当前位置:网站首页>IP packet header analysis and static routing
IP packet header analysis and static routing
2022-07-05 13:54:00 【Cwxh0125】
IP Baotou analysis
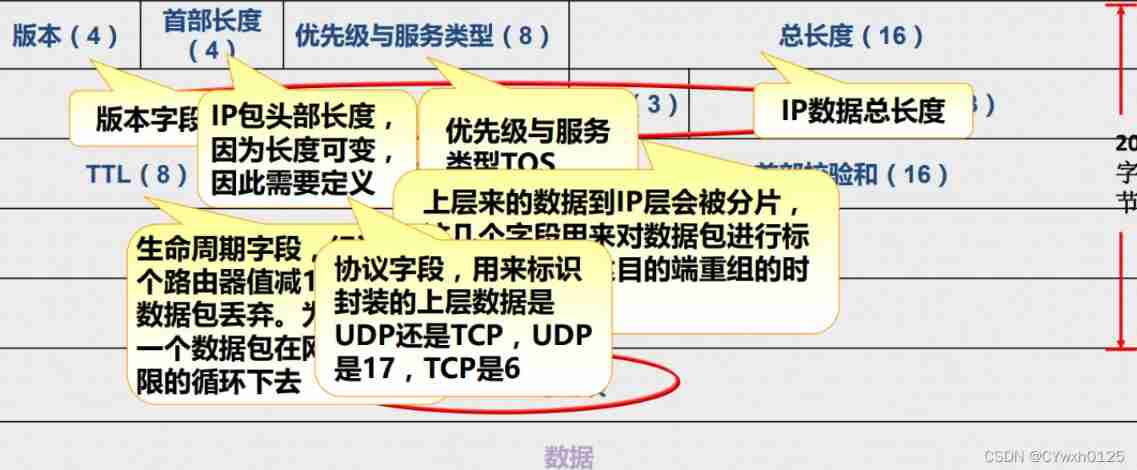
IP Number of header bytes (20-60) It's usually 20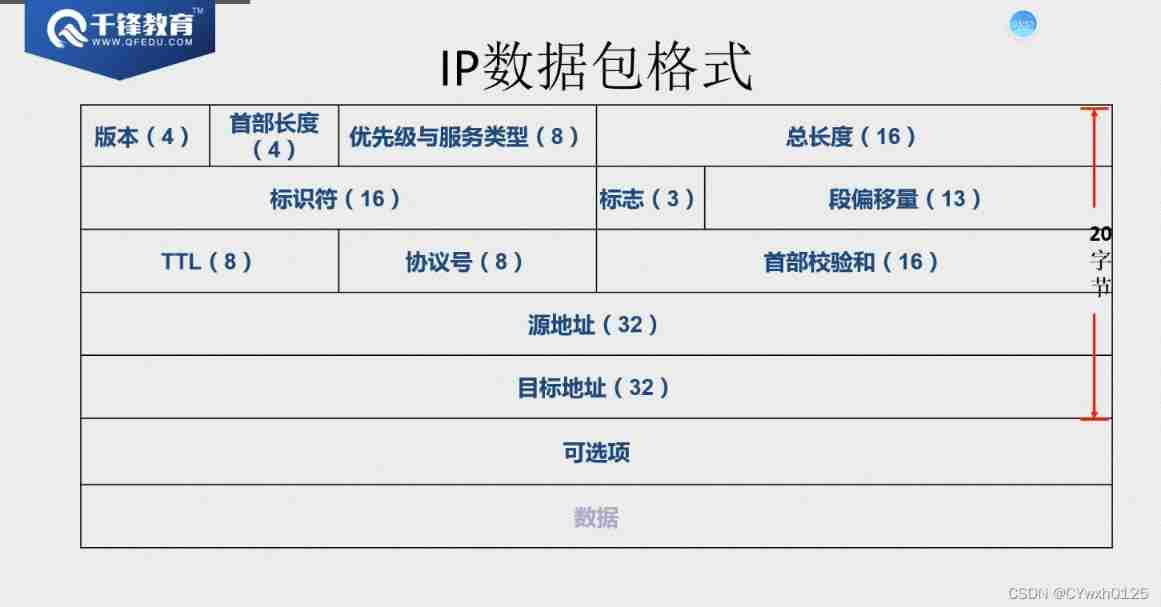
edition : Declare this ip Baotou is ipv4 still ipv6
The length of the first : identification IP baotou The length of How many bytes
Priority and service type : Not commonly used , When using differentiated services , This field only works
Total length : Whole IP package ( message ) The length of
identifier : The data from the upper layer arrives IP layer ( The network layer ) Will be sliced , Each segment is the same byte , And it will produce a ID It is used to identify that these pieces belong to the same ip package , Used for classification and segmentation , After segmentation, all data grams can be reinstalled correctly
