当前位置:网站首页>How to recover the information server and how to recover the server data [easy to understand]
How to recover the information server and how to recover the server data [easy to understand]
2022-07-05 12:14:00 【Full stack programmer webmaster】
Hello everyone , I meet you again , I'm your friend, Quan Jun .
The original title : The server data How to recover
How to recover server data ? Speaking of server data recovery , Many laymen may not understand . The so-called server data recovery , First, we need to split and explain . What is server data ? Xiaobian's explanation to you is : The information on the server storage medium can be collectively referred to as server data . that , Under what circumstances do you need server data recovery ? The premise of server data recovery is that the server data is damaged . What is data corruption ? Unexpected changes in data information are damage or data corruption ! So don't worry if the server is damaged , The data lost in the server can be recovered through professional data recovery technology . that , For server data recovery , Next, our Aite data recovery center gives a specific actual case , For your detailed analysis .
Server media information of server data recovery :
Dell PowerEdge 2600 The server , The server consists of three SCSI Interface server hard disk composition , Single disc is 36GB, At present, there are fewer and fewer , Gradually SAS Hard disk replaces .
Fault detection of server data recovery :
After inspection, it was found that none of the three hard disks was damaged to a large extent , One of the hard disks has some bad sectors ,RAID The cause of the crash is probably due to the instability of the controller or I/O The passage is blocked, causing .
Data recovery process of server data recovery :
First of all, make a complete disk clone of the three hard disks , The capacity of a single disk is relatively small , The cloning time is about 40 About minutes . After cloning , Analyze the underlying data of the three hard disks , Then the virtual tools are used to recombine the disk array data , Extract the data . After the data extraction is completed , Verify important internal database files , Successfully attached , The data in the database table is normal , Data recovery 100% success .
