当前位置:网站首页>Introduction to safety testing
Introduction to safety testing
2022-07-06 15:13:00 【Test Xiaowan】
Catalog
2、 The purpose of the safety test
3、 The difference between safety test and routine test
1、 Security test definition
Security test is a test based on function test , Safety tests provide evidence that , In the face of malicious attacks , The application can still fully meet its needs , It mainly refers to the process of inspecting the product to verify whether it conforms to the definition of safety requirements and product quality standards
2、 The purpose of the safety test
Improve product safety and quality
Try to find security problems and fix them before release to reduce risks
Measure the security level
Verify whether the protection mechanism installed in the system can protect the system in practical application , So that it will not be illegally invaded
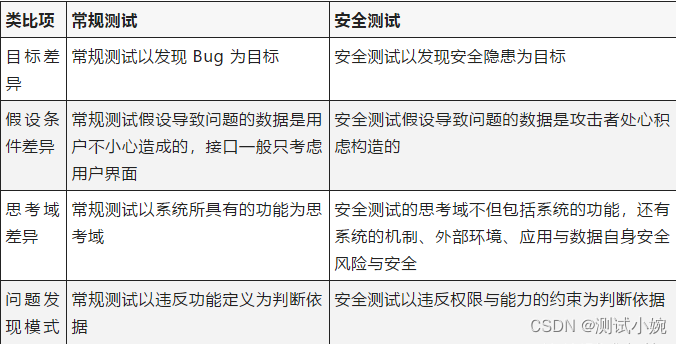
3、 The difference between safety test and routine test
4、 Safety test type
1. Cross site scripts (XSS)
XSS Also called CSS(CROSS SET SCRIPT), Cross-site scripting attacks . It refers to a malicious attacker WEB Insert malicious html Code , When users browse the page , Embedded in it html Code will be executed , So as to achieve the special purpose of malicious users ;( go fishing 、 Stealing cookie、 Manipulate the victim's browser 、 Worm attack )
2. Reflective Cross Station (Reflected XSS)
Server side access http Parameters in the request , Output directly to the client without filtering . If these parameters are scripts , It will execute on the client ( Fishing is common ).
3. Storage type cross station (Stored XSS)
The data entered by the user is stored on the server ( It usually exists in the database ), When other users visit a page , These data are directly output without filtering . This data may be malicious script , Harm to other users .( Hang a horse
common )
In applications that allow uploading files , An attacker uploads a message containing malicious code html perhaps txt file , Users browse these files to execute malicious code ;
Uploading pictures is the most common in general applications , If the picture contains malicious code html perhaps txt file ,, Lower Edition IE When requesting this picture directly , Will ignore Content-Type Execute the code in the picture .
4.DOM cross-site (DOM-Based XSS)
An attacker constructs a code that contains malicious Javascript Of URL, Then entice the user to request this URL. The server did not return malicious after receiving the request Javascript.
Browser processing URL When data in , Execute malicious code .
5. Cross-site request forgery (CSRF)
Force the victim's browser to a vulnerable Web Applications send requests , Finally, achieve the operation behavior required by the attacker .
Malicious requests will bring the browser Cookie. Attacked Web Application trust browser Cookie.
6.SQL Inject
The data entered by the user is used to construct SQL
Query statement , Query sensitive content in the database , Bypass authentication to add 、 Delete 、 Modifying data 、 Denial of service .
7.XML Inject
and SQL The injection principle is the same ,XML It's where the data is stored , When querying or modifying , If you don't escape , Directly input or output data , Will lead to XML Inject holes . Attackers can modify XML data format , Add new XML node , Impact on data processing flow .
8.URL Jump
Web The application received a URL After the parameter , There is no change to the parameters ” Trust URL” Validation of the , Go back to the user's browser and jump to the URL Instructions .( Phishing attack )
9. File systems span
File system ../ On behalf of the parent directory , Through one or more ../ Cross directory restrictions .
10. System commands
The parameters submitted by the user are used to execute the parameters of the system command .
Use ”|” or ”;” Execute multiple orders .
11. Upload files
Web When an application processes a file uploaded by a user , Did not judge whether the file extension is within the allowed range , Or the legality of the contents of the file is not detected , Just save the file on the server , Even upload the script Trojan horse to web Server , Direct control web The server .( The extension is not restricted 、 File contents not checked 、 Virus files )
12. Download any file
Download attachments and other functions
Apache The virtual directory points to
Java/PHP Read the file
Download database configuration file, etc
Directory browsing
13. Access control
Do you have permission to
Some systems do not require permission control
Have you set permissions
With a powerful authority system , But it's not used
Is there any authority to cut corners
URL Level
Menu level
14. Access control
Horizontal authority
Web The application received a user request , When modifying a piece of data , There's no one to judge who the data belongs to , Or judge who the data belongs to , Submitted from the user request Parameters ( User controlled data ) in , Get who the data belongs to id, A malicious attacker can transform the data ID, Or change who you belong to id, Modify data that does not belong to you .
Vertical permissions
because web The application does not do permission control , Or just do permission control on the menu , As a result, malicious users only need to guess the properties of other management pages URL, You can access or control data or pages owned by other roles , Achieve the purpose of authority promotion .
15.Session Expires
Session expiration,
The browser is out of date
The server 30 Minutes no action expired
The server 24 Hours mandatory expiration
Keep talking
5、 Safety test tools
AppScan
A security vulnerability scanning tool , It's quite so " Explore " and " test " The process of , Finally, a very intuitive test report is generated , It is helpful for R & D personnel to analyze and repair
Official website :https://www.ibm.com/developerworks/downloads/r/appscan/
BurpSuite
A necessary integrated penetration testing tool for information security practitioners , It uses automatic test and semi-automatic test , Contains Proxy,Spider,Scanner,Intruder,Repeater,Sequencer,Decoder,Comparer And so on ;
Proxy Function can intercept HTTP/S Proxy server for ( Mobile phones and web);
Spide function - Intelligent sensing web crawler ;
Intruder Functions can be web Automated attacks on Applications , Very suitable for safety testing .
By intercepting HTTP/HTTPS Of web Data packets , Act as a middleman for browsers and related applications , To intercept 、 modify 、 Replay packets for testing .
Official website :https://portswigger.net/burp/
Nmap
A network connection end scanning software , It is used to scan the open network connection of online computers . Determine which services are running on which connections .
Official website :https://nmap.org/
sqlmap
An open source penetration testing tool , It can be used for automatic detection , utilize SQL Inject holes , Get database server permissions . It has a powerful detection engine , Function options of penetration testing for different types of databases , Including getting the data stored in the database , Accessing operating system files can even execute operating system commands through an external data connection .
Official website :http://sqlmap.org/,

