当前位置:网站首页>Redis avalanche, penetration, breakdown
Redis avalanche, penetration, breakdown
2022-07-02 12:37:00 【Squat in the corner and count the ants】
One 、 Cache avalanche :
Concept :
Cache avalanche refers to the cache key Mass to expiration time , At this time, a large number of requests call at the same time , Causes database pressure to be too big even down machine
Examples in actual production :
Take the second kill as an example ,QPS achieve 5000, At this time , If this 5000 Requests are accessed at the same time , stay redis When the cache of is not invalidated , This magnitude of qps,redis It's bearable .
But if , be-all key It all fails at a certain point in time , And the background hasn't had time to brush the cache again ( The cache is usually refreshed when the scheduled task actively refreshes or modifies ), Then at this time , All requests will be directly entered MySQL database .
As you can imagine ,MySQL It's basically unbearable , And it doesn't work to restart , Because your restart speed can never keep up with the user refresh speed .
This phenomenon is called cache avalanche .
Solution :
1、 in the light of key Cache avalanche caused by simultaneous failure
We usually set key when , Should avoid key The expiration time of is the same , You can set key Valid period of , Add a random number , Refresh the data at the same time key The validity period of is set to different ( For example, hundreds of milliseconds to tens of seconds ).
Of course , You can also use the scheme of data preheating , Before a large concurrent access is about to occur , Manually trigger cache different key, Set different expiration times , Make the cache failure time as uniform as possible .
2、 in the light of redis Cache middleware suddenly hangs , The resulting cache avalanche
For small businesses , We can use redis Of sentinel Sentinel mechanism ;
For large businesses , We can use redis Of cluster Cluster solution to deal with .
Whether it's sentinel、 still cluster, All of them have complete automatic failover , about master All of a sudden , It will not affect the normal operation of the business .
Two 、 Cache penetration
Concept :
Cache penetration , It refers to that malicious attackers frequently query data that must not exist in a database .
Cache miss , It will send the request to the database , The database does not have this data , It will not store the data in the cache , This leads to the same request , Always requested , In fact, it's not a cache , Instead, request directly to the database .
At this time , If someone takes advantage of what doesn't exist key Frequently request our application interface , And the magnitude is very large , This will make the storage tier database unbearable , You may die .
Examples in actual production :
For example, there is an interface ,www.haveyb.com/getProductInfo?product_id=109&porduct_type=2,
In normal use , If you request a nonexistent data , such as product_id = 999999999, In fact, this data does not exist in the database , But there is such a malicious attacker , Take this data , Ask you frequently , It's OK when requests come one by one .
But what if tens of thousands of concurrent calls come at the same time ? After you actually miss the cache , All the requests have been sent to the database , But the database does not have this data , You can't put the data in the cache , The result is that requests continue to hit the database , In fact, the database cannot withstand such a large concurrency , It will cause the database to hang up .
This is buffer penetration .
Solution :
1、 Whether the data actually exists or not , We all store this key in the cache ( The validity period should be set shorter , For example, one to three minutes ), Then set the value to a specific value , If the result obtained in the business is this specific value , It will report an error and return .
2、 Another solution is to use redis The bloom filter (Bloom Filter), Hash all possible data to a large enough bitmap in , A certain nonexistent data will be This bitmap Intercept , Thus, the query pressure on the underlying storage system is avoided .
3、 ... and 、 Cache breakdown
1、 Concept
Buffer breakdown refers to a Key Very hot , Constantly carrying big concurrency , Large concurrent centralized access to this point , When this Key At the moment of failure , Continuous large concurrency breaks through the cache , Request directly to the database , At this time , A large amount of concurrency may directly hang up the database .
notes : The most essential difference between cache breakdown and cache avalanche is
Cache avalanche is due to a large number of key At the same time , Cause all requests to directly call the database at the same time , Cause the database to hang up ;
Cache breakdown is due to a hot spot key invalid , Requests that have been blocked by the cache before , Send directly to the database , Cause the database to hang up .
Examples in production :
We have an interface to get the background settings of the merchant system , The cache to redis in , This interface , Other services are called at all times , Such as the order 、 goods 、 Inventory module .
Originally , This data exists in the cache , All requests are blocked by the cache , It's no problem , But if this key Suddenly expired , Then this hot request will be directly called to the database , In the case of large concurrency , Maybe the database will hang up .
