当前位置:网站首页>Ruoyi interface permission verification
Ruoyi interface permission verification
2022-07-03 06:29:00 【xuhss_ com】
High quality resource sharing
| Learning route guidance ( Click unlock ) | Knowledge orientation | Crowd positioning |
|---|---|---|
| 🧡 Python Actual wechat ordering applet 🧡 | Progressive class | This course is python flask+ Perfect combination of wechat applet , From the deployment of Tencent to the launch of the project , Create a full stack ordering system . |
| Python Quantitative trading practice | beginner | Take you hand in hand to create an easy to expand 、 More secure 、 More efficient quantitative trading system |
This article belongs to ruoyi Project practice series
ruoyi In the front end, the system dynamically displays directories and buttons mainly through whether permission characters are included or not . To prevent passage http Request to bypass permission restrictions , The back-end interface also needs to be designed with relevant permissions .
@PreAuthorize Use
Due to @PreAuthorize The principle is not well understood , So here is only a brief explanation in ruoyi How the project is applied .
Before requesting to call the interface , By @preAuthorize The annotated interface needs to be validated first . Via annotation parameters value() Return value true and false To determine whether you have permission .
public @interface PreAuthorize {
String value();
}
Ruoyi Not using native Spel expression , It's using custom PermissionService class , Through which custom methods hasPermi(String Permission) To judge the authority . Use examples of annotations :@PreAuthorize("@ss.hasPermi('system:menu:list')")
public boolean hasPermi(String permission)
{
if (StringUtils.isEmpty(permission))// With annotations, there must be permission value
{
return false;
}
LoginUser loginUser = SecurityUtils.getLoginUser();
if (StringUtils.isNull(loginUser) ||
CollectionUtils.isEmpty(loginUser.getPermissions()))
{
return false;
}
return hasPermissions(loginUser.getPermissions(), permission);
private boolean hasPermissions(Set permissions, String permission)
{
return permissions.contains(ALL_PERMISSION) ||
permissions.contains(StringUtils.trim(permission)); // Determine whether to hold " All permissions ” character , Or hold the permission
}
Interface permission verification process
Use two examples to explain how the front-end request passes through the back-end interface permission verification .
Login Anonymous request

- Login The request path is
/login, In the filter chainAnnoymousAuthenticationFilterAdd anonymousauthenticationTo Spring In the context . because/loginRequest inSecurityConfig.javaSet anonymous request in , So we can successfully reachSysLoginController. - call
SysLoginService.loginMethod , A key line of command :
Authentication authentication = authenticationManager
.authenticate(new UsernamePasswordAuthenticationToken(username, password));
authenticationManager.authenticate() It's the hook method , stay AbstractUserDetailsAuthenticationProvider To realize , According to the incoming token Type to automatically select , here UsernamePasswordAuthenticationToken Will be made by DaoAuthenticationProvider To deal with it ( If you are not clear, you can set two breakpoints before and after to see the call stack ).
3. stay DaoAuthenticationProvider You can see the key line in :
UserDetails loadedUser = this.getUserDetailsService()
.loadUserByUsername(username);
This will invoke our custom implementation UserDetailsServiceImpl#loadUserByUsername Method ( As shown in the flow chart ), get user Information . As for why you use custom methods , Because in SecurityConfig.java Configured in
@Override
protected void configure(AuthenticationManagerBuilder auth) throws Exception
{
auth.userDetailsService(userDetailsService).passwordEncoder(bCryptPasswordEncoder());
}
- Generate token, Then return .
Logged in request
The logged in request process is simple , In the flow chart some filters It will be customized JwtAuthenticationFilter, It will pass token get user Information , And then load Spring The context of , Easy to extract and use .
Once tangled with the point of stepping on the pit
Due to SpringSecurity Relatively unfamiliar , Although powerful , But its complexity is also greatly improved , So while debugging the project, I read many introductory blog posts , All of them mentioned UsernamePasswordAuthenticationFilter, However, I did not see the call of this filter during repeated debugging in the actual project .
reason :Security Configuration files need to be added httpSecurity.formLogin() Enable form login to use this filter. View all... Used by the project filter You can use the following test code :
class RuoYiApplicationTest {
@Autowired
private FilterChainProxy filterChainProxy;
@Test
public void test() {
List filterChains = filterChainProxy.getFilterChains();
for(SecurityFilterChain sfc:filterChains){
for(Filter filter:sfc.getFilters()){
System.out.println(filter.getClass().getName());
}
}
}
}
边栏推荐
- Selenium - 改变窗口大小,不同机型呈现的宽高长度会不一样
- pytorch练习小项目
- Openresty best practices
- Paper notes vsalm literature review "a comprehensive survey of visual slam algorithms"
- The difference between CONDA and pip
- PMP notes
- Svn branch management
- Mysql database table export and import with binary
- When PHP uses env to obtain file parameters, it gets strings
- Derivation of variance iteration formula
猜你喜欢
scroll-view指定滚动元素的起始位置

ROS+Pytorch的联合使用示例(语义分割)

Important knowledge points of redis
Fluentd facile à utiliser avec le marché des plug - ins rainbond pour une collecte de journaux plus rapide

2022 cisp-pte (III) command execution

Kubesphere - Multi tenant management
arcgis创建postgre企业级数据库
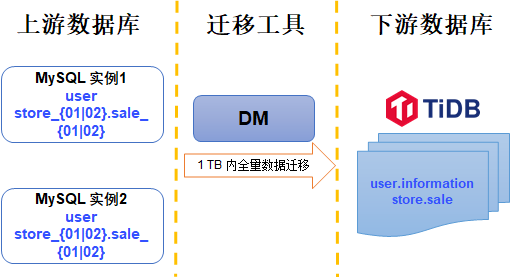
Merge and migrate data from small data volume, sub database and sub table Mysql to tidb
![[5g NR] UE registration process](/img/e3/f881d51fba03010de8c45ea480f3f0.png)
[5g NR] UE registration process
远端rostopic的本地rviz调用及显示
随机推荐
23 design models
PMP notes
爬虫代码基础教学
The win7 computer can't start. Turn the CPU fan and stop it
Floating menu operation
Use @data in Lombok to simplify entity class code
使用conda创建自己的深度学习环境
Paper notes vsalm literature review "a comprehensive survey of visual slam algorithms"
Selenium ide installation recording and local project maintenance
In depth analysis of kubernetes controller runtime
Judge whether the date time exceeds 31 days
arcgis创建postgre企业级数据库
opencv鼠标键盘事件
YOLOV2学习与总结
Important knowledge points of redis
Fluentd is easy to use. Combined with the rainbow plug-in market, log collection is faster
远端rostopic的本地rviz调用及显示
Simple password lock
Numerical method for solving optimal control problem (I) -- gradient method
Local rviz call and display of remote rostopic