当前位置:网站首页>Trends in DDoS Attacks
Trends in DDoS Attacks
2022-07-06 02:31:00 【zy18165754120】
The first thing to notice is , Although hacker activism made headlines , But according to Neustar That's what I'm saying ,DDoS The main motive behind the attack is not :“ Most attacks still come from other sources , That is, blackmailers 、 Cruel competitors and other for-profit attackers ...... Those who aim at your bottom line —— In the form of ransom notes threatening your website or competitors competing for market share —— Still launching most of the overall attacks .”
One problem is that attack technology is becoming more and more complex , At the same time, it is cheap and easy to use . Medium sized companies are unlikely to have the extensive security defenses of large companies . A successful attack may cost such companies 150,000 dollar , But every day just 67 You can hire botnets as an attack tool for us dollars . Extortion and attacking competitors have economic significance .
Another problem is that medium-sized companies will rely heavily on traditional security defense , Like firewalls and IDS/IPS equipment . but Neustar Pointed out that , Firewall becomes DDoS Part of the attack problem .“ They may soon become bottlenecks , Help attackers slow down or shut down your goals ...... stay DDoS During the attack , Firewalls shut down faster than the servers they protect .”
The attack itself becomes smaller and smaller , But more and more frequent and advanced . Although old-fashioned flood attacks are still popular , But concentrated attacks designed to overwhelm processors rather than just block access are increasing . It is called high packet per second (PPS) attack ,“ When it tries to handle the lightning war of requests , The absolute number of packets may make your CPU collapse .” And it's not just for traditional websites and DNS. Encrypted traffic ( Because by definition , It may be of value to the victim ), And the less defensible part of the Internet infrastructure , E.g. e-mail server 、API、SNMP Wait for the default configuration , even to the extent that VoIP Could be attacked .“ Imagine , Because the Internet connection is crowded , No telephone service ,”Neustar say .“ Or because the customer cannot connect to your API And lose sales .”
Last , Two danger signs for the future . First , Whether the defense can handle IPv6 Traffic ?“ If acceptance is slow ,IPv6 It is certain to achieve stability , Therefore, it is wise to ensure your DDoS Solution ( and DNS) It's ready .” Just because mobile infrastructure is not used much , Doesn't mean it won't .“ you 're right ,”Neustar say ,“ You can launch from most smartphones or tablets DDoS attack . The bottom line : Mobile devices are starting to amplify the threat .”
