当前位置:网站首页>pikachu Over permission
pikachu Over permission
2022-08-03 22:09:00 【narukuuuu】
Simple record
Horizontal override
Also known as horizontal override, it means
different users with the same authority can access each other, for example, A and B are users with the same authority, if A can see what theoretically only B can seeinformation, or A can perform operations that theoretically only B can perform, this is horizontal overreach.
Topic presentation
Open the title to see, it is a login interface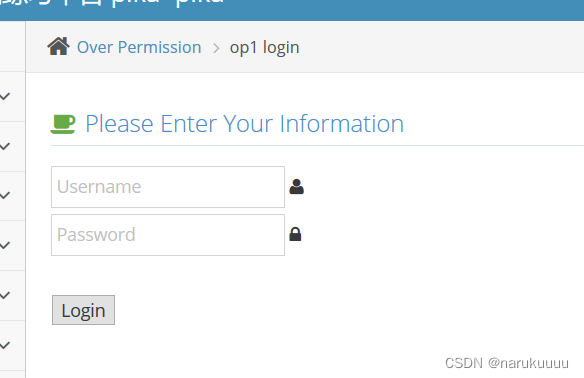
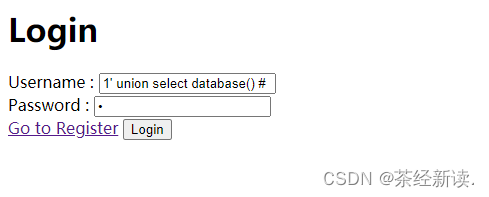