The following figure 1 2 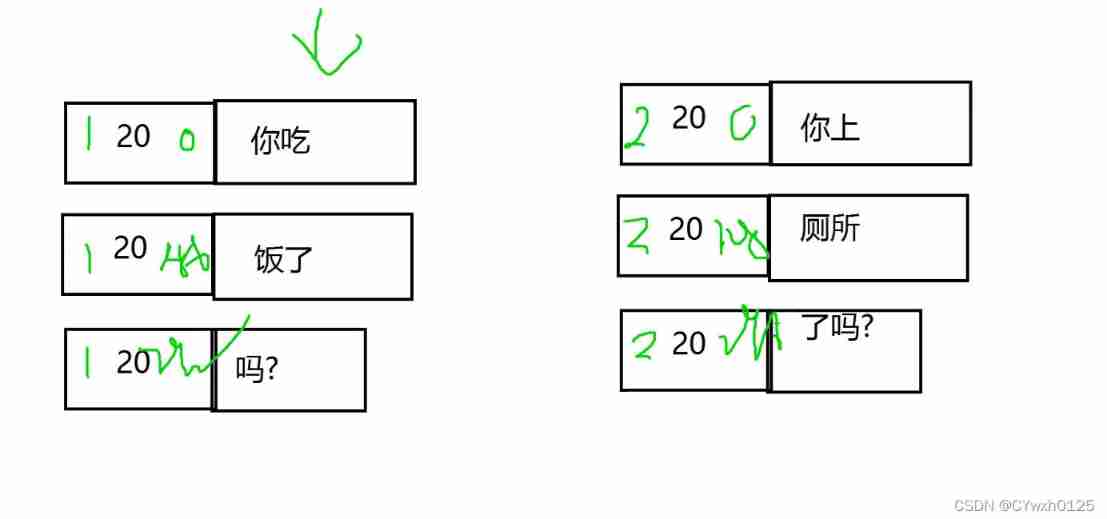
sign : There are three The first bit is not enabled For ever 0 Second 1 It means not divided 0 It's for fragmentation The last one said Is this segment the last segment If 1 Represents not the last fragment Such as 001 It stands for segmentation And there are subsequent slices
In the picture above 0 1480 2960 Segment bias
TTL: Time to live , Every time you go through a router, it's going to decrease 1,TTL Reduced to 0, Packets will be discarded ,TTL The function of value is to prevent packets from permanently circulating on the network , commonly TTL value 100 Here is Linux System ,100 The above is windows System
Agreement No : Identify the upper layer protocol , The encapsulated data used to identify the upper layer is UDP still TCP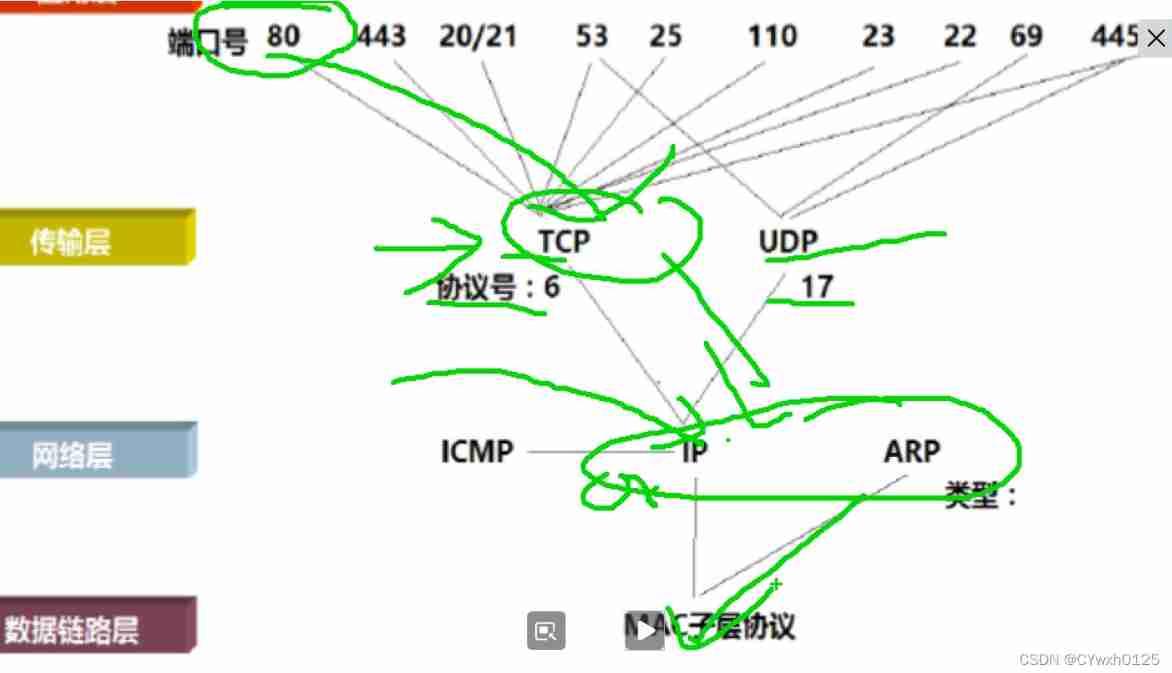
