当前位置:网站首页>leetcode825. Age appropriate friends
leetcode825. Age appropriate friends
2022-07-04 06:48:00 【2021dragon】

LeetCode Series articles
List of articles
One 、 Title Description
On social media sites n n n Users . Give you an array of integers a g e s ages ages, among a g e s [ i ] ( 1 ≤ a g e s [ i ] ≤ 120 ) ages[i](1\leq ages[i] \leq 120) ages[i](1≤ages[i]≤120) It's No i i i Age of users .
If any of the following conditions is true , So users x x x The user will not be y y y Send friend request :
- a g e s [ y ] ≤ 0.5 × a g e s [ x ] + 7 ages[y]\leq0.5\times ages[x]+7 ages[y]≤0.5×ages[x]+7
- a g e s [ y ] > a g e s [ x ] ages[y]>ages[x] ages[y]>ages[x]
- a g e s [ y ] > 100 & & a g e s [ x ] < 100 ages[y]>100\&\&ages[x]<100 ages[y]>100&&ages[x]<100
otherwise , x x x Will y y y Send a friend request .
Be careful , If x x x towards y y y Send a friend request , y y y You don't have to x x x Send a friend request . in addition , Users will not send friend requests to themselves .
Returns the total number of friend requests generated on this social media site .
Two 、 Example
Input : ages = [16, 16]
Output : 2
explain : 2 People send friend requests to each other .
3、 ... and 、 Main idea
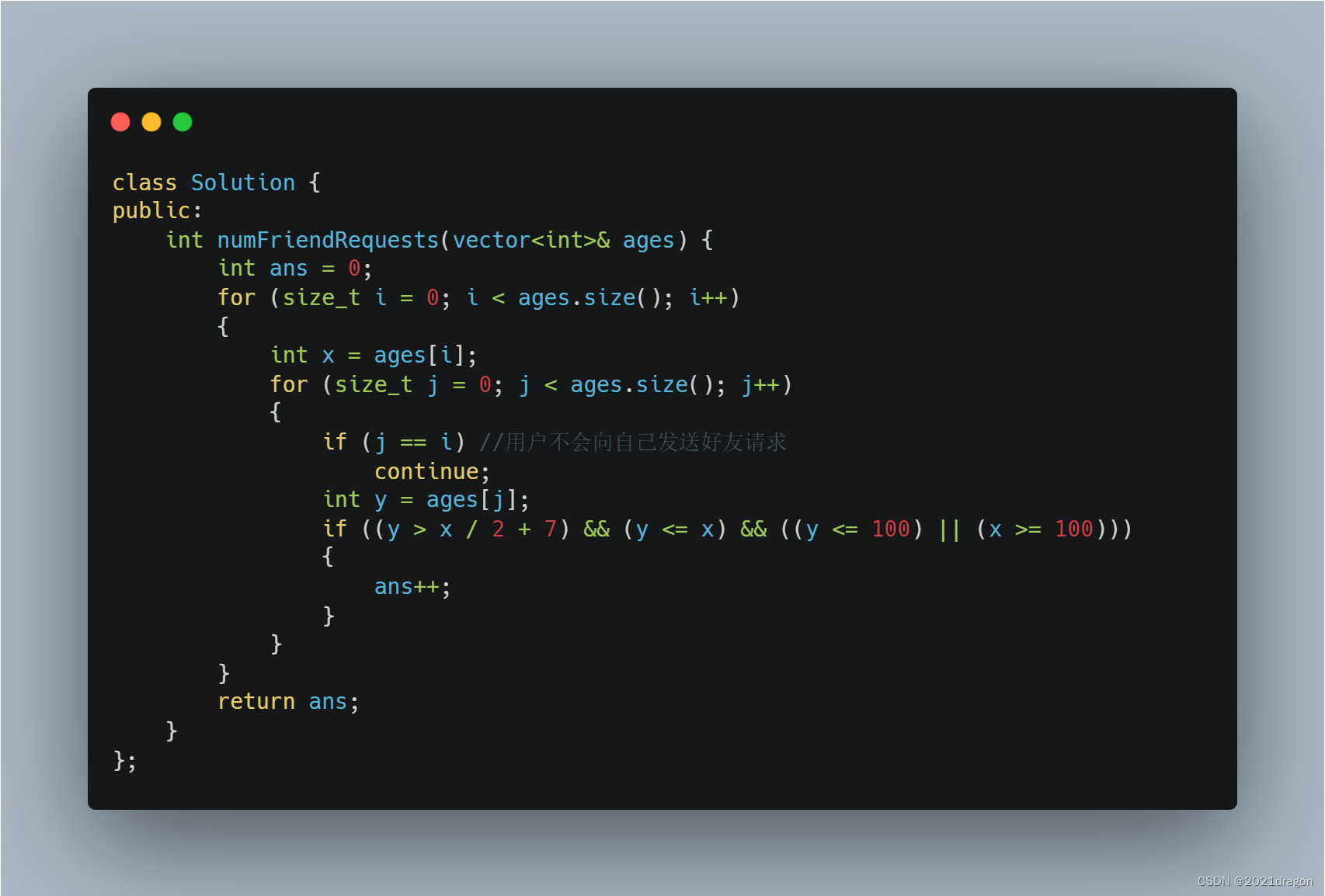
1、 Violence solution
It is very simple to solve the problem with violent solution , To determine which users a user can send friend requests , Just traverse this n − 1 n-1 n−1( Not including myself ) Users , Judge whether the conditions for sending friend requests are met in turn .
