当前位置:网站首页>bellman-ford AcWing 853. 有边数限制的最短路
bellman-ford AcWing 853. 有边数限制的最短路
2022-07-02 09:43:00 【T_Y_F666】
bellman-ford AcWing 853. 有边数限制的最短路
原题链接
算法标签
最短路 Bellman-Ford
思路
由题意 存在负边, 因此不能采用Dijkstra
由于具有边数限制
故采用Bellman-Ford
Bellman-Ford算法
对于存在负权回路的路径
可能不存在最短路
例如下图
1至5最短路 不存在 由于每次在2, 3, 4回路中循环一次, 路几个长度减1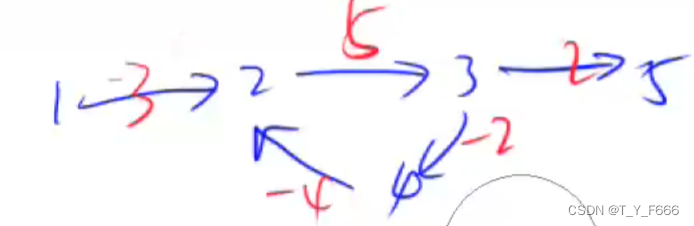
代码
#include<bits/stdc++.h>
#define int long long
#define rep(i, a, b) for(int i=a;i<b;++i)
#define Rep(i, a, b) for(int i=a;i>b;--i)
using namespace std;
const int N = 10005;
// p存储节点祖宗节点 d存储当前节点据祖宗节点的距离
int lst[N], dis[N];
int n,m,k;
inline int read(){
int s=0,w=1;
char ch=getchar();
while(ch<'0'||ch>'9'){if(ch=='-')w=-1;ch=getchar();}
while(ch>='0'&&ch<='9') s=s*10+ch-'0',ch=getchar();
return s*w;
}
void put(int x) {
if(x<0) putchar('-'),x=-x;
if(x>=10) put(x/10);
putchar(x%10^48);
}
struct Edge{
int a, b, c;
}edge[N];
int be(){
memset(dis, 0x3f3f, sizeof dis);
dis[1]=0;
rep(i, 0, k){
memcpy(lst, dis, sizeof dis);
rep(j, 0, m){
Edge e=edge[j];
dis[e.b]=min(dis[e.b], lst[e.a]+e.c);
}
}
if(dis[n]>0x3f3f3f3f/2){
return -1;
}else{
return dis[n];
}
}
signed main(){
ios::sync_with_stdio(false);
cin.tie(0);
cout.tie(0);
n=read(), m=read(), k=read();
rep(i, 0, m){
int x=read(), y=read(), z=read();
edge[i]={x, y, z};
}
if(be()==-1){
puts("impossible");
}else{
printf("%lld", dis[n]);
}
return 0;
}
原创不易
转载请标明出处
如果对你有所帮助 别忘啦点赞支持哈
边栏推荐
- Full link voltage measurement
- AAAI 2022 | Peking University & Ali Dharma Institute: pruning and compression of pre training language model based on comparative learning
- H5 to app
- Anxiety of a 211 programmer: working for 3 years with a monthly salary of less than 30000, worried about being replaced by fresh students
- mysql数据库基础
- Drools executes the specified rule
- drools动态增加、修改、删除规则
- 寻找二叉树中任意两个数的公共祖先
- BOM DOM
- Shutter encapsulated button
猜你喜欢
Deep understanding of P-R curve, ROC and AUC

记录一下MySql update会锁定哪些范围的数据
kubenetes中port、targetPort、nodePort、containerPort的区别与联系
Multiply LCA (nearest common ancestor)
![[ybtoj advanced training guide] similar string [string] [simulation]](/img/eb/acfefc7f85018fe9365d13502e2b0a.jpg)
[ybtoj advanced training guide] similar string [string] [simulation]

高性能纠删码编码

Lekao.com: experience sharing of junior economists and previous candidates in customs clearance