Click on the prompt, find the login information for three accounts, log in to one of the accounts randomly and click to view personal information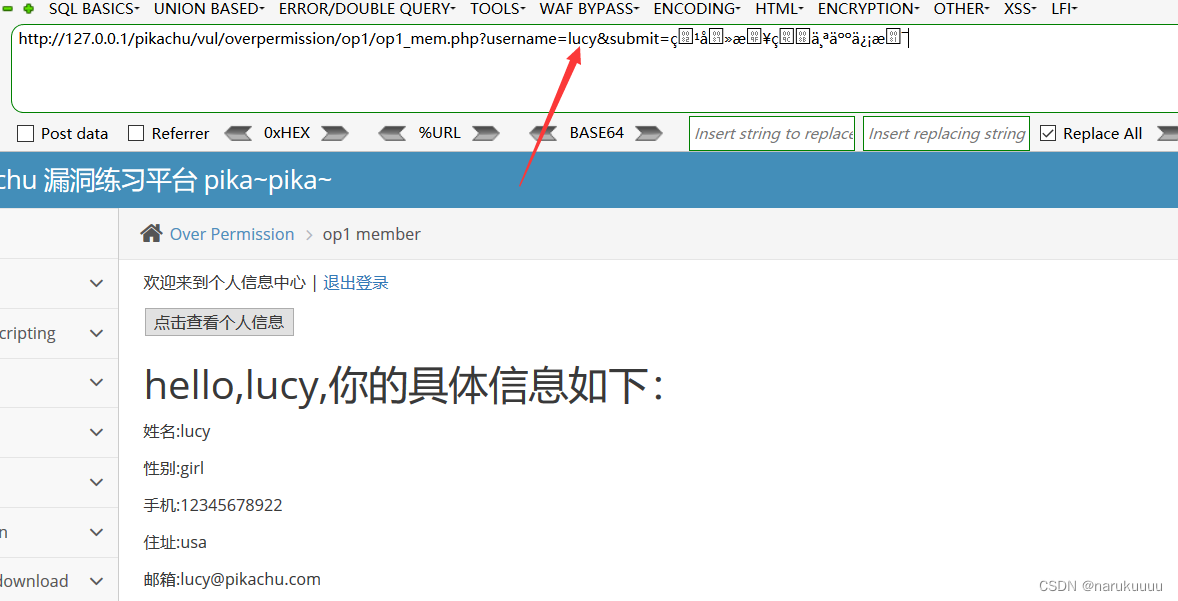
You can find that Url can pass the username as a parameter, try to modify it to other username, and find that it can be echoed successfully, and the authority is successfully exceeded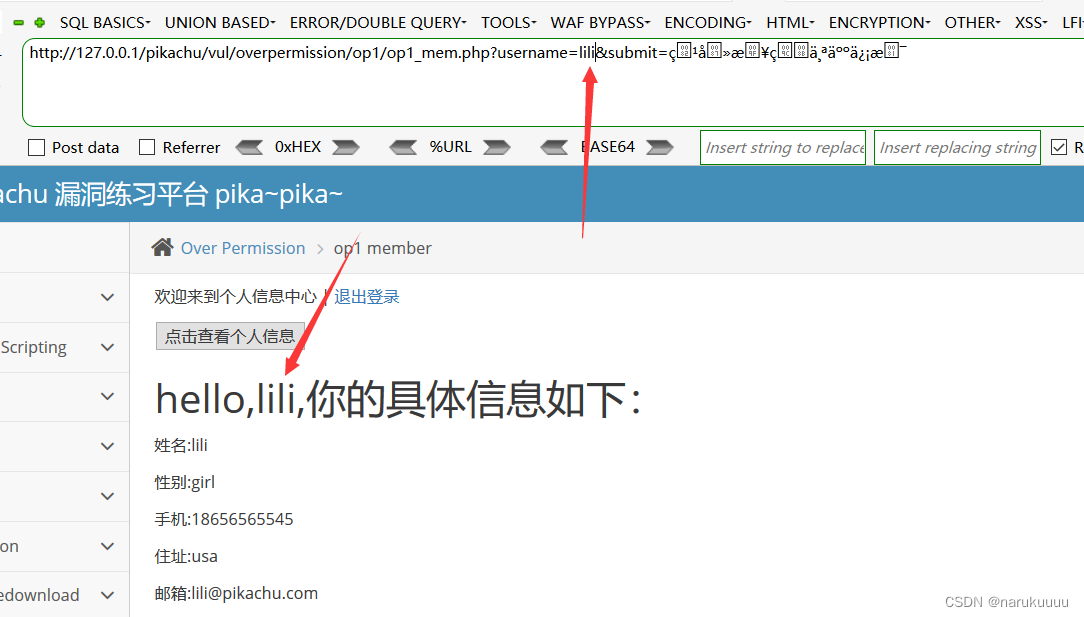
reason
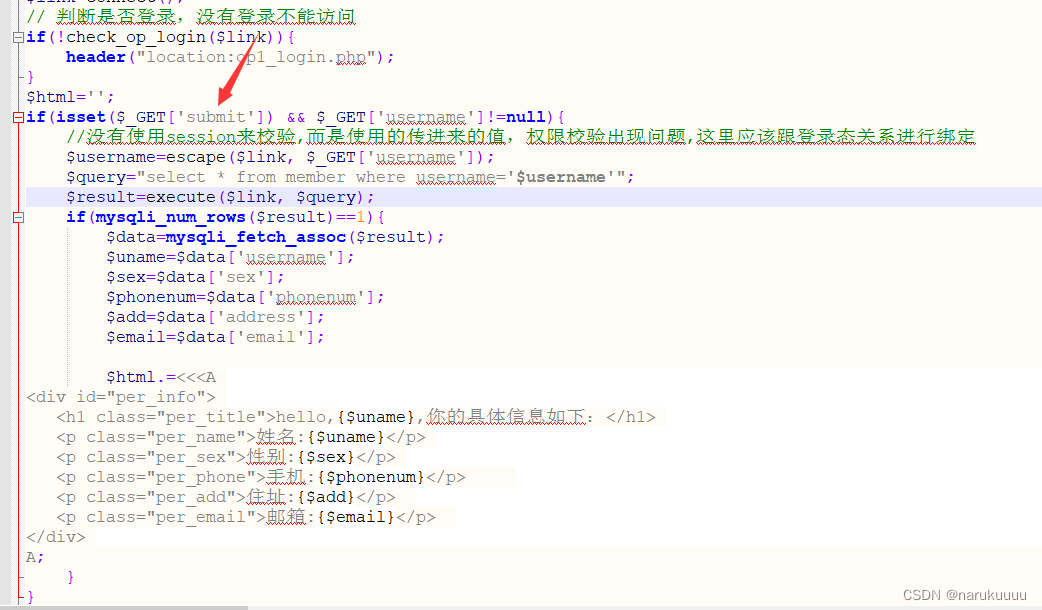
It only judges whether you are logged in and not using session to calibratetest
Checking the check_op_login function in function.php just judges whether ['op']['username'] or ['op']['password'] is defined 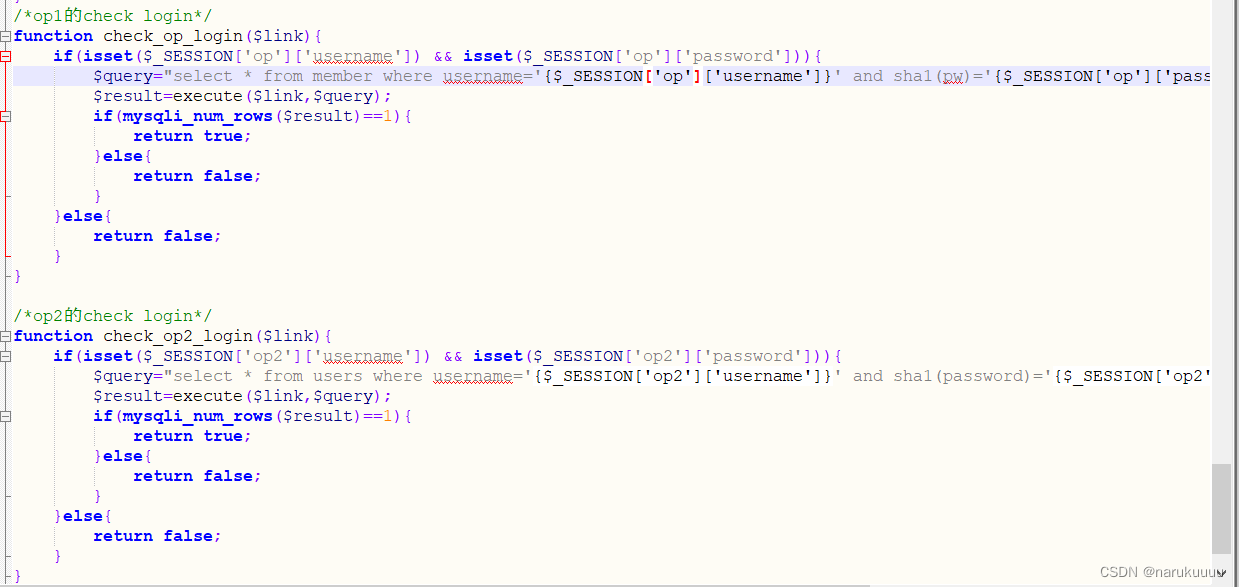
