当前位置:网站首页>Is embedded system really safe? [how does onespin comprehensively solve the IC integrity problem for the development team]
Is embedded system really safe? [how does onespin comprehensively solve the IC integrity problem for the development team]
2022-07-07 20:27:00 【Maihexong】
Jim · Hogan (Jim Hogan) On 2019 year 9 month 4 On the afternoon of Sunday 12:00 The submitted IC Integrity thesis Category :EDA,Onespin,RISC-V
It is a process to reduce the risk of latent vulnerabilities in semiconductor design and its related functions . historically , The market segmentation of the final product determines the capital that can be invested in functional verification . But a few years ago, this long-standing equation failed catastrophically . The reason for the failure is that these vulnerabilities cannot be found , The big reason is the increasing use of Embedded Software . meanwhile , The proportion of functional correctness verification in the total design cost is also increasing .
Besides , The development process must now consider incorporating code security , Code robustness and code credibility as design requirements . Code security ensures that the design can continue to run in a safe manner in the event of random failure , Code robustness ensures that its expected behavior is not changed by environmental hazards or malicious activities . Code credibility is to ensure that no Trojan horse is injected into the design during the development process .
Think carefully , Our connection system is damaged almost every day , This includes the theft of our personal or financial data . Of equal concern are denial of service attacks , Among them, thousands of connected devices are taken over and controlled to achieve the purpose of malicious damage . These are reported security vulnerabilities , But there may be many other security vulnerabilities we haven't heard of .
It is hoped that the failure of any large-scale computer will not lead to the breakdown of the whole airport system , And it can safely and reliably remove the faulty equipment and replace the spare components while the system continues to operate .
We've also heard about injecting Trojan viruses into chips or systems in the production chain , Once the chip or system is deployed, it will be threatened by trojan virus . Therefore, the credibility verification of the code in the final design is very important .
Let's use the most typical driving technology today ( Autopilot ) To illustrate this challenge . This technology is important for code security 、 Code robustness and code credibility have put forward higher requirements , In order to respond to on-site faults in time and ensure that hackers cannot enter the faulty system .
These are the realities that development teams must face today . Today's development teams have to face the reality that most of the tools and methods used in functional verification in the industry can not alleviate these problems . This is a IC Integrity issues .
IC Integrity definition
IC Integrity is a state , In this state , From product specifications to deployed products, even under adverse conditions such as failure or malicious attack , The product design can also be correct within the expected functional range 、 Operate safely and reliably .
IC Integrity will affect from SoC The whole development process from level to implementation and then to deployment . Although most development is at the register transfer level (RTL) The complete , But when a product design is implemented at a higher level of abstraction , It must be combined with some concepts implemented at the physical level . for example ,IC Integrity can be ensured from verification RTL In the process of product deployment , Any unexpected features will not be added 、 Delete or modify . This may include downloading to FPGA Perform equivalence checking on the bitstream . Even though IC Integrity does not strictly include software , But the hardware must provide a secure environment for the software running in it .
Unfortunately, no company or technology can achieve IC All aspects of integrity . contrary , Companies need to adopt many different methods throughout the development process .
I Believe ,OneSpin Solutions The company represents a company that can understand... In multiple market segments IC A company in the sense of integrity . That's why I chose to work with them .
Three pillars
IC Integrity is supported by three pillars :
▷ Functional correctness
▷ Code security
▷ Code credibility and code robustness
Not all industries view each pillar with the same weight , For example, some industries regard functional correctness and code security as essential to their market , Other industries want to include functional safety requirements . Code security and code robustness are linked to some extent , Because if the equipment is unsafe , There is no guarantee that its code is safe , If safety should have been guaranteed All equipment is unsafe , Then when the failure occurs, these devices can not guarantee their safety . Therefore, we should rely on the detected faults to prevent intrusion .
Besides , There are still some secondary problems in some industries , For example, reliability problems . Although fundamentally , This is a foundry , Different problems to be solved by design and other background tasks , However, functional safety plays a vital role in detecting equipment faults , Therefore, security has become an important aspect of reliability .
