当前位置:网站首页>Codeforces 474 F. Ant colony
Codeforces 474 F. Ant colony
2022-07-07 20:03:00 【全栈程序员站长】
大家好,又见面了,我是全栈君。
线段树求某一段的GCD…..
F. Ant colony
time limit per test
1 second
memory limit per test
256 megabytes
input
standard input
output
standard output
Mole is hungry again. He found one ant colony, consisting of n ants, ordered in a row. Each ant i (1 ≤ i ≤ n) has a strength si.
In order to make his dinner more interesting, Mole organizes a version of «Hunger Games» for the ants. He chooses two numbers l and r(1 ≤ l ≤ r ≤ n) and each pair of ants with indices between l and r (inclusively) will fight. When two ants i and j fight, ant i gets one battle point only if si divides sj (also, ant j gets one battle point only if sj divides si).
After all fights have been finished, Mole makes the ranking. An ant i, with vi battle points obtained, is going to be freed only if vi = r - l, or in other words only if it took a point in every fight it participated. After that, Mole eats the rest of the ants. Note that there can be many ants freed or even none.
In order to choose the best sequence, Mole gives you t segments [li, ri] and asks for each of them how many ants is he going to eat if those ants fight.
Input
The first line contains one integer n (1 ≤ n ≤ 105), the size of the ant colony.
The second line contains n integers s1, s2, …, sn (1 ≤ si ≤ 109), the strengths of the ants.
The third line contains one integer t (1 ≤ t ≤ 105), the number of test cases.
Each of the next t lines contains two integers li and ri (1 ≤ li ≤ ri ≤ n), describing one query.
Output
Print to the standard output t lines. The i-th line contains number of ants that Mole eats from the segment [li, ri].
Sample test(s)
input
5
1 3 2 4 2
4
1 5
2 5
3 5
4 5output
4
4
1
1Note
In the first test battle points for each ant are v = [4, 0, 2, 0, 2], so ant number 1 is freed. Mole eats the ants 2, 3, 4, 5.
In the second test case battle points are v = [0, 2, 0, 2], so no ant is freed and all of them are eaten by Mole.
In the third test case battle points are v = [2, 0, 2], so ants number 3 and 5 are freed. Mole eats only the ant 4.
In the fourth test case battle points are v = [0, 1], so ant number 5 is freed. Mole eats the ant 4.
#include <iostream>
#include <cstdio>
#include <cstring>
#include <algorithm>
#include <map>
#include <vector>
using namespace std;
const int maxn=100100;
typedef pair<int,int> pII;
pII b[maxn];
int n,s[maxn];
int g[maxn<<2];
int gcd(int x,int y)
{
if(x==0) return y;
return gcd(y%x,x);
}
void build(int l,int r,int rt)
{
if(l==r)
{
g[rt]=s[l];
return ;
}
int mid=(l+r)/2;
build(l,mid,rt<<1); build(mid+1,r,rt<<1|1);
g[rt]=gcd(g[rt<<1],g[rt<<1|1]);
}
int query(int L,int R,int l,int r,int rt)
{
if(r<L||l>R) return 0;
if(L<=l&&r<=R)
{
return g[rt];
}
int mid=(l+r)/2;
int u=query(L,R,l,mid,rt<<1);
int v=query(L,R,mid+1,r,rt<<1|1);
return gcd(u,v);
}
int main()
{
scanf("%d",&n);
for(int i=1;i<=n;i++)
{
scanf("%d",s+i);
b[i]=(make_pair(s[i],i));
}
sort(b+1,b+1+n);
build(1,n,1);
int m;
scanf("%d",&m);
while(m--)
{
int Left,Right;
scanf("%d%d",&Left,&Right);
int G=query(Left,Right,1,n,1);
int from=lower_bound(b+1,b+n+1,make_pair(G,Left))-(b+1);
int to=lower_bound(b+1,b+1+n,make_pair(G,Right+1))-(b+1);
printf("%d\n",(Right-Left+1)-(to-from));
}
return 0;
}发布者:全栈程序员栈长,转载请注明出处:https://javaforall.cn/116374.html原文链接:https://javaforall.cn
边栏推荐
- Spark judges that DF is empty
- 95年专注安全这一件事 沃尔沃未来聚焦智能驾驶与电气化领域安全
- SQL注入报错注入函数图文详解
- Micro service remote debug, nocalhost + rainbow micro service development second bullet
- 2022如何评估与选择低代码开发平台?
- 使用 BR 备份 TiDB 集群数据到 Azure Blob Storage
- 开发那些事儿:Go加C.free释放内存,编译报错是什么原因?
- H3C s7000/s7500e/10500 series post stack BFD detection configuration method
- 有用的win11小技巧
- 怎样用Google APIs和Google的应用系统进行集成(1)—-Google APIs简介
猜你喜欢
让这个CRMEB单商户微信商城系统火起来,太好用了!
![[paper reading] maps: Multi-Agent Reinforcement Learning Based Portfolio Management System](/img/76/b725788272ba2dcdf866b28cbcc897.jpg)
[paper reading] maps: Multi-Agent Reinforcement Learning Based Portfolio Management System
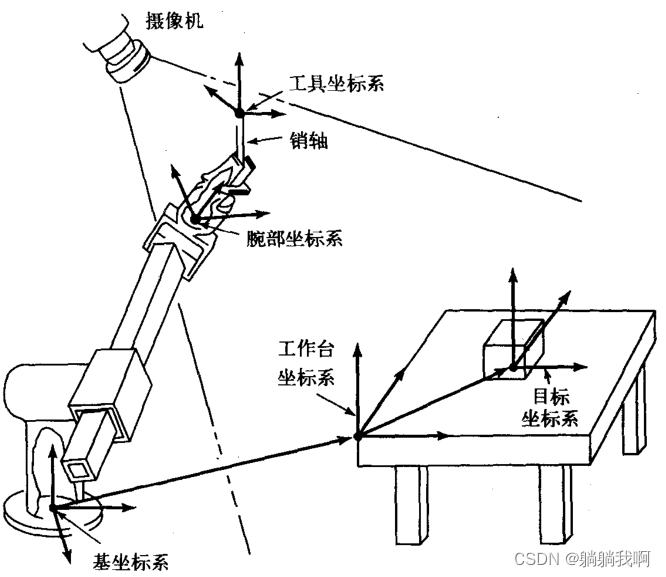
Small guide for rapid formation of manipulator (11): standard nomenclature of coordinate system

