1. Jingtao background optimization
1.1 Path optimization
1.1.1 edit properties The configuration file

1.1.2 edit FileServiceImpl
Dynamically assign values to attributes .
2 Realize the product picture echo
2.1 Reverse proxy
The reverse proxy server is located between the user and the target server , But for users , The reverse proxy server is equivalent to the target server , In other words, users can get the resources of the target server by directly accessing the reverse proxy server . meanwhile , Users don't need to know the address of the target server , There is no need to make any settings on the client side . A reverse proxy server is usually used as Web Speed up , Use reverse proxy as Web Front end server to reduce network and server load , Improve access efficiency . [1]
characteristic :
- The reverse proxy server is located between the user and the target server
- For users , Think of a proxy server as a real server .
- The reverse proxy mechanism protects the real server information .
4. The reverse proxy is generally referred to as the server proxy .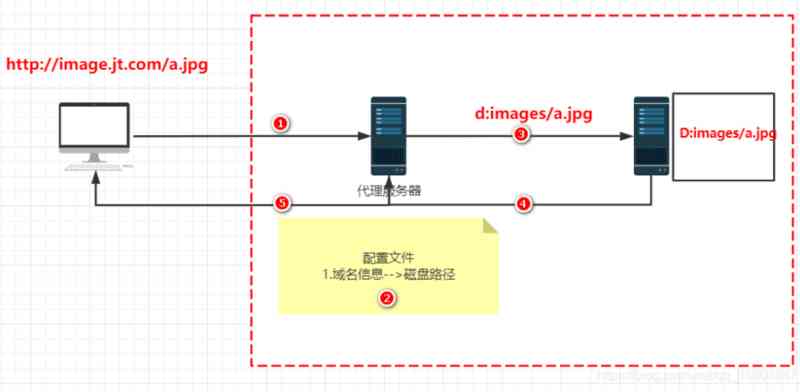
step :
1. When a user initiates a request , The request was intercepted by the proxy server .
2. The proxy server queries its own configuration file , according to url Address to get the real server information .
3. By the proxy server according to the real server information , get data .
4. After the real server receives the request , Return the data to the proxy server .
5. After the proxy server receives the server data , Send the data back to the user , This agency ends .
2.2 Forward agency
2.2.1 Forward agent States
Forward agency , It means a location between the client and the original server (origin server) Server between , To get content from the original server , The client sends a request to the agent and specifies the destination ( Original server ), The agent then forwards the request to the original server and returns the obtained content to the client . Client can use forward proxy .
characteristic :
1. The proxy server is located between the user and the real server
2. Customers know exactly who the service they are visiting ?
3. The server doesn't know who is accessing its own server , Think it's just proxy access .
4. A forward proxy is called a client proxy . Protect the customer's information 
2.3 Nginx
2.3.1 Nginx Server introduction
Nginx (engine x) Is a high-performance HTTP And reverse proxy web The server , It also provides IMAP/POP3/SMTP service .Nginx It was by igor · Mr. Seshoyev was the second most visited city in Russia Rambler.ru Site ( ru :Рамблер) Developed , The first public version 0.1.0 Published on 2004 year 10 month 4 Japan .
It takes the source code as a class BSD Release in the form of license , Because of its stability 、 Rich feature set 、 Known for sample profiles and low system resource consumption .2011 year 6 month 1 Japan ,nginx 1.0.4 Release .
Nginx It's a lightweight model Web The server / Reverse proxy server and email (IMAP/POP3) proxy server , stay BSD-like Issue under agreement . It is characterized by less memory , Strong concurrency , in fact nginx The concurrency ability of is better in the same type of web server , Used in mainland China nginx Website users have : Baidu 、 JD.COM 、 Sina 、 NetEase 、 tencent 、 Taobao, etc. .
characteristic :
1. Less memory No more than 2M
2. Strong concurrency 5 ten thousand / second tomcat 150-220 individual / second
3. development language C Language
2.3.2 Nginx download

2.3.3 nginx install
start-up : First, right-click to run as administrator , After the program flashes back, it means that the server starts normally .
2.3.4 Check Nginx Service startup item
nginx Startup time , It will start 2 Process items , One of them
1. The main process It mainly provides reverse proxy service for users Large memory consumption
2. Daemon To prevent the main process from shutting down accidentally . Small memory 
2.3.4 Start the normal test

