当前位置:网站首页>Research on an endogenous data security interaction protocol oriented to dual platform and dual chain architecture
Research on an endogenous data security interaction protocol oriented to dual platform and dual chain architecture
2022-07-04 06:53:00 【Teacher Liu Feng】
Research on an endogenous data security interaction protocol for dual platform and dual chain architecture
Abstract : since “ data + Business ” Since the dual platform architecture was proposed , The efficiency of data security interaction between China and Taiwan is particularly important . Based on this , This study proposes an efficient interactive protocol , With the help of blockchain double chain structure to ensure data security and credibility , It improves the problem of low interaction efficiency of endogenous data between platforms . The experimental simulation results of the threshold signature technology in the new protocol show that the new protocol signs under the chain 、 Compared with the traditional single chain signature and signature verification method, the on chain signature verification process saves 42.1% The cost of time . The new agreement integrates blockchain technology between China and Taiwan 、 Accelerating the extensive practice of the middle platform and blockchain has a positive role .
key word : Double platform and double chain architecture Efficient data interaction protocol Off chain threshold signature Verify the signature on the chain Blockchain
Research on an endogenous data interaction protocol for the dual-middle platform and dual-chain architecture
Abstract : Since dual-middle platform architecture of “data and business” was first proposed, the efficiency of secure data interaction between middle platforms has become particularly important. This paper proposes an efficient interaction protocol, while ensuring data security and credibility with the help of a blockchain dual-chain structure, to optimize the efficiency of endogenous data interaction between middle platforms. By extracting the core threshold signature technology in the new protocol, the simulation experiment showed that the protocol reduced 42.1% of the overhead time used in the off-chain signature and on-chain verification processes compared with the method for traditional single signature and on-chain verification. The new protocol will have a positive impact on the integration of blockchain technology in the middle platform and on accelerating the overall adoption of the middle platform and blockchain.
Keywords: dual-middle platform and dual-chain architectureefficient data exchange protocoloff-chain threshold signatureon-chain verification signatureblockchain
0 lead said The traditional data center mainly serves for data layering and attribute separation , Have the ability to precipitate public data . The data center collects massive data through data technology 、 Calculation 、 Storage 、 machining , A sharing platform that unifies standards and caliber at the same time . It was first developed by Alibaba in 2016 It is proposed in the Research Report of , The purpose is to help realize the global data specification , Try to fully feed the functions of the technology platform development to the front-end applications ^[1]^ . The reason for the emergence of Alibaba data center comes from the ever-changing data needs and high-speed timeliness requirements of many internal business departments , It is necessary to meet the data needs of multiple business front ends , At the same time, we should also deal with the linear scalability of large-scale data and the decoupling of business systems in complex activity scenarios ^[2]^ . however , The concept of data center is still too broad , There are no industrial standards in the industry . At a time when domestic technology companies are competing to carry out large and medium-sized Platform Planning , In recent years, Zhang Jianfeng, chief information officer of Alibaba, has put forward the idea of business platform architecture on different occasions . The so-called business platform means that all application systems must establish contact with it , In order to better realize the core business operation mechanism of an integrated system . Zhang considered using the new idea of integrating business and data to further refine the functions of the middle office . however , The prominent problem in the process of data and business integration is the efficiency of data interaction . When multiple business flows and data flows are transmitted interactively between middle stations , It is difficult to clarify a complete business and data processing process . The mixture of endogenous business information and data information , Lead to the traceability of business flow 、 The scheduling of data flow becomes cumbersome , The security of data interaction also faces certain challenges . therefore , How to ensure that the endogenous data interaction efficiency between the middle office and the platform can be improved in a safe situation to promote the construction of the middle office is an urgent problem to be studied .
For the above problems , This study uses blockchain technology to split the interactive data . Blockchain technology as a new point-to-point computer technology , It can solve the problem of business traceability 、 Provide possible approaches to rough data scheduling problems . With the help of blockchain technical features , On the one hand, empowering “ data + Business ” The privacy protection of the data security circulation and data security storage of the double middle platform system ; On the other hand, with the help of consensus mechanism and economic model , Integrate the resources of blockchain ecology to carry out technology integration and innovation on the actual landing scene . Blockchain technology is integrated into double platforms , But it will not invade the relevant middle office business , It is similar to the underlying technology of the midrange system , It avoids the inefficiency of blockchain technology in processing massive data directly . Make use of blockchain to be open and transparent 、 It is difficult to be tampered with , Be able to transfer the valuable data that has been processed 、 Storage and traceability , So as to ultimately serve the improvement of data interaction efficiency .
This study is based on the different interactive data sources in the middle stage , Put the business flow information and data flow information on the business chain and data chain based on blockchain for storage respectively , Then, an endogenous data interaction protocol for dual platform and dual chain architecture is proposed . Through this Agreement , The core data information authorizes the uplink data information by collecting a certain number of information subjects in the platform , Send legal information to the designated blockchain in batches . meanwhile , The threshold signature algorithm, which is the core of the protocol, is extracted to construct the model of endogenous data interactive flow . Through the experiment , Analyze the time cost of algorithm in data interaction , And with the traditional single signature on the chain 、 Check and compare , It is proved that the protocol has certain advantages in improving the efficiency of data interaction .
1 Research basis **1.1 Current situation of data center ** Many scholars have done relevant research to promote the development of Zhongtai , In summary , The current data stage mode can be divided into the following three .
The first is Alibaba's original data platform , Mainly in order to “ Tai Chung Tai , Small front desk ” Practice of digitalization under the business strategy of ^[2]^ , By dividing different business boundaries and then business modeling , Then guide the service-oriented construction of the system . On the basis of continuing the strategic idea of data in Taiwan put forward by Alibaba , Deng Lijun proposed to keep up with the development trend of the era of big data , By integrating data into the construction of big data center , Realize the data processing of all businesses , To give full play to the value of data assets ^[3]^ .
The second is the business center . Depending on the business needs , Divide different business boundaries and then conduct business modeling , Then guide the service-oriented construction of the system . For the role of the business center , Gong Zhiqi believes that the business center can solve the problem of efficiency , At the same time, it can also reduce the cost of business innovation ^[4]^ . While Zhao Guandong and other scholars are considering improving the design of the omni channel operation support platform architecture based on business mid platform technology , It mainly includes operational activities 、 Operation channel management, supervision and early warning , It also studies the deployment mode and the business content of the operation support platform for power marketing ^[5]^ .
The third is the fragmented middle stage . On the basis of the first two data centers , Split more finely according to business or function , Make the middle stage fragmented , To reduce costs , Further improve organizational efficiency . In this kind of middle stage practice , Fu Wei believes that the data center follows the principles of high centralization and reusability , Service components can be quickly encapsulated on the basis of the middle stage , Provide it to the front desk for convenient use ^[6]^ .
The functions of traditional data are too centralized , In the real business scenario , The system often needs to obtain the data required by the business through different business services . In this way, even if we consider using the distributed system architecture to realize the traditional data console related functions , Cache penetration still exists technically 、 The problem of avalanche effect . To solve this pain point , The usual approach is to conduct data governance , It can more efficiently improve the computing and storage capacity in high concurrency business scenarios ^[7-8]^ . But considering that the demand analysis of the business will change dynamically with different time points , If the new business cannot be handled in time ^[9]^ , It is also impossible to carry out continuous function iteration and technology replacement according to the characteristics of requirements , Then the benefits of data governance will be greatly reduced . therefore “ data + Business ” The form of double platform structure gradually enters the industry .
1.2 “ data + Business ” Double Center Typical “ data + Business ” The dual platform architecture designs data processing and business services in parallel according to the logical order and the attributes of the processing object , So that the business needs analysis can get feedback in time , It helps to alleviate the technical pain point of single data platform business redundancy in the existing data platform , Achieve the purpose of effective data governance . At the same time, the separation of businesses , It also helps to preprocess some business information in advance , So as to improve the business processing efficiency . Universal “ data + Business ” The structure of double middle platform is as follows chart 1 Shown .
