当前位置:网站首页>The programmer resigned and was sentenced to 10 months for deleting the code. JD came home and said that it took 30000 to restore the database. Netizen: This is really a revenge
The programmer resigned and was sentenced to 10 months for deleting the code. JD came home and said that it took 30000 to restore the database. Netizen: This is really a revenge
2022-07-03 04:48:00 【Python_ leopard】
The programmer “ Delete the library and run away ” The topic of is on the hot search again , More than 100 million views .
however , This time, the database is not deleted , But myself Code written by yourself !
The client is a 29 Year old programmer , Developed for JD home platform 3 Month code .
The day of leaving , He deleted a series of codes written by himself , Including platform coupons 、 Budget system and subsidy rules .
Take a closer look. , The programmer's departure time happens to be 6 month 18 Japan On the day of jd.com promotion .

In recent days, , The programmer was sentenced to imprisonment ten months .
In addition to these dramatic details , Many onlookers also expressed concern about the extreme behavior when leaving 、 Code permission management and other topics are discussed .
Private login control platform delete code
According to the criminal judgment of Shanghai Yangpu District People's court ,2021 year 3 month ,29 A - year-old programmer joined an information technology Co., Ltd. in Beijing , Responsible for the code research and development of JD home platform .
2021 year 6 month 18 Japan , Record a resignation .
On the day of leaving , He has no permission , Log in to the code control platform with your own account ( The server is located in Shanghai ), Send the coupons of jd.com home platform that you wrote during your employment 、 Codes such as budget system and subsidy rules Delete , As a result, relevant projects were forced to postpone .
2021 year 9 month 23 Japan , Lu was caught by the police .
After the incident , In order to ensure the smooth operation of the system , Hire a third-party company to restore the database The total expenditure is about 3 Ten thousand yuan .
And with the help of his family members , compensate for 3.5 Ten thousand yuan and get understanding .
The verdict shows , The defendant recorded a violation of state regulations , Delete the data stored in the computer information system , The consequences are serious , His behavior has constituted Crime of destroying computer information system .
However, after recording someone to the case, he truthfully confessed his crime and voluntarily pleaded guilty , A lighter punishment can be given according to law .
at present , Lu was sentenced to fixed-term imprisonment ten months , The sentence starts with 2021 year 9 month 23 From to 2022 year 7 month 22 Japan .
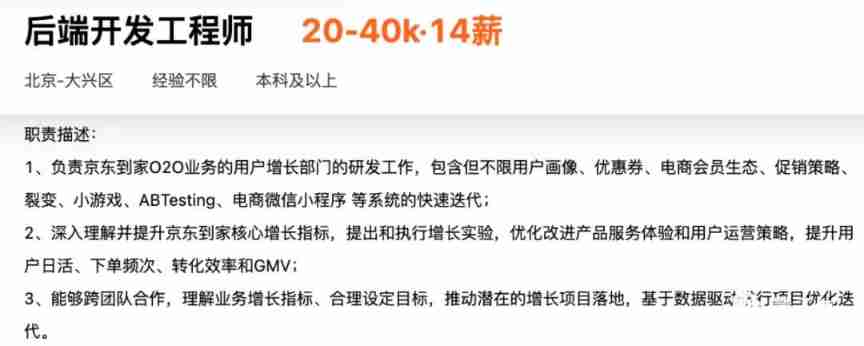
According to the enterprise investigation , Shanghai Jingdong jiayuanxin Information Technology Co., Ltd. does have a wholly-owned subsidiary in Beijing , Its name is Beijing Daguan Information Technology Co., Ltd .

