当前位置:网站首页>Six stones programming: about code, there are six triumphs
Six stones programming: about code, there are six triumphs
2022-07-04 20:21:00 【Liu Kunpeng】
I am often proud of my code . Why proud ? Of course, I feel good . I feel good , In fact, it is also compared . So I thought carefully , Summed up six complacency :
- Clean up useless code
These codes ( With comments ) No one uses it , It's a waste of energy to keep it .
Someone asked , What day do I need to refer to ? Now there is version management , Just check it out .
- Standard naming
By naming , Express the meaning accurately and clearly , It's not easy . Thanks to my language and vocabulary expertise , At this point, I am far superior to others .
- alignment
Alignment code , It is the unique proposition of six stone programming . By aligning , The code becomes neat and beautiful , Feast for the eyes .
- Get rid of weird code
What is weird code ? There is no basis 、 source , There's no reason , It may be the code to solve a problem . such as : Inexplicably added a value ( Such as 0.25), Or multiply by a coefficient , Or a piece of code that deals with a particular situation .
- Merge code
I often add parameters , Merge similar code . In this way, the amount of code can be reduced , Feel a lot , Actually less than expected . The key is to avoid weird mistakes , One modification is all correct .
- Use technique
To solve the problem , The use of other people almost unexpected ( Refers to or participates in related work ) The technique of . Of course, I am very proud .
边栏推荐
- Explicit random number
- Development and construction of DFI ecological NFT mobile mining system
- C语言-入门-基础-语法-流程控制(七)
- Process of manually encrypt the mass-producing firmware and programming ESP devices
- 1002. A+b for Polynomials (25) (PAT class a)
- Lingyun going to sea | Murong Technology & Huawei cloud: creating a model of financial SaaS solutions in Africa
- Decryption function calculates "task state and lifecycle management" of asynchronous task capability
- @Data source connection pool exhaustion caused by transactional abuse
- Wireshark network packet capture
- 更强的 JsonPath 兼容性及性能测试之2022版(Snack3,Fastjson2,jayway.jsonpath)
猜你喜欢
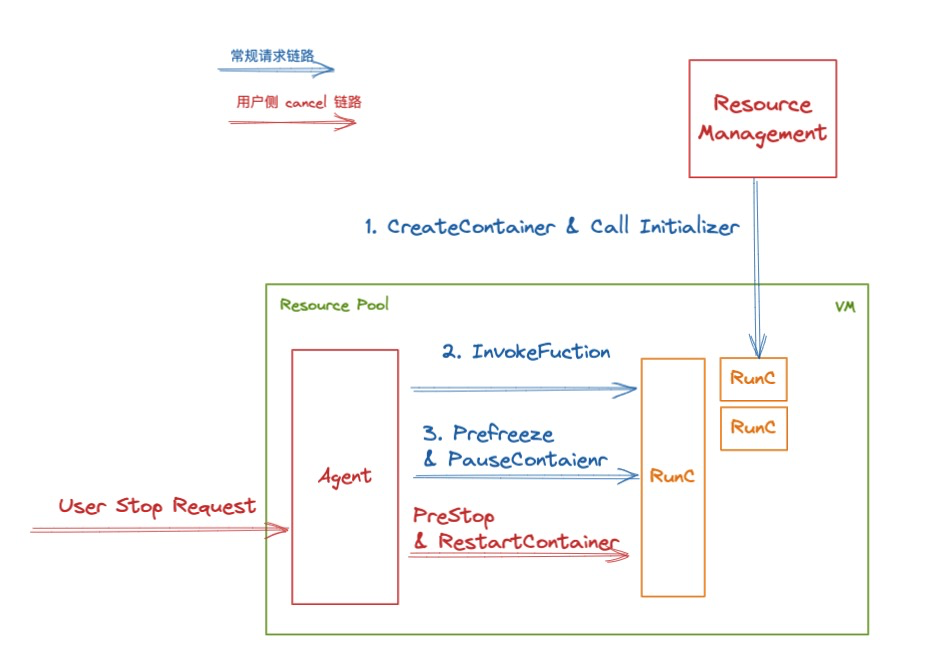
解密函数计算异步任务能力之「任务的状态及生命周期管理」

English grammar_ Noun - use

92. (cesium chapter) cesium building layering
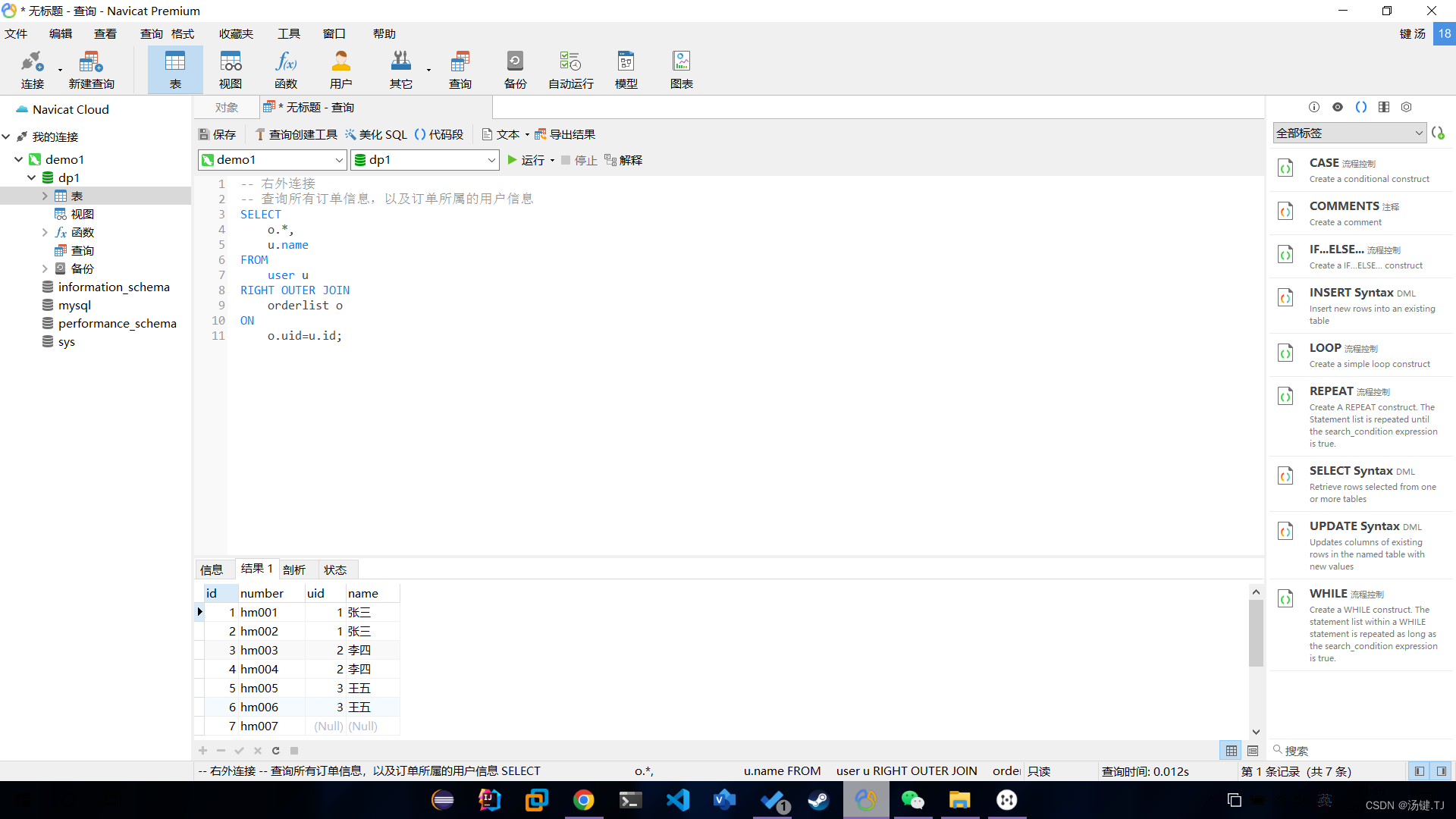
多表操作-外连接查询
![Employment prospects of neural network Internet of things application technology [welcome to add]](/img/b0/fe525a1c4788c2c377d49e6b98cf74.png)
Employment prospects of neural network Internet of things application technology [welcome to add]
Application practice | Shuhai supply chain construction of data center based on Apache Doris

做社交媒体营销应该注意些什么?Shopline卖家的成功秘笈在这里!