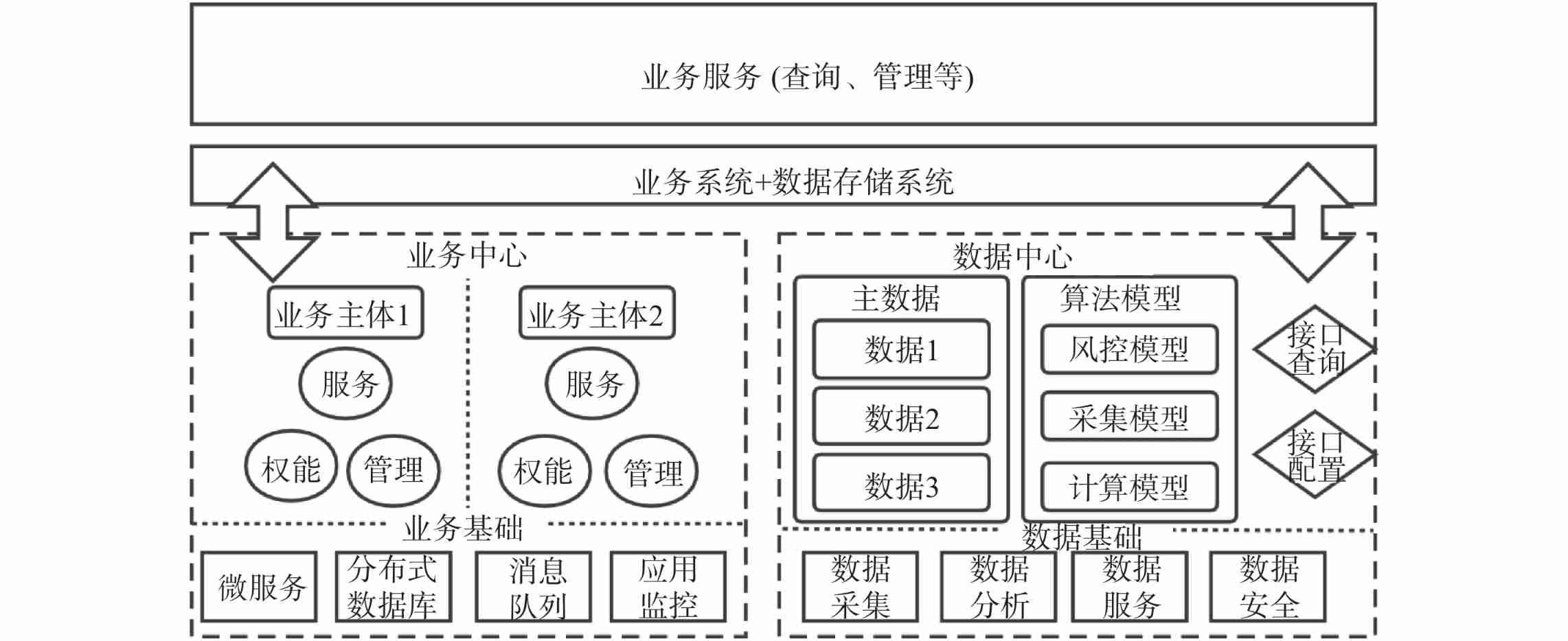 | chart 1 Structure diagram of double middle platform **Fig.1Architectural diagram of dual-middle platform** |
|---|
from chart 1 In the left half of the business, we can see , The basic component of the business platform is the micro service platform 、 Distributed database 、 Message queue and application monitoring , The upper level depends on the different business entities , Allocate different services 、 Power and management measures . The basic component of the right half of the data console is data acquisition 、 Data analysis 、 Data service and data security are four parts , The data center will process different data according to different algorithm models . In the risk control model , The security of master data is required 、 Evaluate and analyze the quality ; In the acquisition model , You need to classify the uploaded data , Collect and integrate similar business data for subsequent processing ; For the calculation model , It mainly extracts the key information in the data for analysis and calculation according to the business needs , Then give the corresponding processing results . Besides , The data center will also provide an interface for data query and give the corresponding data interface configuration , It is convenient to adjust according to service needs , And then call .
Under this dual platform architecture , When doing business analysis , Use the business middle office for processing ; When analyzing data , Then use the data console for processing , Thus reducing the coupling between business and data . At the same time, the two can complement each other 、 Improve each other , Form an enhanced closed loop , And further reduce the redundancy of information in each midrange , Improve certain computing efficiency .
1.3 Dual platform architecture based on blockchain Technology While the data is gradually enriched and improved , Blockchain technology is also maturing . for example , Biya et al. Proposed a double chain structure of user information chain and transaction chain , While ensuring user privacy , Split the business information and transaction data , Reduce the redundancy of node recording information ^[10]^ . Again , Gai Et al. Proposed a conceptual model for integrating blockchain and data platform to create added value ^[11]^ . Li Et al. Also presented a method of using blockchain technology to realize data tracking in the whole data life cycle ^[12]^ .
In view of the previous research , On the basis of double middle stage , In order to better manage data information and business records under the condition of data security and credibility , This research also introduces the dual chain architecture based on blockchain Technology ^[10]^ . According to the needs of specific business and data reading , There will be different consensus mechanisms 、 Different economic models 、 Blockchains with different transaction processing capabilities are combined , In order to build a business system that best meets the actual scenario with the help of different blockchain ecological forces . The specific double chain architecture design is as follows chart 2 Shown .
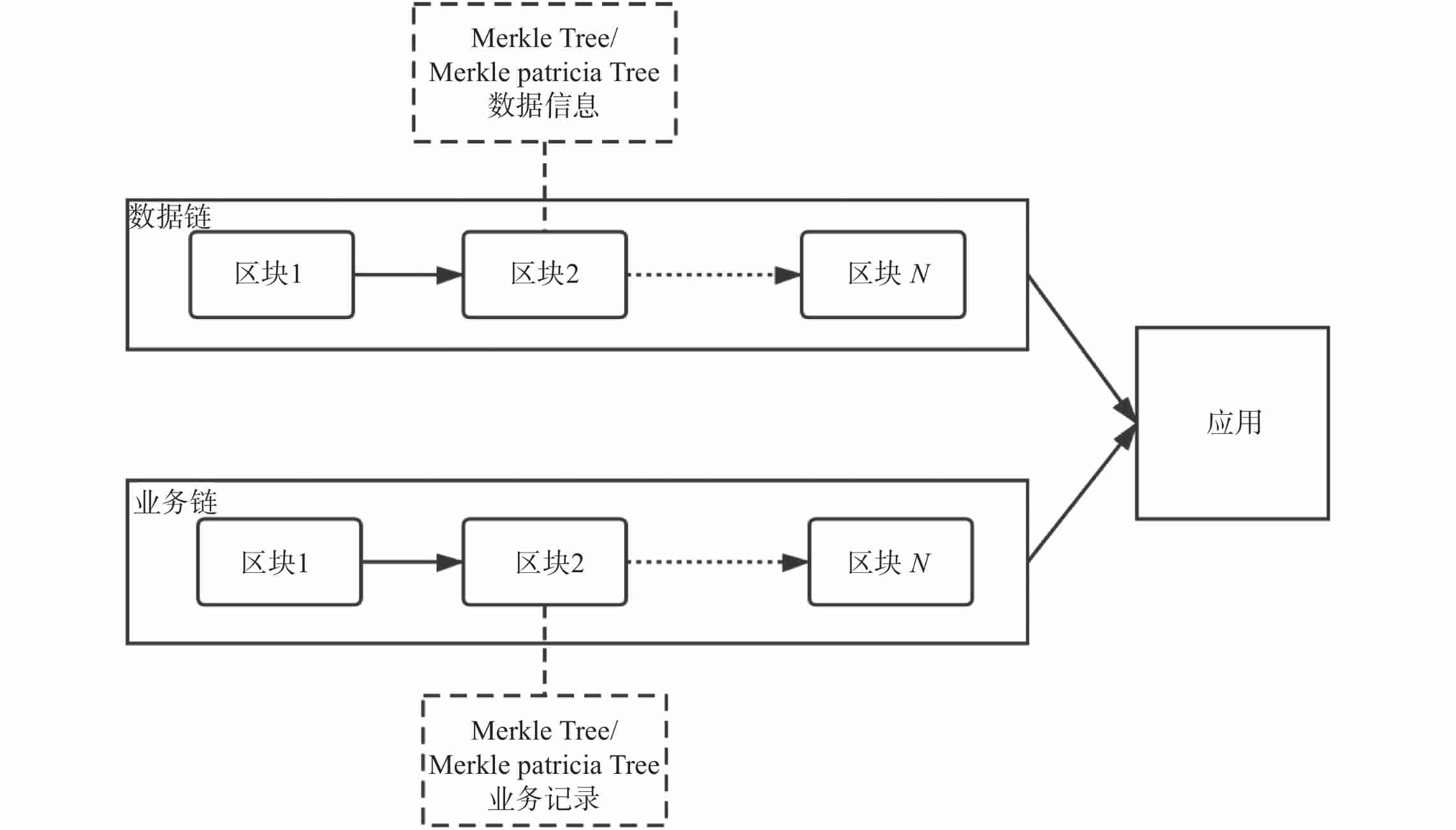 | chart 2 Double chain architecture **Fig.2Architectural diagram of dual-chain** |
|---|
The double chain architecture is split according to the data chain and business chain , And finally serve in an application . Data information is stored in the blocks of the data chain , Business records are stored in the blocks of the business chain . According to business and data characteristics , The data chain in the architecture is regarded as a private chain , The business chain can be a public chain , It can also be an alliance chain . Then according to the data 、 The specific information of the business record decides to adopt the Merkel tree (Merkle Tree) The blockchain of structured storage still uses Merkel Patricia tree (Merkle Patricia Tree) Blockchain with structured storage . At the same time, the number of double chain architecture is not limited to two chains , There may be two kinds of chains distinguished by data type and business type . Each chain can be applied by specific decentralization (Dapp) Or call services for collaborative communication .