You can see from Liepin , This company is recruiting JD home's back-end development engineers , Responsible for fast iteration of coupon and other systems .
This case has also triggered a lot of heated discussion among netizens .
Hot discussion among netizens : There are still doubts
It can be seen that , Compared with the previous database deletion and running , This case is somewhat different .
What the defendant recorded was not the production data in the database , It's the code you write during your work .
I understand IT Netizens in the industry found problems from the details , I think there are still some unclear explanations based on the existing information .
such as , What code is deleted .
If it is the code of the production environment , Reasonably speaking, large companies will have strict management methods for code launching , It needs to be reviewed by the same level and superior before it can be merged into the main branch .
Why does this person have so much authority to record someone ?
If it is the code of the development environment , An important function of the code control platform is version management , Whether it's Git It's still a little older SVN Have backup function , You can rollback the deletion .
So why does the company spend 3 Ten thousand yuan, please ask a third party to recover the data ?

in any case , This case reminds you again , The labor achievements during the work period belong to the company according to the contract .
Even the code written by yourself cannot be deleted on impulse , Otherwise, it will only make life more and more critical .
10 Months in prison plus compensation , Leaving a record will have an impact on finding a job in the future , It's not worth .

in addition , There is also an account in the judgment , The defendant can truthfully confess his crime after recording someone in the case , Compensate the victims and obtain understanding , A lighter punishment can be given according to law .
10 Six months in prison , Compared with similar cases that caused a sensation before , It's really light .
Say, say, make, make , Criminal law is no joke
Delete the library and run away , In the early years, it was more a joke of the programmer circle .
The joke is that after deleting the database due to operational errors and other reasons, you can only run away .
Every time “rm -rf /*” As soon as this mysterious code appears , Old drivers will smile .

But in recent years , The same story as this kind of story , It often happens in reality .
The most influential , is 2020 E-commerce at the beginning of the year SaaS Micro League programmers delete libraries , Cause the company's server to fail for as long as 8 God , exceed 300 Merchants were affected , The market value evaporated in just one day 10 $ .

The defendant he in this case finally committed the crime of destroying computer information system , Sentenced to fixed-term imprisonment 6 year .
After this , And then there is 40 Year old chain home program delete their own 9TB The database was judged 7 year , It is also the crime of destroying computer information system .
Crime of destroying computer information system , It is stipulated in Article 286 of our criminal law , Including three crimes .
The first paragraph is about the regulation of destroying the system itself .
Violation of state regulations , Delete the function of computer information system 、 modify 、 increase 、 interfere , Causes the computer information system to be unable to operate normally , With serious consequences , He shall be sentenced to fixed-term imprisonment of not more than five years or criminal detention ; Especially serious , Sentenced to more than five years' imprisonment .
The second paragraph is for data .
Violation of state regulations , Storage in computer information system 、 Delete data and applications processed or transferred 、 modify 、 Added operations , With serious consequences , Punishment in accordance with the provisions of the preceding paragraph .
The last one is destructive programs such as viruses .
Make deliberately 、 Spread computer viruses and other destructive programs , Affect the normal operation of the computer system , With serious consequences , To punish according to the first paragraph .
Besides deleting the code 、 Except for cases such as database deletion , Recently, a developer, Zhang Mou, and his gang were sentenced for remotely punching cards on nails, which also attracted a lot of attention .
Daniel assistant developed by Zhang APP It can destroy the function of the nailing system to obtain the user's real geographical location , And it's paid software , Monthly subscription 25 element , Baonian 89 element .
As of the crime, there are 10 Million users , Benefit about Five million yuan .
The court ruled that Zhang's behavior was in line with the crime of destroying computer information systems “ Make deliberately 、 Spread computer viruses and other destructive programs ”, And the consequences are serious , The First Instance sentenced him to fixed-term imprisonment 5 year 6 Months .
The court of second instance held that “ Daniel's assistant ” Not in criminal law “ destructive program ”, But Zhang still constitutes the crime of destroying computer information system , Change the sentence to fixed-term imprisonment Four years .
in addition , Develop with Daniel's assistant “ plugin ” Similar game plug-ins , You will also get the crime of destroying computer information system .
last year 12 End of month , The defendant Zhou 、 Mr. Sun 、 Yao provided 《 Protogod 》 Game plug-in profit 199.488 Ten thousand yuan , Sentenced separately 4 year 、3 year 10 Months 、1 year 6 Months .
These examples can be seen , Destroy the computer information system , The consequences are quite serious .
As the netizen said , Don't be impulsive , Take the ridicule seriously .