Head check sum : Verify the three layers IP baotou
Teardrop attack is to target i The computer sending is damaged ip The package is then identified by the computer , sign , Slice offset , The computer crashed due to the failure of the reorganization
Firewall on ip The packet is forbidden to pass in pieces, and only 010 adopt , Then the network layer at the sending end will not be responsible for fragmentation , Instead, the software at the application layer splits the data and sends it , In order to achieve the purpose of no partition
route
route : Router is IP The process of Baotou selecting the path ( Select by routing table )
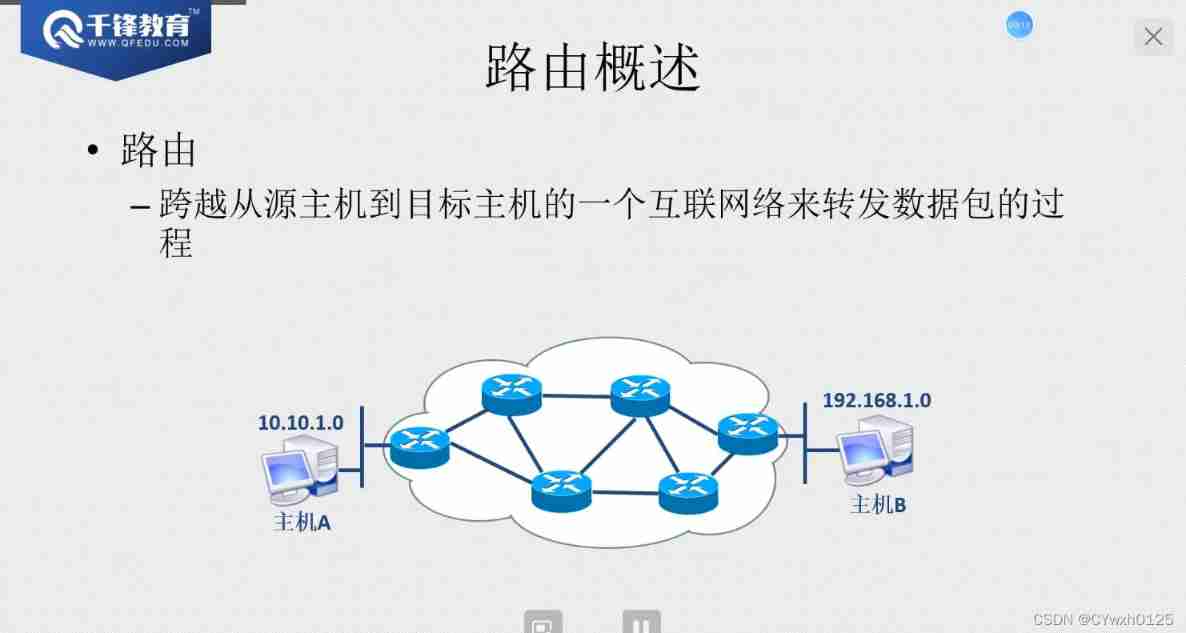
Routing table
- A collection of routing entries maintained in a router