Such an implementation will have the following three benefits in terms of endogenous data interaction : 1) Any user node on the chain can view the general business processing without knowing the privacy data information , In this way, while ensuring data security , It also ensures the authenticity of business records ; 2) Separate business records from data information , Compared with single chain processing , At the same time, it can reduce the redundancy of accounting information of most nodes , The throughput performance of the system is improved to a certain extent ; 3) It is convenient for system operation and management , Be able to expand the business logically .
Combine the above basic knowledge , This paper presents the data interaction process under the dual platform and dual chain architecture , Such as chart 3 Shown . First , Input a data source into the data center , After the data is collected by the data center , Perform security analysis on the information in the data source . Then through the data middle office , Store information in the data link . meanwhile , The business data extracted from the data source is handed over to the business console for processing and judgment . Conduct different business processing for different entities , Then transfer it to the business chain to save , And output the result feedback according to the business needs , That is, implement business services .
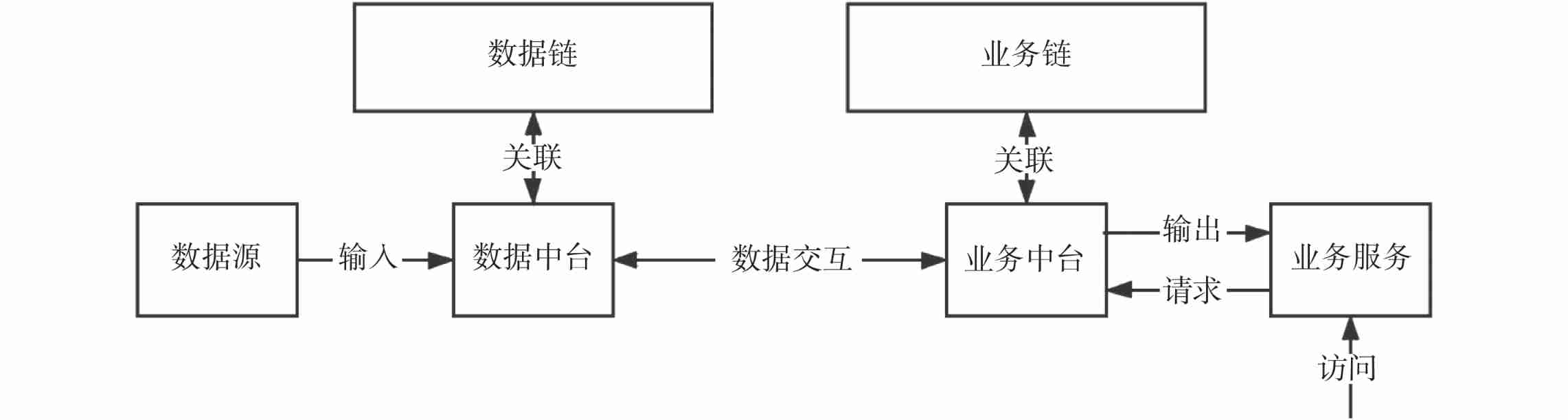 | chart 3 Double platform and double chain interaction process **Fig.3Dual-middle platform and dual-chain interactive process** |
|---|
If the business entity needs to provide relevant services , Then you need to access the business services in the business center , After the business service feeds back to the business middle office , Request the call of relevant data from the data center , And record the business data to the business chain . After receiving the request, the data center will make legal confirmation , Then call the content on the data chain to return , Finally, feed back the content to the business entity . therefore , The architecture design of dual midrange not only effectively improves the accuracy and efficiency of data fragmentation in the service link , At the same time, data coupling is reduced , It is conducive to the pre classification of data sets in future businesses . and , On the basis of taking the double middle platform architecture as the core, it integrates the double chain architecture , Compared with a single blockchain structure, the understanding coupling idea is more effective to distinguish the uplink information . While not using cross chain interaction technology with relatively low efficiency and performance , It can also minimize the amount of concurrent data of blockchain data , Increase throughput , It greatly improves the overall efficiency of the double platform double chain system .
however , When making full use of the technical advantages of the dual platform and dual chain architecture, an unavoidable problem also arises , That is, in order to make full use of the openness and transparency of blockchain 、 Full encryption 、 Advantages of safety traceability , We will face the problem of low efficiency when signing and verifying signatures between double platforms and double chains , Therefore, it is particularly important to design a relatively efficient interaction protocol to improve interaction efficiency .
2 An endogenous data interaction protocol for dual platform and dual chain architecture The following protocol is proposed for the efficiency of data collaboration between the distributed system with dual platforms as the core and the decentralized blockchain system . Such as chart 4 Shown .
combination chart 4, Take the data interaction between business platforms and business chains as an example , The core part of the protocol under study is based on Shure (Shoup) Threshold signature algorithm ^[13]^ To authorize the business records transmitted by the business entity and then upload them . On the one hand, signature generation and verification in Shure threshold signature are completely non interactive , Reduce unnecessary transmission overhead ; On the other hand, Shupu threshold signer identity anti-counterfeiting , Realize the equal distribution of rights among all business entities , Avoid abusing authority to upload malicious business records . The detailed steps of the main algorithms in this protocol are given below .
First step : A polynomial should be randomly selected by the trusted center set in the middle stage $f(x)$ .
| $ f\left( x \right) = \sum\limits_{i = 0}^{t - 1} {{a_i}} {x^i}\;{\rm{mod}}\;p, $ | (1) |
|---|
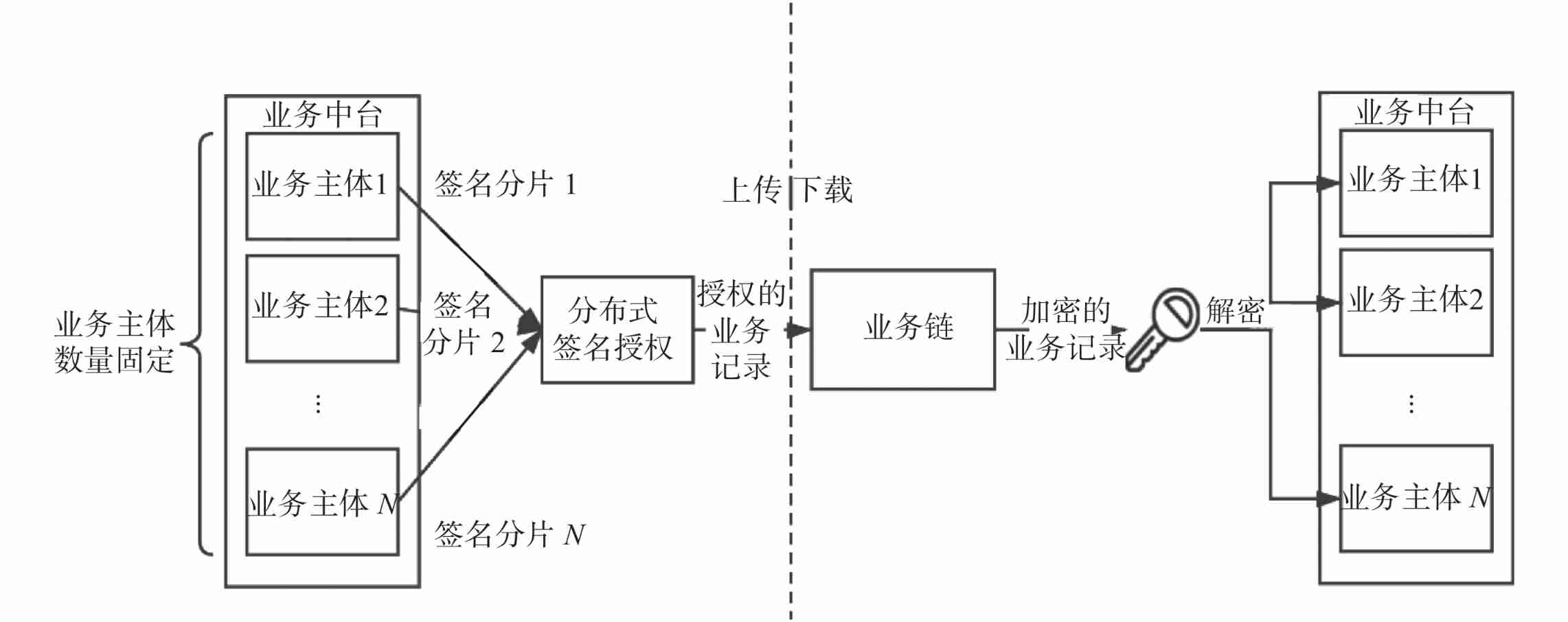 | chart 4 Endogenous data interaction protocol — Take the business center and business chain as an example **Fig.4Endogenous data interactive protocol—using the business platform and business chain as examples** |
|---|
among $ {a}_{0}=d $ Is the initial key parameter ; $ p $ Is the common modulus ; $ t $ Is a safety parameter , Also known as threshold .
