensive prediction performance
- Redis persistence
- 以前国产手机高傲定价扬言消费者爱买不买,现在猛降两千求售
猜你喜欢

海量数据!秒级分析!Flink+Doris构建实时数仓方案

Semaphore of thread synchronization

Leetcode 724. 寻找数组的中心下标(可以,一次过)
![[PHP code injection] common injectable functions of PHP language and utilization examples of PHP code injection vulnerabilities](/img/19/9827a5e8becfc9d5bf2f51bddf803e.png)
[PHP code injection] common injectable functions of PHP language and utilization examples of PHP code injection vulnerabilities

At a time of oversupply of chips, China, the largest importer, continued to reduce imports, and the United States panicked

Practice of constructing ten billion relationship knowledge map based on Nebula graph
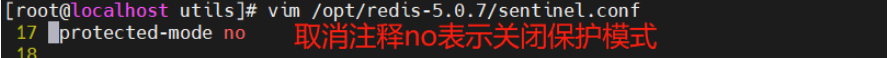
Redis 主从复制、哨兵模式、Cluster集群
![[an Xun cup 2019]attack](/img/1a/3e82a54cfcb90ebafebeaa8ee1ec01.png)
[an Xun cup 2019]attack
![[advanced MySQL] MTS master-slave synchronization principle and Practice Guide (7)](/img/d6/1b916f49ad02dee4ab2c26add324df.png)
[advanced MySQL] MTS master-slave synchronization principle and Practice Guide (7)

隱私計算FATE-離線預測
随机推荐
NLP - monocleaner
Gaode map IP positioning 2.0 backup
Pisa-Proxy 之 SQL 解析实践
机械硬盘和ssd固态硬盘的原理对比分析
Step by step expansion of variable parameters in class templates
[daily 3 questions (3)] maximum number of balls in the box
现在开户有优惠吗?网上开户是否安全么?
Axi bus
巧用redis实现点赞功能,它不比mysql香吗?
A statistical problem of shell script
Pycharm安装与设置
How ASP connects Excel
请求一下子太多了,数据库危
海外仓知识科普
enable_ if
[business security 03] password retrieval business security and interface parameter account modification examples (based on the metinfov4.0 platform)
my.ini文件配置
What if the win system cannot complete the update and is revoking the status change
[XMAN2018排位赛]通行证
[business security-04] universal user name and universal password experiment