边栏推荐
- C杂讲 双向循环链表
- 17 medical registration system_ [wechat Payment]
- Constants and pointers
- History of object recognition
- Installation of pagoda and deployment of flask project
- PyTorch RNN 实战案例_MNIST手写字体识别
- MySQL实战优化高手02 为了执行SQL语句,你知道MySQL用了什么样的架构设计吗?
- 华南技术栈CNN+Bilstm+Attention
- C杂讲 浅拷贝 与 深拷贝
- MySQL combat optimization expert 10 production experience: how to deploy visual reporting system for database monitoring system?
猜你喜欢
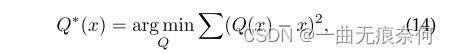
用于实时端到端文本识别的自适应Bezier曲线网络
ZABBIX introduction and installation
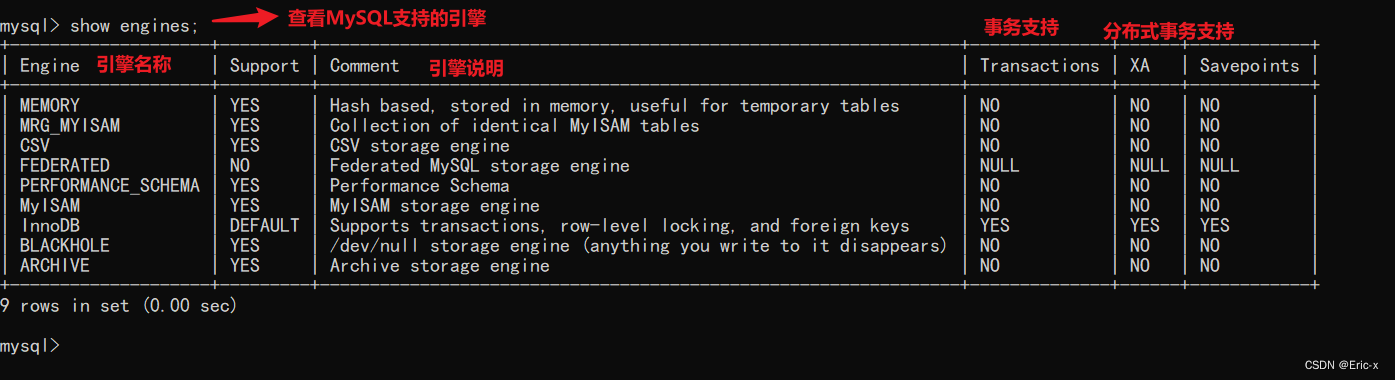
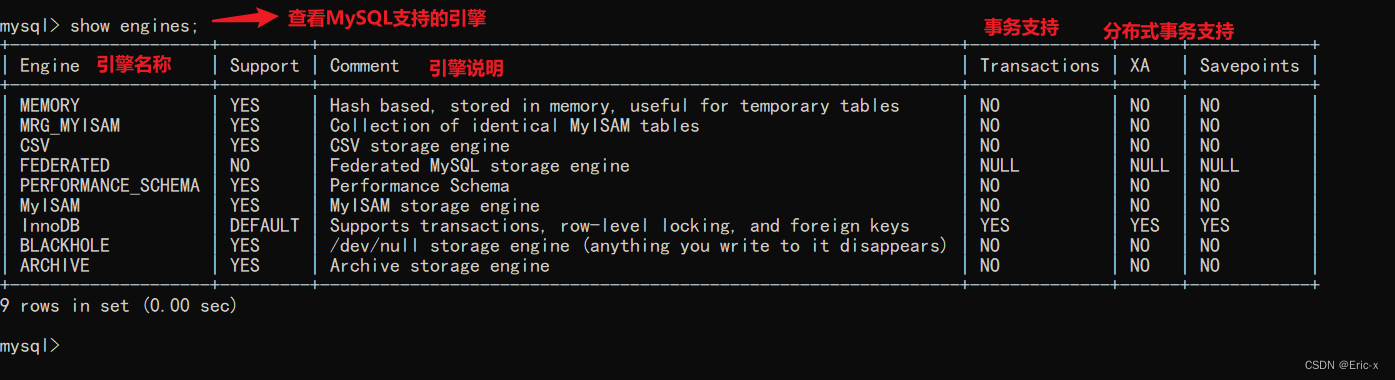
MySQL storage engine
The underlying logical architecture of MySQL
Mexican SQL manual injection vulnerability test (mongodb database) problem solution

The 32-year-old fitness coach turned to a programmer and got an offer of 760000 a year. The experience of this older coder caused heated discussion
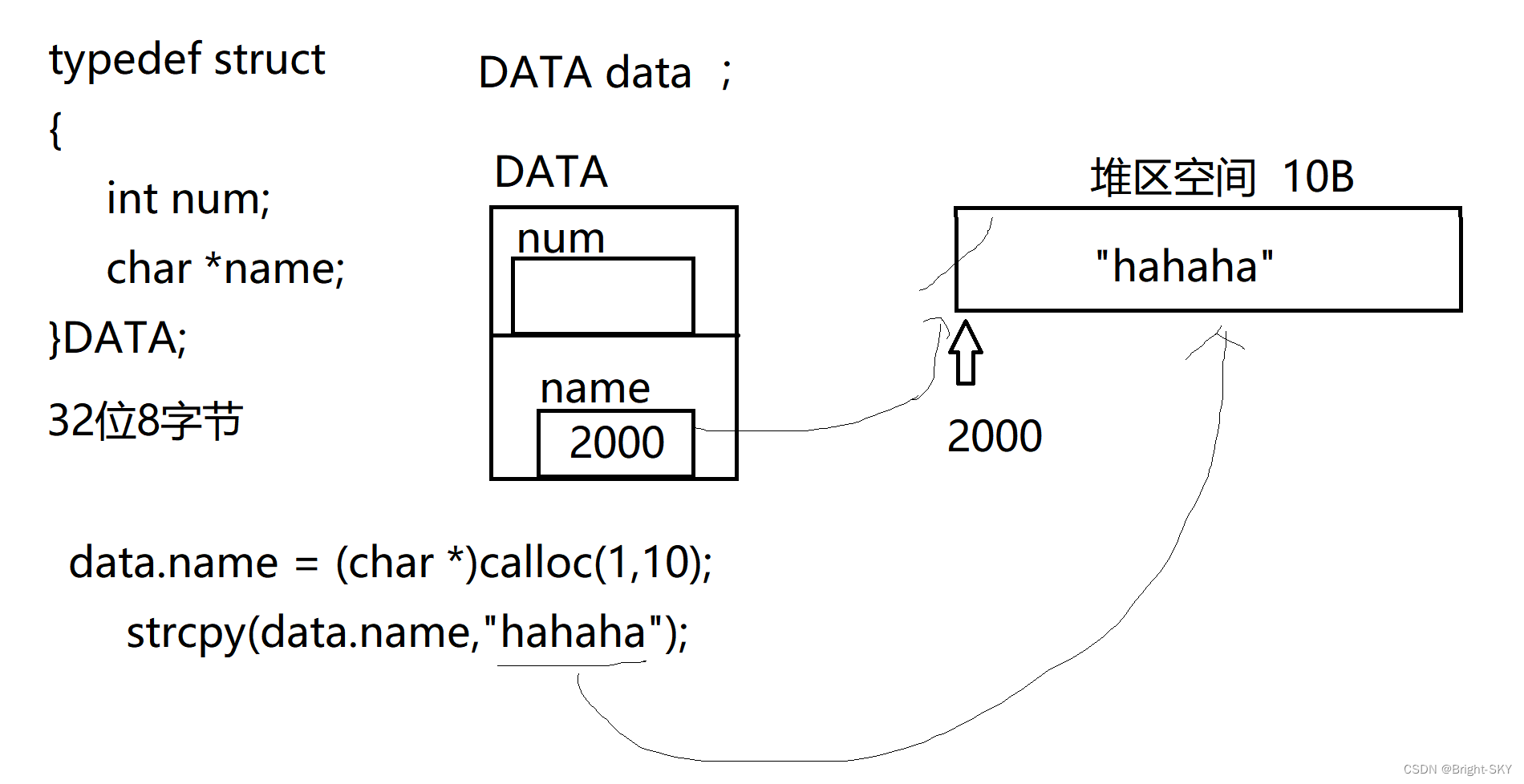
C miscellaneous shallow copy and deep copy
15 医疗挂号系统_【预约挂号】
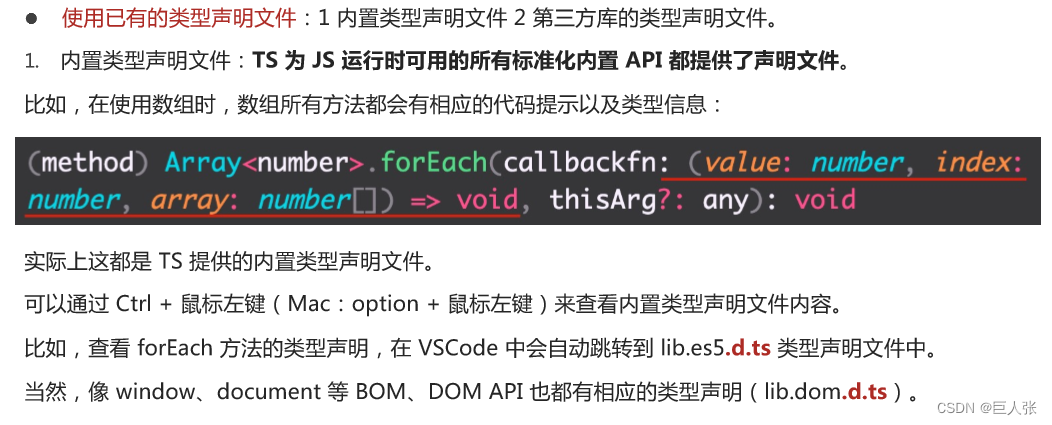
Typescript入门教程(B站黑马程序员)
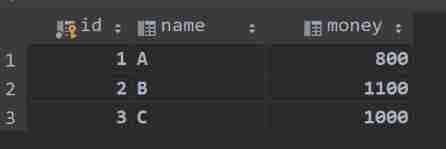
Use JUnit unit test & transaction usage
随机推荐
A new understanding of RMAN retention policy recovery window
How to make shell script executable
The underlying logical architecture of MySQL
Record the first JDBC
Target detection -- yolov2 paper intensive reading
Transactions have four characteristics?
Sed text processing
基于Pytorch的LSTM实战160万条评论情感分类
Notes of Dr. Carolyn ROS é's social networking speech
oracle sys_ Context() function
Retention policy of RMAN backup
Southwest University: Hu hang - Analysis on learning behavior and learning effect
MySQL ERROR 1040: Too many connections
Flash operation and maintenance script (running for a long time)
Time in TCP state_ The role of wait?
MySQL combat optimization expert 10 production experience: how to deploy visual reporting system for database monitoring system?
Zsh configuration file
Constants and pointers
UnicodeDecodeError: ‘utf-8‘ codec can‘t decode byte 0xd0 in position 0成功解决
What is the difference between TCP and UDP?