The second step : The trusted center needs to calculate $ {d}{j} $ , $ j\in {1,\cdots,N} $ , As the number of the corresponding business entity , And send it to the corresponding business entity in the middle office $ {B}{j} $ , namely :
| ${d_j} = f\left( j \right)\;{\rm{mod}}\;p \to {B_j}.$ | (2) |
|---|
meanwhile , The trusted center also needs to give the public key pair $ (n,e) $ , And calculate $ L =l! $ , $ l $ Is the total number of business entities participating in the business record uplink operation .
The third step : By each business entity $ {B}_{j} $ Calculate business records $ m $ Hash the digest and fragment the signature :
| ${\rm{SigSlide}}_j = H(m)^{2L {d_j}}od \;n.$ | (3) |
|---|
Step four : Generate aggregate signatures , First, calculate according to the formula :
| ${\rm SigSlide}^2_j =H(m)^{4L {d_j}}od n, $ | (4) |
|---|
Then according to the Lagrange interpolation formula :
| $y = H{\left( m \right)^{4{L ^2}d}}od n.$ | (5) |
|---|
Make ${e'}=4{L }^{2}$ , According to the extended Euclidean algorithm, we can know the existence of $ a $ and $ b $ bring $ ae+b{e'}=1 $ , So we can get the final aggregate signature :
| ${\rm sigM} = {x^a}{y^b}od n.$ | (6) |
|---|
Step five : Verify whether the aggregated threshold signature is correct by the on chain contract , Judge according to the following formula :
| ${\rm sigM}^e = H( m )od n.$ | (7) |
|---|
If the equation doesn't hold , Then the uplink fails ; If the equation holds , Then the signature is valid , Allow the transaction records to be encrypted and saved on the chain , Wait until you need to call , Then pull relevant information from the chain to decrypt , Thus, the interaction security of endogenous data is guaranteed to a certain extent .
3 Experimental verification and results This chapter will focus on data interaction before data chaining , First, a formal proof and general algorithm of generalized scenario are given , Then carry out simulation experiments , Test the effectiveness of the protocol in data interaction .
3.1 Formal verification To verify whether the on chain and off chain data collaboration technology in this study is reasonable and effective , Take the lead in giving the algorithm flow chart of formal proof to analyze , Such as chart 5 Shown .
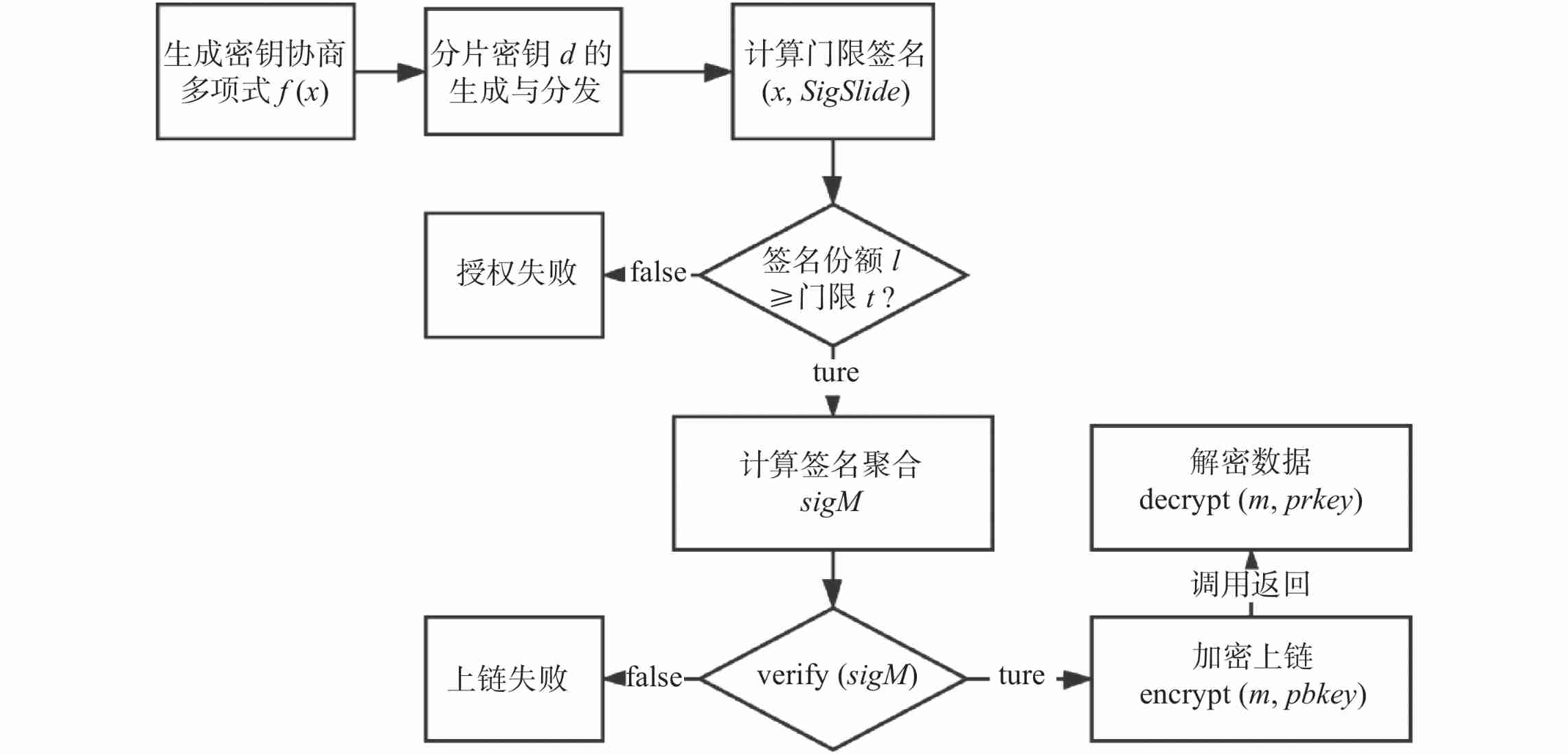 | chart 5 Algorithm flow diagram **Fig.5Algorithm flow diagram** |
|---|
combination chart 5 The algorithm flow chart shown in , First , The first step of the algorithm is based on the formula (1) Generate polynomial of key agreement ; secondly , According to the formula (2) Construct the partition key $ d $ , It is distributed to business subjects or data subjects through anonymous channels .