95年专注安全这一件事 沃尔沃未来聚焦智能驾驶与电气化领域安全

Dachang classic pointer written test questions
使用camunda做工作流设计,驳回操作
![Is embedded system really safe? [how does onespin comprehensively solve the IC integrity problem for the development team]](/img/af/61b384b1b6ba46aa1a6011f8a30085.png)
Is embedded system really safe? [how does onespin comprehensively solve the IC integrity problem for the development team]

使用枚举实现英文转盲文
Apifox interface integrated management new artifact
【C语言】指针进阶---指针你真的学懂了吗?
随机推荐
95年专注安全这一件事 沃尔沃未来聚焦智能驾驶与电气化领域安全
恶魔奶爸 A3阶段 近常速语流初接触
Klocwork 代码静态分析工具
Nebula Importer 数据导入实践
VMWare中虚拟机网络配置
Optimization cases of complex factor calculation: deep imbalance, buying and selling pressure index, volatility calculation
How to meet the dual needs of security and confidentiality of medical devices?
Solve the problem that the executable file of /bin/sh container is not found
恢复持久卷上的备份数据
【OpenCV 例程200篇】223. 特征提取之多边形拟合(cv.approxPolyDP)
嵌入式系统真正安全了吗?[ OneSpin如何为开发团队全面解决IC完整性问题 ]
Tensorflow2.x下如何运行1.x的代码
Mysql子查询关键字的使用方式(exists)
Implement secondary index with Gaussian redis
JNI 初级接触
CodeSonar通过创新型静态分析增强软件可靠性
npm uninstall和rm直接删除的区别
静态测试工具
H3C s7000/s7500e/10500 series post stack BFD detection configuration method
Static analysis of software defects codesonar 5.2 release