当前位置:网站首页>Actual combat simulation │ JWT login authentication
Actual combat simulation │ JWT login authentication
2022-07-04 21:03:00 【Hua Weiyun】
Token The certification process
- As the most popular cross domain authentication solution ,
JWT(JSON Web Token)Loved by developers , The main process is as follows : - The client sends an account and password to request login
- The server receives the request , Verify whether the account and password pass
- After successful verification , The server will generate a unique
token, And return it to the client - Client received
token, Store it incookieperhapslocalStrogein - After that, every time the client sends a request to the server , Will pass
cookieperhapsheaderTake with youtoken - Server side validation
tokenThe effectiveness of the , The data of the response is returned only after passing

Token Certification benefits
- Support cross domain access :
CookieCross domain access is not allowed , That's rightTokenThere is no mechanism , The premise is that the transmitted user authentication information passesHTTPHead transmission - No state :
TokenThe mechanism does not need storage on the serversessionInformation , becauseTokenIt contains the information of all users who log in , Just on the client sidecookieOr local media storage status information - More applicable : As long as it's support
httpProtocol client , You can usetokenauthentication . - Don't need to consider CSRF: Because no longer rely on
cookie, So usingtokenThe authentication method will not happenCSRF, So there is no need to considerCSRFDefense
JWT structure
- One
JWTIt's actually a string , It consists of three parts :Head、loadAndSignature. Middle point.Divided into three parts . Be carefulJWTThere is no line break inside .

- Head / header
headerIt's made up of two parts :tokenThe type ofJWTAnd algorithm name :HMAC、SHA256、RSA
{ "alg": "HS256", "typ": "JWT"}- load / Payload
PayloadPart of it is also aJSONobject , It is used to store the data that needs to be transferred .JWTSpecify seven default fields to choose from .- In addition to the default fields , You can add any field you want , Generally, after the user logs in successfully , Store user information here
iss: The issuer exp: Due time sub: The theme aud: user nbf: Not available until iat: Release time jti:JWT ID Used to identify the JWT{ "iss": "xxxxxxx", "sub": "xxxxxxx", "aud": "xxxxxxx", "user": [ 'username': ' Geek flying rabbit ', 'gender': 1, 'nickname': ' Flying rabbit ' ] }- Signature / Signature
- The signature part is on the above Head 、 load Data signature with two parts of data
- To ensure that the data is not tampered with , You need to specify a key , And this key is usually only known by you , And stored on the server
- The code to generate the signature is generally as follows :
// among secret It's the key String signature = HMACSHA256(base64UrlEncode(header) + "." + base64UrlEncode(payload), secret)JWT Basic use
- The client receives the
JWT, Can be stored inCookieInside , It can also be stored inlocalStorage - then Every time the client communicates with the server , Take this with you
JWT - hold
JWTSave inCookieSend request inside , It can't beCross domain - It's better to put it in
HTTPRequested header informationAuthorizationIn the field
fetch('license/login', { headers: { 'Authorization': 'X-TOKEN' + token }})actual combat : Use JWT Login authentication
Use here
ThinkPHP6IntegrateJWTLogin and authenticate for actual combat simulationinstall JWT Expand
composer require firebase/php-jwt- Package generation JWT And decryption methods