Check the code of the login page and find that all usernames will be defined after login ['op']['username'] and ['op']['password']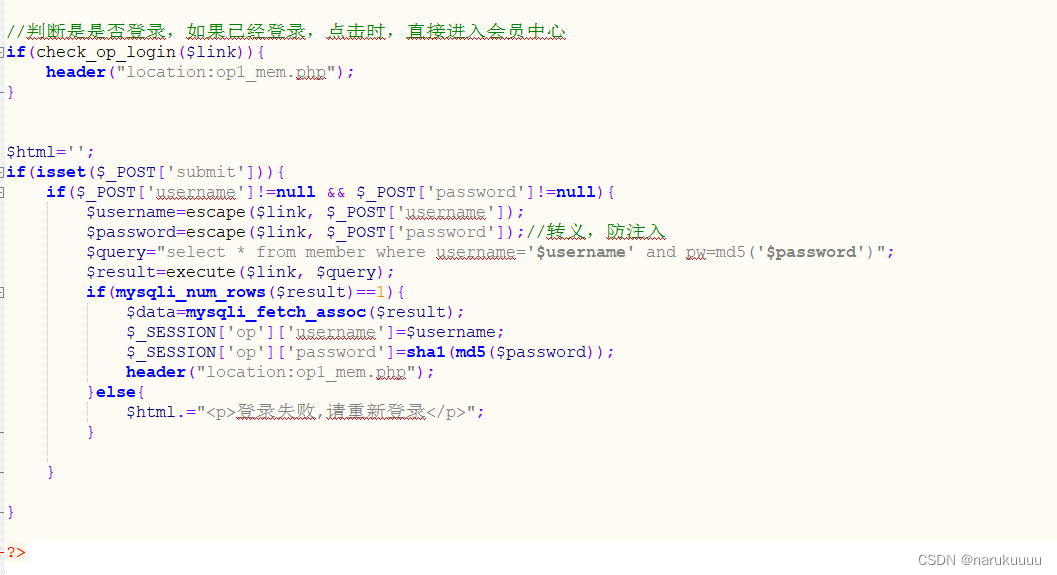
while inThe interface for viewing information only determines whether it is logged in and not which user it is
Vertical override
Also known as vertical override, it means that users with lower permissions can access users with higher permissions.For example, user A has lower authority than B. If A can access resources that theoretically only B can access, or perform operations that theoretically can only be performed by B, that is vertical override.
Topic presentation
pikachu user only has view permission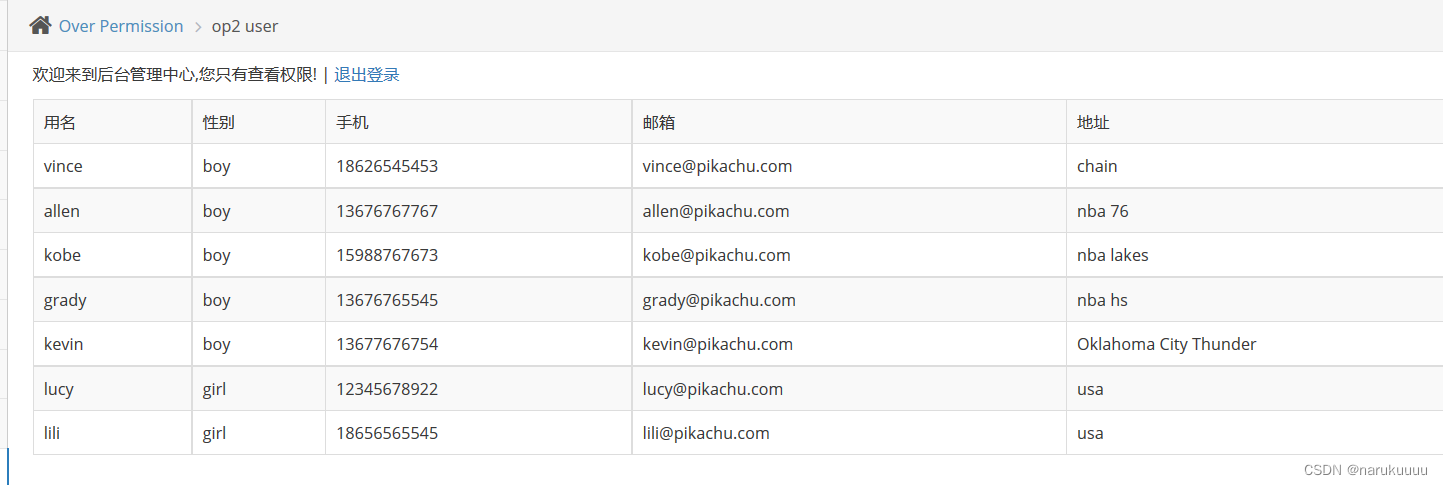
