当前位置:网站首页>The top half and bottom half of the interrupt are introduced and the implementation method (tasklet and work queue)
The top half and bottom half of the interrupt are introduced and the implementation method (tasklet and work queue)
2022-07-04 17:43:00 【Snail taking off】
1、 Considerations for interrupt handlers
(1) In interrupt context , Cannot interact with user space data , Because it may cause sleep or blocking ;
(2) It cannot be handed over before the procedure is completed CPU, Can't sleep , You can't schedule;
(3) Interrupt handlers should be as short as possible , The longer it takes, the worse the response performance ;
(4) The interrupt handler is different from the general handler , Interrupt handlers do not participate in scheduling , So once handed over CPU Will no longer be scheduled ;
2、 Why is the interruption divided into the top half and the bottom half
(1) Interrupt handlers need to do a certain amount of work , Among them, the interrupt handler may soon complete the work to be processed , The work to be completed may also be time-consuming ;
(2) Interrupt handlers prohibit interrupts during execution , Therefore, the interrupt handler should end as soon as possible, and the interrupt blocking time should not be too long , Otherwise, it may cause interrupt loss ;
(3) When the task to be handled by the interrupt handler is objectively time-consuming , There is a contradiction between work and speed , On the one hand, the task itself is time-consuming , On the one hand, time-consuming will lead to slower interrupt response ;
(4) For the third case , So the interruption is divided into upper and lower parts , Put unnecessary but necessary operations on the top half , Put the time-consuming operation in the lower half of the interrupt , Then the upper half calls the lower half ;
3、 Interrupt the top half and bottom half processing principles
(1) Put a very small number of tasks that must be processed immediately into the top half of the interrupt , At this time, you need to shield your own interrupts of the same type , Due to the small number of tasks , So you can handle urgent tasks quickly and undisturbed ;
(2) Put less urgent tasks that need to consume a lot of events into the bottom half of the interruption ;
4、 Interrupt the top half and bottom half
4.1、 The selection principle of the two methods
(1) A medium number of urgent tasks that require less time are placed on tasklet in . No interrupts are masked at this time ( Include interrupts of the same type as your top half ), Therefore, it will not affect the top half's handling of emergency affairs ; At the same time, there will be no user process scheduling , So as to ensure that their urgent tasks can be completed quickly .
(2) It takes more time and is not urgent ( Allow to be deprived of running rights by the operating system ) A large number of tasks are placed on workqueue in . At this point, the operating system will handle this task as quickly as possible , But if the task is too large , During this period, the operating system will also have the opportunity to schedule other user processes to run , This ensures that other user processes will not be unable to run because this task requires running time .
(3) Tasks that may cause sleep are placed in workqueue in . Because in workqueue Sleep is safe . When you need to get a lot of memory 、 When the semaphore needs to be acquired , When you need to perform blocking I/O In operation , use workqueue Very suitable .
summary :tasklet Deal with the bottom half that takes relatively less time , Operation is atomic , It must be run at one time , Can't give up CPU, Can't sleep , But it's fast ; The bottom half of the work queue takes a long time to process , Participate in system mobilization , You can give up CPU You can also sleep ;
4.2、tasklet Sample code
// Interrupt processing bottom half
void func(unsigned long data)
{
int flag;
printk("key-s5pv210: this is bottom half\n");
s3c_gpio_cfgpin(S5PV210_GPH0(2), S3C_GPIO_SFN(0x0)); // input Sister in law ″ Spin
flag = gpio_get_value(S5PV210_GPH0(2));
s3c_gpio_cfgpin(S5PV210_GPH0(2), S3C_GPIO_SFN(0x0f)); // eint2 Sister in law ″ Spin
input_report_key(button_dev, KEY_LEFT, !flag);
input_sync(button_dev);
}
// Definition tasklet And bind the lower half of the interrupt
DECLARE_TASKLET(mytasklet, func, 0);
// The top half of the interrupt handler
static irqreturn_t button_interrupt(int irq, void *dummy)
{
// Do something necessary to interrupt
printk("key-s5pv210: this is top half\n");
// Call the bottom half of the interrupt
tasklet_schedule(&mytasklet);
return IRQ_HANDLED;
}
// Bind interrupt handler
request_irq(BUTTON_IRQ, button_interrupt, IRQF_TRIGGER_FALLING | IRQF_TRIGGER_RISING, "button-x210", NULL);
4.3、 Work queue example code
// Interrupt processing bottom half
void func(unsigned long data)
{
int flag;
printk("key-s5pv210: this is bottom half\n");
s3c_gpio_cfgpin(S5PV210_GPH0(2), S3C_GPIO_SFN(0x0)); // input Sister in law ″ Spin
flag = gpio_get_value(S5PV210_GPH0(2));
s3c_gpio_cfgpin(S5PV210_GPH0(2), S3C_GPIO_SFN(0x0f)); // eint2 Sister in law ″ Spin
input_report_key(button_dev, KEY_LEFT, !flag);
input_sync(button_dev);
}
// Define the work queue and bind the bottom half of the interrupt
DECLARE_WORK(mywork, func);
// The top half of the interrupt handler
static irqreturn_t button_interrupt(int irq, void *dummy)
{
// Do something necessary to interrupt
printk("key-s5pv210: this is top half\n");
// Call the bottom half of the interrupt
schedule_work(&mywork);
return IRQ_HANDLED;
}
// Bind interrupt handler
request_irq(BUTTON_IRQ, button_interrupt, IRQF_TRIGGER_FALLING | IRQF_TRIGGER_RISING, "button-x210", NULL);
边栏推荐
- Great Wall Securities security does not open a securities account
- Win32 API access route encrypted web pages
- Offline and open source version of notation -- comprehensive evaluation of note taking software anytype
- Internet addiction changes brain structure: language function is affected, making people unable to speak neatly
- Web game engine
- High school physics: force, object and balance
- 什么是低代码开发?
