当前位置:网站首页>AAAI2022 | Word Embeddings via Causal Inference: Gender Bias Reducing and Semantic Information Preserving
AAAI2022 | Word Embeddings via Causal Inference: Gender Bias Reducing and Semantic Information Preserving
2022-07-04 03:36:00 【Zhiyuan community】

Address of thesis :https://arxiv.org/pdf/2112.05194.pdf
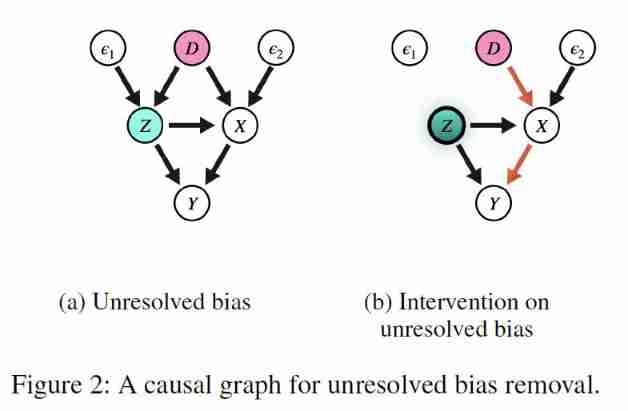
Word vectors are widely used in various naturallanguageprocessing tasks , However, many studies have shown that there are various biases in word vectors ( Such as gender or race ). This paper presents a method based on causal reasoning , It can effectively eliminate gender bias in word vectors and retain other semantics . Specifically , This paper proposes two causal reasoning frameworks , Respectively used to eliminate Potential proxy bias and Unresolved bias. Experiments show that , The word vector obtained by this method can not only better eliminate the bias in the word vector , It can also improve the performance of semantic related tasks .

边栏推荐
- Defensive programming skills
- Tsinghua University product: penalty gradient norm improves generalization of deep learning model
- 1day vulnerability pushback skills practice (3)
- Management and thesis of job management system based on SSM
- JSON string conversion in unity
- system information
- functools下的reduce函数
- Es network layer
- Contest3145 - the 37th game of 2021 freshman individual training match_ D: Ranking
- Formulaire day05
猜你喜欢

Li Chuang EDA learning notes IX: layers

渗透实战-SQLServer提权

New year's first race, submit bug reward more!

Why is it recommended that technologists write blogs?

Development of digital collection trading platform development of digital collection platform

1day vulnerability pushback skills practice (3)

Add token validation in swagger

Nbear introduction and use diagram
![[Wu Enda deep learning] beginner learning record 3 (regularization / error reduction)](/img/e9/818bdfeae766dca7d2318b52b4424d.jpg)
[Wu Enda deep learning] beginner learning record 3 (regularization / error reduction)
Package and download 10 sets of Apple CMS templates / download the source code of Apple CMS video and film website
随机推荐
What kind of experience is it when the Institute earns 20000 yuan a month!
What is cloud primordial?
What is the difference between enterprise wechat applet and wechat applet
渗透实战-guest账户-mimikatz-向日葵-sql提权-离线解密
Unity writes a character controller. The mouse controls the screen to shake and the mouse controls the shooting
[source code analysis] model parallel distributed training Megatron (5) -- pipestream flush
Day05 錶格
How to use websocket to realize simple chat function in C #
Contest3145 - the 37th game of 2021 freshman individual training match_ E: Eat watermelon
数据库SQL语句汇总,持续更新......
system information
National standard gb28181 protocol platform easygbs fails to start after replacing MySQL database. How to deal with it?
Webhook triggers Jenkins for sonar detection
[PaddleSeg 源码阅读] PaddleSeg Transform 的 Normalize操作
1day vulnerability pushback skills practice (3)
Why is it recommended that technologists write blogs?
Leetcode51.n queen
Redis notes (I) Linux installation process of redis
Solve the problems encountered by the laravel framework using mongodb
[untitled]