About Python Technology reserve
Learn from good examples Python Whether it's employment or sideline, it's good to make money , But learn to Python Still have a learning plan . Finally, let's share a complete set of Python Learning materials , For those who want to learn Python Let's have a little help !
One 、Python Learning routes in all directions
Python All directions are Python Sort out the common technical points , Form a summary of knowledge points in various fields , The use of it is , You can find the corresponding learning resources according to the above knowledge points , Make sure you learn more comprehensively .
Two 、 Learning software
If a worker wants to do a good job, he must sharpen his tools first . Study Python Common development software is here , It saves you a lot of time .

3、 ... and 、 Getting started video
When we were watching videos to learn , You can't just move your eyes and brain without hands , A more scientific way to learn is to use them after understanding , At this time, the hand training program is very suitable .
Four 、 Practical cases
Optical theory is useless , Learn to knock together , Do it , Can you apply what you have learned to practice , At this time, we can make some practical cases to learn .
5、 ... and 、 Interview information
We learn Python Must be to find a well paid job , The following interview questions are from Ali 、 tencent 、 The latest interview materials of big Internet companies such as byte , And the leader Ali gave an authoritative answer , After brushing this set of interview materials, I believe everyone can find a satisfactory job .
This full version of Python A full set of learning materials has been uploaded CSDN, Friends can scan the bottom of wechat if necessary CSDN The official two-dimensional code is free 【 Guarantee 100% free 】

边栏推荐
- Contents of welder (primary) examination and welder (primary) examination in 2022
- Market status and development prospect prediction of global colorimetric cup cover industry in 2022
- 普通本科大学生活避坑指南
- Youdao cloud notes
- The reason why the entity class in the database is changed into hump naming
- Introduction to JVM principle
- Symbol of array element product of leetcode simple problem
- Market status and development prospects of the global automatic tea picker industry in 2022
- GFS distributed file system (it's nice to meet it alone)
- Current market situation and development prospect forecast of the global fire boots industry in 2022
猜你喜欢
Internationalization and localization, dark mode and dark mode in compose

Php+mysql registration landing page development complete code
2022 new examination questions for the main principals of hazardous chemical business units and examination skills for the main principals of hazardous chemical business units

Preparation for school and professional cognition

带有注意力RPN和多关系检测器的小样本目标检测网络(提供源码和数据及下载)...
Uipath practice (08) - selector

Leetcode simple question: check whether two string arrays are equal

After job hopping at the end of the year, I interviewed more than 30 companies in two weeks and finally landed
The programmer went to bed at 12 o'clock in the middle of the night, and the leader angrily scolded: go to bed so early, you are very good at keeping fit
Why should programmers learn microservice architecture if they want to enter a large factory?
随机推荐
有道云笔记
Market status and development prospect prediction of the global forward fluorescent microscope industry in 2022
Library management system based on SSM
Shell script Basics - basic grammar knowledge
消息队列(MQ)介绍
雇佣收银员(差分约束)
【PHP漏洞-弱类型】基础知识、php弱相等、报错绕过
Career planning of counter attacking College Students
Learn to use the idea breakpoint debugging tool
Priv-app permission异常
Introduction to message queuing (MQ)
2022 Shandong Province safety officer C certificate examination content and Shandong Province safety officer C certificate examination questions and analysis
The least operation of leetcode simple problem makes the array increment
[SQL injection point] location and judgment of the injection point
Leetcode simple question: check whether the array is sorted and rotated
Kingbasees plug-in KDB of Jincang database_ exists_ expand
7. Integrated learning
Reptile exercise 03
[BMZCTF-pwn] 18-RCTF-2017-Recho
Market status and development prospect prediction of the global fire alarm sensor industry in 2022