- Kunming Third Ring Road Closure project will pass through these places. Is there one near your home?
- Is it safe for CITIC Securities to open an account online? Is the account opening fee charged
- Wuzhicms code audit
猜你喜欢
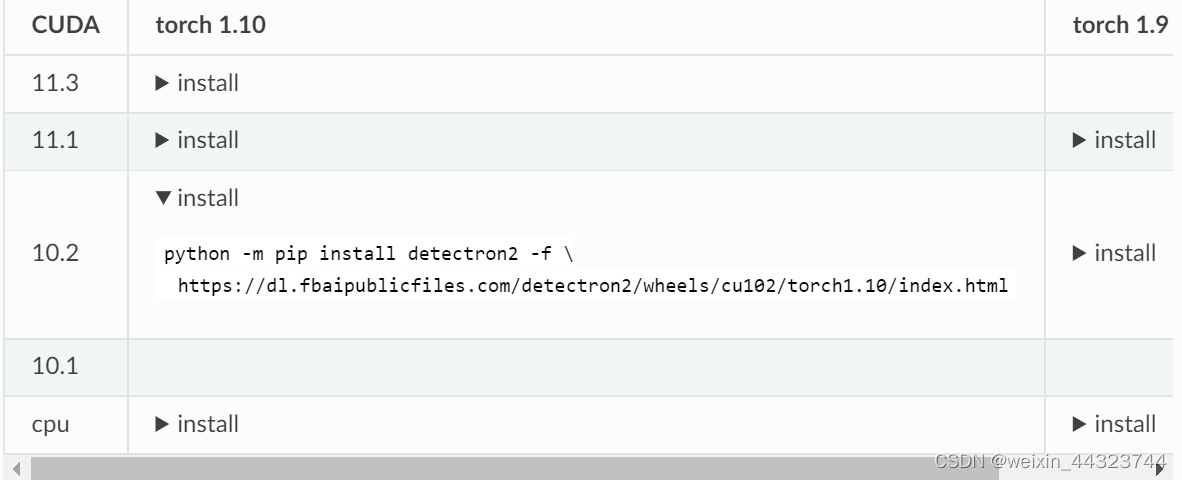
Detectron2 installation method
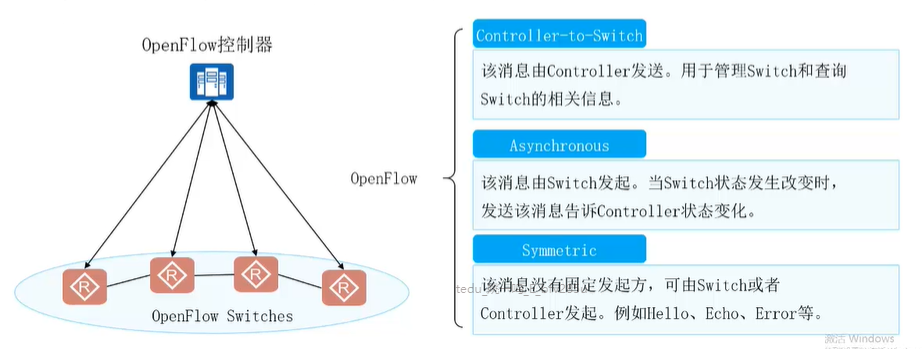
