当前位置:网站首页>12306: mom, don't worry about me getting the ticket any more (1)
12306: mom, don't worry about me getting the ticket any more (1)
2022-07-06 15:20:00 【Jane said Python】
One 、 Write it at the front
On the occasion of national day , I'm still trying to get a train ticket , I can only take the bus home and worry ~ And you? ?
The good news is here. , After learning this tweet , You don't have to ask for this circle of friends every day anymore , Please qq There's space .
Chapter one , So let's log in 12306, After reading this , You will learn to : How to simulate login , Basic image verification method , striking one snag after another , The process is interesting , Refer to some online materials .
Two 、 A meal operation
technological process ( The words are a little ugly , Just look ):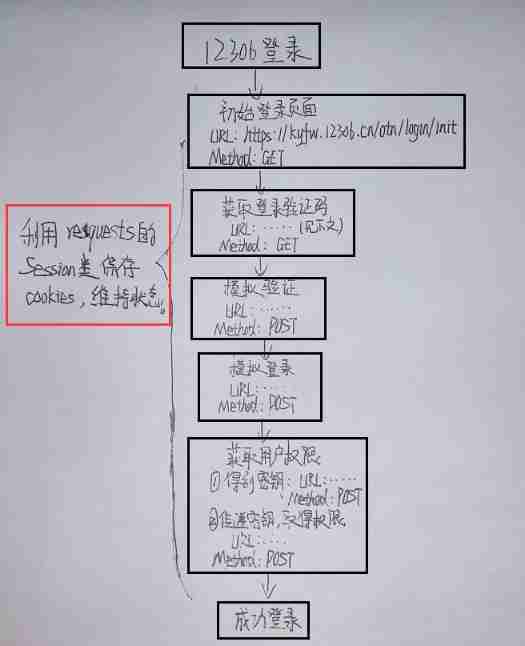
1. Login image verification cracking
(1) Get the login page ,session preservation cookies value .