<?php/** * Desc: JWT authentication * Author: autofelix * Time: 2022/07/04 */namespace app\services;use app\Helper;use Firebase\JWT\JWT;use Firebase\JWT\Key;class JwtService{ protected $salt; public function __construct() { // Get a unique string from the configuration information , You can write whatever you like md5('token') $this->salt = config('jwt.salt') || "autofelix"; } // jwt Generate public function generateToken($user) { $data = array( "iss" => 'autofelix', // Issuer Can be null "aud" => 'autofelix', // Face users , Can be null "iat" => Helper::getTimestamp(), // The issuance of time "nbf" => Helper::getTimestamp(), // Take effect immediately "exp" => Helper::getTimestamp() + 7200, //token Expiration time Two hours "user" => [ // Record user information 'id' => $user->id, 'username' => $user->username, 'truename' => $user->truename, 'phone' => $user->phone, 'email' => $user->email, 'role_id' => $user->role_id ] ); $jwt = JWT::encode($data, md5($this->salt), 'HS256'); return $jwt; } // jwt Decrypt public function chekToken($token) { JWT::$leeway = 60; // Subtract... From the current time 60, Leave some room for time $decoded = JWT::decode($token, new Key(md5($this->salt), 'HS256')); return $decoded; }}- After the user logs in , Generate JWT identification
<?phpdeclare (strict_types=1);namespace app\controller;use think\Request;use app\ResponseCode;use app\Helper;use app\model\User as UserModel;use app\services\JwtService;class License{ public function login(Request $request) { $data = $request->only(['username', 'password', 'code']); // .... Relevant logic for verification ... $user = UserModel::where('username', $data['username'])->find(); // Verify by generating JWT, Return to front end save $token = (new JwtService())->generateToken($user); return json([ 'code' => ResponseCode::SUCCESS, 'message' => ' Login successful ', 'data' => [ 'token' => $token ] ]); }}- Middleware verifies whether the user logs in
- stay
middleware.phpRegister middleware
<?php// Global middleware definition file return [ // ... Other middleware // JWT verification \app\middleware\Auth::class];- After registering middleware , Improve the verification logic in the permission verification middleware
<?phpdeclare (strict_types=1);namespace app\middleware;use app\ResponseCode;use app\services\JwtService;class Auth{ private $router_white_list = ['login']; public function handle($request, \Closure $next) { if (!in_array($request->pathinfo(), $this->router_white_list)) { $token = $request->header('token'); try { // jwt verification $jwt = (new JwtService())->chekToken($token); } catch (\Throwable $e) { return json([ 'code' => ResponseCode::ERROR, 'msg' => 'Token Validation failed ' ]); } $request->user = $jwt->user; } return $next($request); }}边栏推荐
- E-week finance | Q1 the number of active people in the insurance industry was 86.8867 million, and the licenses of 19 Payment institutions were cancelled
- 伦敦银走势图分析的新方法
- What if the computer page cannot be full screen? The solution of win11 page cannot be full screen
- Go notes (3) usage of go language FMT package
- What should I do if my computer sharing printer refuses access
- 【1200. 最小絕對差】
- idea恢复默认快捷键
- Record the online bug solving list (unfinished to be continued 7/4)
- 仿ps样式js网页涂鸦板插件
- Flet tutorial 04 basic introduction to filledtonalbutton (tutorial includes source code)
猜你喜欢
剑指 Offer II 80-100(持续更新)
What if the win11 shared file cannot be opened? The solution of win11 shared file cannot be opened
LeetCode+ 81 - 85 单调栈专题
Flet教程之 04 FilledTonalButton基础入门(教程含源码)
heatmap.js图片热点热力图插件
How does the computer save web pages to the desktop for use
JS卡牌样式倒计时天数
面对同样复杂的测试任务为什么大老很快能梳理解决方案,阿里十年测试工程师道出其中的技巧
From automation to digital twins, what can Tupo do?
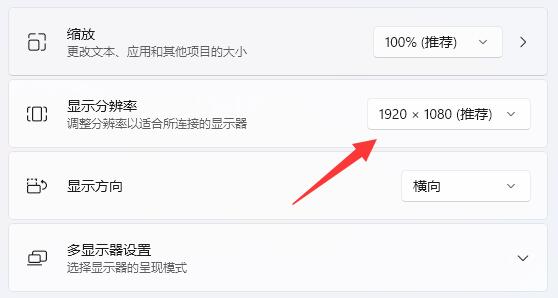
电脑页面不能全屏怎么办?Win11页面不能全屏的解决方法
随机推荐
企业数字化转型最佳实践案例:基于云的数字化平台系统安全措施简介与参考
Flet教程之 04 FilledTonalButton基础入门(教程含源码)
TweenMax表情按钮js特效
In the face of the same complex test task, why can the elder sort out the solution quickly? Ali's ten-year test engineers showed their skills
Summary of the mistakes in the use of qpainter in QT gobang man-machine game
《动手学深度学习》(三) -- 卷积神经网络 CNN
仿ps样式js网页涂鸦板插件
测试用例 (TC)
LeetCode+ 81 - 85 单调栈专题
网件r7000梅林系统5g不稳定 5g信号经常掉线解决方法
Idea plug-in
LeetCode 8. String conversion integer (ATOI)
go defer的使用说明
Record the online bug solving list (unfinished to be continued 7/4)
Idea case shortcut
Managed service network: application architecture evolution in the cloud native Era
HMS Core 机器学习服务
[1200. Minimum absolute difference]
Stack: how to realize the judgment of valid brackets?
卷积神经网络在深度学习中新发展的5篇论文推荐