On this basis , Give threshold signature of business record or data information , And judge whether the number of signatures reaches the threshold specified number , without , Authorization fails , Can't do the following ; If the threshold specified quantity is reached , According to the formula (4)—(6) Calculate an aggregated signature ${\rm sigM}$ ; And then according to the formula (7) To be verified by the contract , Judge the legitimacy of the signature . If it's not legal , Business records or data information will fail to be linked ; If the legitimate , That is, call the encryption function ${\rm encrypted}(\cdots )$ Carry out the encryption and uplink operation of business records or data information , The encryption method is as follows .
| $ c{\text{encypted}}=c{\text{message}}^{k_{\text{pbkey}}}, $ | (8) |
|---|
among $c{\text{message}}$ It is a message that needs to be encrypted , $k{\text{pbkey}}$ Is the public key used for encryption . Finally, if you need to query the content stored on the chain , Then call the decryption function ${\rm decrypted}(\cdots )$ , The decryption method is as follows .
| $ c{\text{decypted}}=c{\text{encypted}}^{k_{\text{prkey}}}, $ | (9) |
|---|
among $k_{\text{prkey}}$ Is the private key used for decryption . After obtaining the plaintext of the decrypted business record or data information , A complete formal proof process is the end .
From the above formal proof, we can see , There were two rounds of questions before the data was linked , One is the verification of the number of signatures during data transmission ; The second is the verification of aggregate signatures , Ensure the safe transmission of data . After the data is linked, it is encrypted by a specific algorithm function , When calling, you only need to decrypt with the corresponding decryption function , You can get complete and reliable data plaintext information .
3.2 General algorithm design This section will introduce the process of data collaboration on and off the chain from the algorithm level , The pseudo code of data interaction call is as follows .
Begin
Input:
callerId; // caller ID
operation; // operation
operationId; // Operation identifier , Is it business operation or data operation
sigM: [SigSlide_1, SigSlide_2 $,\cdots, $ SigSlide_N]; //sigM Sign for aggregation , SigSlide Fragment the signature of a single caller
Output:
message; // Boolean type , Indicates whether the uplink operation is successful
Load Input ; // Load the information flow of the incoming contract under the chain
If (!verifySig(callerId, sigM)) // Verify whether the aggregated signature message is legal
Return false;
If (operationId = 1) // Determine which operation to perform
executeBusiness(); // Perform business operations
Else if (operationId = 2)
executeData(); // Perform data operations
Else
Return false;
If (saveToContract(callerId, operation, sigM)) // Save relevant information to the chain
Return true;
Else
Return false;
End
The first step of the algorithm needs to load the relevant operation information flow of the caller ; The second step is to verify the validity of the aggregate signature , Determine whether the identity of the aggregate signer is legal , And whether the number of signatures in the aggregate signature meets the specified standard , That is to judge how many signature fragments ; Step 3 check the specific operation contents , according to operationId Analyze whether the specific operation is business operation or data operation , Then it is distributed to different chain contracts for processing ; The fourth step is the uplink storage of business records or data information , Add new content to the blockchain through smart contracts for secure storage .
3.3 Simulation of endogenous data interaction process In order to further illustrate the feasibility of endogenous data interaction protocol , The threshold signature algorithm, which plays a key role in improving the efficiency of endogenous data interaction in the extraction protocol, is simulated , Take the interaction between the platform and the business chain as an example , Set the threshold to 6, The number of business entities signing is 13 The plan , Conduct corresponding coding tests . In this test , The main hardware environment is as follows : Intel dual core i7 processor 2.5 GHz、 Memory 8 GB、Win10 System 64 position .
For a single endogenous data interaction , Based on the improved protocol signature coding test results, such as chart 6 Shown .
from chart 6 It can be seen that , news $ m $ 、 Aggregate signature 、 model $ n $ Aggregate signature after 、 Message summaries are all digital streams in the form of large numbers . And according to the previous signature verification formula (7) It's not hard to see. , Aggregate signature $ e $ Power module $ n $ After the signature of the digital flow and message digest module $ n $ The content of the digital stream after is consistent , Thus it is confirmed that chart 6 The signature verification process in is legal and effective .