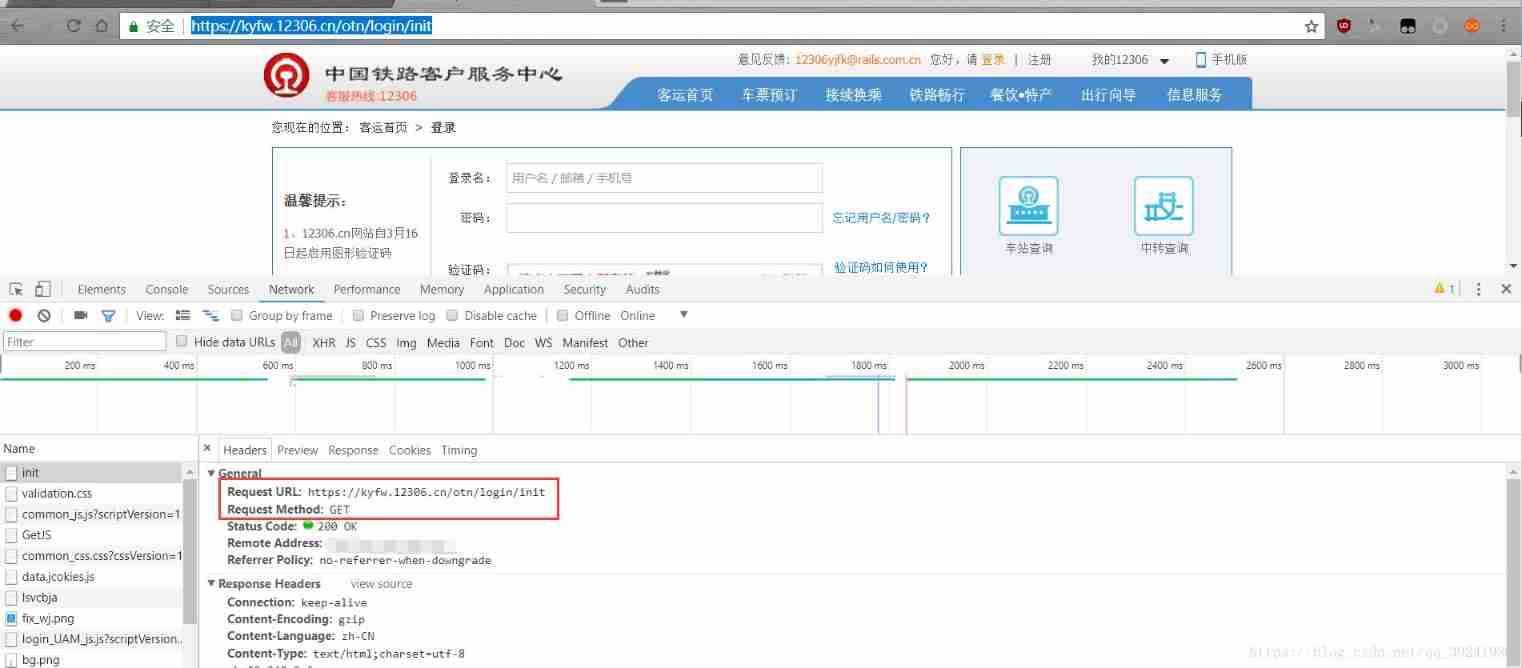
Access page :https://kyfw.12306.cn/otn/login/init,F12 Page analysis , as follows :
Headers in
Request URL: https://kyfw.12306.cn/otn/login/init
Request Method: GET
- Code :
import requests import os from fake_useragent import UserAgent # 1. Get login # Request header , Anti creep camouflage headers = {
"User-Agent": UserAgent(verify_ssl=False).random, "Host":"kyfw.12306.cn", "Referer":"https://kyfw.12306.cn/otn/passport?redirect=/otn/" } login_url = 'https://kyfw.12306.cn/otn/login/init' # 1.1 cookie keep session = requests.Session() # 1.2 get request login_response = session.get(login_url,headers = headers) login_html = login_response.text # print(login_html) (2) Get the verification picture , Crack the verification operation
- Cracking ideas :
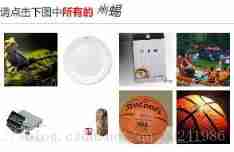