Functional correctness
Functional correctness refers to proving that a design performs all expected functions defined by its functional requirements . Requirements can also define behaviors that never occur .
For more and more markets and Applications , It is no longer sufficient to use simulation only to achieve the level of verifying the correctness of functions . Moreover, the elimination of system errors from the design makes it impossible for the design team to adopt new verification methods because the scale and complexity of such design errors are increasing . Even if added by hardware 、 Supplement by simulation or physical prototype , Simulation is no longer enough to complete the task of functional verification . Since the performance of single processor has stabilized , And the simulation algorithm can not be parallelized , Therefore, the simulation function cannot be extended . Even in the form of custom hardware to accelerate the increase in parallelism , But the cost is very high . Common methods such as constrained random test generation are becoming increasingly inefficient , In particular, there is no reliable way to determine coverage . Fundamentally speaking , This method is flawed , Because these technologies can never guarantee the correctness of functions , And can't solve IC Code security required for integrity , Problems in code robustness and code credibility .
Wilson Research New research shows that , The number of chip redesigns is growing , This shows that fewer and fewer companies are achieving the goal of functional verification . Progressive companies are adopting formal verification technology at an increasing rate , Although only a few companies have developed to the extent that they can sign in only using formal tools .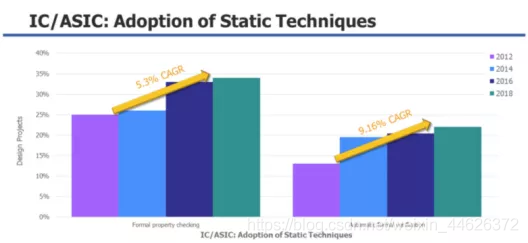
2018 The increase in the use of formal technology in . source : Wilson research group
This approach needs to be changed . The creation of automatic form technology helps to accelerate its application , But the company must invest the necessary resources in the early stage , Thus, formal technology can replace most functional verification methods , So it can greatly replace the use of dynamic verification method ( Such as simulation ), Formal verification can greatly reduce the time required .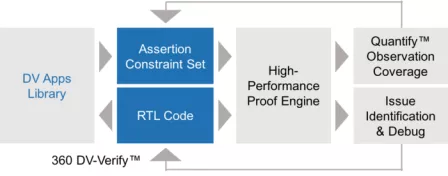
Formal verification
Functional safety
Functional safety means that the system must be able to detect and respond to random faults when running , To prevent failure .
The technical competition for autonomous vehicle makes people pay more attention to safety . Although some industries such as avionics have long focused on security , But their method is to verify the safety through a large number of repeated tests , And this kind of industry doesn't think cost is the main problem . For the automotive industry , This is not true , Because it is estimated that , The cost of electronic equipment will soon become half the cost of cars . Use a rough method ( Copy for example ), It's easier to prove that safety , But when safety is directly incorporated into the design , More in-depth analysis is needed , This also increases the complexity of the function verification task .
The traditional method of safety verification is through fault simulation . This requires simulating the functional verification suite with every potential fault injected into the system , To see if faults can be detected during the design process and respond appropriately . Given that many chip return kits take days or weeks to run , So this is clearly not a viable solution . Even if technologies have been developed to reduce the size of the required test set and the number of faults that need to be checked , But these still represent a huge amount of computation .
Nowadays, new technologies are urgently needed to reduce or eliminate fault simulation , because SoC Level hardware analysis and failure mode analysis need to be automated , And the built-in security mechanism in the design needs to be fully verified .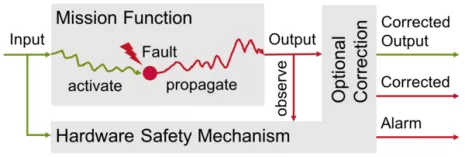
Fault detection
Credibility and robustness
Credibility and robustness mean , Even under duress , The system will only perform its intended function , And the data that should be kept confidential will still be retained in this way without being destroyed .