Solution :
1、 Set the data to never expire ( Update only , Do not delete or expire )
2、 For the key Of value Set a timeout value internally , When accessing , It is found that the timeout value has been reached , Just update the cache , And reset the timeout value ( For this key, It can be set not to expire , Or the timeout value is less than the expiration time set externally )
$key = 'system_setting_106976';
$timestamp = time();
$data = [
'value' => 12345678,
'timeout' => $time
];
setnx($key, $data, $time + 360);边栏推荐
- Post request body content cannot be retrieved repeatedly
- Interview with meituan, a 34 year old programmer, was rejected: only those under the age of 30 who work hard and earn little overtime
- drools决策表的简单使用
- Bom Dom
- 2.7 binary tree, post order traversal - [FBI tree]
- Heap (priority queue)
- 倍增 LCA(最近公共祖先)
- Lekao: 22 year first-class fire engineer "technical practice" knowledge points
- IPhone 6 plus is listed in Apple's "retro products" list
- WSL 2 will not be installed yet? It's enough to read this article
猜你喜欢
![[ybtoj advanced training guidance] cross the river [BFS]](/img/4e/83f14452ea6410768cdd01e725af2e.jpg)
[ybtoj advanced training guidance] cross the river [BFS]

计数类DP AcWing 900. 整数划分
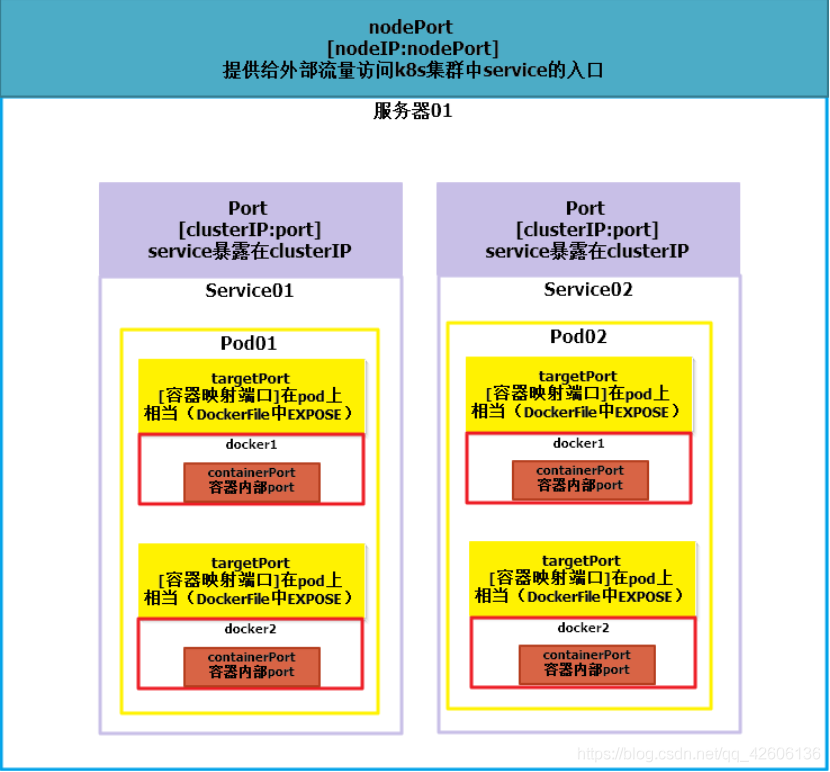