Download the verification image from the page to the local , Then select the correct picture position as required , Pass the correct picture coordinates , Click on the simulation page , Send a request , Simulate the verification operation . - Verify image page analysis :
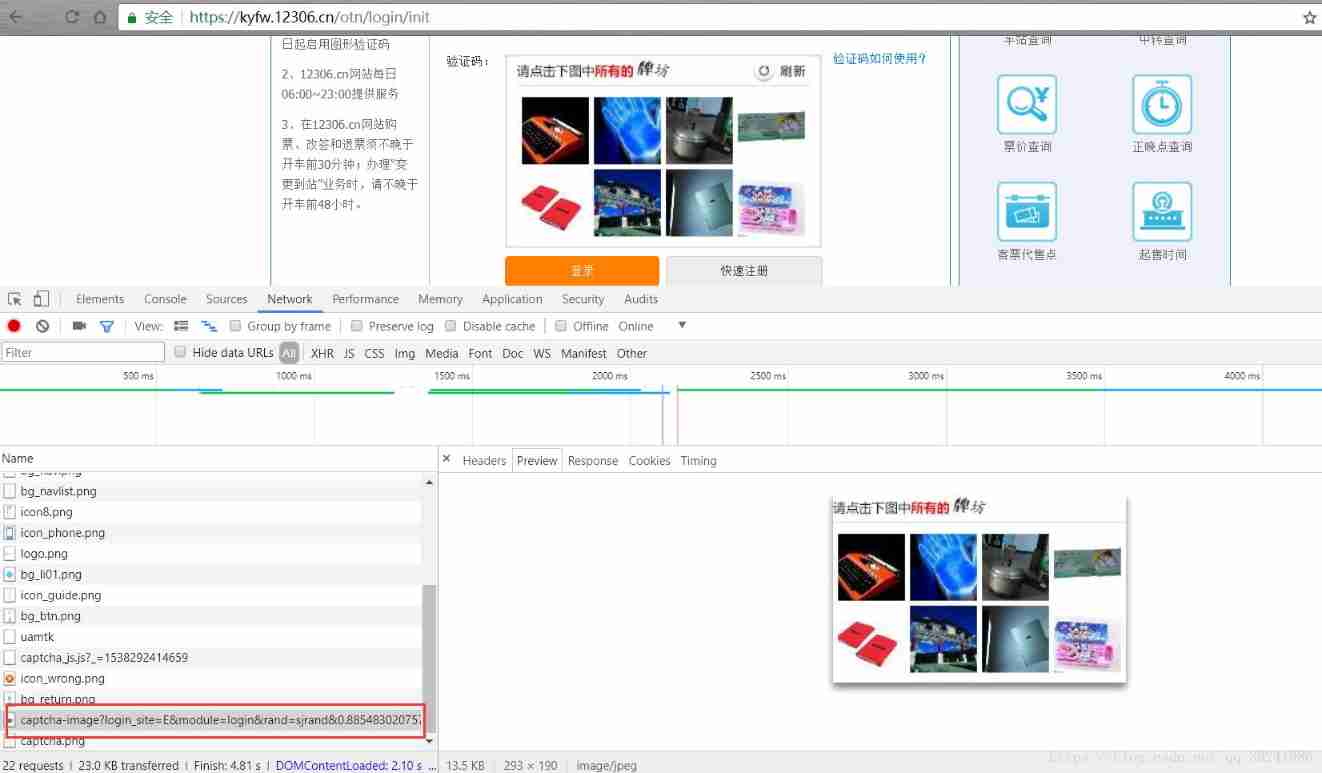
Headers in
Request URL: https://kyfw.12306.cn/passport/captcha/captcha-image?login_site=E&module=login&rand=sjrand&0.8854830207575652
Request Method: GET
- Check the validation analysis :
You must enter the account password on the page , Only after verifying the selection can it be loaded , So I enter my account number and wrong password , Picture verification , Load the following results :
captcha-check : Used to check and verify whether the picture is selected correctly ( Verify the correct )
login : User login account 、 Password judgment
All are POST request
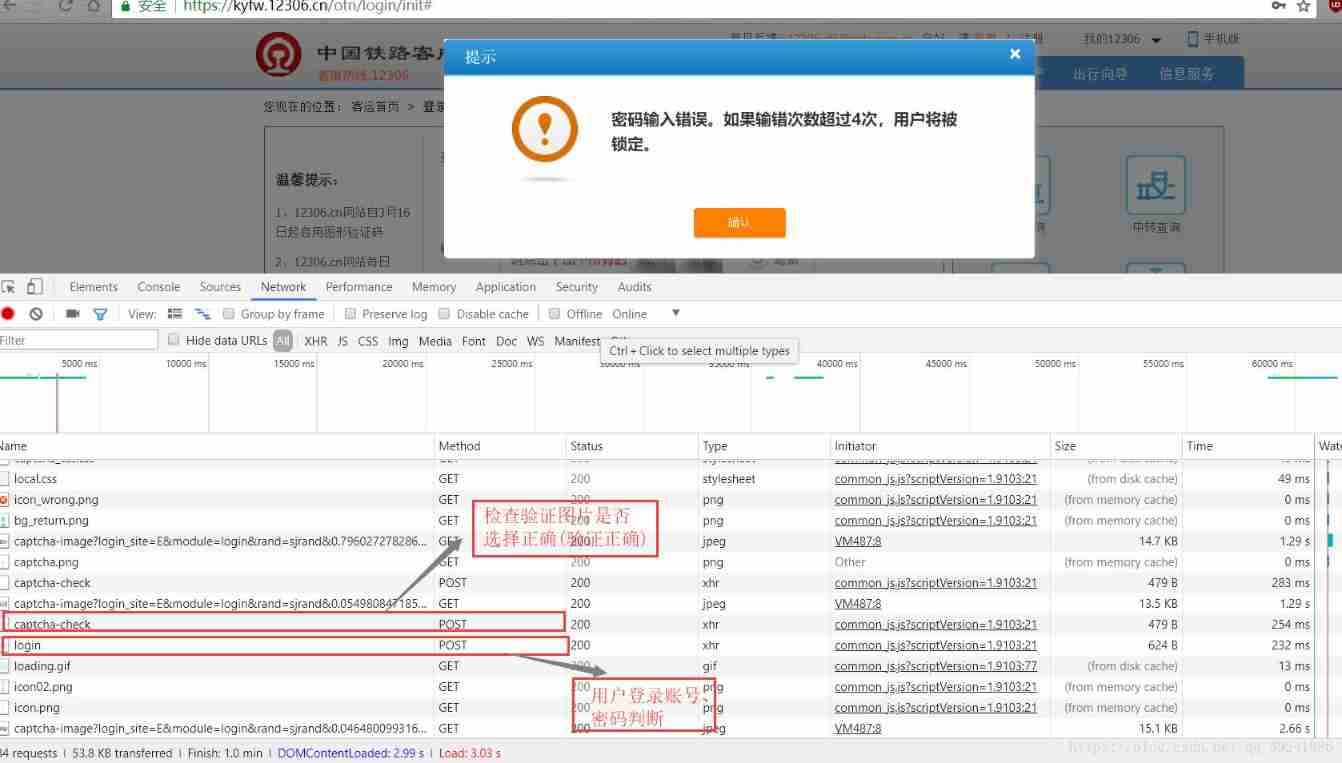
Headers in
Request URL: https://kyfw.12306.cn/passport/captcha/captcha-check
Request Method: POST
data = {
“answer”: positions,