2.4 NGINX Introduction case description
2.4.1 Profile description

2.5 NGINX Realize image echo
2.5.1 edit Nginx.conf file

2.5.2 nginx command
Catalog : stay nginx In the root directory of 
command :
2.5.3 edit hosts file
Introduce : HOSTS File is the operating system for the convenience of development , A domain name formed locally with IP The mapping file of . But the file is only valid for this machine .
Location : C:WindowsSystem32driversetchosts
The contents of the document :
2.5.4 About nginx Echo picture error description
1. Check if the configuration file is correct 
2. Check the upload path 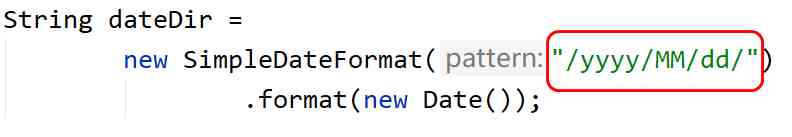
3. Check nginx Whether the configuration is normal 
4. Check nginx Whether it starts normally 
5. Check hosts Whether the document is valid If it doesn't work, restart the computer 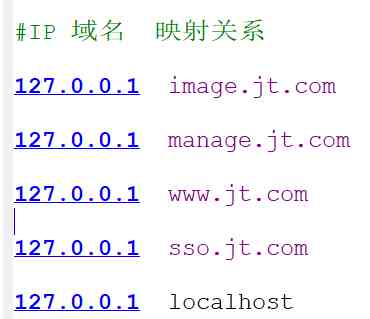
2.6 Realize the proxy of domain name
2.6.1 Business needs
demand : Need to pass through http://manage.jt.com Domain access l...:8091 Server for .
operation :
1. modify hosts file
2. modify nginx Configuration file for
2.6.2 modify nginx.conf The configuration file
modify nginx after , Just restart .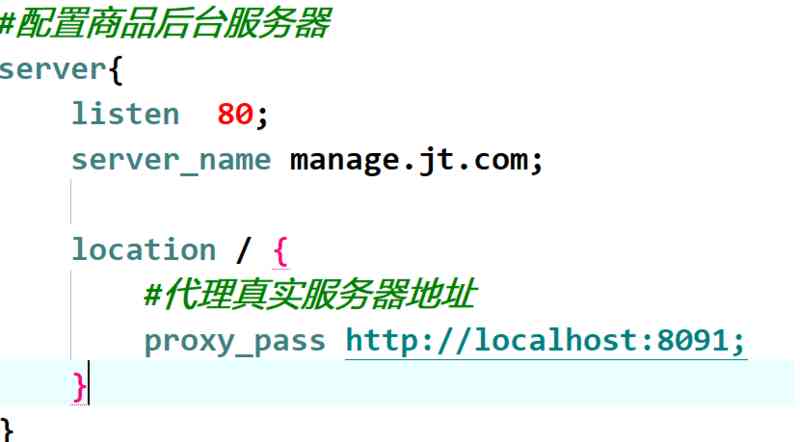
2 nginx Advanced usage
2.1 nginx Load balancing mechanism
explain : In order to improve the processing capacity of the background server , You can add servers . Strategies for load balancing .
2.2 Get the server port number dynamically .
Request path : http://manage.jt.com/getPort Get the current server port number information .
2.3 Project package
2.3.1 utilize maven Way to pack
explain : Modify the respective port number , Then package the project 
2.3.2 Use compression tools to package
take xxx.war Change it to xxx.zip Then use the compression tool to modify the configuration file , Then it was changed to xxx.war that will do 
2.3.3 Project release
command : java -jar 8081.war Will occupy a terminal window , At run time , The terminal can't be turned off .

2.3.4 Release the key combination of resources
ctrl + c
2.4 nginx Load balancing test
2.4.1 Polling strategy
explain : according to nginx.conf Access the configuration files in order 
2.4.2 Weight strategy
explain : Because the company's physical servers may have high and low performance , In order to allow high-performance servers to process more data .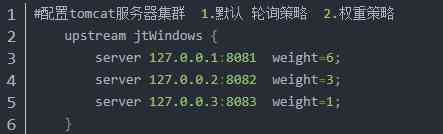
2.4.3 IPHASH Strategy
explain : If necessary The server and IP Address When Binding , Use this strategy 
principle :

![[最佳实践]了解 Eolinker 如何助力远程办公](/img/7b/e786e0d73114e6c6800747580aad2d.jpg)