The differences and relationships among port, targetport, nodeport and containerport in kubenetes

趣味 面试题
China traffic sign detection data set
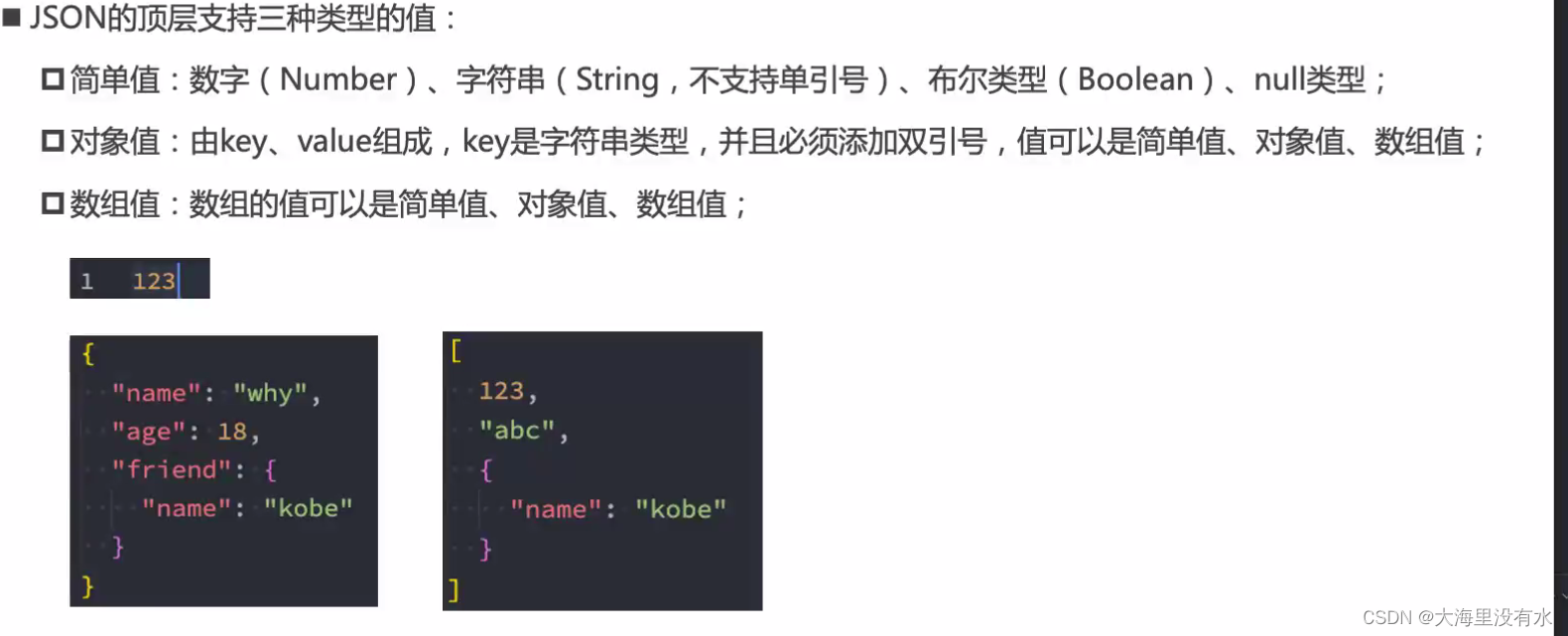
JSON序列化 与 解析

arcgis js 4.x 地图中加入图片
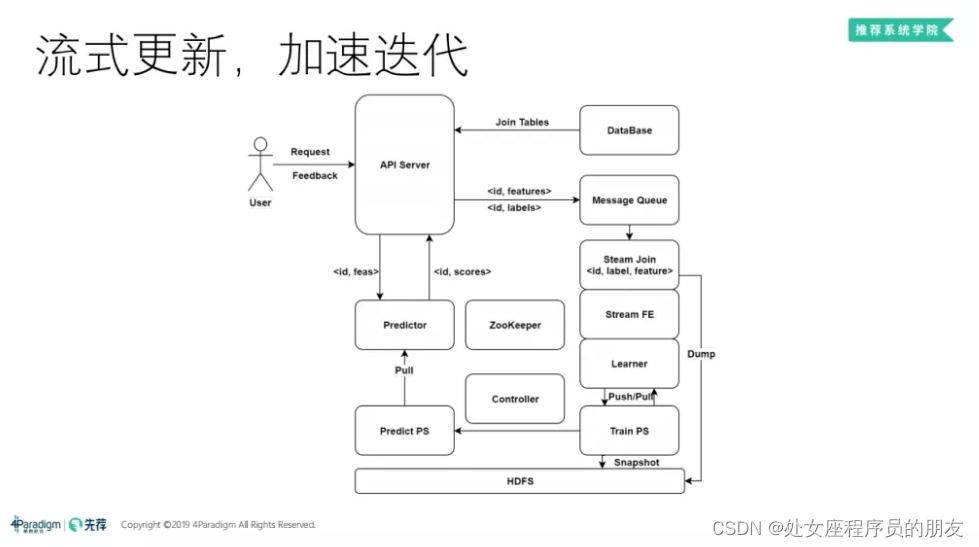
分布式机器学习框架与高维实时推荐系统
Programmers can't find jobs after the age of 35? After reading this article, you may be able to find the answer
PR 2021 quick start tutorial, learn about the and functions of the timeline panel
随机推荐
drools执行String规则或执行某个规则文件
Simple understanding of ThreadLocal
Fluent fluent library encapsulation
CDH存在隐患 : 该角色的进程使用的交换内存为xx兆字节。警告阈值:200字节
"As a junior college student, I found out how difficult it is to counter attack after graduation."
Jenkins user rights management
排序---
Jenkins voucher management
[I'm a mound pytorch tutorial] learning notes
寻找二叉树中任意两个数的公共祖先
BOM DOM
Experiment of connecting mobile phone hotspot based on Arduino and esp8266 (successful)
记录一下MySql update会锁定哪些范围的数据
Input a three digit number and output its single digit, ten digit and hundred digit.
AI中台技术调研
Lombok common annotations
drools执行指定的规则
Discrimination of the interval of dichotomy question brushing record (Luogu question sheet)
Why do programmers have the idea that code can run without moving? Is it poisonous? Or what?
Differences between nodes and sharding in ES cluster