边栏推荐
- Capitalize the title of leetcode simple question
- STC-B学习板蜂鸣器播放音乐2.0
- pytest
- 接口测试面试题及参考答案,轻松拿捏面试官
- Detailed introduction to dynamic programming (with examples)
- China's county life record: go upstairs to the Internet, go downstairs' code the Great Wall '
- Global and Chinese markets for complex programmable logic devices 2022-2028: Research Report on technology, participants, trends, market size and share
- Don't you even look at such a detailed and comprehensive written software test question?
- ucore lab6 调度器 实验报告
- Should wildcard import be avoided- Should wildcard import be avoided?
猜你喜欢
Threads and thread pools
Don't you even look at such a detailed and comprehensive written software test question?
ucore lab5用户进程管理 实验报告

Capitalize the title of leetcode simple question
软件测试行业的未来趋势及规划
软件测试面试回答技巧
MySQL数据库(一)
Stc-b learning board buzzer plays music

Rearrange spaces between words in leetcode simple questions
Fundamentals of digital circuits (II) logic algebra
随机推荐
The latest query tracks the express logistics and analyzes the method of delivery timeliness
Threads and thread pools
Capitalize the title of leetcode simple question
Stc-b learning board buzzer plays music
MySQL数据库(三)高级数据查询语句
ucore lab5用户进程管理 实验报告
MySQL数据库(四)事务和函数
Install and run tensorflow object detection API video object recognition system of Google open source
Contest3145 - the 37th game of 2021 freshman individual training match_ A: Prizes
Réponses aux devoirs du csapp 7 8 9
Iterators and generators
Statistics 8th Edition Jia Junping Chapter 2 after class exercises and answer summary
Heap, stack, queue
Leetcode simple question: check whether the numbers in the sentence are increasing
ucore lab8 文件系统 实验报告
Global and Chinese market of maleic acid modified rosin esters 2022-2028: Research Report on technology, participants, trends, market size and share
Global and Chinese markets of cobalt 2022-2028: Research Report on technology, participants, trends, market size and share
安全测试入门介绍
[oiclass] share prizes
Fundamentals of digital circuits (I) number system and code system