The above case analysis seems simple , However, the actual data recovery technicians gradually recover professionally through complex data recovery methods , This process is not something that I can explain clearly in a few simple words .
Publisher : Full stack programmer stack length , Reprint please indicate the source :https://javaforall.cn/149170.html Link to the original text :https://javaforall.cn
边栏推荐
- Course design of compilation principle --- formula calculator (a simple calculator with interface developed based on QT)
- 自动化测试生命周期
- Pytorch MLP
- [mainstream nivida graphics card deep learning / reinforcement learning /ai computing power summary]
- byte2String、string2Byte
- Yolov5 target detection neural network -- calculation principle of loss function
- Matlab struct function (structure array)
- How to clear floating?
- 2022年国内云管平台厂商哪家好?为什么?
- Halcon template matching actual code (I)
猜你喜欢
Wireless WiFi learning 8-channel transmitting remote control module
![[mainstream nivida graphics card deep learning / reinforcement learning /ai computing power summary]](/img/1a/dd7453bc5afc6458334ea08aed7998.png)
[mainstream nivida graphics card deep learning / reinforcement learning /ai computing power summary]
Mongodb replica set
Matlab superpixels function (2D super pixel over segmentation of image)
Pytorch MLP
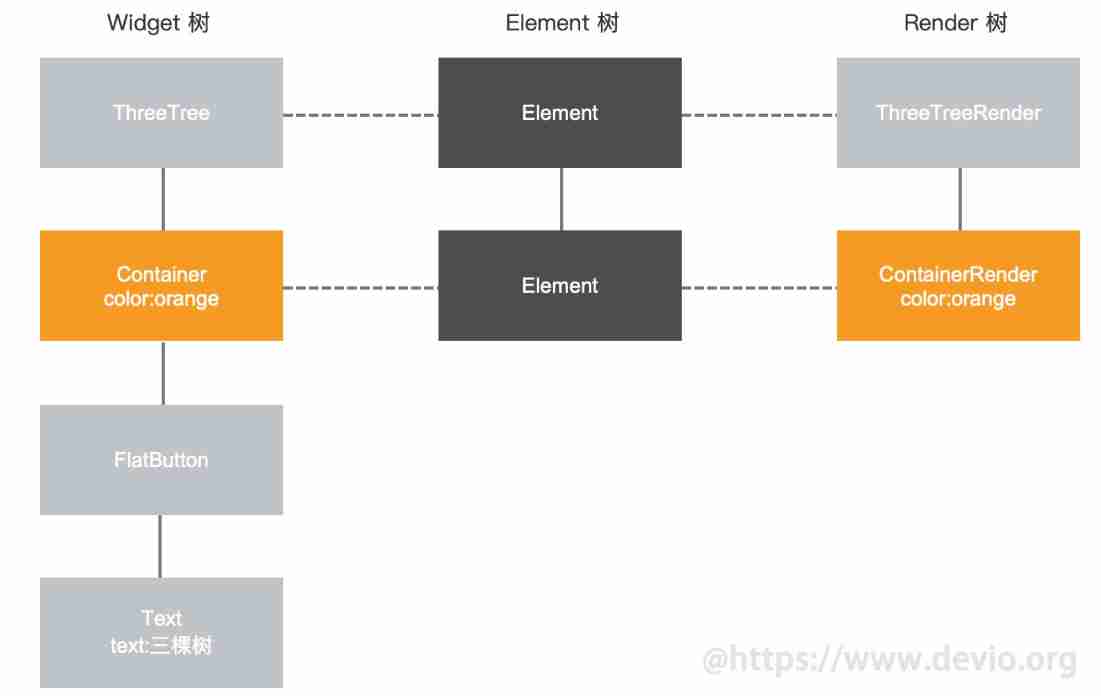
Read and understand the rendering mechanism and principle of flutter's three trees
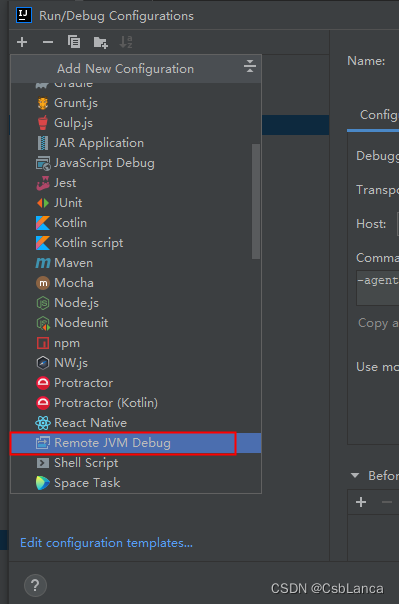
Check the debug port information in rancher and do idea remote JVM debug
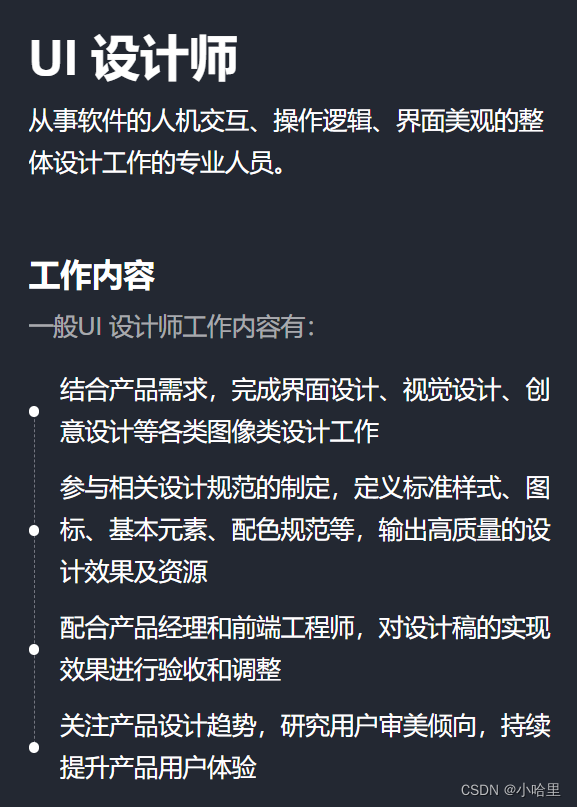
互联网公司实习岗位选择与简易版职业发展规划
Network five whip
Use and install RkNN toolkit Lite2 on itop-3568 development board NPU
随机推荐
PXE启动配置及原理
报错ModuleNotFoundError: No module named ‘cv2.aruco‘
Understanding the architecture type of mobile CPU
byte2String、string2Byte
Matlab superpixels function (2D super pixel over segmentation of image)
II. Data type
Intern position selection and simplified career development planning in Internet companies
Vscode shortcut key
Embedded software architecture design - message interaction
abap查表程序
多表操作-自关联查询
MySQL transaction
Principle of redis cluster mode
Linux安装部署LAMP(Apache+MySQL+PHP)
MySQL regular expression
Pytorch weight decay and dropout
【 YOLOv3中Loss部分计算】
互联网公司实习岗位选择与简易版职业发展规划
只是巧合?苹果 iOS16 的神秘技术竟然与中国企业 5 年前产品一致!
16 channel water lamp experiment based on Proteus (assembly language)