当前位置:网站首页>Have you done the network security "physical examination" this year?
Have you done the network security "physical examination" this year?
2022-06-29 09:24:00 【Cyberpeace】

Global network security incidents occur frequently , Hackers roam all walks of life , The enterprise network system lights up “ A red light ”. In recent days, , Decentralized trading platform FSWAP Official sources say they were maliciously attacked , The hacker tries to encrypt communication through blockchain ; This year, 5 month , Russia's largest bank Sberbank( The Federal Reserve Bank ) Encounter the largest ever DDoS attack ; In the same month , The domestic digital collection platform Tianqiong digital collection said that it suffered malicious attacks , Hackers use false balances to buy and steal users' collections .
The financial industry has the attribute of high profit , It has always been the main target of cyber criminals . As one of the key industries , Finance and energy 、 Electric power 、 The network security problems of telecom operators and other enterprises have attracted much attention .
among , Network security “ physical examination ” It has risen to the height of laws and regulations .
《 Network security law of the people's Republic of China 》 Article 38
The operator of critical information infrastructure shall, on its own or by entrusting a network security service institution, test and evaluate the security and possible risks of its network at least once a year , The inspection and evaluation and improvement measures shall be submitted to the relevant departments responsible for the security protection of key information infrastructure .
《 Key information infrastructure security regulations 》 Article 17.
The operator shall conduct network security detection and risk assessment on key information infrastructure at least once a year by itself or by entrusting a network security service institution , Timely rectify the safety problems found , And submit the information according to the requirements of the protection department .
There is usually a lack of talents in enterprise network security self inspection 、 Continuous penetration is limited 、 A series of problems such as verification of vulnerability harm degree . The detection and evaluation method based on Automated Penetration simulates real hacker attacks , It can widely test many known security vulnerabilities in a large number of systems , Without the tedious manual testing process , Effectively reduce the working time cost of network security operation and maintenance personnel , Improve the self checking ability of enterprise network , It has become an important tool for enterprise network security detection and risk assessment “ Optimization tools ”.
4 Step by step to thoroughly investigate the hidden dangers of the intranet
With ten years of network security experience, saining network security , Developed a powerful penetration test capability 、 Integration of multiple penetration modes 、 Automatic penetration platform with rich attack modules , In the process of network security physical examination , Depth of penetration 、 Fully capture the network system “ Weak points ”“ Risk point ”, Help enterprises thoroughly investigate the hidden dangers of the intranet .

Automated Penetration platform workflow
1. Target discovery scan
Automatic penetration will first be applied to network devices through built-in modules 、 operating system 、 database 、Web Applications and services 、 Deep scan the basic information of Internet of things devices and systems , Third party tool scanning can be imported to cooperate with vulnerability scanning tool for depth scanning 、 Scan thoroughly .
2. Get access
After confirming the risk point , By brute force 、 Automated vulnerability exploitation 、 Manual exploit 、 Social engineering 、Web Application scanning uses different penetration “ attack ” The way , Obtain access to the target site .
3. Target control
penetration “ attack ” After success , Further use Meterpreter、 Command line Shell、 agent /VPN Springboard and other technologies to establish a session , On the Intranet 、 Host and other target points .
4. collect evidence
After completion of control , Start collecting password hash values 、 System files 、 Screen shots and other sensitive information of controlled target points . Finally, clean the penetration marks , Generate a report , Complete the entire automated penetration workflow .
Automated penetration through collection “ Weak points ”“ Risk point ” Information and generate test report , Help enterprises visualize 、 Clearly understand the security issues of the Intranet environment .
Saining network security automation penetration platform has a wealth of 、 Continuously updated attack module resource library , Ensure that real vulnerabilities can be fully verified , Support users to import custom attack modules , Adjust the penetration intensity according to the business content , Avoid affecting the normal operation of important business systems , Provide professional services for enterprise network testing and evaluation 、 Customizable “ Medical tools ”.
边栏推荐
- [to.Net] C data model, from Entity Framework core to LINQ
- Jar package and war package
- 专业结构record
- CMD enter virtual machine
- Research progress of target detection in the era of deep convolutional neural network
- Recursive RBAC menu level display infinite classification
- Picture format -webp
- Summary of IO streams
- Write down some written test questions
- pytorch总结—自动求梯度
猜你喜欢

pytorch总结—自动求梯度

Mongodb persistence
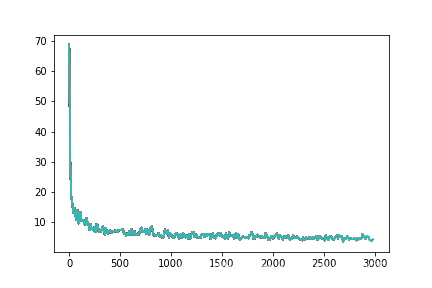
train_on_batch保存一下loss函数变化的图像

