当前位置:网站首页>Patch NTP server at the beginning of DDoS counterattack
Patch NTP server at the beginning of DDoS counterattack
2022-07-06 02:31:00 【zy18165754120】
According to the DDoS Defense company NSFOCUS call ,IT The industry seems to be right 2014 Relevant at the beginning of the year DDoS The warning of amplifying the increasing risk of attack has responded well , Patched a large number of vulnerable servers .
The US provider announced on Tuesday New statistics , call 3 Global vulnerability in January NTP The number of servers is about 21,000 platform ,5 The month fell again to 17,600 platform . This is lower than 2013 year 12 Of the month 432,120 people .
however , The system administrator still needs to finish the work . The report also claims that , It can enlarge the flow 700 Times more NTP The number of amplifiers has increased from 12 Of the month 1,224 One added to today's 2,100 individual .
“US-CERT And network time protocol strongly recommend that system administrators ntpd Upgrade to 4.2.7p26 Or later ,”NSFOCUS say .
“4.2.7p26 Users of earlier versions should use noquery To block all status queries , Or use disable monitor To disable ntpdc –c monlist command , At the same time, other status queries are still allowed .”
As early as 1 month , The United States CERT Just warn , Using public server NTP Zoom in DDoS The threat of attack is growing .
If it's not properly protected , The global NTP The ubiquity of servers makes them potentially dangerous agents for such attacks . A series of connected devices are used NTP To synchronize their clocks .
Attackers can get through “monlist” Query the last of the requests to connect to the server 600 individual IP List of addresses , Thus, it is quite easy to take advantage of open NTP The server .
Then what they need to do is disguise the source address as the victim's source address , Overwhelm them by sending a large number of results IT System .
Suggest upgrading to a new one NTP Version will be automatically disabled monlist function .
Network security company Incapsula stay 3 A project released in September DDoS Threat situation Research Show , since 1 Since the month ,NTP Amplification attacks have undergone a major shift , Maximum attack reached 180Gbps.
边栏推荐
- [Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 12
- 剑指 Offer 30. 包含min函数的栈
- Use the list component to realize the drop-down list and address list
- Dachang image library
- 2022 edition illustrated network pdf
- 3D drawing ()
- Global and Chinese markets of screw rotor pumps 2022-2028: Research Report on technology, participants, trends, market size and share
- Prepare for the autumn face-to-face test questions
- Minecraft 1.18.1、1.18.2模组开发 22.狙击枪(Sniper Rifle)
- MySQL (IV) - transactions
