当前位置:网站首页>Stealing others' vulnerability reports and selling them into sidelines, and the vulnerability reward platform gives rise to "insiders"
Stealing others' vulnerability reports and selling them into sidelines, and the vulnerability reward platform gives rise to "insiders"
2022-07-04 21:15:00 【CSDN program life】
In today's highly developed network big data era , The development of each company depends on the blessing of the Internet . But at the same time , Various security vulnerabilities 、 Illegal cracking and other problems emerge in endlessly , No matter how perfect the system is, it will also be vulnerable Bug.
In this context , Instead of letting hackers find and attack security vulnerabilities that are hard to find , It's better to pay “ White hat hacker ” Disclose first , Then make repairs as soon as possible .
As mentioned in this article HackerOne Is a world-famous “ White hat hacker ” Gathering place , It is used to coordinate vulnerability disclosure , And provide an intermediary platform for vulnerability hunters who submit security reports with monetary rewards .

But in recent days ,HackerOne It was revealed that one of its internal employees stole the vulnerability report submitted by others through the vulnerability reward platform , And disclose the relevant reports to the affected customers to obtain economic rewards .
The culprit is locked
6 month 22 Japan ,HackerOne Received a request from a customer , Ask them to investigate a use "rzlr " Suspicious vulnerabilities disclosed by the person of the account through non platform communication channels . The customer noticed , The same security issue has been passed before HackerOne Submitted .
Generally speaking , Vulnerability collision , That is, multiple researchers find and report the same safety problems , It happens all the time . under these circumstances , There are obvious similarities between real reports and reports from threat actors , This urges people to observe carefully .
HackerOne After investigation, it is determined , One of its employees is from 4 month 4 Joined the company on the th to 6 month 23 Japan , The platform system has been accessed for more than two months , Seven companies were contacted to report vulnerabilities that had been disclosed through their systems .
The theft vulnerability report is sold off as a sideline
The company said , The rogue employee received a reward from some reports submitted by him . This makes HackerOne Be able to track the whereabouts of money , And determine whether the perpetrator is “ Numerous customer projects ” One of the staff who disclosed the diversion vulnerability .
“ The threat actor created a HackerOne Puppet account , And received a reward in a few disclosures . After determining that these rewards may be improper , The company contacted the relevant payment supplier , They cooperated with us to provide more information .”——HackerOne
After analyzing the network traffic of the threat actor ,HackerOne More evidence has been found to link their main accounts on the platform with puppet accounts . Finally, less than... After the investigation 24 Hours of time ,HackerOne Identified the threatening actor , And terminated his system access 、 Locked his laptop remotely .
In the next few days ,HackerOne The suspect's computer was imaged and analyzed by remote forensics , And reviewed the data access log of the employee during work , To identify all vulnerability bounty projects that the threat actor has interacted with .
6 month 30 Japan ,HackerOne Fired the threatening actor :
“ According to the examination with the lawyer , We will decide whether it is appropriate to conduct criminal transfer of this matter . We continue to conduct forensic analysis on logs generated by former employees and equipment used .”—— HackerOne
HackerOne Pointed out that , Its former employees used “ Threatening ” and “ Intimidating ” Language , And urge customers to contact the company when they receive the disclosure made in an offensive tone .
HackerOne Express ,“ In the vast majority of cases ”, It has no evidence that vulnerable data has been misused . However , Reports of visits by internal threat actors , Whether for malicious or legal purposes , Have been separately informed of the access date and time of each vulnerability disclosure .