In the past year , The obvious thing is , The performance of processor design is compromised by many security issues . Discover new vulnerabilities , And fixes for these vulnerabilities usually mean a decline in processor performance .
Before robust design , Many infrastructures for connecting devices and realizing communication have been implemented . This basically means , Every device connected to the Internet is vulnerable . We have seen many examples of using this method to access corporate networks and steal data , Even if these companies have adopted technologies such as firewalls to prevent such intrusion .
In the chip , It must be ensured that the software running on the processor is also protected . Because it doesn't just mean ensuring that the software can be trusted , Moreover, privileged software can need to run in an environment inaccessible to user level applications . The failure of these mechanisms means that malicious users can endanger the device and all instruments that trust the device .
The semiconductor industry relies on component reuse , Some of these components may be developed in-house , Other components come from third-party companies . People have questioned the credibility of these third-party devices , Especially when these equipment are developed or owned by foreign countries . Throughout the design and implementation process , The credibility of these devices needs to be constantly reviewed .
We also heard more about side channel attacks , These attacks by looking at secondary characteristics ( Including power and radiation information ) Extract data from the system .
Different from the correctness and safety of functions , The robustness and credibility verification of functions is not to prove that something is right , But to show something that doesn't exist . This is using dynamic technology ( For example, simulation ) A task that can never be completed . Only through formal technology can we ensure the robustness and credibility of health care .
achieve IC integrity
The design team indicates that the design has been completed and verified and deployed on site , A lot will happen between the two .
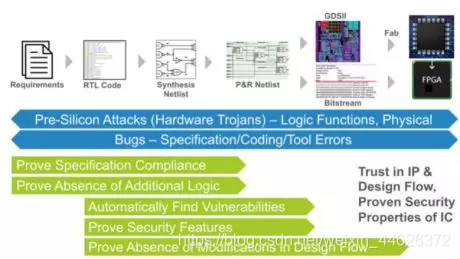
From demand to chip vulnerabilities . source :OneSpin Solution
These things are mainly in two aspects : Integration and implementation .
When used in design IP when , If it's time to IP The block is not properly or legally connected , Then IP The transfer of blocks and their integration into large systems may undermine efforts made in any of these three pillars . Verification of chip assembly usually involves millions of connections , These connections cannot be fully verified using dynamic authentication .
During the implementation of the system, many changes will be made to the design . Each of these transformations can damage any of the three pillars .
Inserting test logic into the system can damage code quality . Inserting a power reduction circuit may affect the correctness and safety of the function . The tool may contain errors in the wrong add or delete behavior . Even the placement of components and connecting lines may cause side channel attacks because some circuit board layouts cannot be fully understood . These are just examples of unexpected changes that could damage the system .
In addition, malicious acts may occur . Recent examples show that , Rogue components have been added to some printed circuit boards , This makes remote access and data theft possible . As a result, the industry is increasingly worried about the use of unqualified or counterfeit parts . In these cases , How do you know what you use IP Is trustworthy ?
FPGA It also leads to another level of vulnerability , Therefore, the bitstream downloaded to the device must be protected . But this needs to ensure that the bit data flow is guaranteed throughout the development process and life cycle .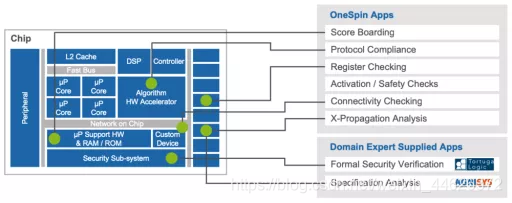 Integration verification
Integration verification
Thinking paradigm
To further explain some problems , It's worth considering an emerging example in the industry . Open source RISC-V Instruction set architecture (ISA) The rapid rise of has aroused great interest in the whole semiconductor industry . Some companies may choose to develop their own processor implementations , Other companies may buy processors from third-party companies . How do you know the processor is ISA A faithful representative of , And can be trusted ?
RISC-V Our developers are developing a verification suite for the combination gauge , But this only shows that under limited conditions , Realization and ISA Specifications match . That's it .
