当前位置:网站首页>Deep embedding and alignment of Google | protein sequences
Deep embedding and alignment of Google | protein sequences
2022-07-03 05:14:00 【Zhiyuan community】
Once trained ,DEDAL A gap and replacement scoring matrix calculated specifically for each new pair of sequences will be generated . Besides , Gaps and replacement scores are background : For each pair of positions , They depend on the complete sequence to be aligned . Then use a standard SW The algorithm uses these parameters to calculate the best arrangement . This article shows that ,DEDAL It can be effectively trained on modern hardware with accelerators . Once the training is done ,DEDAL With the standard SW comparison , The alignment quality predicted for remote homologues is improved 2-3 times , And it produces an alignment score that can detect remote homologues more accurately .
The figure above shows the data from Pfam-A Examples of sequence alignment of two protein domains of seeds .
a. Respectively from the Pfam-A Seed database ( The second line )、DEDAL forecast ( The third line ) Harmony PFASUM70 Alternative matrix prediction ( In the fourth row ) The comparison . This article shows Pfam-A Seed and DEDAL All residues in the two sequences aligned , But it didn't show PFASUM Aligned upstream and downstream misaligned residues in the sequence . The residues highlighted in green correspond to conservative residues that are correctly aligned , The residues shown in red correspond to predicted alignment and Pfam-A Differences between seed alignments .
b. come from PFASUM Substitution scores between all residue pairs of the substitution matrix .
c. from DEDAL Predicted SW Parameters .

In terms of Technology , This article explores two ways to create a distinguishable SW Align modules , Need to be in " Learn alignment " Training in the task DEDAL Parameters of , Use smoothing or perturbation techniques ; This paper finds that there is no obvious difference in performance between the two , And in the final DEDAL The disturbance based method is implemented in the model . About training DEDAL The permutation of , This paper finds that , When this article hopes DEDAL When accurate local arrangement can be predicted , Use Pfam Expand the domain instead of Pfam Domains are beneficial . Pre training in masking language modeling tasks DEDAL when , The sequences related to families outside the distribution are separated from " Protein universe " Exclude from , This leads to a slight decrease in the performance of remote homologues , Although the performance gap relative to the baseline is not obvious .
About the strategy of end-to-end joint training converter and parameter , This paper finds that this is indeed significantly better than the more classic two-step strategy , That is, first train the converter encoder in the shielded language modeling task , Then fix the converter at " Learn alignment " Training parameter device in task . This shows that , A general language model , Such as ESM, It's not enough. , At least fine tune , To achieve the best performance of alignment .
The above figure shows the application of learning embedding in downstream tasks . This paper evaluates the benefits of context sensitive embedding by simply training a model , In this model , The replacement cost is limited to depend only on the amino acids to be aligned ; It's not hard to see. , This paper observes that the performance of this model has a great decline , Achieved and " aim " The performance of the best replacement matrix in .
边栏推荐
- cookie session jwt
- Automatic voltage rise and fall 5-40v multi string super capacitor charging chip and solution
- leetcode860. Lemonade change
- [research materials] 2021 annual report on mergers and acquisitions in the property management industry - Download attached
- (完美解决)matplotlib图例(legend)如何自由设置其位置
- Web APIs exclusivity
- Go practice -- use redis in golang (redis and go redis / redis)
- appium1.22.x 版本后的 appium inspector 需单独安装
- Promise
- 1119 pre- and post order traversals (30 points)
猜你喜欢

(subplots用法)matplotlib如何绘制多个子图(轴域)

Botu uses peek and poke for IO mapping
音频焦点系列:手写一个demo理解音频焦点与AudioMananger

【实战项目】自主web服务器

JQ style, element operation, effect, filtering method and transformation, event object