super user adminPermission to modify user information and add users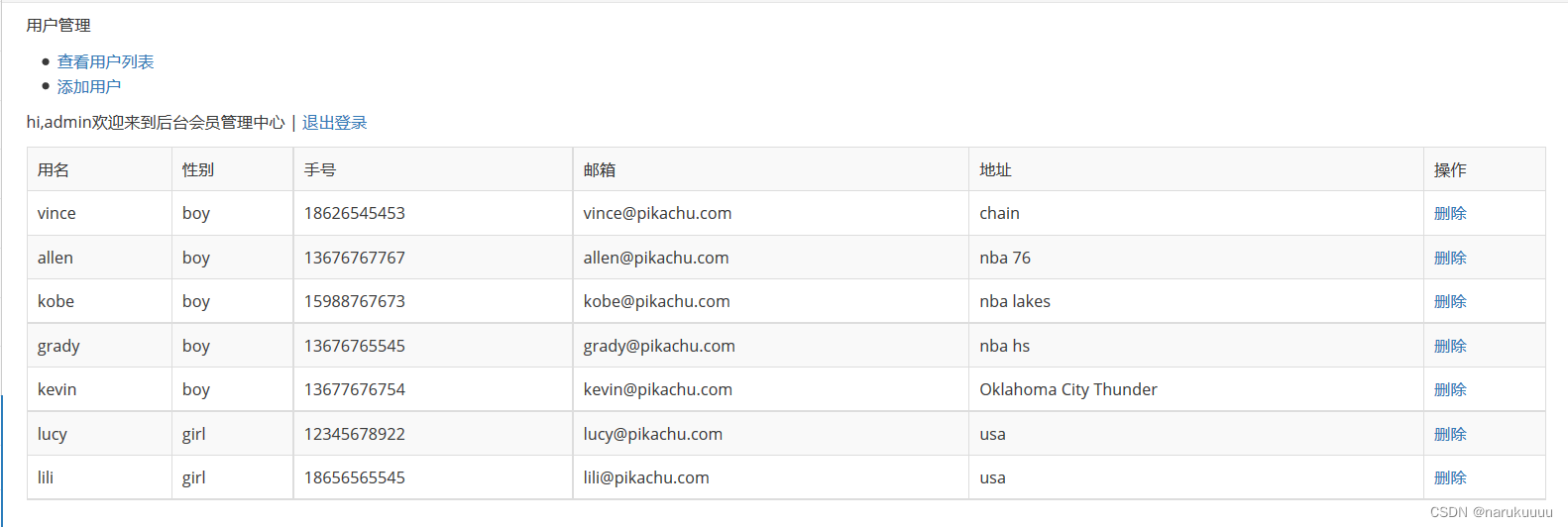
use adminThe user adds a new user test1, pay attention to the url at this time
Open another browser to log in to the ordinary user pikachu and try to directly copy the admin user's add user URL to add users (unauthorized access)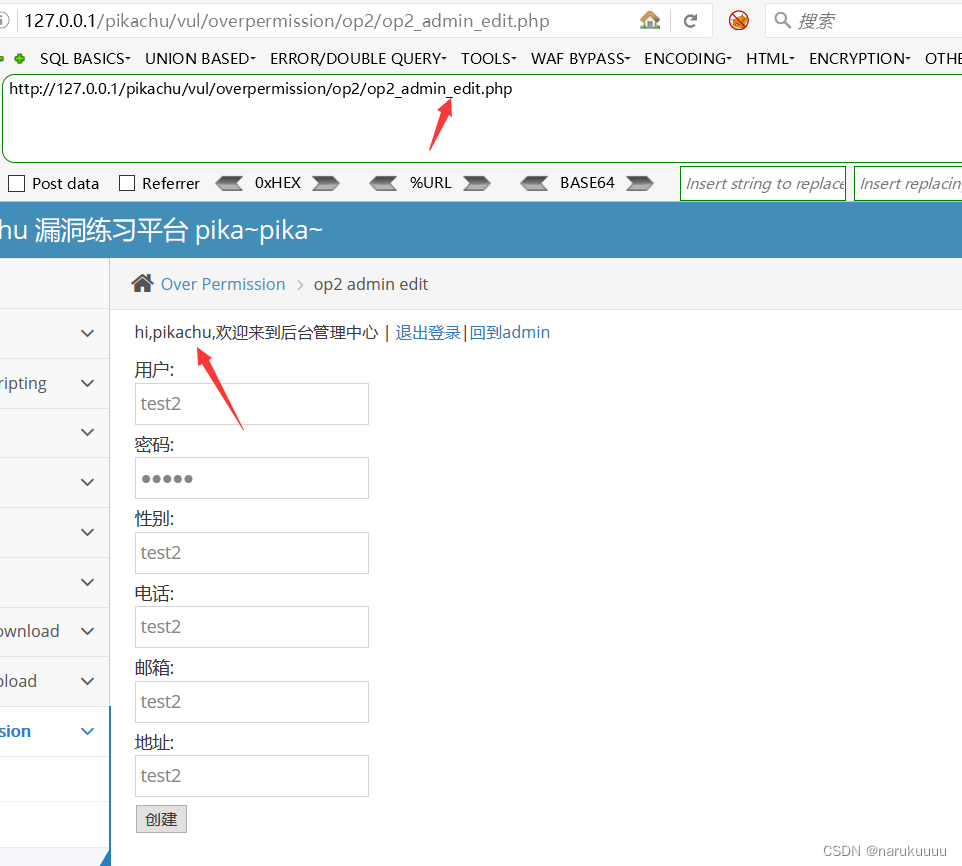
After adding the user as the ordinary user pikachu, I found that the login interface was returned, but re-login the user and check the user information to find that the user just added has been added successfully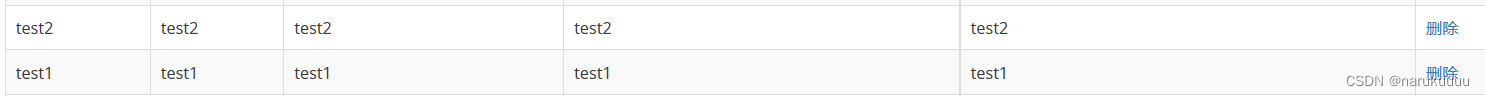
Log in as pikachu user and capture packets and cookie values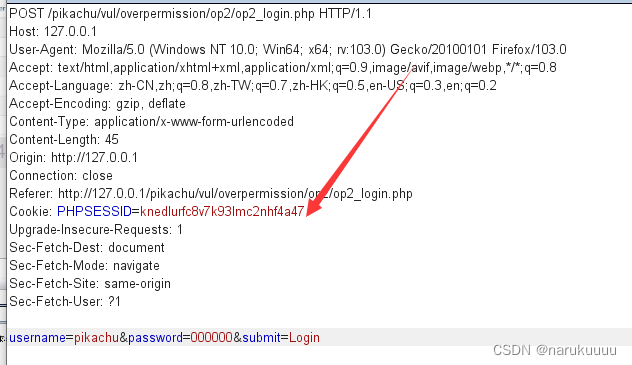