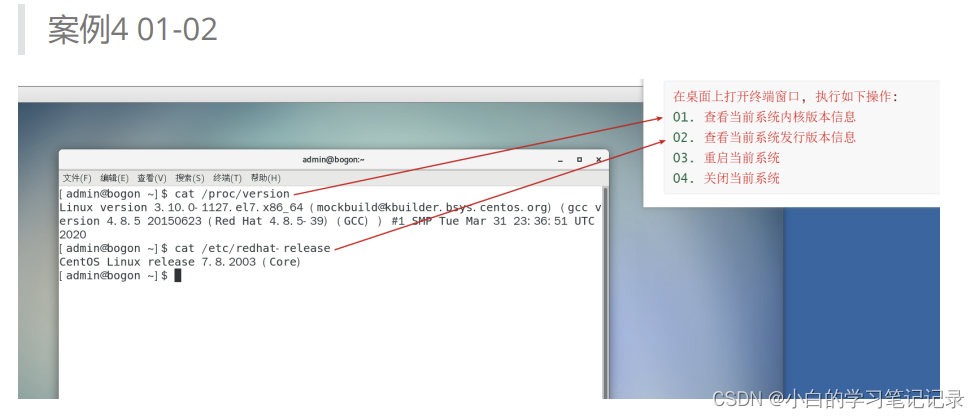
黑马程序员-软件测试--08阶段2-linux和数据库-23-30-进程端口相关,修改文件权限,端口号信息的获取,程序和进程相关操作,linux命令案例
Actual combat simulation │ JWT login authentication
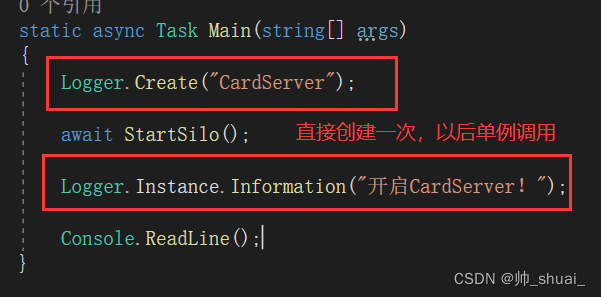
C server log module
随机推荐
六石编程学:关于代码,有六个得意
1500万员工轻松管理,云原生数据库GaussDB让HR办公更高效
92. (cesium chapter) cesium building layering
kotlin 继承
Swagger突然发癫
Development and construction of DFI ecological NFT mobile mining system
YOLOv5s-ShuffleNetV2
[problem] Druid reports exception SQL injection violation, part always true condition not allow solution
1009 product of polynomials (25 points) (PAT class a)
Siemens HMI download prompts lack of panel image solution
多表操作-内连接查询
实战模拟│JWT 登录认证
HDU 1372 & POJ 2243 Knight moves (breadth first search)
What financial products can you buy with a deposit of 100000 yuan?
Niuke Xiaobai month race 7 F question
Is it necessary to apply for code signing certificate for software client digital signature?
记一次 .NET 某工控数据采集平台 线程数 爆高分析
[QNX hypervisor 2.2 user manual]6.3.1 factory page and control page
HMM hidden Markov model and code implementation
黑马程序员-软件测试--09阶段2-linux和数据库-31-43修改文件权限字母发的说明,-查找链接修改文件,查找文件命令,链接文件,压缩解压方式,vi编辑器基本使用,