边栏推荐
- Thinking on Architecture Design (under continuous updating)
- Ue4- how to make a simple TPS role (II) - realize the basic movement of the role
- 【coppeliasim】高效传送带
- The ECU of 21 Audi q5l 45tfsi brushes is upgraded to master special adjustment, and the horsepower is safely and stably increased to 305 horsepower
- [robot library] awesome robots Libraries
- HttpRunnerManager安装(三)-Linux下配置myql数据库&初始化数据
- 技术管理进阶——什么是管理者之体力、脑力、心力
- 【无标题】数据库中一条查询SQL执行的过程
- [Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 16
- 一个复制也能玩出花来
猜你喜欢
Use the list component to realize the drop-down list and address list
![[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 13](/img/29/49da279efed22706545929157788f0.jpg)
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 13
![[robot library] awesome robots Libraries](/img/72/d3e46a820796a48b458cd2d0a18f8f.png)
[robot library] awesome robots Libraries

【机器人库】 awesome-robotics-libraries
UE4 - how to make a simple TPS role (I) - create a basic role
![[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 11](/img/6a/398d9cceecdd9d7c9c4613d8b5ca27.jpg)
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 11
2022 edition illustrated network pdf
ReferenceError: primordials is not defined错误解决
![[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 16](/img/c3/f3746b161012acc3751b2bd0b8f663.jpg)
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 16
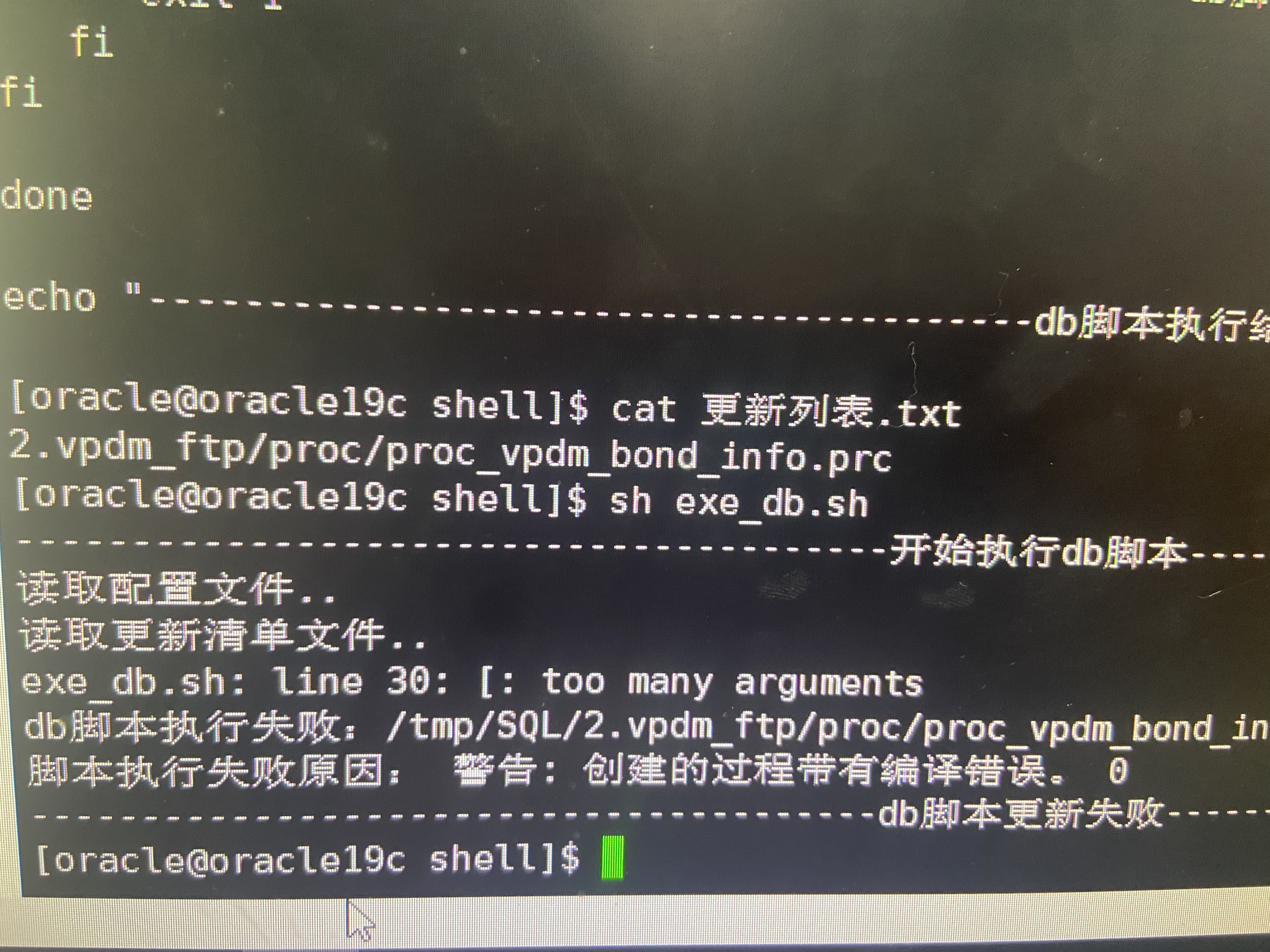
Shell script updates stored procedure to database
随机推荐
Adapter-a technology of adaptive pre training continuous learning
MySQL learning notes - subquery exercise
LeetCode 103. Binary tree zigzag level order transverse - Binary Tree Series Question 5
技术管理进阶——什么是管理者之体力、脑力、心力
Multi function event recorder of the 5th National Games of the Blue Bridge Cup
Redis delete policy
Advanced technology management - what is the physical, mental and mental strength of managers
ReferenceError: primordials is not defined错误解决
Multiple solutions to one problem, asp Net core application startup initialization n schemes [Part 1]
SQL table name is passed as a parameter
[Digital IC manual tearing code] Verilog asynchronous reset synchronous release | topic | principle | design | simulation
MySQL winter vacation self-study 2022 11 (7)
Structural theme model (I) STM package workflow
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 23
高数_向量代数_单位向量_向量与坐标轴的夹角
Minecraft 1.16.5 生化8 模组 2.0版本 故事书+更多枪械
Global and Chinese markets of screw rotor pumps 2022-2028: Research Report on technology, participants, trends, market size and share
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 19
一题多解,ASP.NET Core应用启动初始化的N种方案[上篇]
零基础自学STM32-野火——GPIO复习篇——使用绝对地址操作GPIO