Although in chart 6 The encrypted message is given in $ m $ 、 Aggregate signature and other signatures 、 Key data content in the signature verification process , But it does not clarify the interaction between these data and the business chain . chart 7 Give the open source smart contract development environment in the same hardware environment Remix Test the two main function interfaces of data upload and download based on the business chain .
chart 7 in , The main function interface of data upload is ${\rm addMessage}\left(\right)$ , The specified business entity needs to correspond to the bytecode value of the aggregate signature after authorization and the encrypted function ${\rm encrypted}(\dots )$ Encrypted message after processing $ m $ The bytecode value of is passed into the function interface , Then judge whether the signature is correct inside the function interface , Then encrypt the message $ m $ The bytecode value of is uploaded to the specified block on the business chain for storage . Wait until you need to download it, and then use another function interface ${\rm getMessage}\left(\right)$ , Enter the mapping number of the corresponding block information to be queried , Then you can get the specified aggregate signature stored in the previous chain and the messages to be decrypted in the chain $ m $ . Last call ${\rm decrypted} (\dots )$ Function decrypts the encrypted message , You can get relevant business records . Besides , The address information of the previously specified business entity can also be obtained in the return value , Facilitate the internal tracking of data source subjects in the business , For effective supervision .
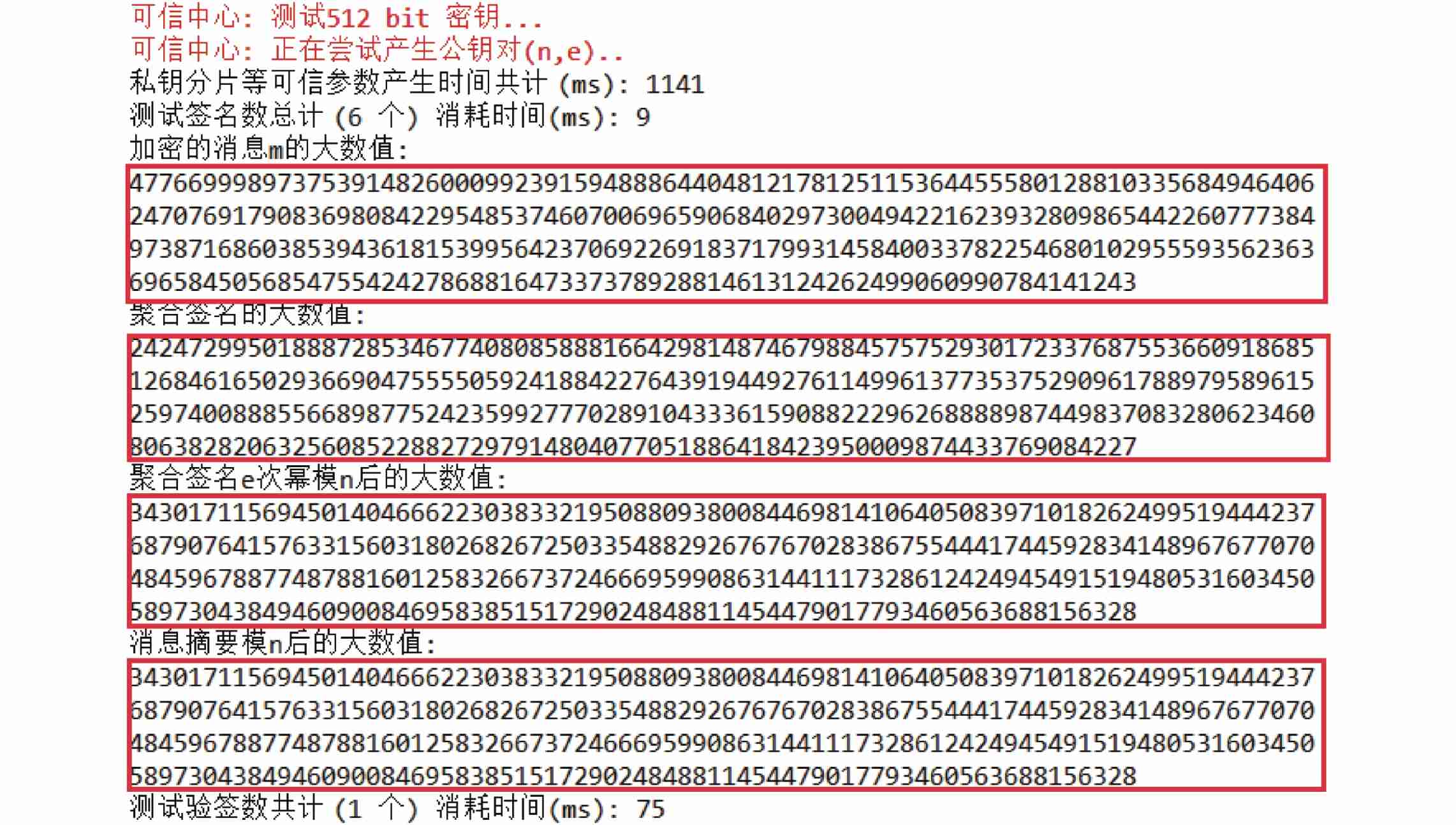 | chart 6 Single signature verification test result diagram **Fig.6Unit testing about results of signature and verification** |
|---|
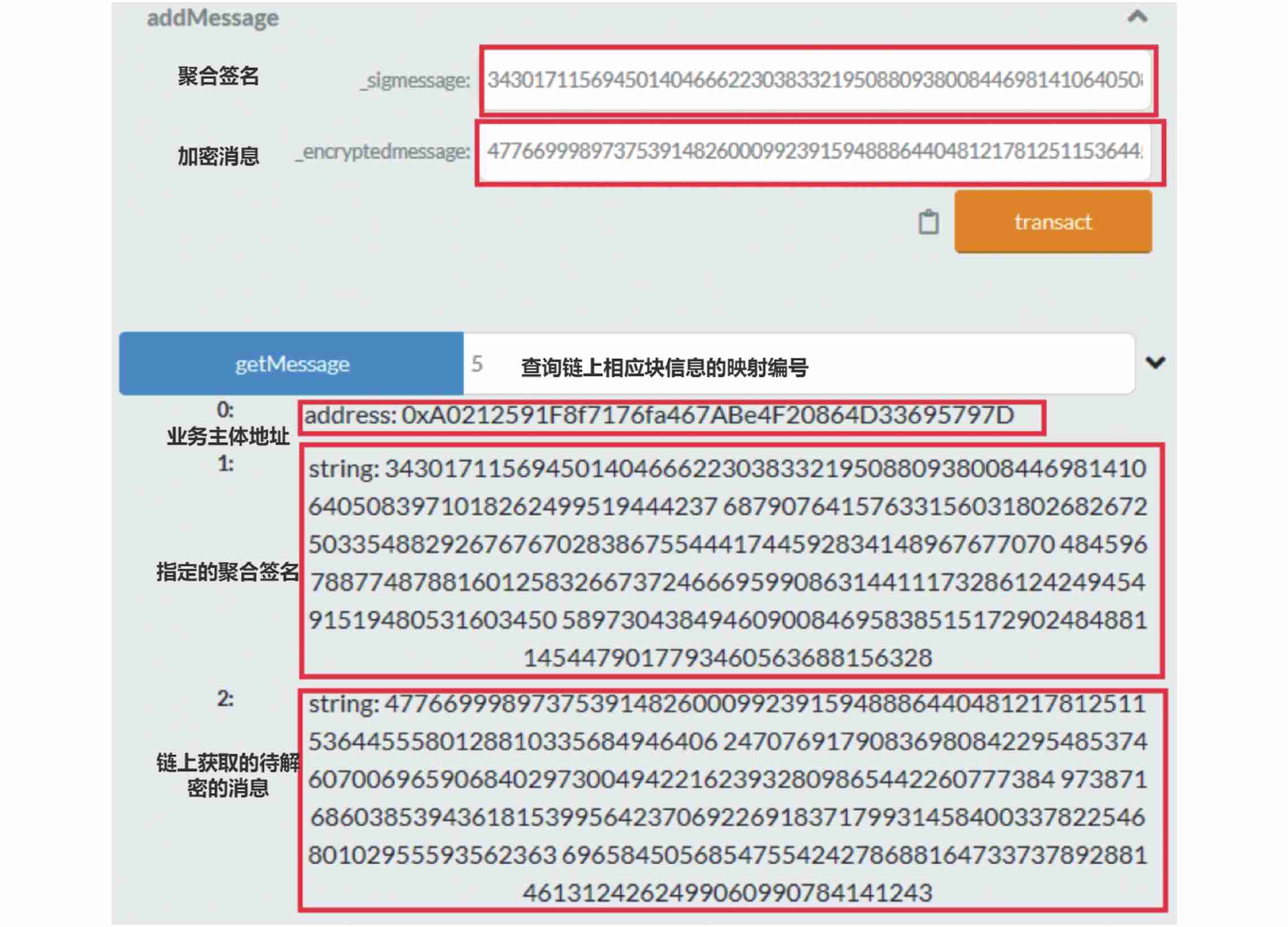 | chart 7 Data upload and download function interface based on business chain **Fig.7Data upload and download parameter result graph based on a business chain** |
|---|
In order to prove that the threshold signature algorithm applied in the protocol can effectively improve the efficiency of endogenous data interaction , This paper sets up three groups of signature verification control groups , They are the off chain signature and the signature verification control group 、 On chain signature and signature verification control group and signature based on Improved Protocol 、 Check and control group . By setting 20 Secondary monomer test , Sign each group 、 The cost of verification is analyzed in detail , The time cost of each test is as follows surface 1 Shown . In this test , The main hardware environment is as follows : Intel dual core i7 processor 2.5 GHz、 Memory 8 GB、Win10 System 64 position .
| surface 1 The time cost of three groups of signatures and signature verification test control group **Tab. 1The overhead time for a control group with three sets of signatures and verification tests** |
|---|
from surface 1 Can be seen in , stay 20 In the secondary monomer test , In general, the signature and signature verification time of the off chain signature and signature verification experimental control group is the shortest . But because if the endogenous data interaction is signed off the chain 、 attestation , Blockchain structure is not involved , Then in business traceability 、 There is no good guarantee for data security , It also has no practical application value . Therefore, we mainly analyze the signatures of the latter two control groups 、 The result of time cost in signature verification . The chain signature and signature verification control group will sign the endogenous data between platforms 、 The process of signature verification is all handled by blockchain , Although in business traceability 、 Data security is guaranteed , However, due to the long time for signature and verification , Therefore, accordingly , The efficiency of data interactive processing will be low . therefore , Taken together , Signature scheme designed by protocol , After signing off the chain, it will be handed over to the chain for signature verification , It can improve the efficiency of data interaction between platforms , With the help of blockchain double chain structure, we can trace the source of middle and Taiwan businesses 、 The goal of accurate data scheduling , And ensure the credibility and security of data .
For a more intuitive comparison, on the premise of using blockchain Technology , The threshold signature scheme in the protocol is different from the traditional single chain signature 、 The time cost of the signature verification scheme , Separate calculation 20 The average of the total time cost of the two schemes' signature and signature verification in the sub monomer test , Give such as chart 8 Column diagram shown . from chart 8 It can be seen that the total time cost of signature and signature verification of the on chain signature and signature verification algorithm is 32067.9 ms, Based on the improved protocol signature algorithm, the total time cost of signature and signature verification of the on chain signature and off chain signature verification algorithm is 18563.3 ms. by comparison , The protocol signature algorithm saves nearly 42.1% The cost of time .
