当前位置:网站首页>Understand one-way hash function
Understand one-way hash function
2022-07-03 05:39:00 【Manon stayup】

WeChat search : Code the agriculture StayUp
Home address :https://gozhuyinglong.github.io
The source code to share :https://github.com/gozhuyinglong/blog-demos

1. Definition
One way hash function (one-way hash function) It refers to different input values , Calculation by one-way hash function , Get a fixed length output value . This input value is called news (message), The output value is called Hash value (hash value).

The one-way hash function is also called Message digest function (message digest function)、 hash function perhaps Hash function . The message entered is also called The original (pre-image). The output hash value is also called A summary of the news (message digest) perhaps The fingerprint (fingerprint), Equivalent to the ID card of the message .
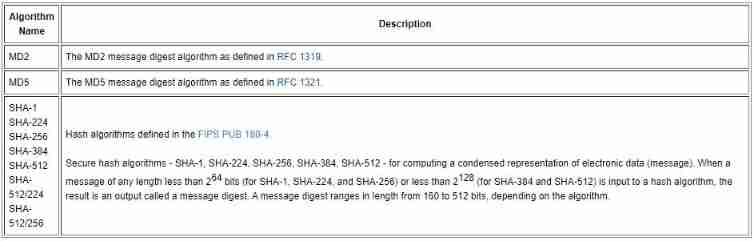
There are many algorithms for implementing one-way hash functions , Common are :MD5、SHA-1、SHA-2 and SHA-3.
2. characteristic
By the definition above , Our understanding of one-way hash functions is still vague . The following describes the characteristics of one-way hash function , Make a deep impression .
2.1 Hash value length is fixed
No matter how long the message is , The length of hash value calculated by the same algorithm is always fixed . such as MD5 Algorithm , No matter how much input , The length of the resulting hash value is always 128 The bit (16 byte ).
However, bits are units that computers can recognize , We humans are more used to using hexadecimal strings to represent ( One byte occupies two hexadecimal characters ).

2.2 Different messages have different hash values
Use the same message , The resulting hash values must be the same .
Use different messages , The resulting hash values are also different . Even if there is only one bit difference , The resulting hash value will also be very different .
This feature is also called Resistance to PengZhuangXing , For the algorithm with weak anti-collision , We should not use .

2.3 It's unidirectional
Hash values can only be calculated from messages , Cannot reverse calculate message from hash value .

2.4 Fast calculation
Computing hash values is fast . Although the longer the news , The longer it takes to calculate the hash value , But it will also be completed in a short time .
3. Common algorithms
MD5 And SHA-1 The algorithm has been broken , Should not be used for new purposes ;SHA-2 And SHA-3 It's still safe , have access to .
SHA-2 Include :SHA-224、SHA-256、SHA-384、SHA-512、SHA-512/224、SHA-512/256.
SHA-3 Include :SHA3-224、SHA3-256、SHA3-384、SHA3-512.
| The algorithm name | Hash length | Is it safe? |
|---|---|---|
| MD5 | 128 | unsafe |
| SHA-1 | 160 | unsafe |
| SHA-224 | 224 | Security |
| SHA-256 | 256 | Security |
| SHA-384 | 384 | Security |
| SHA-512 | 512 | Security |
| SHA-512/224 | 224 | Security |
| SHA-512/256 | 256 | Security |
| SHA3-224 | 224 | Security |
| SHA3-256 | 256 | Security |
| SHA3-384 | 384 | Security |
| SHA3-512 | 512 | Security |
4. Application scenarios
One way hash functions do not ensure the confidentiality of information , It is a cryptographic technology to ensure the integrity of information . Let's look at its application scenario .
4.1 User password protection
When the user sets the password , Do not record the password itself , Only record the hash value of the password , Only the user knows the plaintext of the password . When checking the password , As long as the password entered is correct , The resulting hash value must be the same , Indicates that the verification is correct .
To prevent the rainbow watch from cracking , You can also salt the password , Just verify the password , The calibration can be completed by using the same salt .

The benefits of using hash values to store passwords are : Even if the database is stolen , Nor can we deduce the ciphertext from the plaintext , Make password storage more secure .
4.2 Interface signature
In order to ensure the safety of the interface , It can be sent by signature .
The sender and receiver should have one Share secret key . When the sender sends a request to the receiver , Attach a signature to the parameter ( Signed by Share secret key + Business parameters , Generate one-way hash function encryption ). When the receiver receives it , Generate the signature in the same way , Then compare it with the received signature , If the same , Attestation successfully .
In this way, you can verify whether the business parameters have been tampered with , And verify the identity of the sender .

4.3 Document integrity verification
When a file is mounted to a web site , Its hash value and algorithm are also attached , such as Tomcat Official website .