Log in to the administrator account to add user test3, and capture packets together, replace the original cookie value with the pikachu user's cookie value, and re-Send package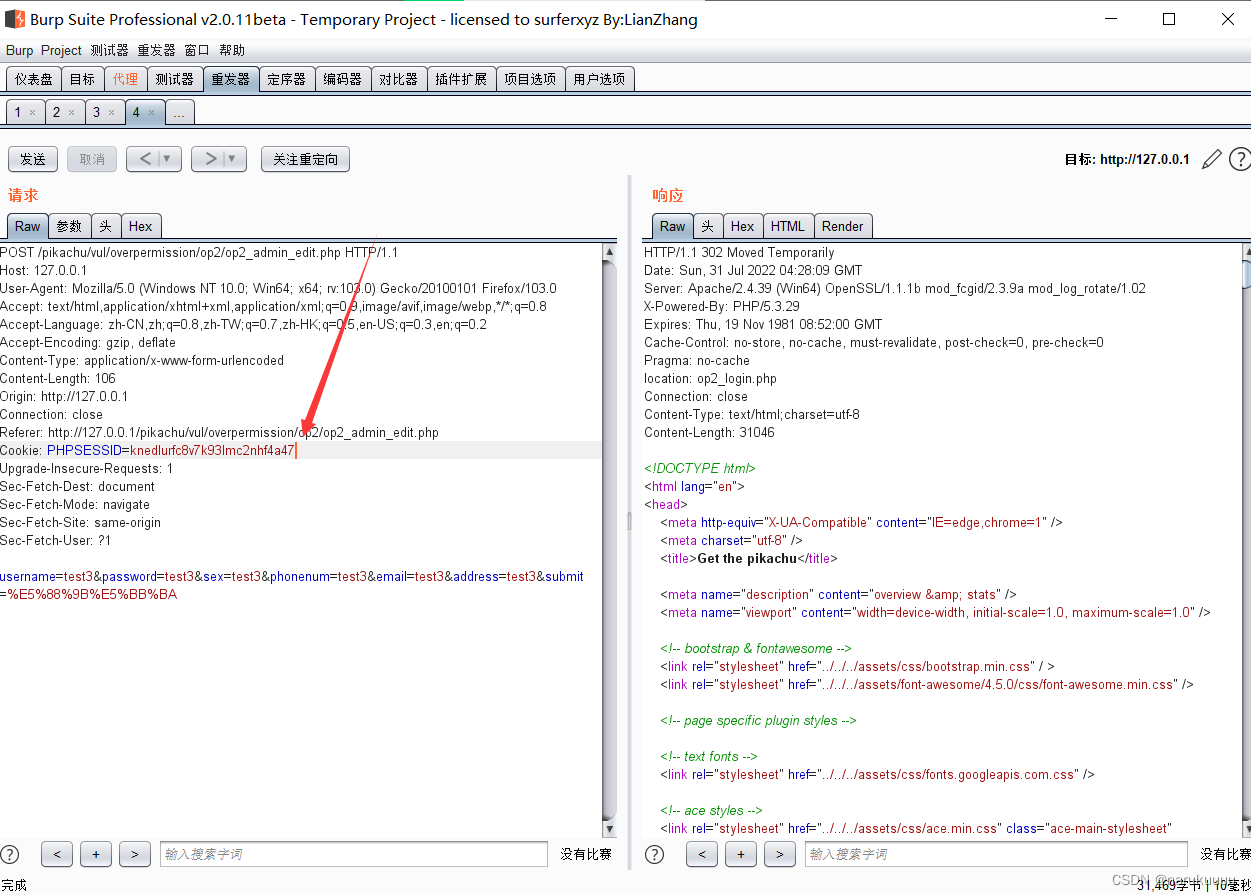
You can see that there are two test3, one isThe test3 user added by the admin user, one is added by replaying the admin data package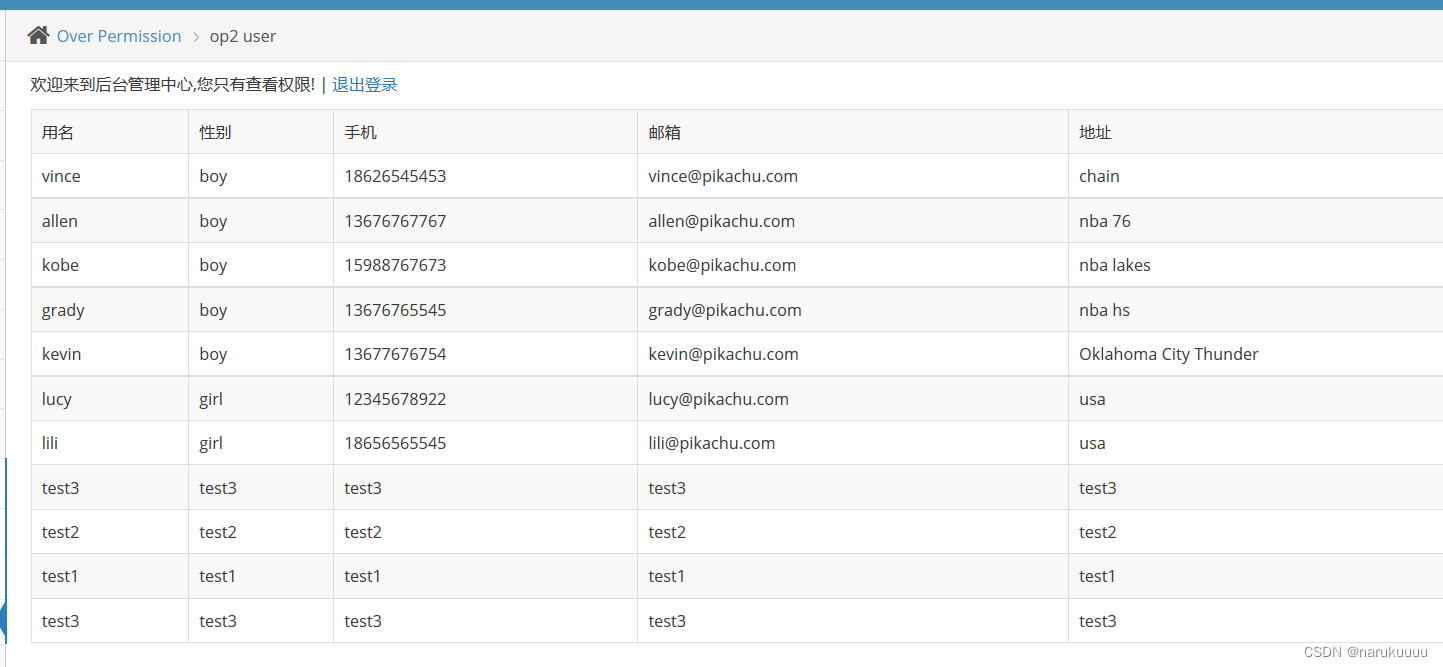
reason
Theop2_login.php page judges the level of the logged-in users to determine which page they enter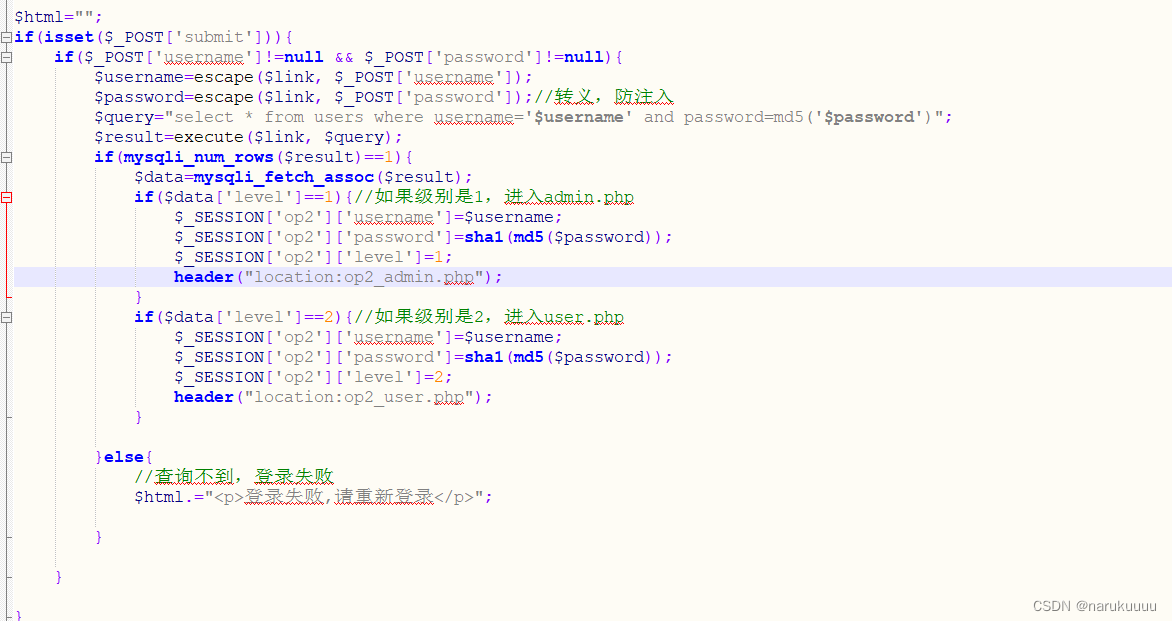
op2_user.php only determines whether to log in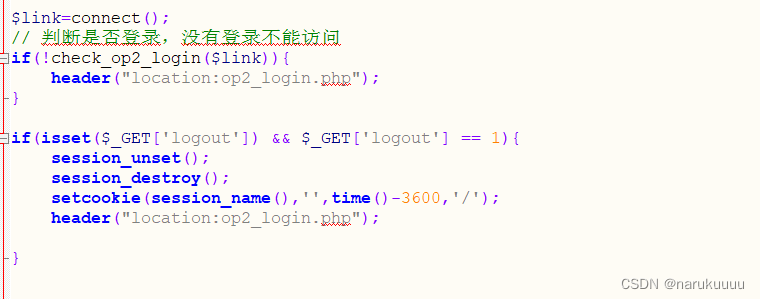