HackerOne He also sent an email to inform hackers who submitted content on the platform that had been visited by rogue employees :
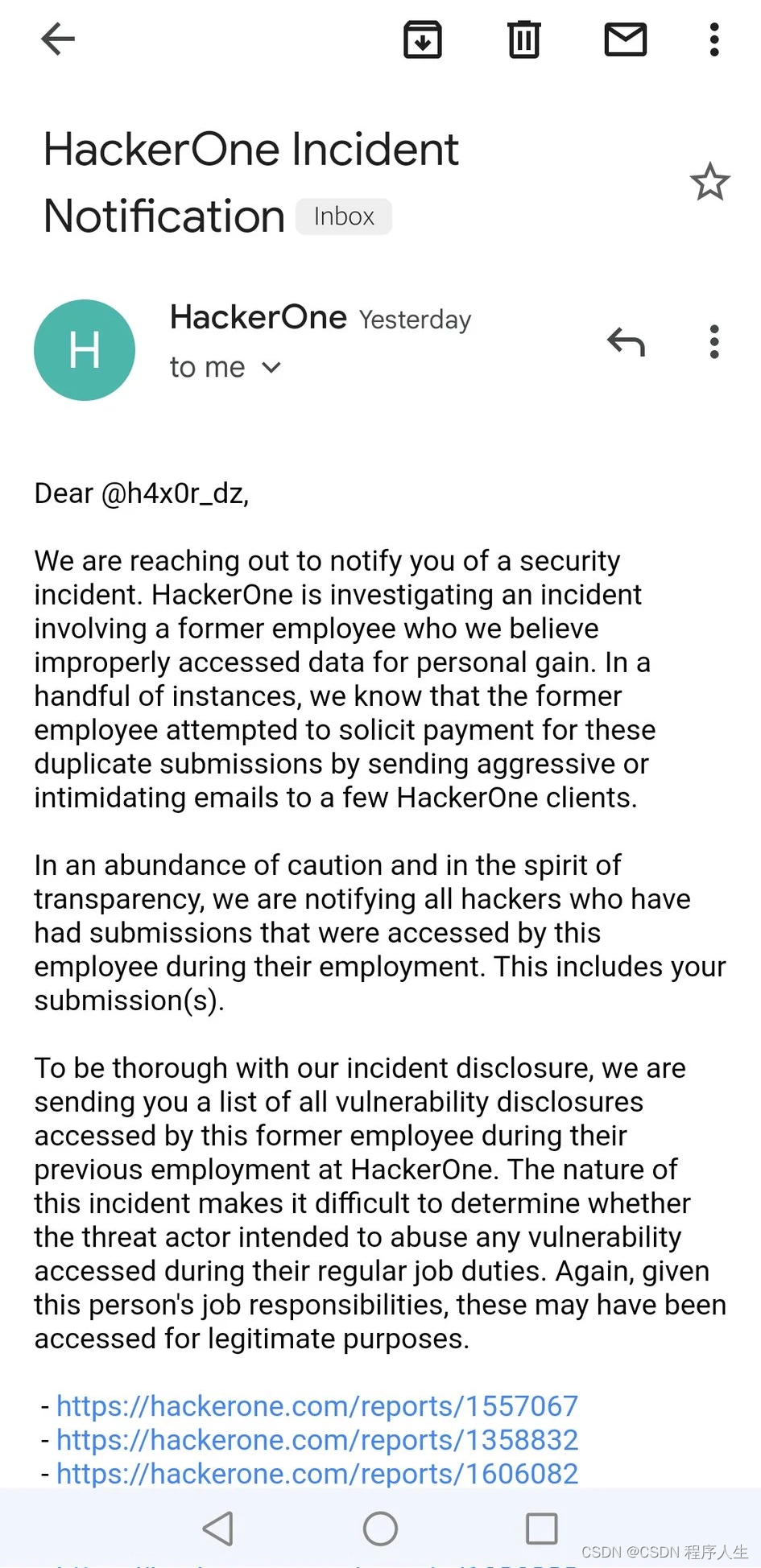
source :@H4x0r-DZ twitter
Email the hackers concerned about the incident , It also includes a list of reports of legitimate visits by threatening actors , As part of its work , Or intended to abuse the submitted vulnerability report . Besides , All reports submitted by this former employee are marked as duplicates , It will not affect the payment of legal security personnel .
HackerOne In the event report, it is concluded that :“ To make a long story short , This is a serious incident . We believe that the access of internal personnel has now been controlled . Internal threat is one of the most insidious threats in network security , We are ready to make every effort to reduce the possibility of such events in the future .”
Reference link :
3.A HackerOne Employee Stole Vulnerability Reports From Security Researchers | PCMag
Twenty years ago ,《 The programmer 》 When it was first published , We should pay full attention to the growth of software people . today , Our original intention remains the same : Behind the lines of code , It's a living developer's ambition to change the world . therefore ,《 New programmers 004》 from C++ The father of Bjarne Stroustrup、C# The father of Anders Hejlsberg、MySQL The father of Michael "Monty" Widenius、PostgreSQL Co founder of global development group Bruce Momjian Wait for the programmer's grandfather , Go to jiayangqing, vice president of Alibaba 、 Pan Aimin, founder and chairman of instruction set 、Vue.js By you Yuxi ……48 It's a big tech guy , Create our programming life together 、 Our technological age .《 New programmers 004》 Fully listed , Welcome to subscribe to !