The development of a complete verification suite is very expensive . Many people will need to pay a lot of money for the core business “ Taxes ”. But how do users know if their authentication is sufficient ? How can you trust that the kernel does not contain trojan virus programs ? How do you know if it has passed the necessary procedures to ensure its security and robustness ?
therefore RISC-V The developer of the core must prove that the core complies with ISA standard , And in addition to the specified content , The nuclear does nothing else . But if the development of the verification suite is an important part of the value of shelf nuclear products , Then developers are unlikely to make it public . So how can suppliers prove that their core is trustworthy ? There is a third party RISC-V Can integrity solutions provide answers ?
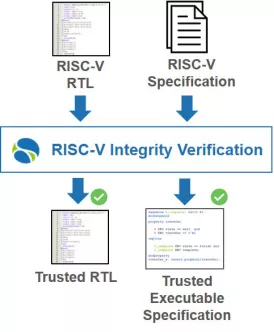
RISC-V Formal verification of
Conclusion
Functional verification will become more and more difficult . The company continues to try to use existing and inherent technology , At the same time, these technologies are becoming more and more inefficient . Besides , Functional correctness is now just one of the verification tasks faced by many companies . Functional safety 、 The increase of robustness and credibility increases the complexity of verification tasks , This is a problem that cannot be solved by old technology .IC Integrity is becoming more and more important in industry ( Including embedded , cloud , Infrastructure and automotive industry ) A mandatory requirement for .
The existence of advanced technology can solve many aspects of these problems . State of the art development teams are developing and deploying new technologies . As more and more companies realize code quality , Product safety 、 Robustness and credibility are gradually becoming the factors of product differentiation , The demand for these solutions is also growing .
( copyright , Plagiarism will investigate )
More information :http://www.softtest.cn/
边栏推荐
- CodeSonar网络研讨会
- Apifox 接口一体化管理新神器
- Apifox interface integrated management new artifact
- 上海交大最新《标签高效深度分割》研究进展综述,全面阐述无监督、粗监督、不完全监督和噪声监督的深度分割方法
- Network principle (1) - overview of basic principles
- Deep learning model compression and acceleration technology (VII): mixed mode
- Yolov6:yolov6+win10--- train your own dataset
- How does codesonar help UAVs find software defects?
- [award publicity] issue 22 publicity of the award list in June 2022: Community star selection | Newcomer Award | blog synchronization | recommendation Award
- guava多线程,futurecallback线程调用不平均
猜你喜欢
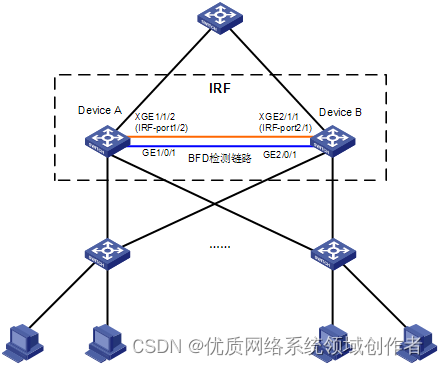
H3C s7000/s7500e/10500 series post stack BFD detection configuration method

How does codesonar help UAVs find software defects?
【mysql篇-基础篇】事务

CodeSonar如何帮助无人机查找软件缺陷?
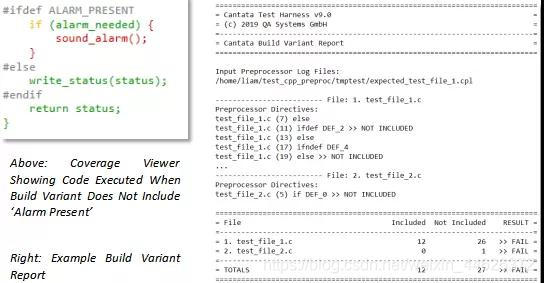
Cantata9.0 | 全 新 功 能
Small guide for rapid formation of manipulator (12): inverse kinematics analysis
Make this crmeb single merchant wechat mall system popular, so easy to use!