The check_op2_login function in the function is the same as check_op1_login, but only determines whether the variable is defined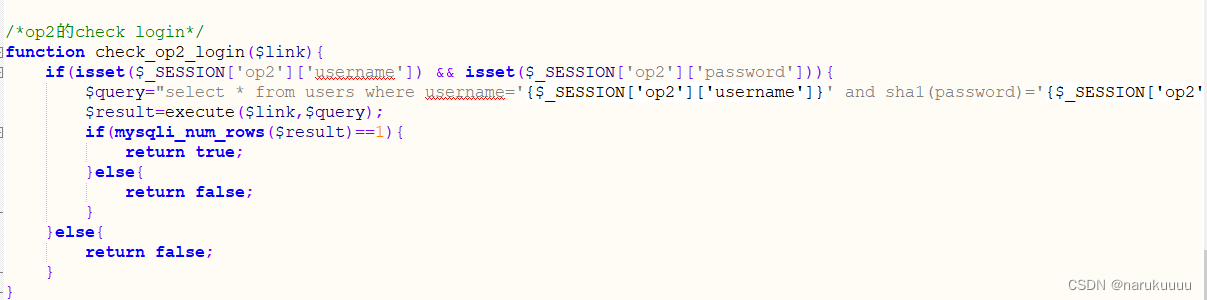
op2_admin.php On this page, the login and level level judgments are made, so after logging in to the pikachu user, accessing the admin.php page will directly jump to the login page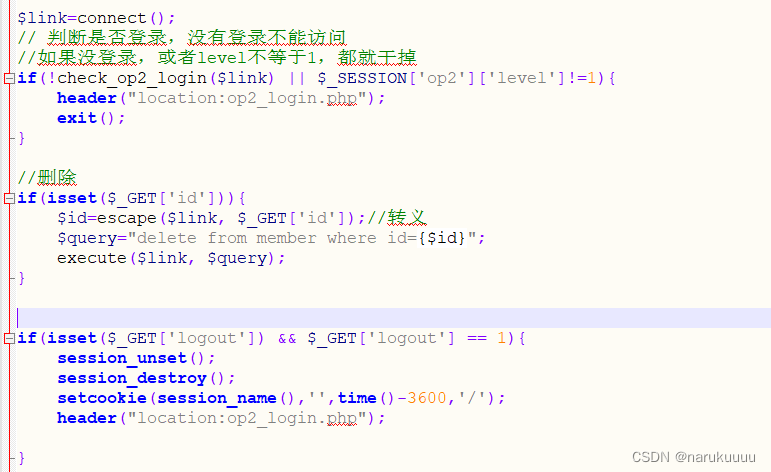
The page for adding users op2_admin_edit.php only verifies whether the user is logged in, if not, it will jumpOn the login page, the user permission level is not verified, but the front end shows that adding a user is an operation that can only be performed by a user with a permission level of 1, so there is a vertical unauthorized vulnerability.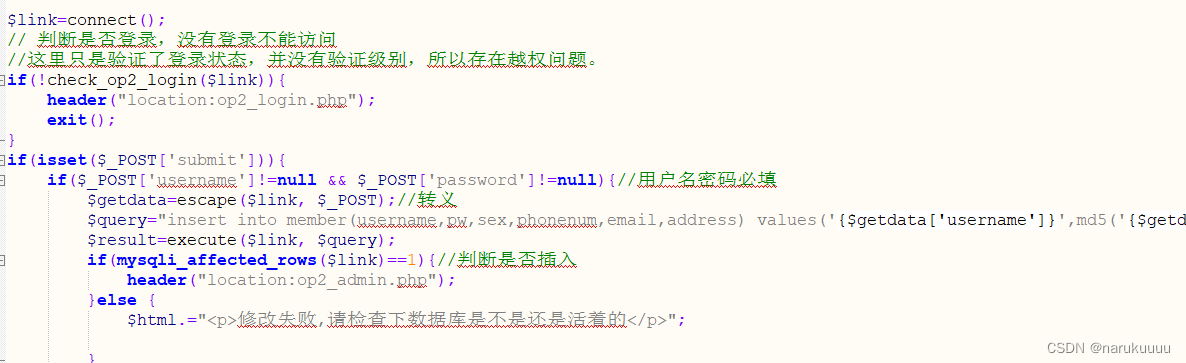
