当前位置:网站首页>Vulnerability discovery - API interface service vulnerability probe type utilization and repair
Vulnerability discovery - API interface service vulnerability probe type utilization and repair
2022-06-26 06:26:00 【Dark white earphone】

Test ideas
Information collection and information utilization
First step : First, identify whether the website has cdn,waf Products such as , If there is, it will be bypassed .
The second step : Scan the port information collected from the website , real ip Address ,ip Bound other domain names .
The third step : Website sensitive path scanning
Step four : domain name + Port sensitive information scanning
Step five :ip+ Port sensitive directory scanning
remarks : Dictionaries should not be just sensitive paths , There should also be backup files zip rar tar tar.gz Etc
Port service class security test
According to the previous information collected for the target port service class probe after the security test , It's mainly about attack methods : password security ,WEB
Class vulnerability , Version vulnerability, etc , The harm can be great or small . Belongs to port service / Third party service security testing surface . Generally in
The security test scheme selected in the case of known applications without ideas .
API Interface -WebServiceRESTful API
https://xz.aliyun.com/t/2412
According to the functional direction of the application itself , The safety test objectives need to have API Interface calls can be used for such tests , Mainly involved in safety
The whole question : Self safety , coordination WEB, Business logic, etc , The harm can be great or small , Belongs to the application API Interface network service
Service test surface , Generally, it is also a test scheme in the case of interface call .
WSDL( Network service description language ,Web Services Description Language) It's based on XML Language , Used to describe
Web Services And how to access them .
Vulnerability keywords :
coordination shodan,fofa,zoomeye Search is also good ~
inurl:jws?wsdl
inurl:asmx?wsdl
inurl:aspx?wsdl
inurl:ascx?wsdl
inurl:ashx?wsdl
inurl:dll?wsdl
inurl:exe?wsdl
inurl:php?wsdl
inurl:pl?wsdl
inurl:?wsdl
filetype:wsdl wsdl
http://testaspnet.vulnweb.com/acuservice/service.asmx?WSDL

Domain information collection
1. Subdomain collection  2. Search the other party's domain name through the domain name registration platform , View the registered domain name related to the target domain name ( These domain names have different suffixes , But usually the same person registers )
2. Search the other party's domain name through the domain name registration platform , View the registered domain name related to the target domain name ( These domain names have different suffixes , But usually the same person registers ) 3. Search the keyword of the target website through the browser
3. Search the keyword of the target website through the browser
4. Domain name access and IP visit , The directory may be different : When collecting, you should not only scan the directory under the domain name , You have to scan ip Under address .
When collecting, you should not only scan the directory under the domain name , You have to scan ip Under address .
Goby Port scanning ( give an example )
Find out 4848 port . It can also be used. Nmap.
Baidu's corresponding service vulnerabilities 
Super weak password detection tool
https://github.com/shack2/SNETCracker/releases
WSDL
WSDL( Network service description language ,Web Services Description Language) It's based on XML Language , Used to describe Web Services And how to access them .( Mainly used for interface )
API The interface test
https://xz.aliyun.com/t/2412
AWVS scanning
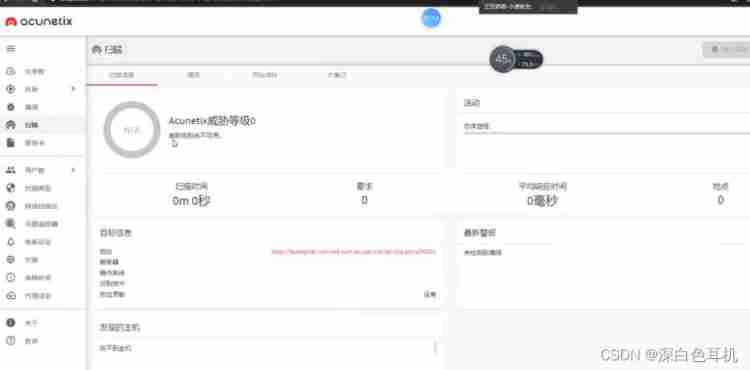 The scanned results exist SQL Inject holes
The scanned results exist SQL Inject holes 
Copy the packet , stay sqlmap The installation directory , Create a new document  Copy the packet into .
Copy the packet into .
But pay attention to awvs The test statement of is deleted . Write any parameter here , Add after *, tell sqlmap To test here
Write any parameter here , Add after *, tell sqlmap To test here 
sqlmap To test 
Inject success 
边栏推荐
- typescript的class结合接口(interface)的简单使用
- Underlying principle of MySQL index
- Logstash——使用throttle过滤器向钉钉发送预警消息
- typescript的type
- 宝塔服务器搭建及数据库远程连接
- Work accumulation - problems encountered in using ThreadLocal in web requests
- Dpdk - tcp/udp protocol stack server implementation (II)
- 数据可视化实战:数据可视化
- Logstash -- send an alert message to the nail using the throttle filter
- Simple use of enum type in TS
猜你喜欢

Transformer中的Self-Attention以及Multi-Head Self-Attention(MSA)

Keepalived to achieve high service availability

技术能力的思考和总结

Connexion et déconnexion TCP, détails du diagramme de migration de l'état

Evolution history of qunar Bi platform construction

Tencent's 2022 school recruitment of large factories started with salary, and the general contracting of cabbage is close to 40W!

Zotero文献管理工具之Jasminum(茉莉花)插件
C# Nuget离线缓存包安装

EFK昇級到ClickHouse的日志存儲實戰
vs code 使用 prettier 格式化 js 的时候, 函数定义的名称和括号之间有一个空格, 而 eslit 又不允许这个空格.
随机推荐
3.pyinstaller模块介绍
Pytorch mixing accuracy principle and how to start this method
LightGBM--调参笔记
Pychart cannot run designer Exe (this application failed to start because no Qt platform plugin could be I appears)
Comparison between Prometheus and ZABBIX
ts中枚举类型(enum)简单使用
Requirement analysis of personal blog system
Load balancer does not have available server for client: userService问题解决
Container with the most water
Go language learning notes 1.2- variables
Install pyinstaller
Go learning notes 1.3- data types of variables
Play with a variety of application scenarios and share secrets with Kwai MMU
How to make the main thread wait for the sub thread to execute before executing
Handwritten background management framework template (I)
How can an enterprise successfully complete cloud migration?
Logstash——使用throttle过滤器向钉钉发送预警消息
How to select and build a real-time data warehouse scheme
Go language learning notes 1.1
Custom reference formats used by Zotero