“login_site”: “E”,
“rand”: “sjrand”
}
- Code :
# 2. Get and crack the authentication operation # 2.1 Download verification picture captcha_url = 'https://kyfw.12306.cn/passport/captcha/captcha-image?login_site=E&module=login&rand=sjrand&0.8854830207575652' captcha_response = session.get(captcha_url,headers = headers) # File save path image_path = os.path.abspath('image') + '/captcha_image.jpg' # Write to file in binary with open(image_path,'wb') as image_file: image_file.write(captcha_response.content) # 2.2 verification check_url = 'https://kyfw.12306.cn/passport/captcha/captcha-check' # The input data format is :x1,y1,x2,y2,...,xn,yn positions = input(" Please enter the verification code : ") # Correct picture coordinates # Send verification code data = {
"answer": positions, "login_site": "E", "rand": "sjrand" } check_response = session.post(check_url,data = data,headers = headers) check_result = check_response.json() # Tests found ,result_code = 4 when , Indicates that the verification is successful if not check_result['result_code'] == 4: exit(" Validation failed ") print(check_result ) - Running results :
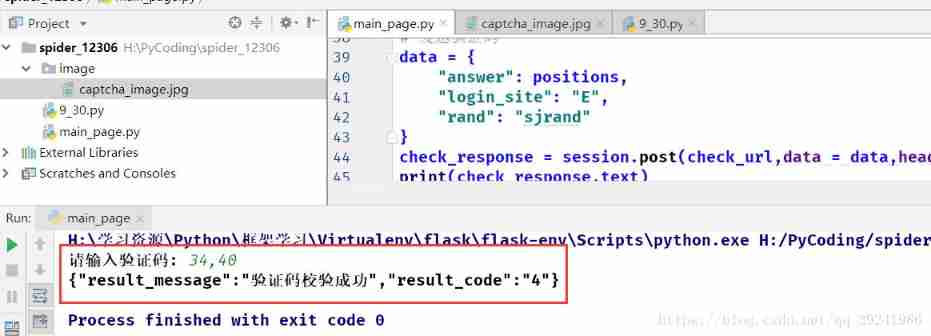
2. Sign in
(1) Sign in login analysis
- F12 analysis
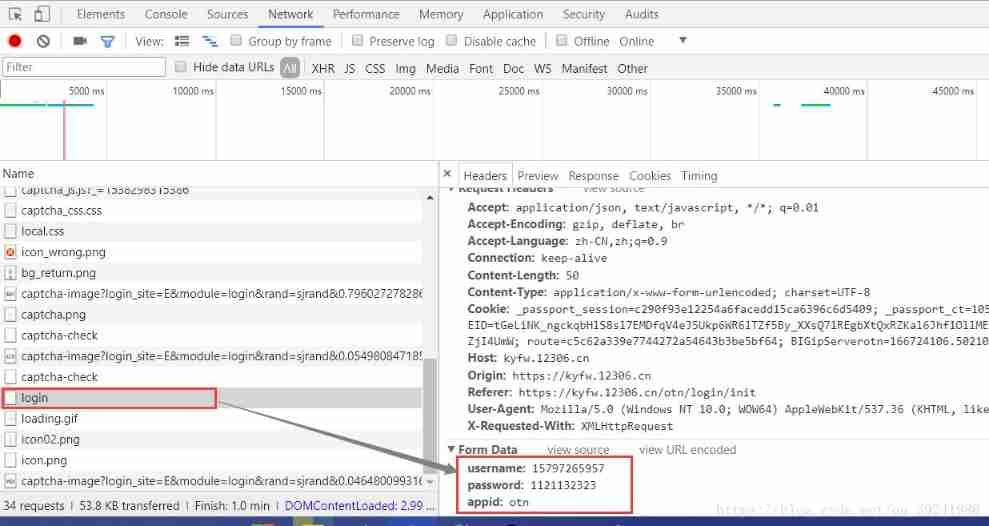
Request URL: https://kyfw.12306.cn/passport/web/login
Request Method: POST
data = {
‘username’: Account_number, # The user account
‘password’: Password, # User password
‘appid’: ‘otn’
}
- Code :
# 3. Start the login operation login_check_url = 'https://kyfw.12306.cn/passport/web/login' login_check_data = {
'username': Account_number, 'password': Password, 'appid': 'otn' } login_check_response = session.post(login_check_url,data=login_check_data,headers = headers) print(login_check_response.json()) - Running results :
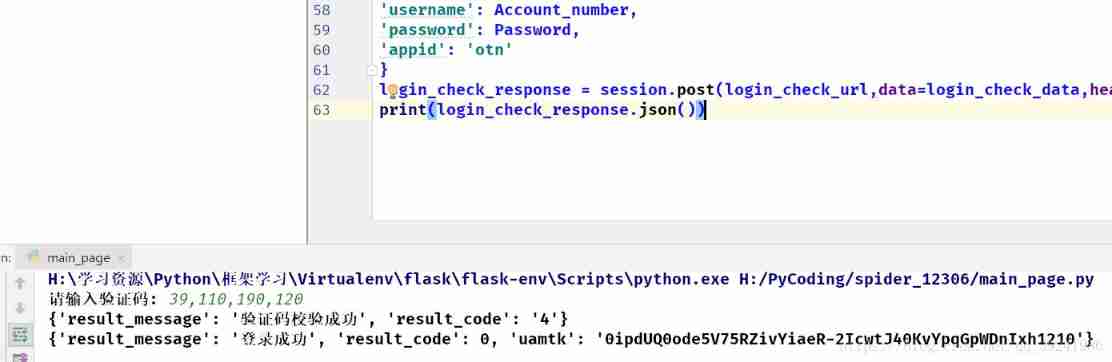
However, there is no real login success .