Reference article:
https://blog.csdn.net/elephantxiang/article/details/113480084
https://blog.csdn.net/qq_37077262/article/details/103025989
边栏推荐
猜你喜欢

FVCOM 3D Numerical Simulation of Hydrodynamics, Water Exchange, Dispersion and Transport of Oil Spills丨FVCOM Model Watershed, Numerical Simulation Method of Marine Water Environment
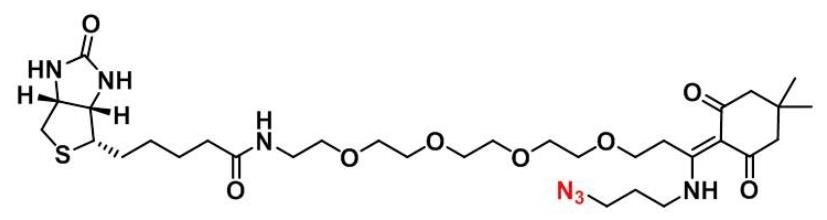
CAS:1797415-74-7_TAMRA-Azide-PEG-Biotin
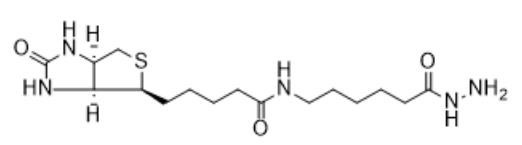
CAS:908007-17-0_Biotin-azide_Biotin azide

E - Swap

码率vs.分辨率,哪一个更重要?
October 2019 Twice SQL Injection
2022-08-02 mysql/stonedb慢SQL-Q18-内存使用暴涨分析