【华为HCIA持续更新】SDN与FVC
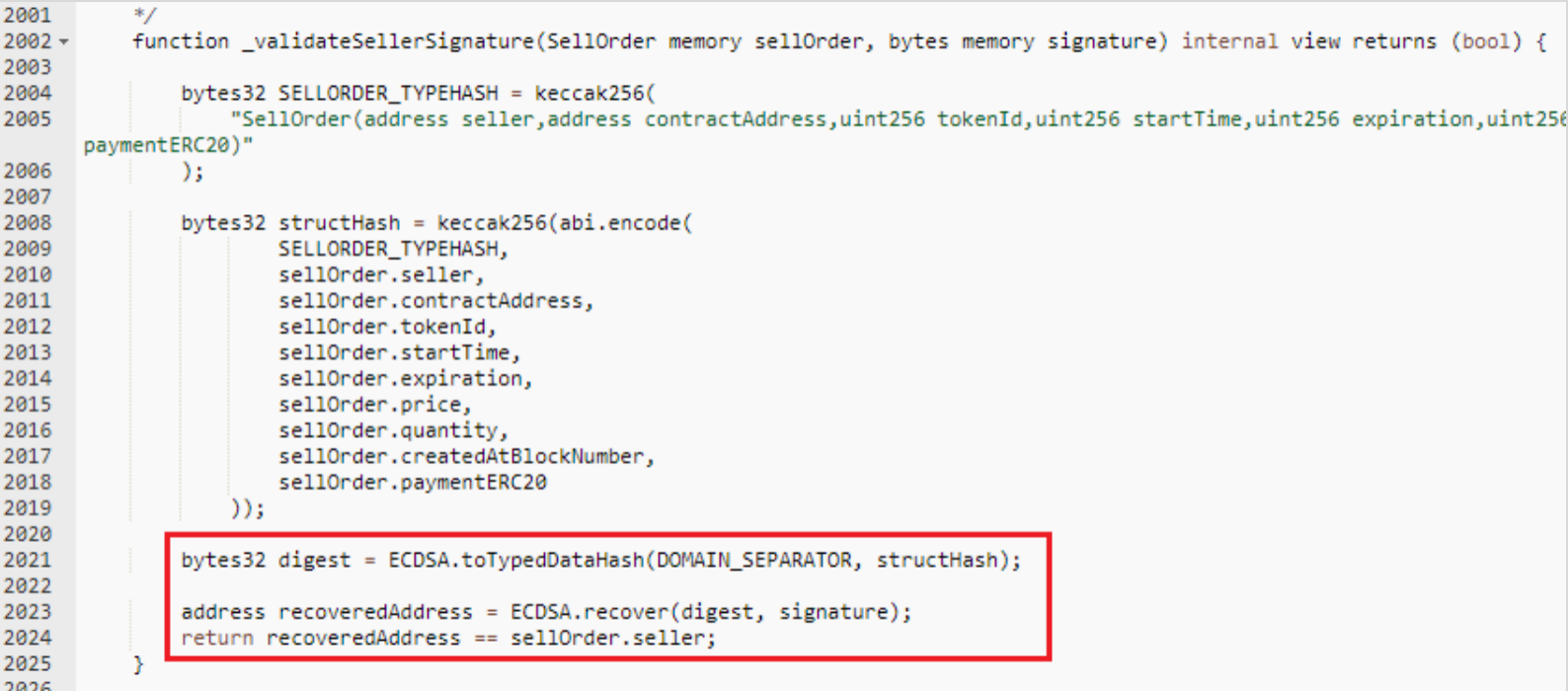
NFT流动性市场安全问题频发—NFT交易平台Quixotic被黑事件分析
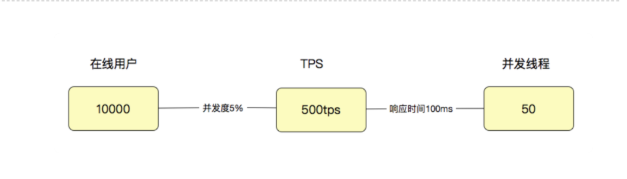
PingCode 性能测试之负载测试实践
【HCIA持续更新】WLAN工作流程概述
超标量处理器设计 姚永斌 第6章 指令解码 摘录

NFT liquidity market security issues occur frequently - Analysis of the black incident of NFT trading platform quixotic

我写了一份初学者的学习实践教程!