After the user downloads , Calculate its hash value , Whether the comparison results are the same , To verify the integrity of the file .
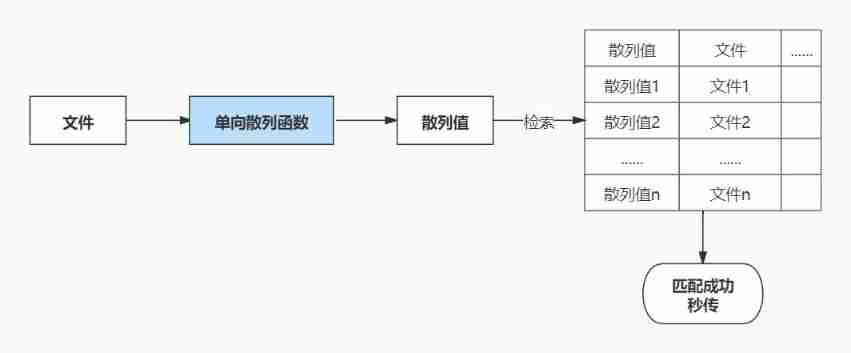
4.4 Cloud disk second transmission
When we put our favorite videos on the network disk , Found that it took only a few seconds to upload successfully , And this file has several G size , How to do it ?
Actually this “ Second transmission ” The function can be realized by using one-way hash function .
When we upload a file , The cloud disk client will first generate a hash value for the file . Take this hash value and match it in the database , If it matches , This indicates that the file already exists on the ECS . Simply associate the hash value with the user , You can complete this “ Upload ”.
such , Only one copy of a file will be saved on the ECS , It greatly saves the space of ECS .
5. Code implementation
JDK Of java.security.MessageDigest Class provides us with a message digest algorithm , be used for MD5 and SHA Hash value generation for . The following code makes a simple encapsulation , Easy to use .
public class MDUtil {
/**
* MD5 encryption
*
* @param data Data to encrypt
* @return 32 Hexadecimal string
*/
public static String MD5(byte[] data) {
try {
MessageDigest md = MessageDigest.getInstance("MD5");
byte[] bytes = md.digest(data);
return bytesToHexString(bytes);
} catch (NoSuchAlgorithmException e) {
e.printStackTrace();
}
return "";
}
/**
* MD5 encryption
*
* @param data Data to encrypt
* @return 32 Hexadecimal string
*/
public static String MD5(String data) {
return MD5(data.getBytes());
}
/**
* SHA-1 encryption
*
* @param data Data to encrypt
* @return 40 Hexadecimal string
*/
public static String SHA1(byte[] data) {
try {
MessageDigest md = MessageDigest.getInstance("SHA-1");
byte[] bytes = md.digest(data);
return bytesToHexString(bytes);
} catch (NoSuchAlgorithmException e) {
e.printStackTrace();
}
return "";
}
/**
* SHA-1 encryption
*
* @param data Data to encrypt
* @return 40 Hexadecimal string
*/
public static String SHA1(String data) {
return SHA1(data.getBytes());
}
/**
* SHA-224 encryption
*
* @param data Data to encrypt
* @return 56 Hexadecimal string
*/
public static String SHA224(byte[] data) {
try {
MessageDigest md = MessageDigest.getInstance("SHA-224");
byte[] bytes = md.digest(data);
return bytesToHexString(bytes);
} catch (NoSuchAlgorithmException e) {
e.printStackTrace();
}
return "";
}
/**
* SHA-224 encryption
*
* @param data Data to encrypt
* @return 56 Hexadecimal string
*/
public static String SHA224(String data) {
return SHA224(data.getBytes());
}
/**
* SHA-256 encryption
*
* @param data Data to encrypt
* @return 64 Hexadecimal string
*/
public static String SHA256(byte[] data) {
try {
MessageDigest md = MessageDigest.getInstance("SHA-256");
byte[] bytes = md.digest(data);
return bytesToHexString(bytes);
} catch (NoSuchAlgorithmException e) {
e.printStackTrace();
}
return "";
}
/**
* SHA-256 encryption
*
* @param data Data to encrypt
* @return 64 Hexadecimal string
*/
public static String SHA256(String data) {
return SHA256(data.getBytes());
}
/**
* SHA-384 encryption
*
* @param data Data to encrypt
* @return 96 Hexadecimal string
*/
public static String SHA384(byte[] data) {
try {
MessageDigest md = MessageDigest.getInstance("SHA-384");
byte[] bytes = md.digest(data);
return bytesToHexString(bytes);
} catch (NoSuchAlgorithmException e) {
e.printStackTrace();
}
return "";
}
/**
* SHA-384 encryption
*
* @param data Data to encrypt
* @return 96 Hexadecimal string
*/
public static String SHA384(String data) {
return SHA384(data.getBytes());
}
/**
* SHA-512 encryption
*
* @param data Data to encrypt
* @return 128 Hexadecimal string
*/
public static String SHA512(byte[] data) {
try {
MessageDigest md = MessageDigest.getInstance("SHA-512");
byte[] bytes = md.digest(data);
return bytesToHexString(bytes);
} catch (NoSuchAlgorithmException e) {
e.printStackTrace();
}
return "";
}
/**
* SHA-512 encryption
*
* @param data Data to encrypt
* @return 128 Hexadecimal string
*/
public static String SHA512(String data) {
return SHA512(data.getBytes());
}
/**
* Convert byte array to hexadecimal string
*
* @param bytes Byte array
* @return Hexadecimal string
*/
private static String bytesToHexString(byte[] bytes) {
StringBuilder hexValue = new StringBuilder();
for (byte b : bytes) {
int val = b & 0xFF;
if (val < 16) {
hexValue.append("0");
}
hexValue.append(Integer.toHexString(val));
}
return hexValue.toString();
}
}
These algorithms are used to calculate “123456” Hash value :
public static void main(String[] args) {
System.out.println("MD5\t\t" + MDUtil.MD5("123456"));
System.out.println("SHA-1\t" + MDUtil.SHA1("123456"));
System.out.println("SHA-224\t" + MDUtil.SHA224("123456"));
System.out.println("SHA-256\t" + MDUtil.SHA256("123456"));
System.out.println("SHA-384\t" + MDUtil.SHA384("123456"));
System.out.println("SHA-512\t" + MDUtil.SHA512("123456"));
}
Output results :
MD5 e10adc3949ba59abbe56e057f20f883e
SHA-1 7c4a8d09ca3762af61e59520943dc26494f8941b
SHA-224 f8cdb04495ded47615258f9dc6a3f4707fd2405434fefc3cbf4ef4e6
SHA-256 8d969eef6ecad3c29a3a629280e686cf0c3f5d5a86aff3ca12020c923adc6c92
SHA-384 0a989ebc4a77b56a6e2bb7b19d995d185ce44090c13e2984b7ecc6d446d4b61ea9991b76a4c2f04b1b4d244841449454
SHA-512 ba3253876aed6bc22d4a6ff53d8406c6ad864195ed144ab5c87621b6c233b548baeae6956df346ec8c17f5ea10f35ee3cbc514797ed7ddd3145464e2a0bab413
I use it Java8, Not yet SHA-3, So the above code only encapsulates MD5、SHA-1 and SHA-2.
from Java9 Start supporting SHA-3