(1) Sign in Access
- Basic analysis
Successfully logged in 12306 The following page is an illustration :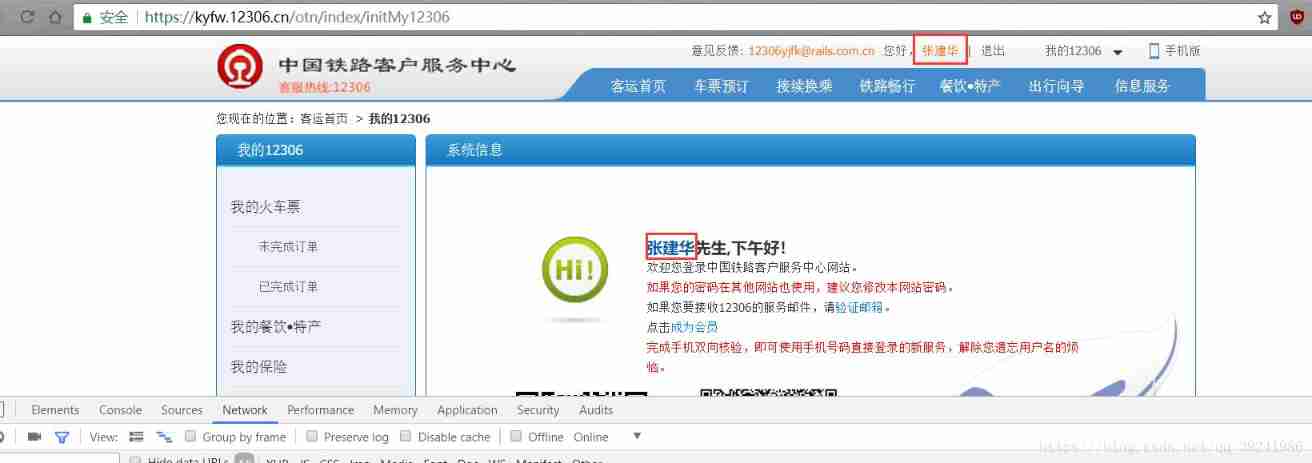
You can find that the source code of the page we crawled does not contain my name : Are we really successful in login ,12306 The internal permission verification of is troublesome , It can be seen from the initial diagram , Disguised verification , In addition to the password and account number input , And permission settings , Or two floors , The code is as follows , If you don't understand, add me on wechat :zs820553471 Well .
- Code
# 4. Access permissions authority # 4.1 Get permission key :newapptk uamtk_data = {
"appid":"otn" } uamtk_url = "https://kyfw.12306.cn/passport/web/auth/uamtk" uamtk_response = session.post(uamtk_url, headers=headers, data=uamtk_data) uamtk_dict = uamtk_response.json() newapptk = uamtk_dict['newapptk'] # print(uamtk_dict['newapptk']) # 4.2 Pass key , Access permissions uamauthclient_data = {
"tk" : newapptk } uamauthclient_url = "https://kyfw.12306.cn/otn/uamauthclient" uamauthclient_response = session.post(uamauthclient_url, headers=headers, data=uamauthclient_data) # 5 Really login initMy_url = "https://kyfw.12306.cn/otn/index/initMy12306" initMy_response = session.get(initMy_url, headers=headers) my_name = initMy_response.text.find(" Zhang Jianhua ") if not my_name == -1: print(" The user has successfully logged in ") - Running results
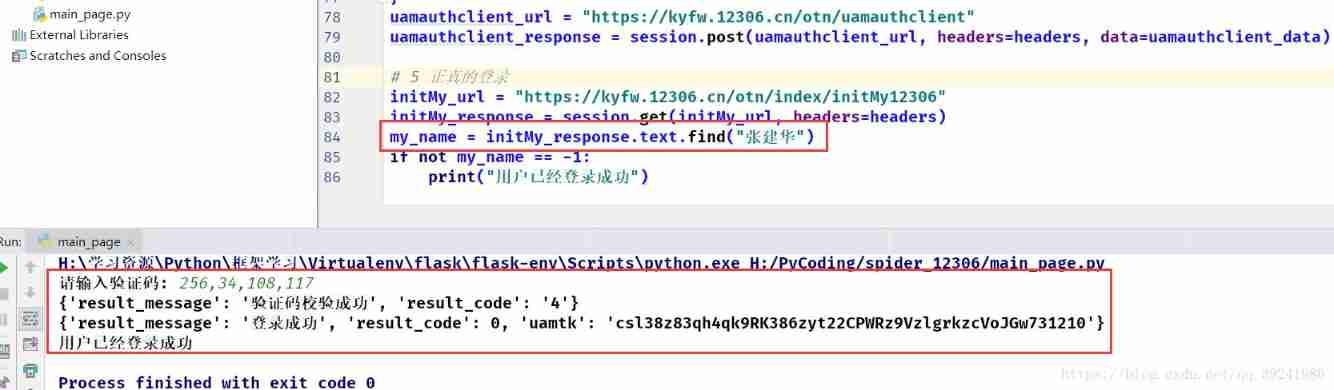
3、 ... and 、 Just talk about
When I first wrote this tweet, I wanted to finish it one by one 12306 Sign in , Train number information acquisition , Grab tickets , Ticket purchase , It can be written , Finding things is not so simple , The spirit is willing but the flesh is weak , Yesterday in GitHub I opened an account on the Internet ,12306 The series will be in GitHub Update on ( The code has been on the code cloud before , The convenience of Chinese ), Welcome aboard , With complete , No longer worry about buying tickets .

边栏推荐
- UCORE lab5 user process management experiment report
