当前位置:网站首页>Another CVPR 2022 paper was accused of plagiarism, and Ping An insurance researchers sued IBM Zurich team
Another CVPR 2022 paper was accused of plagiarism, and Ping An insurance researchers sued IBM Zurich team
2022-06-30 18:19:00 【Computer Vision Research Institute】
Pay attention to the parallel stars
Never get lost
Institute of computer vision


official account ID|ComputerVisionGzq
Study Group | Scan the code to get the join mode on the homepage
Computer Vision Institute column
author :Edison_G
「 They are not copying the text , It's plagiarism .」
from 《 Almost Human 》
01
summary
yesterday , Someone is here. reddit Post posting ,IBM Zurich Research Center plagiarized its own paper , And it was CVPR 2022 To receive the .
The poster wrote :
My name is Xianbiao Qi, Is a computer vision researcher with more than ten years of research experience . I am writing this blog to complain about a serious case :IBM Employees of the Zurich Research Center deliberately plagiarized our papers . They are not copying the text , It's plagiarism .
Qi The suspected plagiarized paper mentioned is entitled 「PingAn-VCGroup's Solution for ICDAR 2021 Competition on Scientific Literature Parsing Task B: Table Recognition to HTML( Safety VCGroup by ICDAR 2021 Scientific literature analysis competition task B Solutions provided :HTML Form identification )」, The author is from Ping An insurance and Ping An technology , Upload arXiv The time is 2021 year 5 month ,2021 year 7 The code was released in January ,2021 year 9 Month issued Tablemaster Pre training model ,2021 year 11 Month issued tablemaster_mmocr docker Environmental Science . The competition mentioned in the paper is 2021 year 4 At the end of the month , from IBM Another team hosted .

Thesis link :https://arxiv.org/pdf/2105.01848.pdf
As stated in the title of the paper , This article is for ICDAR 2021 Scientific literature analysis competition task B(HTML Form identification ) Provides a set of solutions . say concretely , They divided table content recognition into four subtasks : Table structure identification 、 Text line detection 、 Text line recognition and box assignment . The table structure recognition algorithm is based on a robust image text recognition algorithm MASTER custom .PSENet Used to detect each text line in the table image . The text line recognition model is also built on MASTER above . Last , In the box allocation stage , They will PSENet The detected text box is associated with a structure item reconstructed by table structure prediction , And the recognizable content of the text line is filled in the corresponding item .

Accused of plagiarism IBM The paper is entitled 「TableFormer: Table Structure Understanding with Transformers(TableFormer: use Transformer Understanding table structure )」, Upload arXiv The time is 2022 year 3 month , Submit to CVPR The time of is unknown .

Thesis link :https://arxiv.org/pdf/2203.01017.pdf
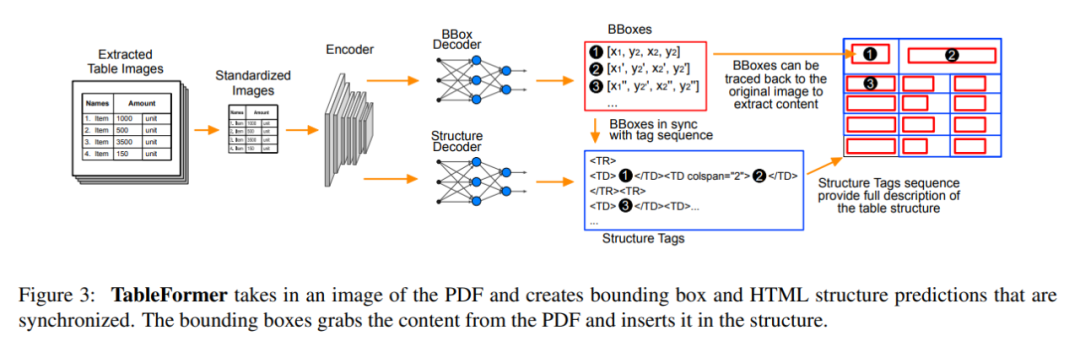
In this paper ,IBM A new table structure recognition model is proposed by the researchers of , It improves the latest end-to-end deep learning model from two aspects ( From PubTabNet Of encoder-dual-decoder). First , They introduced a new object detection decoder for table cells . In this way , They can go directly from PDF Get programmatic... From the source PDF Table cell contents of , This avoids customization OCR Decoder training . This architectural change has led to more accurate table content extraction . secondly , They will LSTM The decoder is replaced by based on transformer The decoder of .
Qi Express ,IBM Their methodology was plagiarized in this paper 、 Preprocessing 、 post-processing 、 Visual effect 、 Reasoning 、 System level solutions 、 Code 、 Pre training model, etc , but 「 In order not to be caught 」, They don't quote Qi Papers of others .

Next ,Qi A dozen pictures show what he thinks IBM Where there is plagiarism .

Qi The suspected plagiarism points displayed 1: methodology . He thinks that ,IBM Of the researchers copied their ideas , Rewrite the 「 contribution 」 part , And redrawn the structure diagram according to their diagram .

Qi The suspected plagiarism points displayed 2: Preprocessing .

Qi The suspected plagiarism points displayed 3: post-processing .

Qi The suspected plagiarism points displayed 4: Reasoning acceleration method

Qi The suspected plagiarism points displayed 5: skill .

Qi The suspected plagiarism points displayed 6: Text line detection and text line recognition .

Qi The suspected plagiarism points displayed 7: System level solutions .

Qi The suspected plagiarism points displayed 8: Visual effect .