Obviously, the time complexity of this violent solution is O ( N 2 ) O(N^2) O(N2), When the amount of user data is too large, the computing time will soar , Therefore, this solution is not recommended .
2、 Sort + Double pointer
Carefully observe the three conditions given by the topic , You will find that condition three is actually contained in condition two , If condition 3 is met, condition 2 must be met , So as long as the first two conditions are not met , So users x x x You can tell users y y y Send friend request , That is, users y y y Need to meet : 0.5 × a g e s [ x ] + 7 < a g e s [ y ] ≤ a g e s [ x ] 0.5\times ages[x]+7<ages[y]\leq ages[x] 0.5×ages[x]+7<ages[y]≤ages[x]
This relationship is represented by a number axis as follows :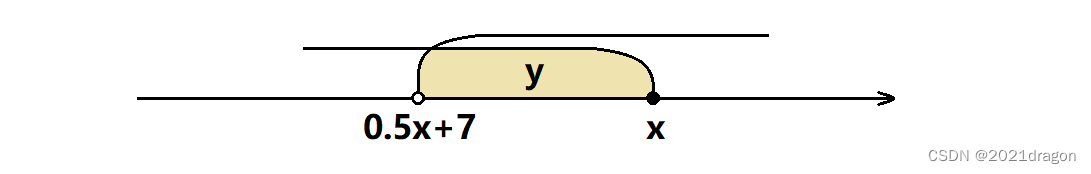
If there are users who meet the requirements y y y, that 0.5 × x + 7 < x 0.5\times x+7<x 0.5×x+7<x, namely x > 14 x > 14 x>14. in other words , If a user's age is less than or equal to 14, Then the user will not be able to send friend requests to any user .
Now it seems , Want to know the user x x x To which users y y y Send friend request , In fact, it is necessary to find the corresponding left and right boundaries on the number axis , Users whose age is in this area are users x x x Users who can send friend requests .
When looking for the left and right boundaries, you can use l e f t left left and r i g h t right right Subscript indicating the left and right boundaries ( Double pointer ), If you use closed intervals on both sides , namely l e f t left left It points to the first user who meets the requirements , r i g h t right right It refers to the last user who meets the requirements , So in the end r i g h t − l e f t right-left right−left The value of is the user who meets the requirements y y y The number of .( Be careful : It's not here r i g h t − l e f t + 1 right-left+1 right−left+1, Because the user x x x It is also in the region , But users x x x Don't send friend requests to yourself )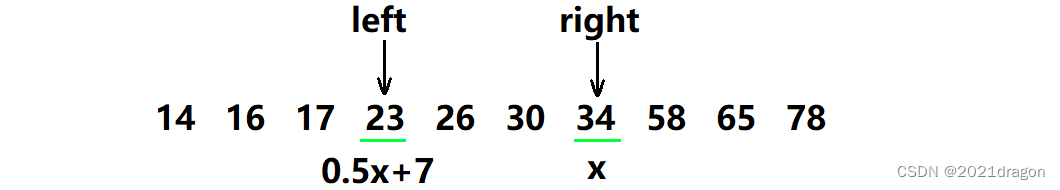
So the steps to solve the problem are as follows :
- To the given n n n Sort by the age of users .
- Traverse this one by one n n n Age of users .
- When traversing users , If the user's age is less than or equal to 14, Then the number of friend requests that the user can send out is 0; If the user is older than 14, Then find the area that meets the transmission requirements through the double pointer , Then we can get the number of friend requests that the user can send out .