Handwritten virtualdom
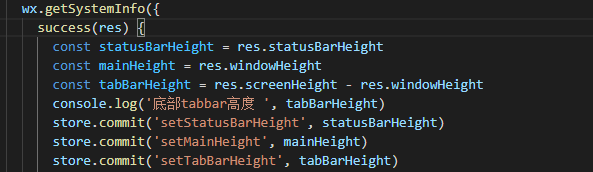
记自定义微信小程序顶部导航栏

Ue4 installe le plug - in datasmith dans la version 4.20-23

UE4 remove the mask transparent white edge in the material
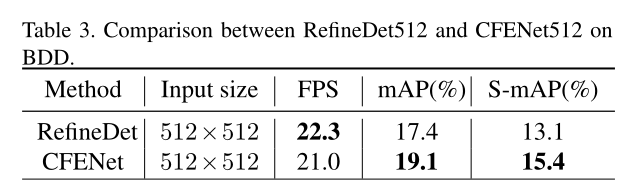
SSD改進CFENet

How is epoll encapsulated in golang?
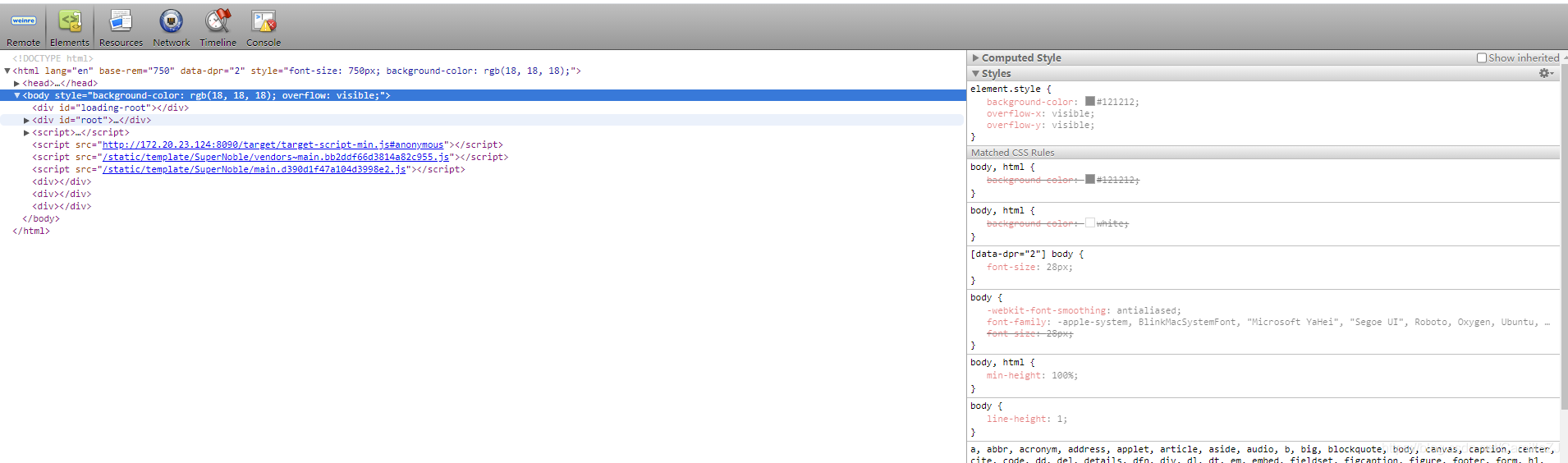
Debugging H5 page -weinre and spy debugger real machine debugging
随机推荐
UE4 VS的Visual Assist插件设置
Debugging H5 page -weinre and spy debugger real machine debugging
Jar package and war package
深入RC、RS、DaemonSet、StatefulSet(七)
超融合架构和传统架构有什么区别?
Wechat applet user refuses to authorize geographic location information and calls up the authorization window again
train_on_batch保存一下loss函数变化的图像
微信小程序子组件向页面传值(父子组件间的通信)带源码
Pytorch summary learning series - data manipulation
UE4 去掉材质中Mask透明白边
Wechat applet latest canvas2d handwritten signature
HB5470民用飞机机舱内部非金属材料燃烧测试
ServerApp. iopub
Mh/t 6040 smoke density test of aviation materials
Wechat applet project: tab navigation bar
Pytorch learning summary - memory cost of operation
promise方法的简单使用
Find the most repeated element in the string
Summary of IO streams
Verilog data type