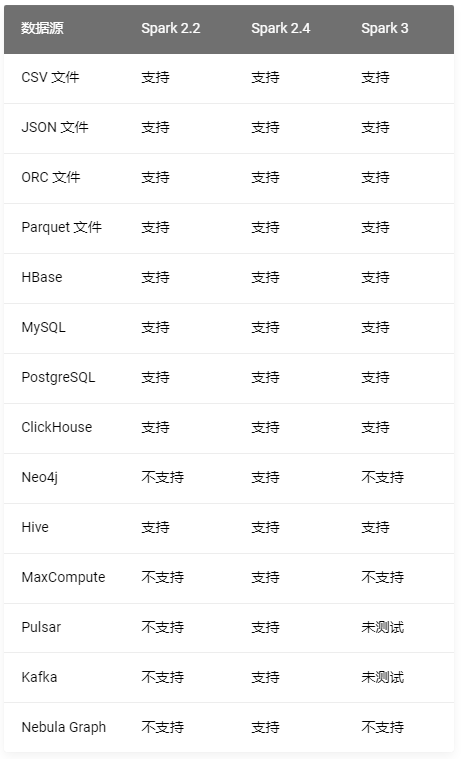
Nebula importer data import practice
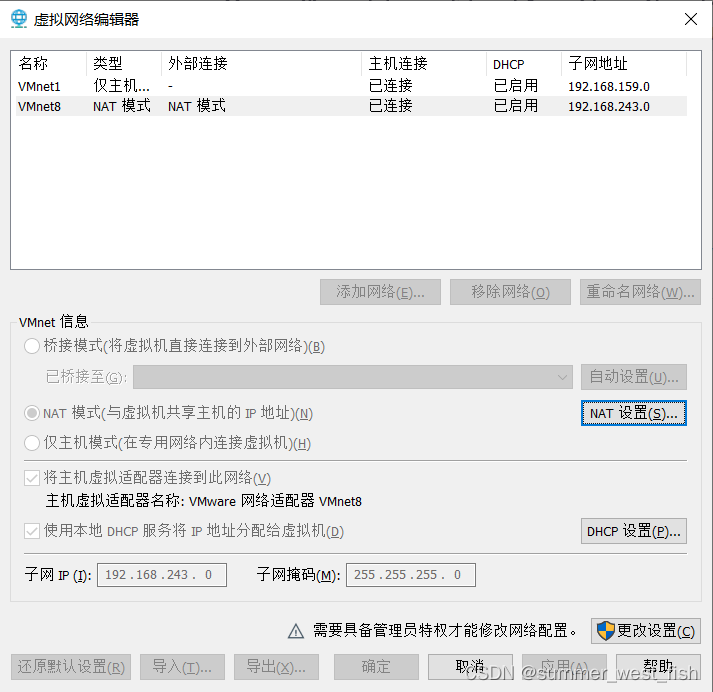
VMWare中虚拟机网络配置

PHP method of obtaining image information
随机推荐
How to test CIS chip?
Klocwork code static analysis tool
Dachang classic pointer written test questions
Flask1.1.4 Werkzeug1.0.1 源码分析:路由
Machine learning notes - explore object detection datasets using streamlit
Klocwork 代码静态分析工具
论文解读(ValidUtil)《Rethinking the Setting of Semi-supervised Learning on Graphs》
使用 BR 备份 TiDB 集群数据到 Azure Blob Storage
万字总结数据存储,三大知识点
软件缺陷静态分析 CodeSonar 5.2 新版发布
Is it safe to open a stock account at present? Can I open an account online directly.
使用camunda做工作流设计,驳回操作
JNI 初级接触
H3C S7000/S7500E/10500系列堆叠后BFD检测配置方法
静态测试工具
[philosophy and practice] the way of program design
Write a jump table
[paper reading] maps: Multi-Agent Reinforcement Learning Based Portfolio Management System
C语言 整型 和 浮点型 数据在内存中存储详解(内含原码反码补码,大小端存储等详解)
Micro service remote debug, nocalhost + rainbow micro service development second bullet