- Mysql database (IV) transactions and functions
- 软件测试方法有哪些?带你看点不一样的东西
- Automated testing problems you must understand, boutique summary
- 基于485总线的评分系统双机实验报告
- Stc-b learning board buzzer plays music 2.0
- Contest3145 - the 37th game of 2021 freshman individual training match_ A: Prizes
- How to build a nail robot that can automatically reply
- CSAPP Shell Lab 实验报告
- 几款开源自动化测试框架优缺点对比你知道吗?
猜你喜欢
Servlet
UCORE lab1 system software startup process experimental report
全网最详细的postman接口测试教程,一篇文章满足你
转行软件测试必需要知道的知识

Rearrange spaces between words in leetcode simple questions
MySQL数据库(四)事务和函数
Intensive learning notes: Sutton book Chapter III exercise explanation (ex17~ex29)
自动化测试你必须要弄懂的问题,精品总结
How to build a nail robot that can automatically reply
What is "test paper test" in software testing requirements analysis
随机推荐
ucore lab5
[HCIA continuous update] working principle of static route and default route
How to change XML attribute - how to change XML attribute
Heap, stack, queue
Global and Chinese markets of Iam security services 2022-2028: Research Report on technology, participants, trends, market size and share
Common Oracle commands
Maximum nesting depth of parentheses in leetcode simple questions
The wechat red envelope cover designed by the object is free! 16888
MySQL transactions
The number of reversing twice in leetcode simple question
Leetcode simple question: check whether two strings are almost equal
UCORE lab5 user process management experiment report
Global and Chinese markets of cobalt 2022-2028: Research Report on technology, participants, trends, market size and share
What are the business processes and differences of the three basic business modes of Vos: direct dial, callback and semi direct dial?
The minimum number of operations to convert strings in leetcode simple problem
[pytorch] simple use of interpolate
How to become a good software tester? A secret that most people don't know
Investment operation steps
If the position is absolute, touchablehighlight cannot be clicked - touchablehighlight not clickable if position absolute
Oracle foundation and system table