6. Complete code
Please visit my Github, If it helps you , Welcome to a Star, thank you !
7. Recommended reading
边栏推荐
- [written examination question analysis] | | get [sizeof and strlen] [pointer and array] graphic explanation + code analysis
- Map的扩容机制
- Final review (Day6)
- How to set up altaro offsite server for replication
- Altaro set grandfather parent child (GFS) archiving
- [Shangshui Shuo series together] day 10
- 2022.7.2day594
- Deploy crawl detection network using tensorrt (I)
- 期末复习DAY8
- 6.23 warehouse operation on Thursday
猜你喜欢

【一起上水硕系列】Day 10
![Together, Shangshui Shuo series] day 9](/img/39/c1ba1bac82b0ed110f36423263ffd0.png)
Together, Shangshui Shuo series] day 9

Common interview questions of microservice
![[written examination question analysis] | | get [sizeof and strlen] [pointer and array] graphic explanation + code analysis](/img/c6/8847218fa43c87e3eb51c021961eb7.jpg)
[written examination question analysis] | | get [sizeof and strlen] [pointer and array] graphic explanation + code analysis

Webrtc protocol introduction -- an article to understand ice, stun, NAT, turn

中职网络子网划分例题解析
How to use source insight
Gan network thought
![[set theory] relational closure (reflexive closure | symmetric closure | transitive closure)](/img/c8/2995c503e9dabae4e2cc704449e04f.jpg)
[set theory] relational closure (reflexive closure | symmetric closure | transitive closure)
(perfect solution) how to set the position of Matplotlib legend freely
随机推荐
Basic introduction of redis and explanation of eight types and transactions
Progressive multi grasp detection using grasp path for rgbd images
6.23星期四库作业
[set theory] relational closure (relational closure related theorem)
今天很多 CTO 都是被干掉的,因为他没有成就业务
[together Shangshui Shuo series] day 7 content +day8
Final review (Day7)
How to set up altaro offsite server for replication
(subplots usage) Matplotlib how to draw multiple subgraphs (axis field)
Get and monitor remote server logs
Analysis of the example of network subnet division in secondary vocational school
PHP笔记超详细!!!
Final review (Day2)
ninja: build stopped: subcommand failed.
MySQL startup error: several solutions to the server quit without updating PID file
2022.6.30DAY591
NG Textarea-auto-resize
EMD distance - example of use
[untitled]
Calculation method of AUC