- Finally, add up the number of friend requests that each user can send out .
Particular attention , When determining the age area that meets the requirements through the double pointer , Only for the first time n n n Search from scratch based on users . Later, when determining the area , The left and right boundaries of the region only need to be searched backwards based on the left and right boundaries of the previous user . because 0.5 × x + 7 0.5\times x+7 0.5×x+7 And x x x It's a linear relationship , When x x x When it increases , 0.5 × x + 7 0.5\times x+7 0.5×x+7 The value of will also increase , So we don't need to judge the last user's l e f t left left Whether the user's age before the pointer is in this limited area .
3、 Count sorting + The prefix and
If you look closely, you will find that the age of the given user of the title is [ 1 , 120 ] [1, 120] [1,120] Within the scope of , Therefore, we can count and sort the number of users of all ages .
For example, we store the sorting results in c n t cnt cnt In the array , here c n t [ a g e ] cnt[age] cnt[age] It means that the age is a g e age age Number of users , And each age is a g e age age The number of friend requests that users can send out is : ( ∑ i = 0.5 × a g e + 8 a g e c n t [ i ] ) − 1 (\sum_{i=0.5\times age+8}^{age}cnt[i])-1 (∑i=0.5×age+8agecnt[i])−1, One minus one is because users will not send friend requests to themselves .
To avoid traversing every time c n t cnt cnt Sum arrays , We can calculate c n t cnt cnt Array prefix and array p r e pre pre, p r e [ a g e ] pre[age] pre[age] It represents the age group located in 1 ~ age Number of users : p r e [ a g e ] = ∑ i = 1 a g e c n t [ i ] pre[age]=\sum_{i=1}^{age}cnt[i] pre[age]=∑i=1agecnt[i].
At this time, each age is a g e age age The number of friend requests that users can send out can be written as : p r e [ a g e ] − p r e [ 0.5 × a g e + 7 ] − 1 pre[age]-pre[0.5\times age+7]-1 pre[age]−pre[0.5×age+7]−1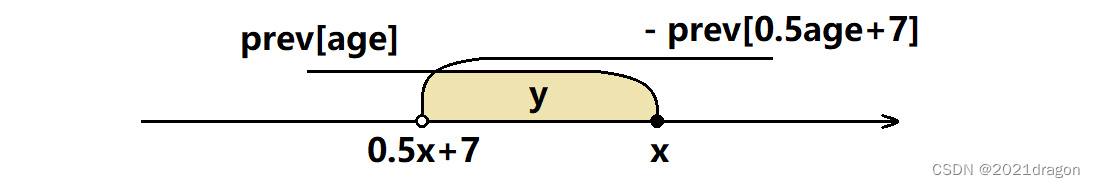
At this point, we can O ( 1 ) O(1) O(1) Calculate an age of a g e age age The number of friend requests that users of can send out , Multiply this value by c n t [ a g e ] cnt[age] cnt[age] It is the total number of friend requests that all users in this age group can send out .
So the steps to solve the problem are as follows :
- Count and sort the number of users in each age group .
- Count out c n t cnt cnt Array prefix and array p r e pre pre.
- adopt ( p r e [ a g e ] − p r e [ 0.5 × a g e + 7 ] − 1 ) × c n t [ a g e ] (pre[age]-pre[0.5\times age+7]-1)\times cnt[age] (pre[age]−pre[0.5×age+7]−1)×cnt[age] The formula calculates the total number of friend requests that users of each age group can send out , Adding them up is the final result .