边栏推荐
- Automatic generation of interface automatic test cases by actual operation
- Configuration of DNS server of Huawei ENSP simulator
- Actual combat simulation │ JWT login authentication
- Advantages of RFID warehouse management system solution
- Automatic insertion of captions in word
- Idea configuration standard notes
- LeetCode 8. String conversion integer (ATOI)
- Gobang go to work fishing tools can be LAN / man-machine
- 分析伦敦银走势图的技巧
- RFID仓储管理系统解决方案的优点
猜你喜欢
y56.第三章 Kubernetes从入门到精通 -- 业务镜像版本升级及回滚(二九)
The video sound of station B is very low - solution
接口設計時的一些建議
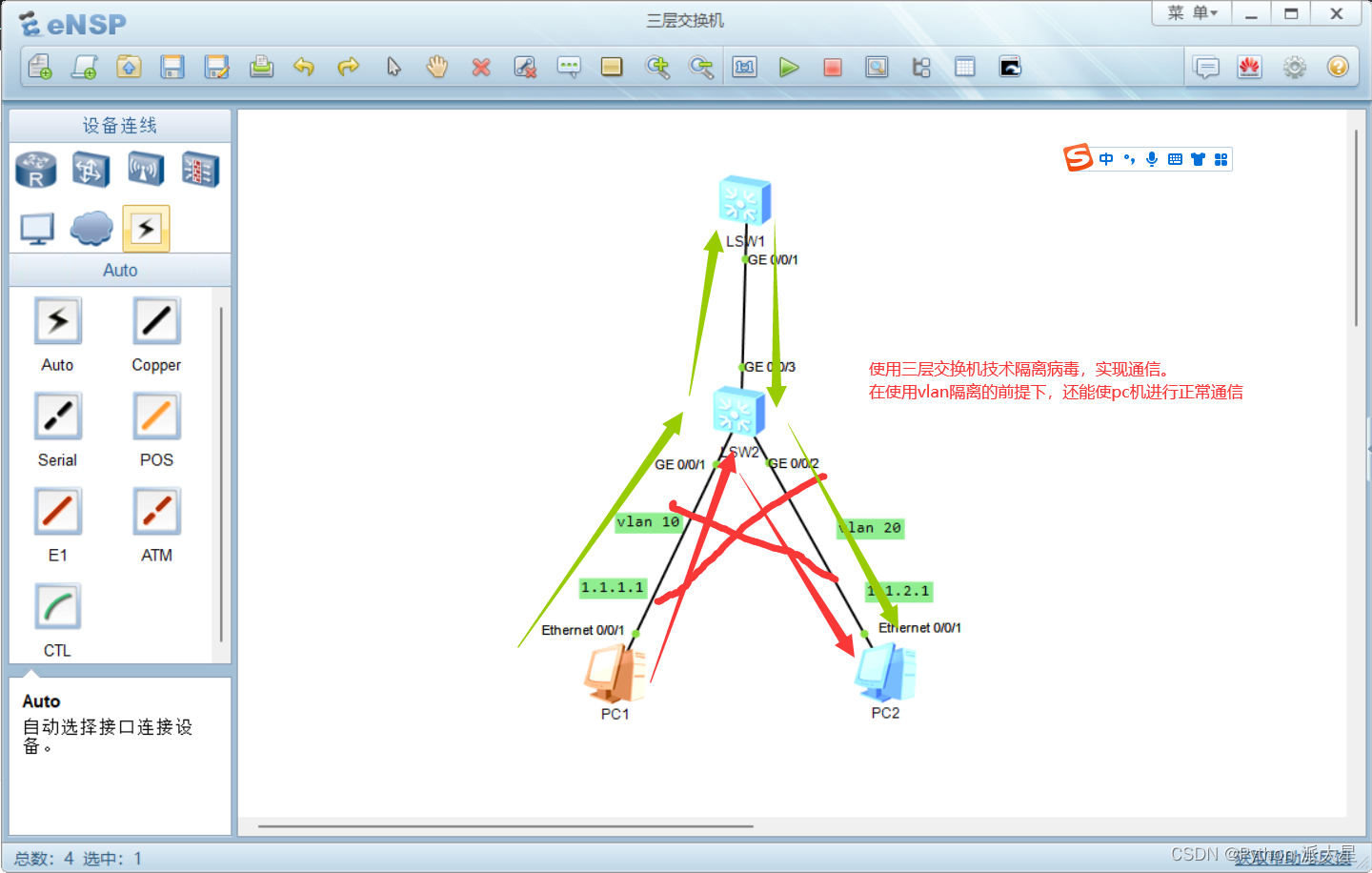
Huawei ENSP simulator layer 3 switch
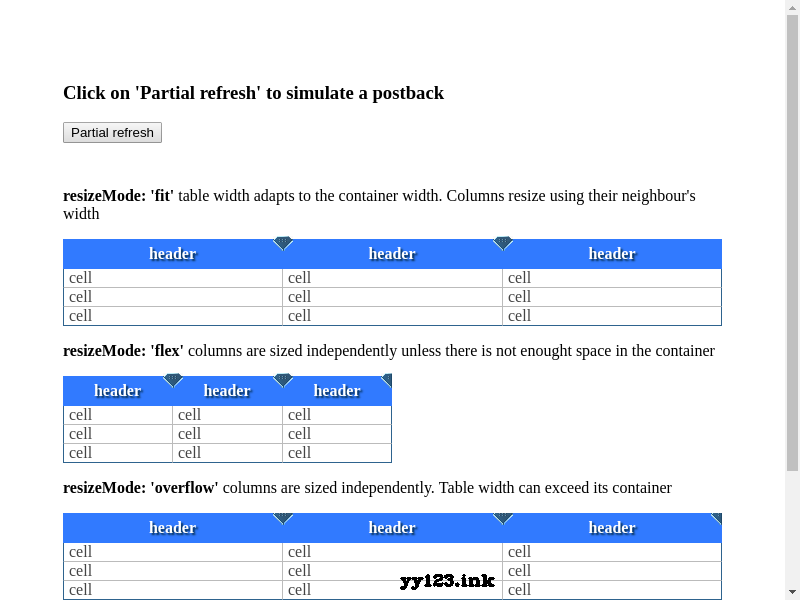
colResizable.js自动调整表格宽度插件
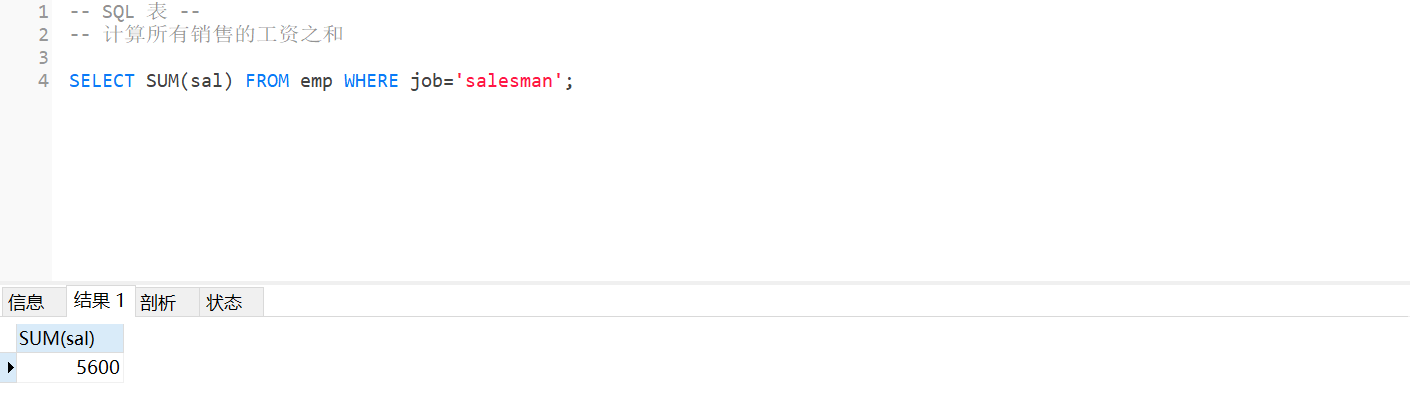
MySQL - database query - use of aggregate function, aggregate query, grouping query

多模輸入事件分發機制詳解

Y56. Chapter III kubernetes from entry to proficiency -- business image version upgrade and rollback (29)

伦敦银走势图分析的新方法

多模输入事件分发机制详解
随机推荐
[micro service SCG] use of predict
基于OpenCV haarcascades的对象检测
华为模拟器ensp常用命令
Four traversal methods of binary tree, as well as the creation of binary tree from middle order to post order, pre order to middle order, pre order to post order, and sequence [specially created for t
测试员的算法面试题-找众数
hash 表的概念及应用
仿ps样式js网页涂鸦板插件
记一次重复造轮子(Obsidian 插件设置说明汉化)
__init__() missing 2 required positional arguments 不易查明的继承错误
为什么说不变模式可以提高性能
【Try to Hack】宽字节注入
Introduction to pressure measurement of JMeter
哈希表、哈希函数、布隆过滤器、一致性哈希
杰理之AD 系列 MIDI 功能说明【篇】
GVM use
What are the functional modules of RFID warehouse management system solution
Huawei ENSP simulator realizes communication security (switch)
LeetCode 7. 整数反转
Automatic insertion of captions in word
Go language notes (2) some simple applications of go