Shell编程的条件语句
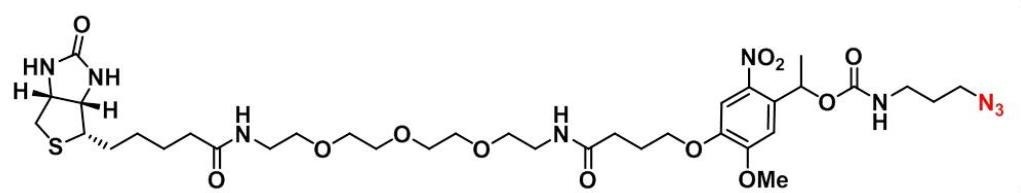
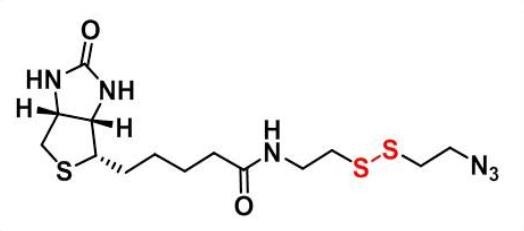
CAS:1620523-64-9_Azide-SS-biotin_生物素-二硫-叠氮
CAS:122567-66-2_DSPE-Biotin_DSPE-Biotin
随机推荐
图的基础概念
老板:公司系统太多,能不能实现账号互通?
483. Smallest Good Base
三年黑盒测试工程师对嵌入式软件测试的理解
384. Shuffle an Array
LitJson报错记录
如何设计 DAO 的 PoW 评判标准 并平衡不可能三角
LVS负载均衡集群
一些思考:腾讯股价为何持续都低
Basic Concepts of Graphs
Flink--Join以及Flink函数
CAS:1620523-64-9_Azide-SS-biotin_biotin-disulfide-azide
目标检测的国内外研究现状
472. Concatenated Words
PowerMockup 4.3.4::::Crack
CAS:1260586-88-6_Biotin-C5-Azide_Biotin-C5-Azide
AI首席架构师13-AICA-智能文档分析技术在行业场景中的应用
for循环练习题
Nacos配置文件管理、微服务获取Nacos配置文件
[b01lers2020]Life on Mars