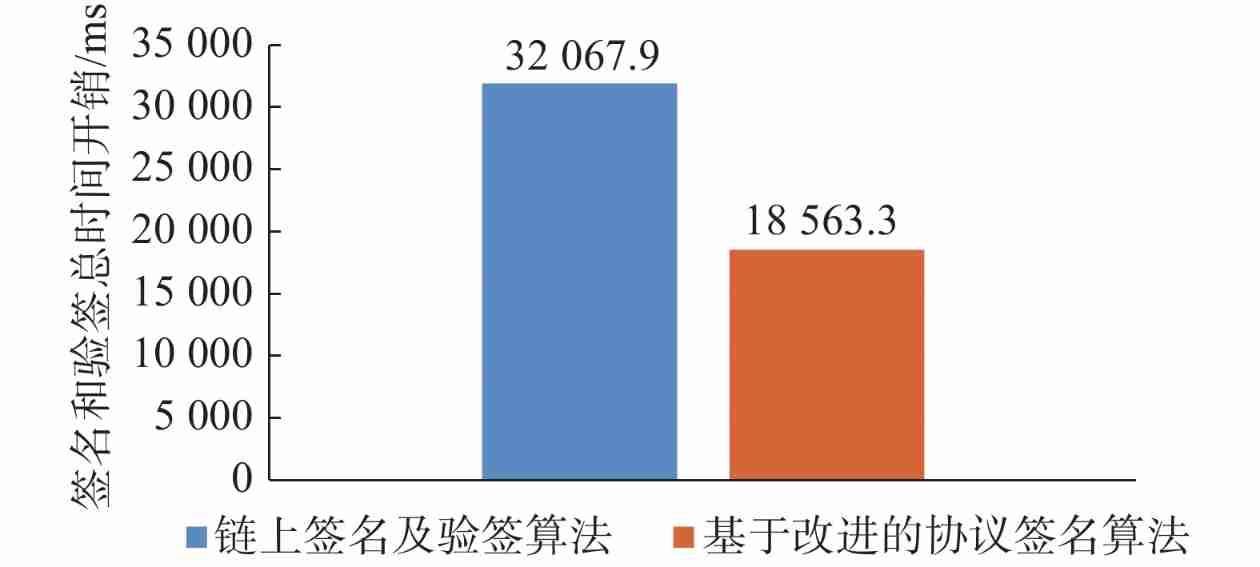 | chart 8 The total time cost of signature and signature verification of two different schemes is compared with the histogram **Fig.8Column chart comparing the total overhead time of signature and verification for two different schemes** |
|---|
Sum up , Experimental results show that the protocol algorithm has high efficiency in the process of endogenous data interaction , The efficiency of signature verification is relatively low , Compared with the traditional single chain signature 、 The way of signature verification , The protocol has high efficiency in the interactive processing of endogenous data .
4 please On This study starts from “ data + Business ” Starting from the design of the double middle platform architecture , Combined with blockchain double chain technology , Cut into the interaction efficiency of the endogenous data in the transmission channel from the data of the dual medium platform to the blockchain , An efficient interactive protocol design is given , The main innovations are as follows .
(1) By introducing blockchain technology into the midrange , Improves the interactive security of endogenous data , It ensures the credibility of midrange data before it is linked . An improved Shure threshold endogenous data interaction protocol is constructed to ensure the security of data before being linked .
(2) Based on the above work, a fusion chain signature is designed 、 The interaction mechanism of signature verification on the chain , It improves the data interaction efficiency of double platforms and double chains . Experimental results show that , This mechanism reduces 42.1% Time cost of , It improves the efficiency of data interaction between the middle platform and blockchain systems .
Of course , The new agreement still faces the following challenges : First , On a technical level , Other technologies must also be integrated , Like big data 、 New technologies such as artificial intelligence , To continuously optimize the technical structure of the middle office . secondly , At the policy level , There should be national support for blockchain Technology , Encourage the implementation of good technical standards and the release of relevant credible norms , Try to avoid technology doing evil in macro-control . Last , At the business level , We need to continue to segment the business structure , It makes the business platform more efficient in extracting relevant information from the data , So as to enhance the business processing ability .
5 junction On This paper proposes an endogenous data interaction protocol for dual platform and dual chain architecture , The realizability of the protocol is proved from the derivation of the algorithm formula . The formal verification is given for the data collaboration between the middle platform and blockchain systems , The key mechanism of collaboration is simulated , The results show that this mechanism can improve the interaction efficiency between endogenous data in the system . This new protocol under the dual platform and dual chain architecture will be beneficial to “ Blockchain + Zhongtai ” The landing application of has certain enlightenment . Of course , Zhongtai is still a developing concept , New problems and demands will continue to arise in the application practice of the middle platform , This will be the direction of continuous research in the future .
reference
| [1] | Eve · Maurice , Li Shu , Ruan Fang , etc. . Platform organization : At the forefront of organizational change “ Preface ” [J]. Harvard Business Review , 2016(10): 108-134. |
|---|---|
| [2] | Tan Hu , Chen Xiaoyong . Explain Alibaba cloud data center in detail , A comprehensive understanding of big data “ online celebrity ” [EB/OL]. Ali data . (2019-09-23) [2020-07-14]. https://dp.alibaba.com/exchange/article?spm=a215hz.13439232.0.0.b2f54aa0InEHIF&articleId=28. |
| [3] | Deng Lijun . Data center and big data center analysis [J]. Electronic world , 2019(22): 85-86. |
| [4] | Gong Zhiqi . On the application and challenge of business platform in ports [J]. Computer products and circulation , 2019(10): 165. |
| [5] | Zhao Guandong , Zhang Caijun , Ouyang Hong , etc. . Research on the architecture design of Omni channel operation support platform based on business platform [J]. Power supply , 2019(6): 67-71. |
| [6] | Fu Wei . Dongfang Jinxin Data Center [J]. Software and integrated circuits , 2019(8): 98. |
| [7] | LI Z, YANG Y. RRect: A novel server-centric data center network with high power efficiency and availability[J]. IEEE Transactions on Cloud Computing, 2018, 914-927. |
| [8] | WIN N W, THEIN T. An efficient big data analytics platform for mobile devices[J]. International Journal of Computer Science and Information Security, 2015, 13(9): 1-10. |
| [9] | ANTHONY A, SHIH Y K, JIN R, et al. Leveraging a graph-powered, real-time recommendation engine to create rapid business value [C]// Proceedings of the 10th ACM Conference on Recommender Systems. 2016: 385-386. |
| [10] | BIA , Zhou Bei , Leng Kaijun , etc. . Public blockchain of pharmaceutical business resources based on double chain architecture [J]. Computer science , 2018, 45(2): 40-47. |
| [11] | GAI K, CHOO K K R, ZHU L. Blockchain-enabled reengineering of cloud datacenters[J]. IEEE Cloud Computing, 2018, 5(6): 21-25. |
| [12] | LI H C, GAI K K, FANG Z K, et al. Blockchain-enabled Data Provenance in Cloud Datacenter Reengineering [C]// Proceedings of the 2019 ACM International Symposium on Blockchain and Secure Critical (BSCI’19). New York: Association for Computing Machinery, 2020: 68-74. |
| [13] | SHOUP V. Practical threshold signatures [C]// International Conference on the Theory and Applications of Cryptographic Techniques. Berlin: Springer-Verlag, 2000: 207-220. |
边栏推荐
- selenium IDE插件下载安装使用教程
- How can the old version of commonly used SQL be migrated to the new version?
- 响应式移动Web测试题
- Tar source code analysis 9
- 【FPGA教程案例7】基于verilog的计数器设计与实现
- [GF (q) + LDPC] regular LDPC coding and decoding design and MATLAB simulation based on the GF (q) field of binary graph
- tars源码分析之6
- What is the use of cloud redis? How to use cloud redis?
- what the fuck! If you can't grab it, write it yourself. Use code to realize a Bing Dwen Dwen. It's so beautiful ~!