猜你喜欢
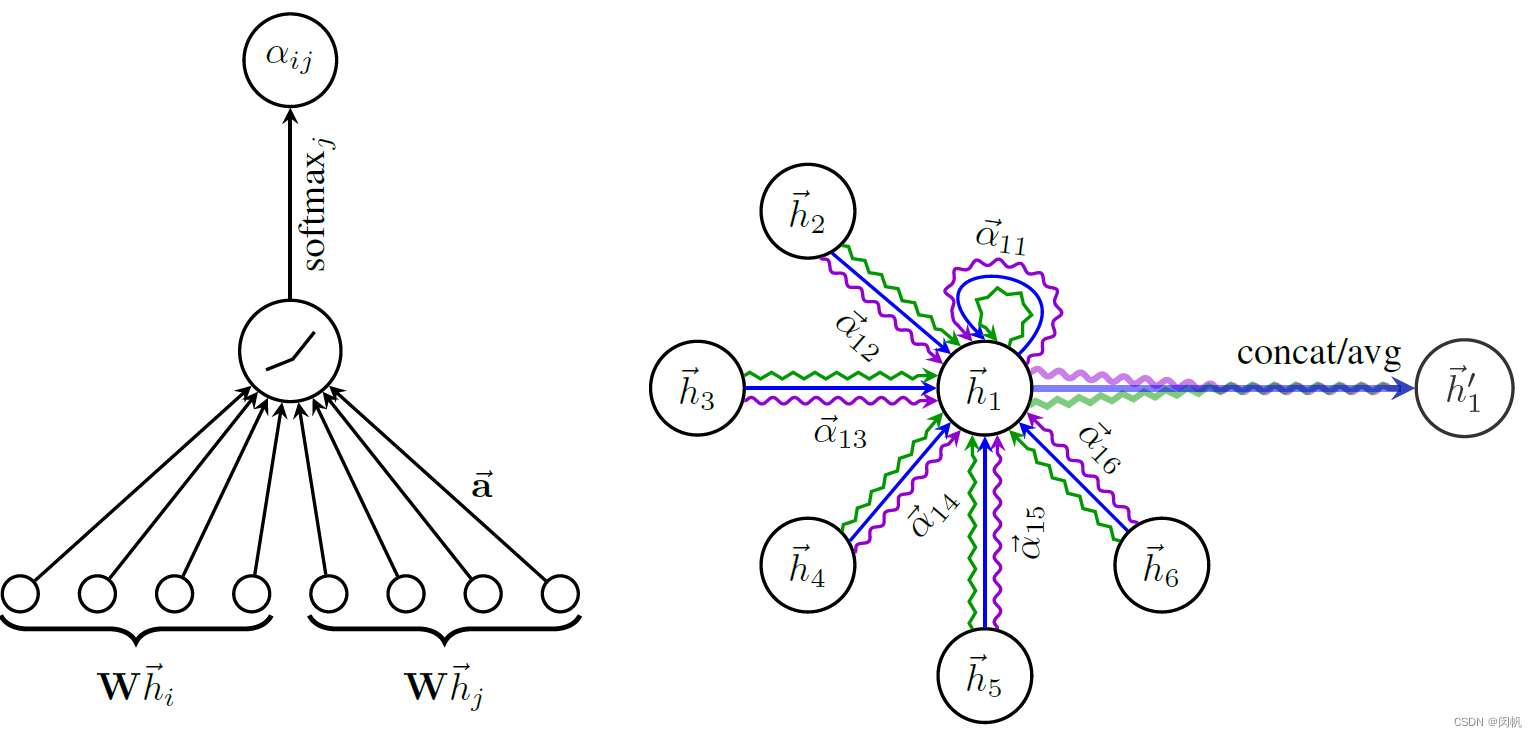
Paper notes: graph neural network gat
ReferenceError: primordials is not defined错误解决
![[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 23](/img/72/a80ee7ee7b967b0afa6018070d03c9.jpg)
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 23
![[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 16](/img/c3/f3746b161012acc3751b2bd0b8f663.jpg)
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 16
![[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 15](/img/72/0fe9cb032339d5f1ccf6f6c24edc57.jpg)
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 15
![[Wu Enda machine learning] week5 programming assignment EX4 - neural network learning](/img/37/83953c24ec141667b304f9dac440f1.jpg)
[Wu Enda machine learning] week5 programming assignment EX4 - neural network learning
![[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 11](/img/6a/398d9cceecdd9d7c9c4613d8b5ca27.jpg)
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 11
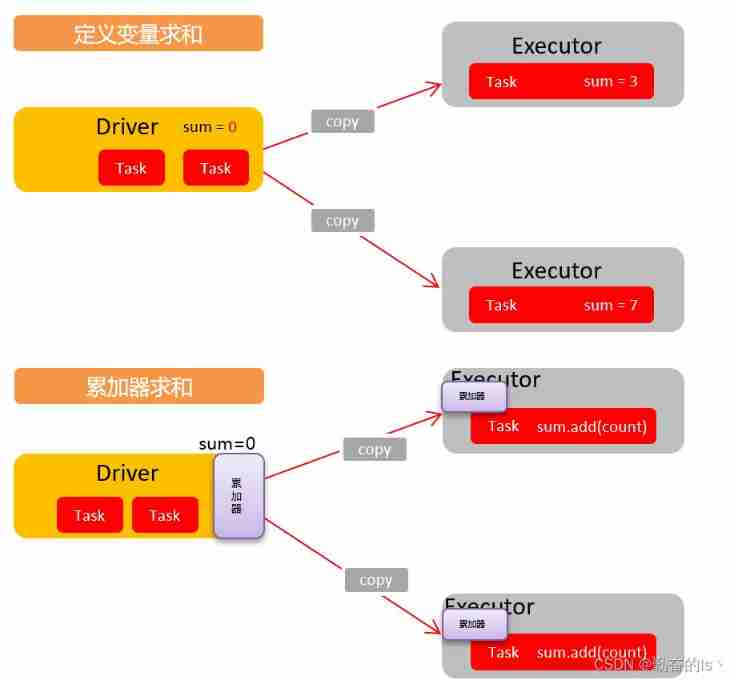
Spark accumulator
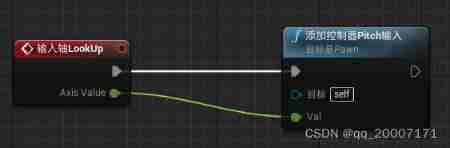
Ue4- how to make a simple TPS role (II) - realize the basic movement of the role
![[untitled] a query SQL execution process in the database](/img/de/700ee20934fc2cd4a019f761148ef9.png)
[untitled] a query SQL execution process in the database
随机推荐
MySQL lethal serial question 1 -- are you familiar with MySQL transactions?
High number_ Vector algebra_ Unit vector_ Angle between vector and coordinate axis
Redis installation
Lecture 4 of Data Engineering Series: sample engineering of data centric AI
Blue Bridge Cup group B provincial preliminaries first question 2013 (Gauss Diary)
SQL table name is passed as a parameter
继承的构造函数
Structural theme model (I) STM package workflow
[community personas] exclusive interview with Ma Longwei: the wheel is not easy to use, so make it yourself!
Advanced technology management - what is the physical, mental and mental strength of managers
零基础自学STM32-野火——GPIO复习篇——使用绝对地址操作GPIO
一位博士在华为的22年
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 20
Global and Chinese market of wheelchair climbing machines 2022-2028: Research Report on technology, participants, trends, market size and share
2022 eye health exhibition, vision rehabilitation exhibition, optometry equipment exhibition, eye care products exhibition, eye mask Exhibition
The ECU of 21 Audi q5l 45tfsi brushes is upgraded to master special adjustment, and the horsepower is safely and stably increased to 305 horsepower
[robot library] awesome robots Libraries
Déduisez la question d'aujourd'hui - 729. Mon emploi du temps I
Bigder: I felt good about the 34/100 interview, but I didn't receive the admission
MySQL winter vacation self-study 2022 11 (6)