- The router chooses the route according to the routing table
The formation of routing table
- Direct connection network segment
To configure IP Address , port UP state , Form a direct route - Non direct network segment
The following figure shows the routing tables of the two routers 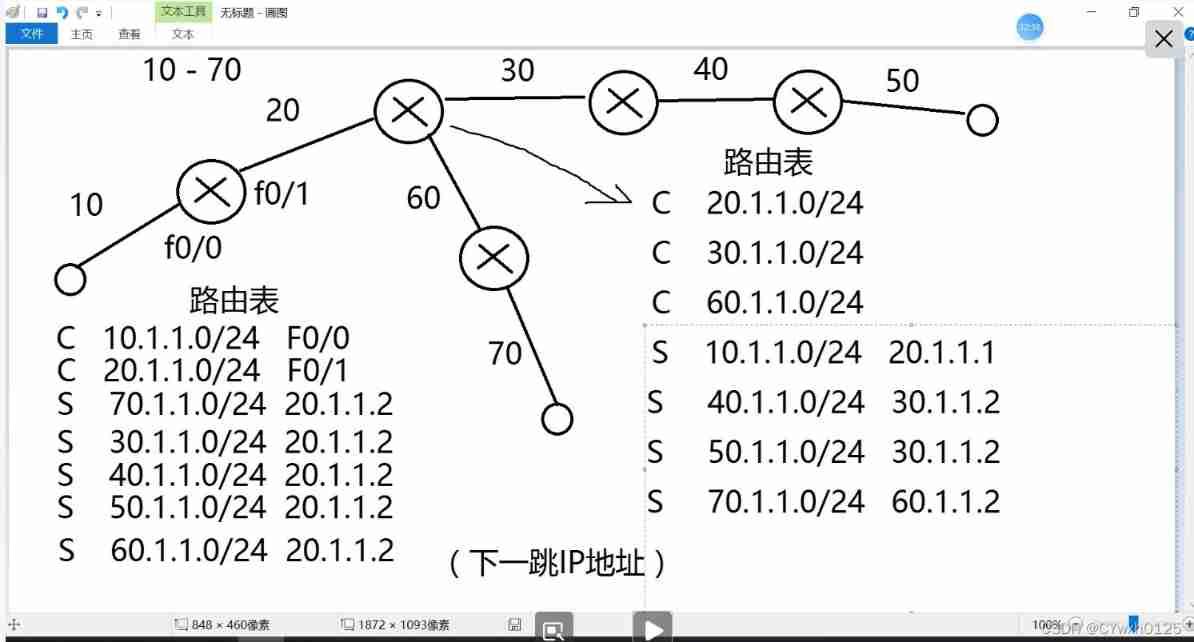
c Representative direct connection s It's static
Optimize routing tables Use default routing s*0.0.0.0/0 When the router cannot find the routing entry of the target network in the routing table , The router forwards the request to the default routing interface
For example, the routing table on the left of the above figure You can replace the last five lines with s*0.0.0.0/0
Multiple lines can also be connected between routers 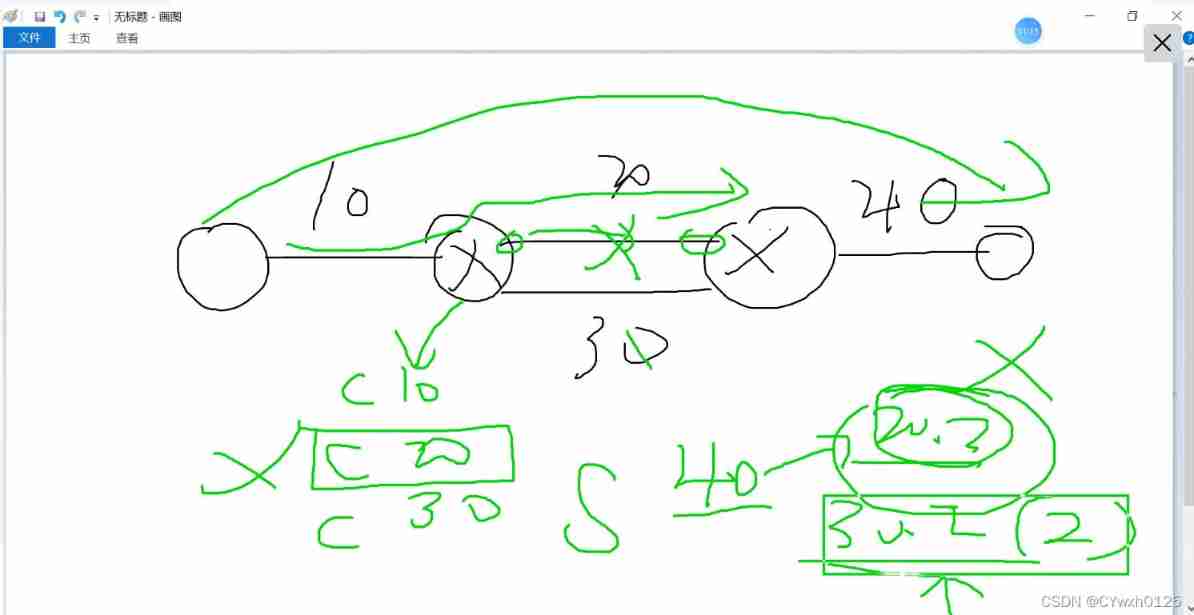
Static routing
conf t
ip route Target segment Subnet mask Next jump IP
Such as ip route 70.1.1.0 255.255.255.0 20.1.1.2
Default route
conf t
ip route 0.0.0.0 0.0.0.0 Next jump IP
Such as :
ip route 0.0.0.0 0.0.0.0 20.1.1.2
Floating route :
Add a space after the static or default route + Numbers ( Positive integer )
ip route 0.0.0.0 0.0.0.0 20.1.1.2
ip route 0.0.0.0 0.0.0.0 30.1.1.2 2
边栏推荐
- Datapipeline was selected into the 2022 digital intelligence atlas and database development report of China Academy of communications and communications
- [public class preview]: basis and practice of video quality evaluation
- 【云资源】云资源安全管理用什么软件好?为什么?
- 几款分布式数据库的对比
- Request + BS4 crawl Netease cloud music popular comments
- Usage, installation and use of TortoiseSVN
- Catch all asynchronous artifact completable future
- NFT value and white paper acquisition
- :: ffff:192.168.31.101 what address is it?