Qi The suspected plagiarism points displayed 9: Misleading readers .
I'm looking Qi After the example given , Some people think these are very strong evidence ,IBM It is difficult for the team to prove that their papers are original ,Qi We should go to CVPR Procedure Committee complaints .
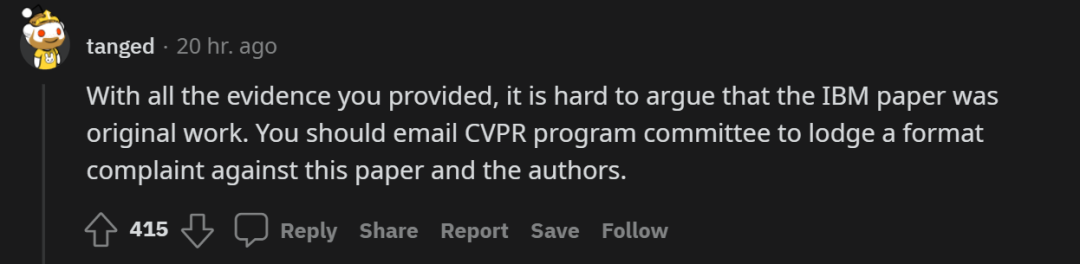
however , Some people think that , The evidence is not strong enough :「 The two groups are working on the same problem , Using the same public data , Their solutions also have similarities . But this does not mean that one side copies the other . for example 「 Suspected of plagiarism 1」 The content shown in is not so close 」.

at present , We haven't seen it at the bottom of the post yet IBM The author's response .
however , It is worth mentioning that , This is not this year CVPR The only suspected plagiarism incident exposed . A few days ago , A netizen in YouTube It was revealed that , A paper from Seoul University copied a dozen other papers , At present, the author of this paper has apologized and withdrawn his manuscript .
Maybe , The top meeting papers need more effort in checking the duplicate .
Reference link :https://www.reddit.com/r/MachineLearning/comments/vlpnuw/d_ibm_zurich_research_plagiarised_our_paper_and/
THE END
Please contact the official account for authorization.

The learning group of computer vision research institute is waiting for you to join !
ABOUT
Institute of computer vision
The Institute of computer vision is mainly involved in the field of deep learning , Mainly devoted to face detection 、 Face recognition , Multi target detection 、 Target tracking 、 Image segmentation and other research directions . The Research Institute will continue to share the latest paper algorithm new framework , The difference of our reform this time is , We need to focus on ” Research “. After that, we will share the practice process for the corresponding fields , Let us really experience the real scene of getting rid of the theory , Develop the habit of hands-on programming and brain thinking !
VX:2311123606

Previous recommendation
AI Help social security , The latest video abnormal behavior detection method framework
Improved shadow suppression for illumination robust face recognition
Text driven for creating and editing images ( With source code )
Based on hierarchical self - supervised learning, vision Transformer Scale to gigapixel images
YOLOS: Rethink through target detection Transformer( With source code )
Fast YOLO: For real-time embedded target detection ( Attached thesis download )
边栏推荐
- Tensorflow2 深度学习十必知
- Importing alicloud ECS locally to solve deployment problems
- Nielseniq welcomes dawn E. Norvell, head of retail lab, to accelerate the expansion of global retail strategy
- 漏洞复现----35、uWSGI PHP 目录遍历漏洞 (CVE-2018-7490)
- 力扣解法汇总1175-质数排列
- [sword finger offer] sword finger offer 53 - ii Missing numbers from 0 to n-1
- Redis (IX) - enterprise level solution (II)
- [bjdctf2020]the mystery of ip|[ciscn2019 southeast China division]web11|ssti injection
- C language structure
- DeFi借贷协议机制对比:Euler、Compound、Aave和Rari Capital
猜你喜欢

Deep understanding of JVM (V) - garbage collection (II)

Alexnet of CNN classic network (Theory)

Customer relationship CRM management system based on SSH

Type ~ storage ~ variable in C #
![[PROJECT] Xiaomao school (IX)](/img/01/f7fc609e7a156d6e60ce6482ba2ac1.jpg)
[PROJECT] Xiaomao school (IX)

autocad中文语言锁定只读警报怎么解决?
![[software testing] basic knowledge of software testing you need to know](/img/cf/875f7a2a6f678eef22cd8b9e0f912d.jpg)
[software testing] basic knowledge of software testing you need to know

Php8.0 environment detailed installation tutorial
Servlet operation principle_ API details_ Advanced path of request response construction (servlet_2)

Redis (III) - transaction
随机推荐
Research on the principle of Tencent persistence framework mmkv
[BJDCTF2020]The mystery of ip|[CISCN2019 华东南赛区]Web11|SSTI注入
uni-app进阶之内嵌应用【day14】
Ardunio esp32 obtains real-time temperature and humidity in mqtt protocol (DH11)
漏洞复现----37、Apache Unomi 远程代码执行漏洞 (CVE-2020-13942)
Elastic 8.0: opening a new era of speed, scale, relevance and simplicity
【机器学习】K-means聚类分析
MSF后渗透总结
基于SSH的客户关系CRM管理系统
leetcode:787. The cheapest transfer flight in station K [k-step shortest path + DFS memory + defaultdict (dict)]
火山引擎入选国内首个《边缘计算产业全景图》
Php8.0 environment detailed installation tutorial
Solve the problem of unable to connect to command metric stream and related problems in the hystrix dashboard
Synchronized summary
MySQL advanced - index optimization (super detailed)
Do fresh students get a job or choose a job after graduation?
Post MSF infiltration summary
Simulation of campus network design based on ENSP
Switching routing (VLAN) experiment
ASP. Net authentication code login