- The sorting in C language realizes the number sorting method from small to large
猜你喜欢
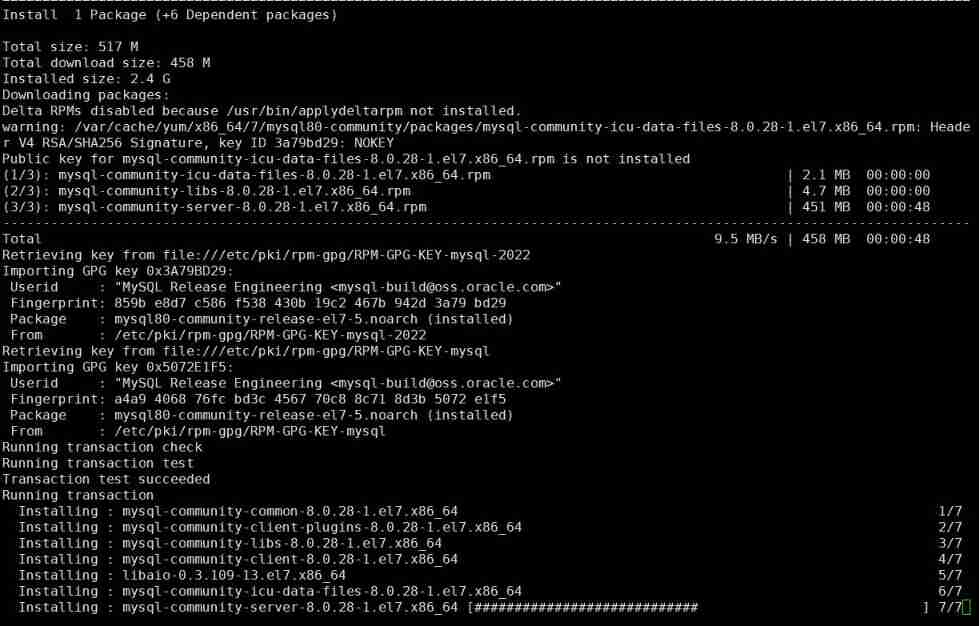
MySQL relearn 2- Alibaba cloud server CentOS installation mysql8.0
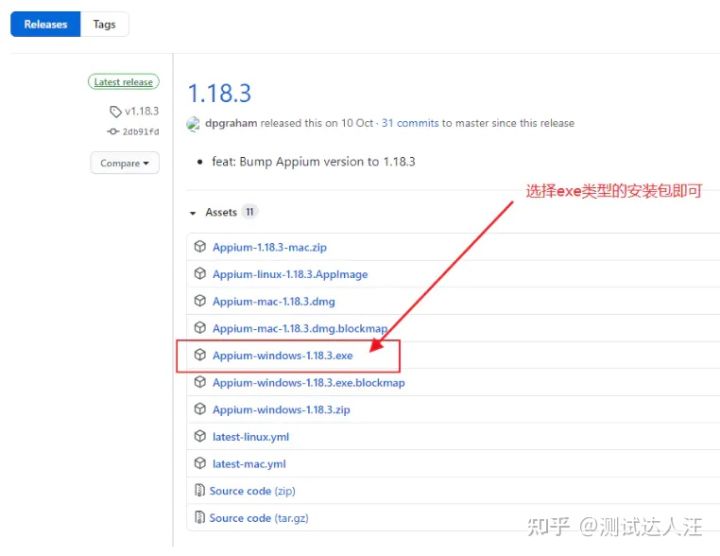
Appium foundation - appium installation (II)
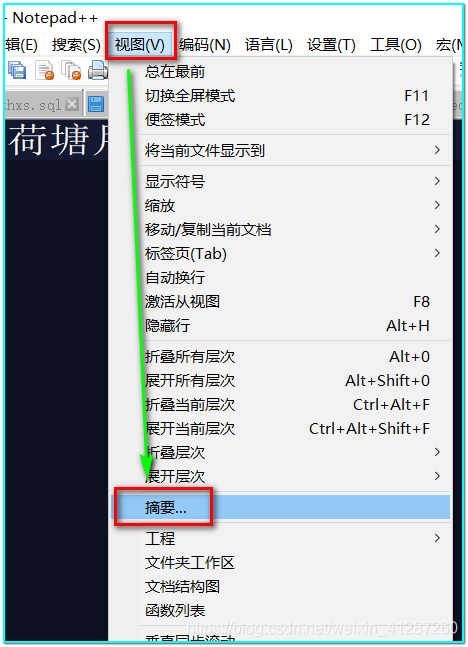
notepad++如何统计单词数量
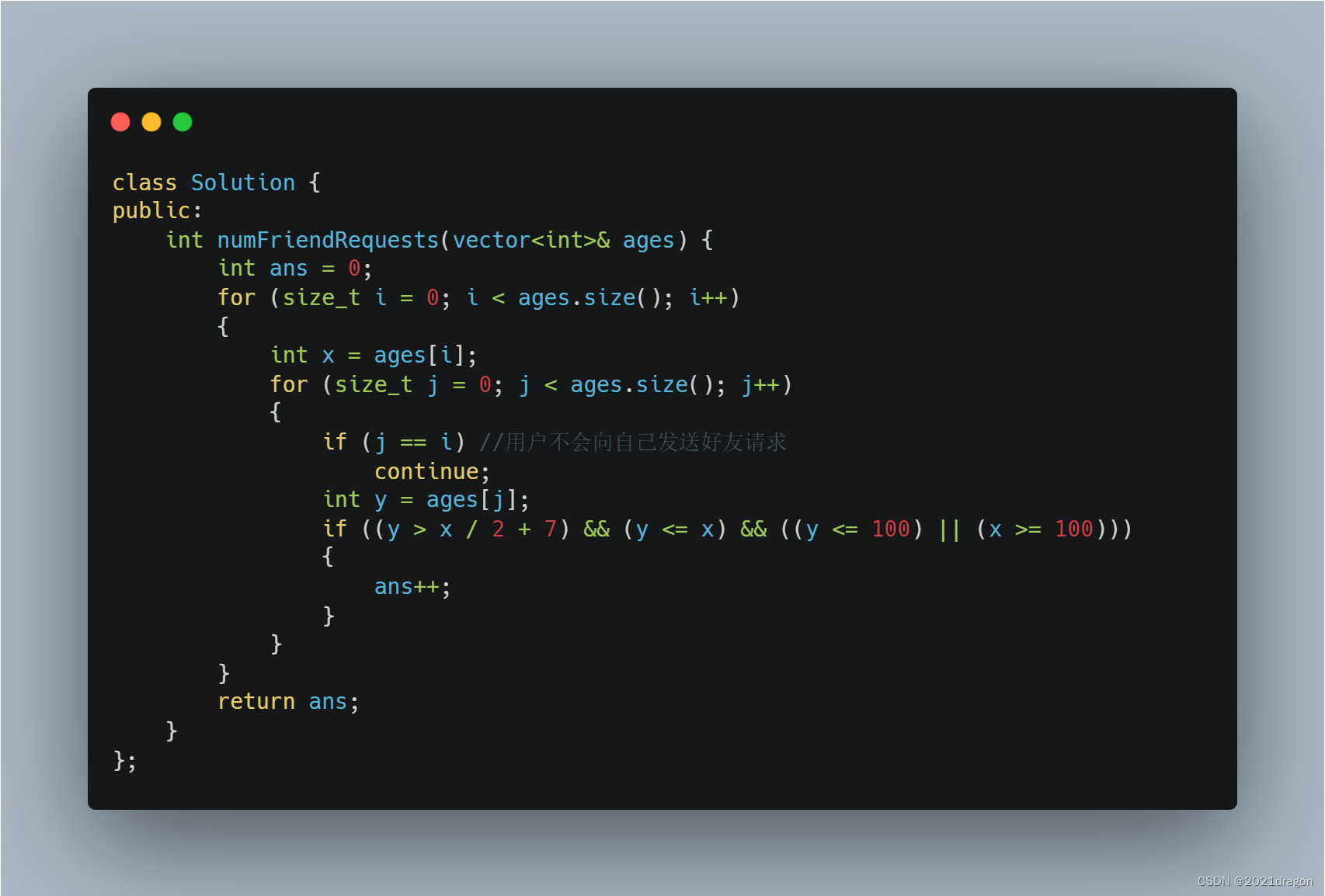
leetcode825. Age appropriate friends
MySQL 45 lecture learning notes (VII) line lock

Another company raised the price of SAIC Roewe new energy products from March 1
![[number theory] fast power (Euler power)](/img/1e/5d032c8f2e43f553b4543d28ea2a2d.jpg)
[number theory] fast power (Euler power)

Common usage of time library
P26-P34 third_ template

what the fuck! If you can't grab it, write it yourself. Use code to realize a Bing Dwen Dwen. It's so beautiful ~!
随机推荐
请问旧版的的常用SQL怎么迁移到新版本里来?
the input device is not a TTY. If you are using mintty, try prefixing the command with ‘winpty‘
Mysql 45讲学习笔记(七)行锁
[GF (q) + LDPC] regular LDPC coding and decoding design and MATLAB simulation based on the GF (q) field of binary graph
Displaying currency in Indian numbering format
JS common time processing functions
MySQL 45 lecture learning notes (x) force index
MySQL 45 lecture learning notes (12) MySQL will "shake" for a while
Common usage of time library
高薪程序员&面试题精讲系列119之Redis如何实现分布式锁?
The final week, I split
tars源码分析之2
GoogleChromePortable 谷歌chrome浏览器便携版官网下载方式
Tar source code analysis 9
What is tweeman's law?
Code rant: from hard coding to configurable, rule engine, low code DSL complexity clock
MySQL 45 lecture learning notes (XIV) count (*)
校园网络问题
2022, peut - être la meilleure année économique de la prochaine décennie, avez - vous obtenu votre diplôme en 2022? Comment est - ce prévu après la remise des diplômes?
Software keywords and process information intercepted by Golden Shield video player