- Idea remote debugging agent
猜你喜欢
昆仑太科冲刺科创板:年营收1.3亿拟募资5亿 电科太极持股40%
LeetCode_2(两数相加)

The real king of caching, Google guava is just a brother
![[server data recovery] a case of RAID5 data recovery stored in a brand of server](/img/04/c9bcf883d45a1de616c4e1b19885a5.png)
[server data recovery] a case of RAID5 data recovery stored in a brand of server
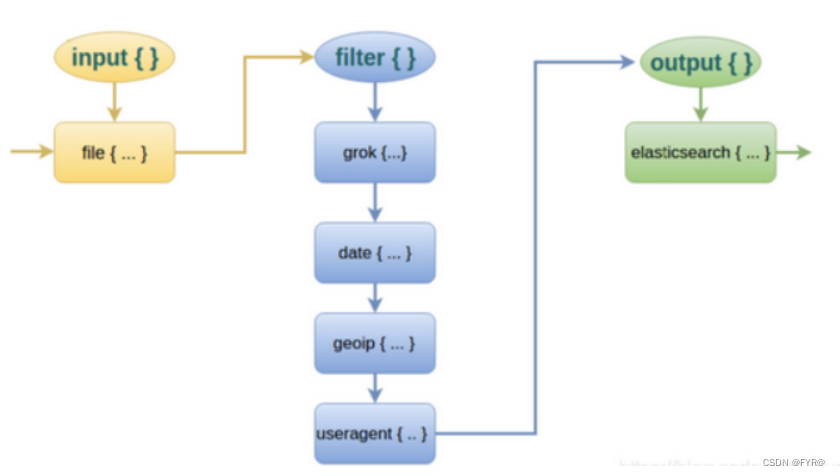
ELFK部署
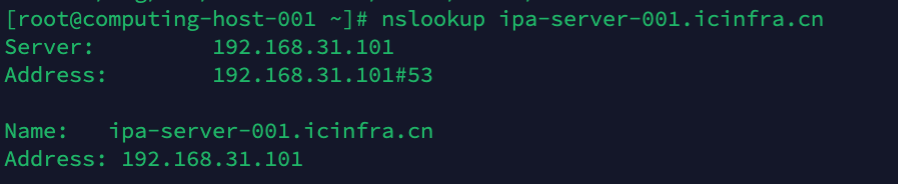
::ffff:192.168.31.101 是一个什么地址?
![Primary code audit [no dolls (modification)] assessment](/img/b8/82c32e95d1b72f75823ca91c97138e.jpg)
Primary code audit [no dolls (modification)] assessment
基于微信小程序的订餐系统
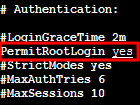
When using Tencent cloud for the first time, you can only use webshell connection instead of SSH connection.
内网穿透工具 netapp
随机推荐
LeetCode_3(无重复字符的最长子串)
asp.net 读取txt文件
[South China University of technology] information sharing of postgraduate entrance examination and re examination
2022 construction welder (special type of construction work) special operation certificate examination question bank and online simulation examination
Aikesheng sqle audit tool successfully completed the evaluation of "SQL quality management platform grading ability" of the Academy of communications and communications
Blue Bridge Cup study 2022.7.5 (morning)
Recommendation number | what are interesting people looking at?
Request + BS4 crawl Netease cloud music popular comments
Prefix, infix, suffix expression "recommended collection"
Ueditor + PHP enables Alibaba cloud OSS upload
PostgreSQL Usage Summary (PIT)
内网穿透工具 netapp
Those things I didn't know until I took the postgraduate entrance examination
面试官灵魂拷问:为什么代码规范要求 SQL 语句不要过多的 join?
Can graduate students not learn English? As long as the score of postgraduate entrance examination English or CET-6 is high!
Datapipeline was selected into the 2022 digital intelligence atlas and database development report of China Academy of communications and communications
Wechat app payment callback processing method PHP logging method, notes. 2020/5/26
Xampp configuring multiple items
几款分布式数据库的对比
Win10 - lightweight gadget