Class loading mechanism (detailed explanation of the whole process)
![[set theory] relational power operation (relational power operation | examples of relational power operation | properties of relational power operation)](/img/8b/c10423ee95200a0d94f9fb9dde76eb.jpg)
[set theory] relational power operation (relational power operation | examples of relational power operation | properties of relational power operation)
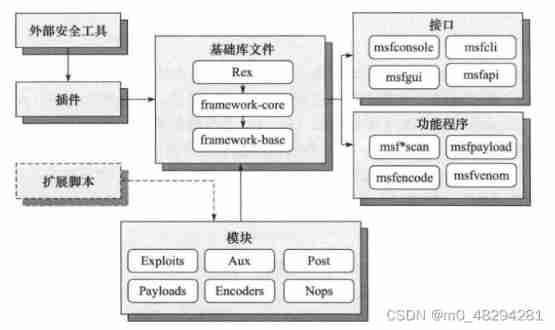
Basic use of Metasploit penetration testing framework
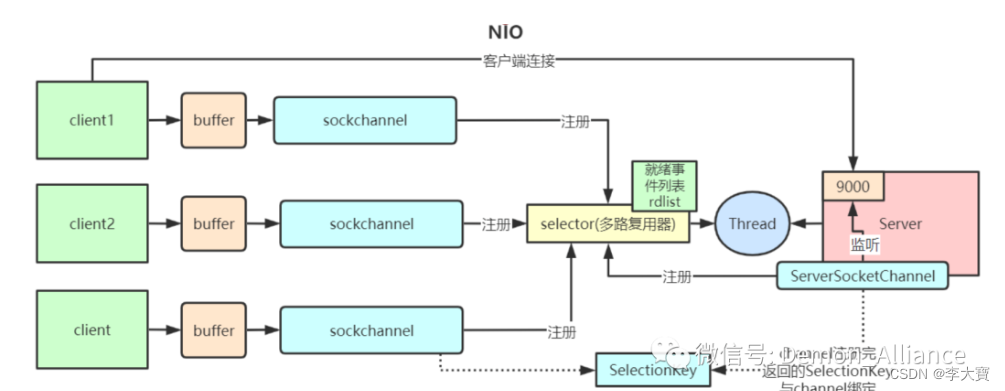
BIO、NIO、AIO区别
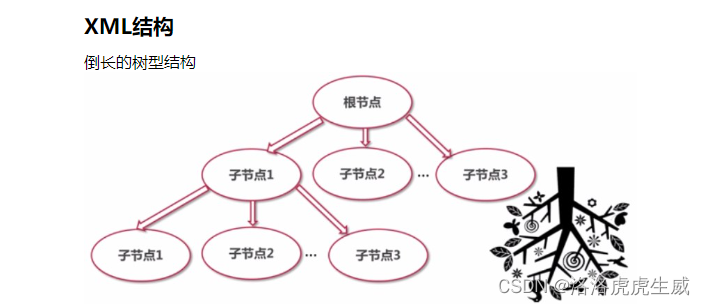
XML配置文件
随机推荐
[backtrader source code analysis 4] use Python to rewrite the first function of backtrader: time2num, which improves the efficiency by 2.2 times
RT thread flow notes I startup, schedule, thread
SSM framework integration
谷歌 | 蛋白序列的深度嵌入和比对
MySQL master-slave configuration
音频焦点系列:手写一个demo理解音频焦点与AudioMananger
Kept hot standby and haproxy
Go practice -- use redis in golang (redis and go redis / redis)
[set theory] relationship properties (common relationship properties | relationship properties examples | relationship operation properties)
Sprintf formatter abnormal exit problem
Go practice -- generate and read QR codes in golang (skip2 / go QRcode and boombuilder / barcode)
联想R7000显卡的拆卸与安装
Congratulations to musk and NADELLA on their election as academicians of the American Academy of engineering, and Zhang Hongjiang and Fang daining on their election as foreign academicians
Source insight garbled code solution
Retirement plan fails, 64 year old programmer starts work again
1118 birds in forest (25 points)
Without 50W bride price, my girlfriend was forcibly dragged away. What should I do
Promise
[backtrader source code analysis 5] rewrite several time number conversion functions in utils with Python
JS string and array methods

