当前位置:网站首页>So this is the BGP agreement
So this is the BGP agreement
2022-07-04 20:22:00 【Programmer cxuan】
See for the last article Ten thousand words long text burst liver routing protocol !
We talked above RIP 、OSPF Agreements are based on AS That is, the agreement within the autonomous system , They can be considered as intra domain routing protocols ; Now we are going to talk about AS The agreement between , This is also called Inter domain routing protocol , Or external gateway protocol , One of its most famous agreements is BGP agreement , At present, the most used protocol version is BGP The fourth version of BGP - 4, Referred to as BGP ( Border Gateway Protocol ).
stay RIP and OSPF Among these agreements , By IP Network address for routing control , and BGP The protocol requires routing control through the entire Internet , The scope is much larger .
BGP The environment and RIP、OSPF The environment is different , The main reason is that the scale of the Internet is too large , It makes the routing between autonomous systems more difficult . The router on the Internet is right for any IP The address can find its destination network through the routing table . This is a very large collection , If link state protocol is used RIP and OSPF Words , You must maintain a very large set of routes , On the one hand, the efficiency of routing table retrieval is very low , And such a huge data item is not easy to maintain . Another point is for each router metric Dissimilarity , It's possible that this metric It's through 100 Routes , And that link arrives 100 A route may directly report an error .
And the routing between autonomous systems must consider the policy problem , These strategies need to put politics 、 regional 、 Safety or economic considerations .
Due to the existence of these special circumstances ,BGP The protocol is just to choose a better route to the destination network , Instead of choosing the best route ,BGP Adopted Path vector routing protocol , It is associated with RIP and OSPF There's a big difference .
stay BGP Agreement , Every AS There are many within the autonomous system BGP Border router , This BGP The border router is quite a spokesman within the autonomous system . Different AS Between BGP If the border router wants to exchange routing information , You need to establish TCP Connect , And then switch on this connection BGP Message to establish BGP conversation , adopt TCP Able to provide reliable service . Two exchange messages BGP Border routers are called each other's temporary stations ( The angel ) Or peer station .
The following figure is a use BGP Border router and AS Diagram of the relationship :

BGP The network accessibility information exchanged is a series of routes to reach a certain network . When each BGP Once the border router exchanges reachability information , You will choose one to reach each AS Better routing path .
BGP Support classless inter domain routing CIDR, therefore BGP The routing table of should also include the current destination network prefix 、 Next hop router , And what it takes to reach the destination network AS .
stay BGP Just running ,BGP The next stop is to exchange the whole BGP Routing table , In the future, just update the part with new changes when changes occur . This will save network bandwidth and reduce router overhead , This feature and OSPF Very similar .
BGP - 4 There are mainly the following types of messages :
- OPEN ( open ) message , Used with adjacent BGP Area boundary routers establish relationships , Perform communication initialization .
- UPDATE ( to update ) message , Used to announce routing information , And list multiple routes that need to be updated .
- KEEPALIVE ( Keep alive ) message , It is used to periodically verify the connectivity of adjacent stations .
- NOTIFICATION ( notice ) message , Used to send detected errors .
If two adjacent stations belong to two different autonomous systems , And when one of the temporary stations plans to exchange routes with other temporary stations , At this time, there should be a process of route negotiation . The negotiation process includes whether the temporary router can also accept additional routing information . Therefore, you should send it first when you start the negotiation OPEN message , If the temporary station can accept this relationship , Just use KEEPALIVE Message response . After response , Two temporary stations are even established .
After the relationship is established , We need to maintain each other , This is after establishing the relationship with the couple , As masters, you can't ignore others for three days or two ? As the saying goes , Feelings need to be maintained , Then this routing relationship also needs to be maintained . Each of the two communicating parties needs to be sure whether the other party already exists , So two BGP Border routers need to be switched regularly KEEPALIVE message , Generally, this regular time is 30 s.
BGP Border routers can use UPDATE Message to update the route : Including removing previously notified routes and adding new routes . You can undo multiple routes at a time , But add a new route UPDATE Only one message can be added .
Of course. BGP Does not exist in the “ Good news spreads fast, bad news spreads slowly ” The problem of ( Feeling RIP The problem of was played out ). because BGP There is not only one border router , And when a router or link fails , because BGP The border router can obtain routing information from more than one adjacent station , So it's easy to choose a new route .
Here is BGP The message format of :

The four message types introduced above have common message headers , The first one is 19 byte , The general header is mainly divided into three fields .
- Mark marker Field is 16 Byte length , Used to identify received BGP message , If you don't use authentication , The marking field should be set to all 1.
- The length field indicates the entire length, including the generic header BGP The length of the message , In bytes , The minimum is 19, The maximum is 4096.
- The value of the type field is 1 To 4, Corresponding to the introduction sequence of the above messages .
OPEN There are 6 A field , As shown in the following picture