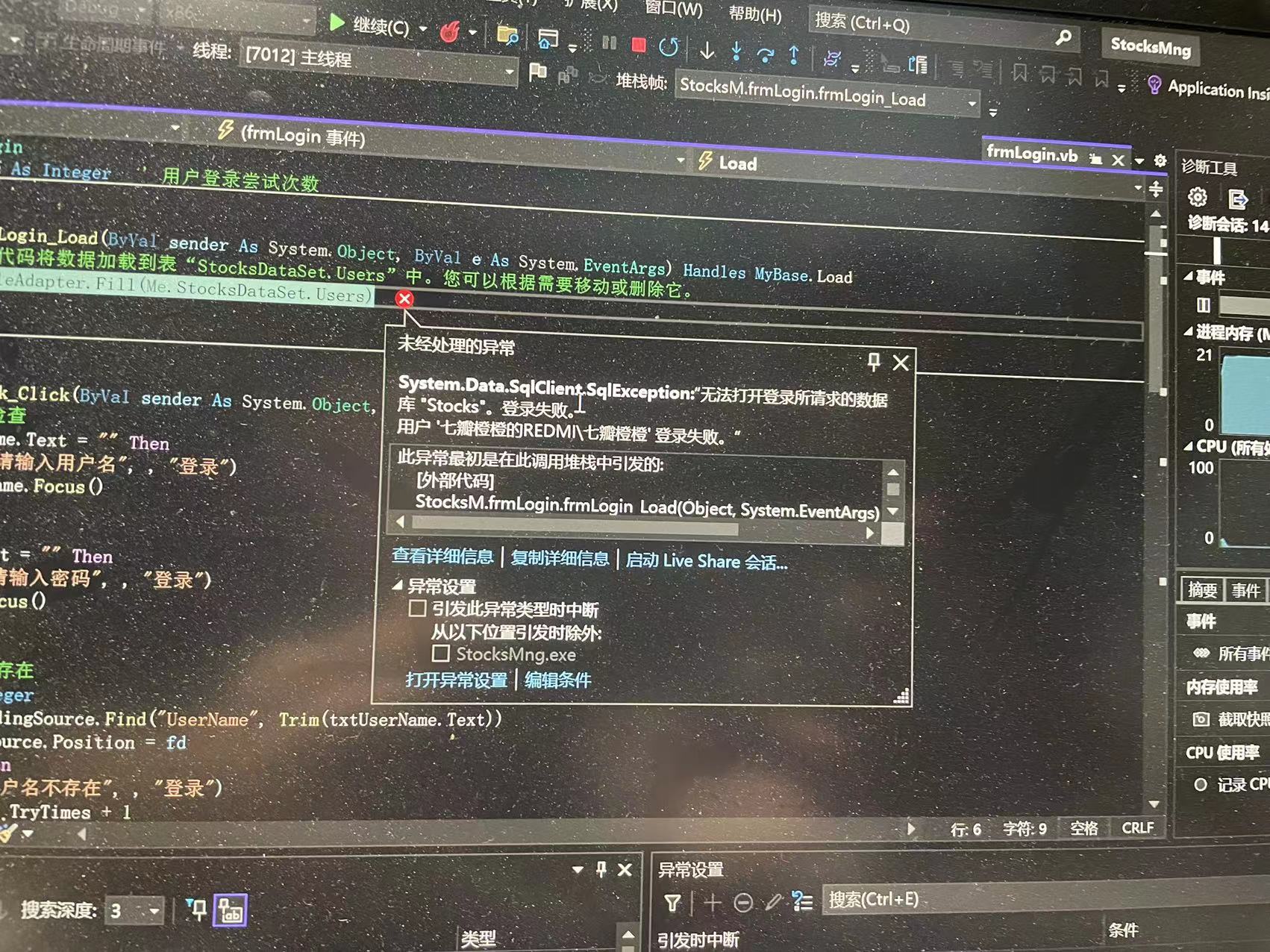
VB cannot access database stocks
DataKit——真正的统一可观测性 Agent
随机推荐
Master the use of auto analyze in data warehouse
Go micro tutorial - Chapter 2 go micro V3 using gin and etcd
shell脚本的替换功能实现
开发者,MySQL专栏完更,助你轻松从安装到入门进阶
【HCIA持续更新】WLAN概述与基本概念
数学分析_笔记_第7章:多元函数的微分学
detectron2安装方法
Superscalar processor design yaoyongbin Chapter 7 register rename excerpt
MVC模式和三层架构
7 RSA Cryptosystem
斑马识别成狗,AI犯错的原因被斯坦福找到了丨开源
Is it safe for Great Wall Securities to open an account? How to open a securities account
The 18th IET AC / DC transmission International Conference (acdc2022) was successfully held online
Vb无法访问数据库stocks
Internet addiction changes brain structure: language function is affected, making people unable to speak neatly
Two methods of MD5 encryption
中断的顶半部和底半部介绍以及实现方式(tasklet 和 工作队列)
【每日一题】556. 下一个更大元素 III
[system analyst's road] Chapter 7 double disk system design (structured development method)
What if Kaili can't input Chinese???