Experiment of connecting mobile phone hotspot based on Arduino and esp8266 (successful)
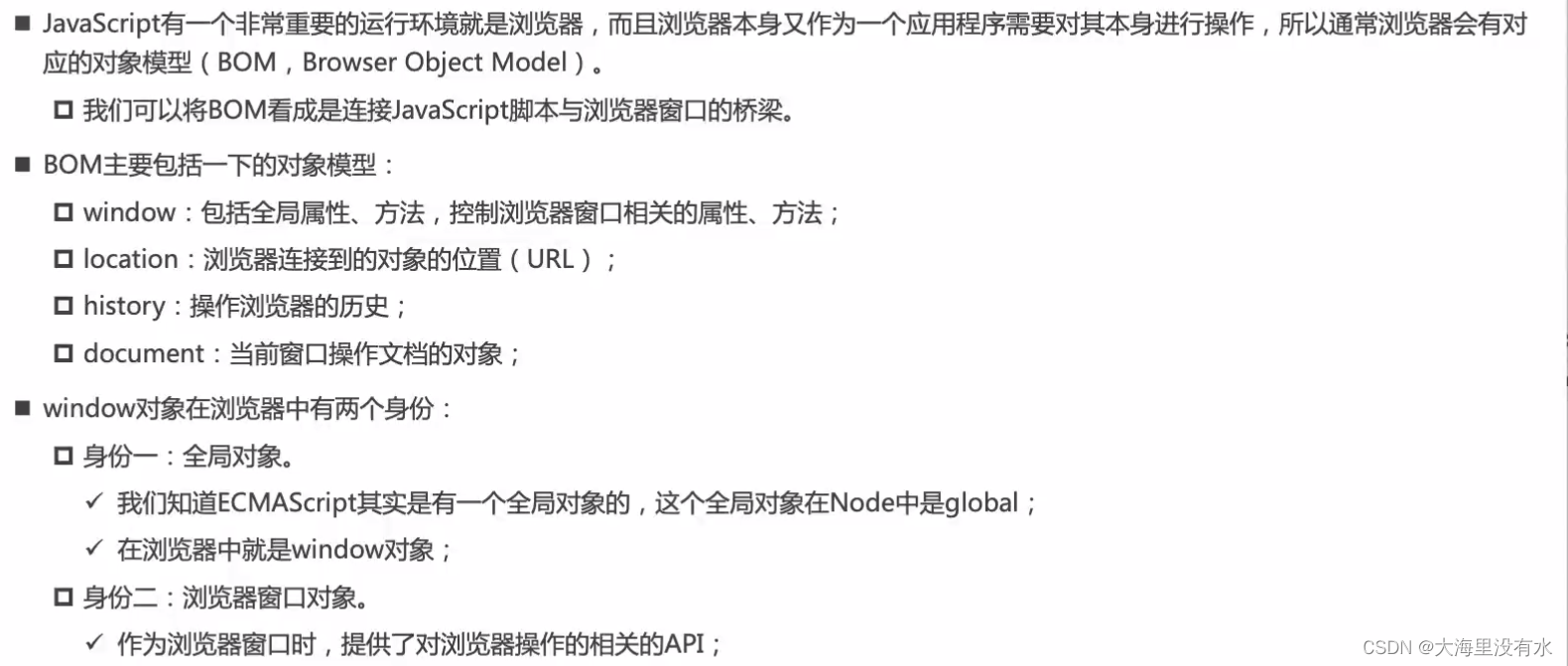
BOM DOM
Programmers can't find jobs after the age of 35? After reading this article, you may be able to find the answer
随机推荐
In development, why do you find someone who is paid more than you but doesn't write any code?
Leetcode739 daily temperature
Docker-compose配置Mysql,Redis,MongoDB
Intel 内部指令 --- AVX和AVX2学习笔记
JSON序列化 与 解析
AAAI 2022 | Peking University & Ali Dharma Institute: pruning and compression of pre training language model based on comparative learning
js 迭代器 生成器 异步代码处理 promise+生成器 -> await/async
Shuttle encapsulated AppBar
PR 2021 quick start tutorial, learn about the and functions of the timeline panel
MySQL indexes and transactions
The blink code based on Arduino and esp8266 runs successfully (including error analysis)
Drools executes the specified rule
There is a hidden danger in CDH: the exchange memory used by the process of this role is XX megabytes. Warning threshold: 200 bytes
post请求体内容无法重复获取
CDA data analysis -- Introduction and use of aarrr growth model
LeetCode—剑指 Offer 51. 数组中的逆序对
1380. Lucky numbers in the matrix [two-dimensional array, matrix]
Find the factorial of a positive integer within 16, that is, the class of n (0= < n < =16). Enter 1111 to exit.
Less than three months after the programmer was hired, the boss wanted to launch the app within one month. If he was dissatisfied, he was dismissed immediately
深拷貝 事件總線