The first three fields are BGP General message header , The following fields are Version edition ( 1 byte , The value is 4 ), My AS This autonomous system number ( 2 byte , It is the only one in the world 16 Bit system number ) , Hold Time Retention time ( 2 byte , The time in seconds to maintain the relationship as a temporary station ),BGP Identifier BGP identifier ( 4 byte , The router IP Address ), Here are optional lengths and optional parameters .
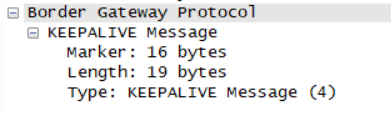
KEEPALIVE Message only BGP 19 General header of bytes .
UPDATE The message has five fields , As shown in the figure below

In the message Unfeasible routes length Indicates infeasible route length , There is a field message behind that is not listed , Namely Withdrawn Routes , List of routes to undo , hinder Total Path Attribute Length Indicates the total length of path attributes , hinder Path attributes It means path attribute , final NLRI Identify the network that sent this message .
NOTIFICATION The message has three fields , As shown in the figure below

Mainly including error codes ( 1 byte ), Error subcode ( 1 byte ) , There are error data behind .
Link to the original text :6 Minutes to watch BGP agreement .
边栏推荐
- Informatics Olympiad 1336: [example 3-1] find roots and children
- 更强的 JsonPath 兼容性及性能测试之2022版(Snack3,Fastjson2,jayway.jsonpath)
- Template_ Judging prime_ Square root / six prime method
- 2022 Health Exhibition, Beijing Health Expo, China Health Exhibition, great health exhibition November 13
- What is the application technology of neural network and Internet of things
- 1005 spell it right (20 points) (pat a)
- Introduction to ACM combination counting
- Offset function and windowing function
- How is the entered query SQL statement executed?
- Multi table operation inner join query
猜你喜欢

C语言-入门-基础-语法-流程控制(七)
实战模拟│JWT 登录认证
![[Beijing Xunwei] i.mx6ull development board porting Debian file system](/img/46/abceaebd8fec2370beec958849de18.jpg)
[Beijing Xunwei] i.mx6ull development board porting Debian file system
c# . Net MVC uses Baidu ueditor rich text box to upload files (pictures, videos, etc.)
Chrome development tool: what the hell is vmxxx file
![[problem] Druid reports exception SQL injection violation, part always true condition not allow solution](/img/cc/160bc8ccdc378901510c1b61c3f5d3.png)
[problem] Druid reports exception SQL injection violation, part always true condition not allow solution

Creation of JVM family objects
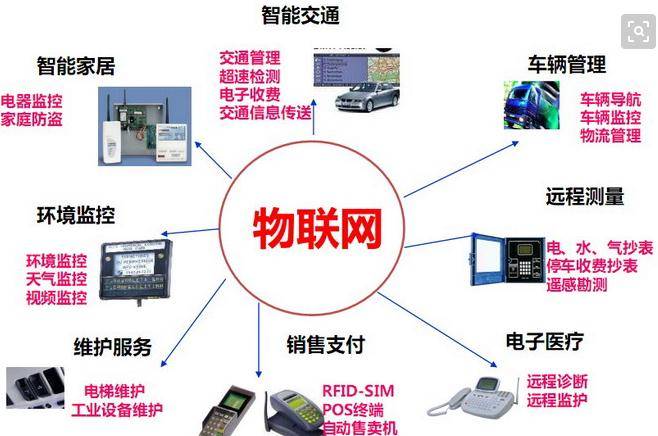
Employment prospects and current situation of Internet of things application technology

What are the consequences of closing the read / write channel?
TCP两次挥手,你见过吗?那四次握手呢?
随机推荐
Pythagorean number law (any three numbers can meet the conditions of Pythagorean theorem)
凌云出海记 | 一零跃动&华为云:共助非洲普惠金融服务
做社交媒体营销应该注意些什么?Shopline卖家的成功秘笈在这里!
PHP pseudo original API docking method
How is the entered query SQL statement executed?
C # better operation mongodb database
The company needs to be monitored. How do ZABBIX and Prometheus choose? That's the right choice!
BCG 使用之新建向导效果
[graduation season] green ant new fermented grains wine, red mud small stove. If it snows late, can you drink a cup?
水晶光电:长安深蓝SL03的AR-HUD产品由公司供应
Template_ Judging prime_ Square root / six prime method
1006 sign in and sign out (25 points) (PAT class a)
Multi table operation - external connection query
Niuke Xiaobai month race 7 who is the divine Archer
Abc229 summary (connected component count of the longest continuous character graph in the interval)
华为云云商店首页 Banner 资源位申请
Write it down once Net analysis of thread burst height of an industrial control data acquisition platform
Dark horse programmer - software testing - stage 08 2-linux and database-23-30-process port related, modify file permissions, obtain port number information, program and process related operations, Li
c# .net mvc 使用百度Ueditor富文本框上传文件(图片,视频等)
Free soldier