Four 、 Code implementation
1、 Violence solution
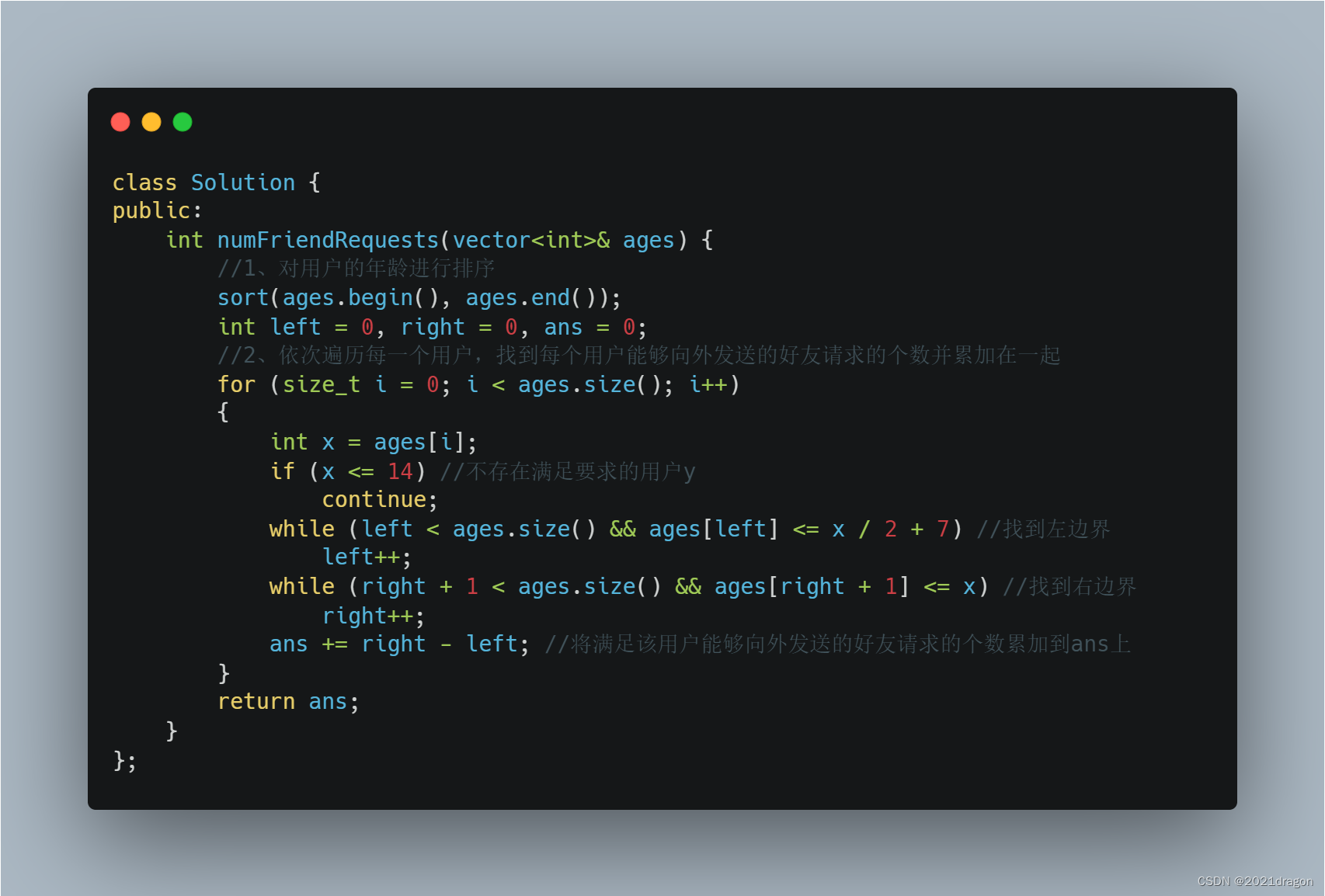
2、 Sort + Double pointer
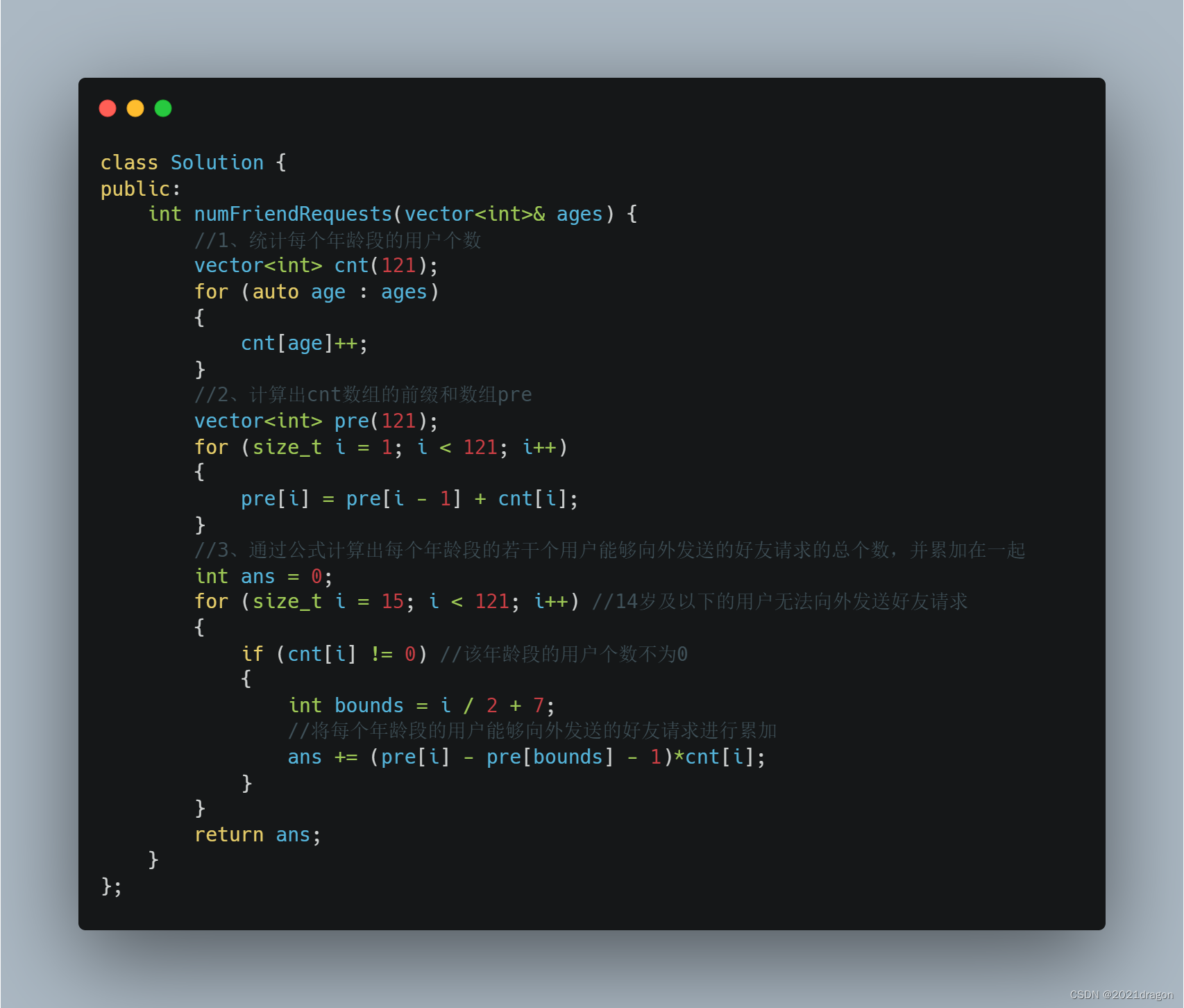
3、 Count sorting + The prefix and
边栏推荐
- Wechat applet scroll view component scrollable view area
- ADC voltage calculation of STM32 single chip microcomputer
- JS common time processing functions
- [network data transmission] FPGA based development of 100M / Gigabit UDP packet sending and receiving system, PC to FPGA
- Lottery system test report
- Cervical vertebra, beriberi
- [number theory] fast power (Euler power)
- Tar source code analysis 9
- uniapp 自定義環境變量
- Dimension and format of data
猜你喜欢
centos8安装mysql.7 无法开机启动
17-18. Dependency scope and life cycle plug-ins
27-31. Dependency transitivity, principle
Tree DP
notepad++如何统计单词数量

Another company raised the price of SAIC Roewe new energy products from March 1
selenium驱动IE常见问题解决Message: Currently focused window has been closed.
Uniapp custom environment variables
![[GF (q) + LDPC] regular LDPC coding and decoding design and MATLAB simulation based on the GF (q) field of binary graph](/img/5e/7ce21dd544aacf23b4ceef1ec547fd.png)
[GF (q) + LDPC] regular LDPC coding and decoding design and MATLAB simulation based on the GF (q) field of binary graph
Google Chrome Portable Google Chrome browser portable version official website download method
随机推荐
tars源码分析之1
centos8安装mysql.7 无法开机启动
tars源码分析之7
What is a spotlight effect?
Mysql 45讲学习笔记(十三)表数据删掉一半,表文件大小不变
MySQL 45 lecture learning notes (x) force index
Bicolor case
ADC voltage calculation of STM32 single chip microcomputer
颈椎、脚气
what the fuck! If you can't grab it, write it yourself. Use code to realize a Bing Dwen Dwen. It's so beautiful ~!
Boast about Devops
Analysis of tars source code 1
What is Gibson's law?
Cochez une colonne d'affichage dans une colonne de tableau connue
8. Factory method
List of top ten professional skills required for data science work
notepad++如何统计单词数量
【MySQL】数据库视图的介绍、作用、创建、查看、删除和修改(附练习题)
MySQL learning notes 3 - JDBC
Can the out of sequence message complete TCP three handshakes