当前位置:网站首页>2.7 binary tree, post order traversal - [FBI tree]
2.7 binary tree, post order traversal - [FBI tree]
2022-07-02 12:33:00 【I boiled the night white_】
List of articles
Title Description

Input description
The first line is an integer N(0<=N<=10)
The second line is a length of 2N Of “01” strand .
Output description
Output a string , namely FBI The subsequent traversal sequence of the tree .
I/o sample
Input :
3
10001011
Output :
IBFBBBFIBFIIIFF
The final code
1. c/c++
#include <bits/stdc++.h>
using namespace std;
char s[2000],tree[280000]; //tree[] Full binary tree
// First, the leaf node has a value , Then determine the value of the parent node according to the value of the leaf node
void build_FBI(int k,int left,int right)
{
// Reach the leaf node
if(left==right)
{
if(s[right]=='1') tree[k]='I';
else tree[k]='B';
return;
}
int mid=(left+right)/2; // Split in two
build_FBI(2*k,left,mid); // Recursive left half
build_FBI(2*k+1,mid+1,right); // Recursive right half
if(tree[2*k]=='B' && tree[2*k+1]=='B') // Both left and right sons B
tree[k]='B';
else if(tree[2*k]=='I'&&tree[2*k+1]=='I') // Both left and right sons I
tree[k]='I';
else tree[k]='F';
}
void postorder (int v){
// After the sequence traversal
if(tree[2*v])
postorder (2*v);
if(tree[2*v+1])
postorder (2*v+1);
printf("%c",tree[v]);
}
int main(){
int n;
scanf("%d",&n);
scanf("%s",s+1);
build_FBI(1,1,strlen(s+1));
// Post order traversal output
postorder(1);
}
2. java
3. python
Process understanding

边栏推荐
- "As a junior college student, I found out how difficult it is to counter attack after graduation."
- Simple understanding of ThreadLocal
- How to write a pleasing English mathematical paper
- Error in kubeadm join: [error port-10250]: port 10250 is in use [error fileavailable--etc kubernetes PKI
- There is a hidden danger in CDH: the exchange memory used by the process of this role is XX megabytes. Warning threshold: 200 bytes
- 甜心教主:王心凌
- mysql索引和事务
- Map and set
- CDA data analysis -- common knowledge points induction of Excel data processing
- CDH6之Sqoop添加数据库驱动
猜你喜欢
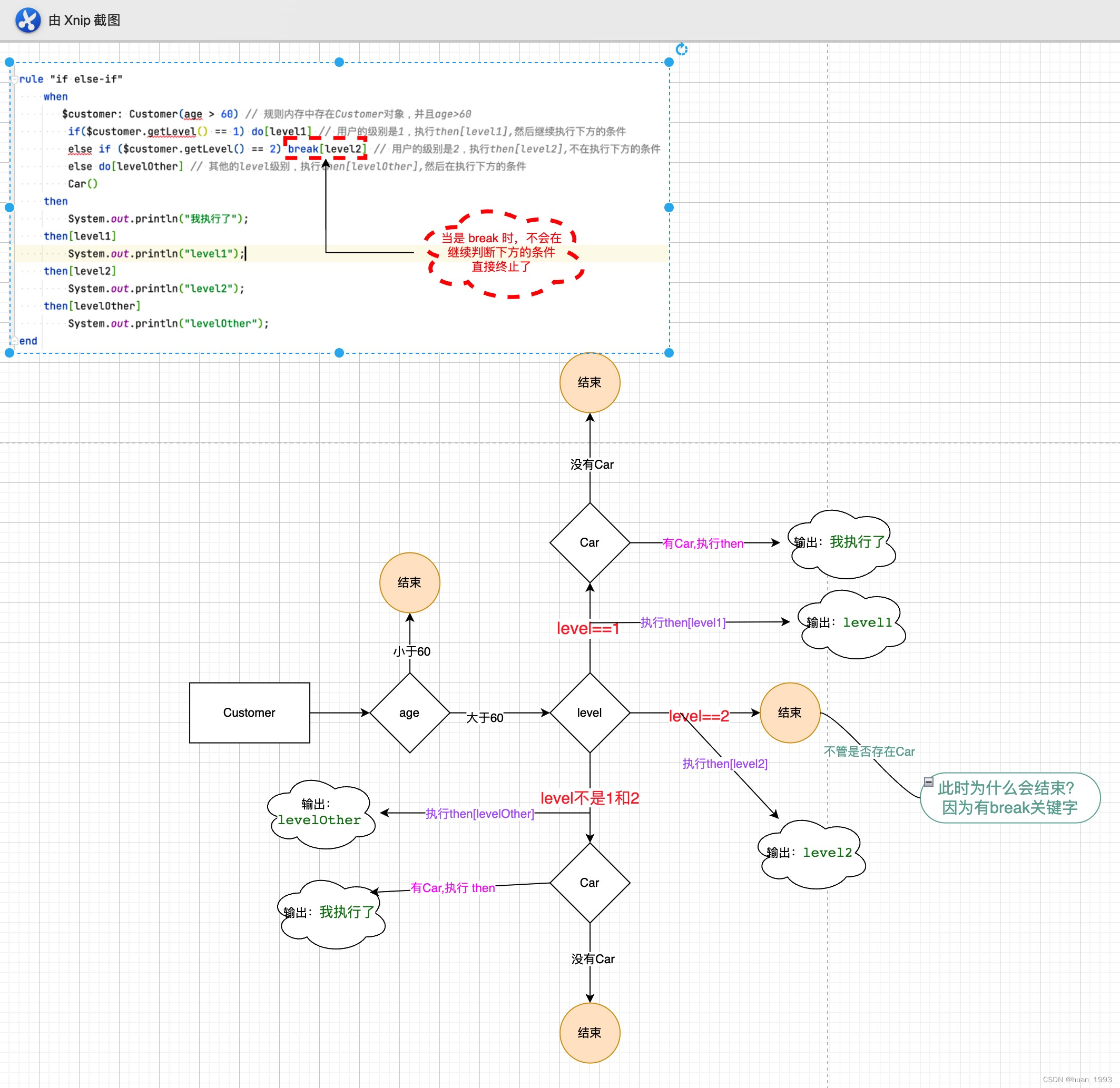
drools中then部分的写法

排序---

Experiment of connecting mobile phone hotspot based on Arduino and esp8266 (successful)
深拷贝 事件总线
Docker compose configuration mysql, redis, mongodb
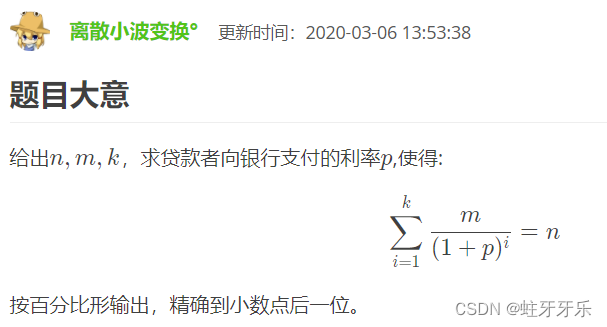
Discrimination of the interval of dichotomy question brushing record (Luogu question sheet)

Fresh, 2022 advanced Android interview must know 100 questions (interview questions + answer analysis)
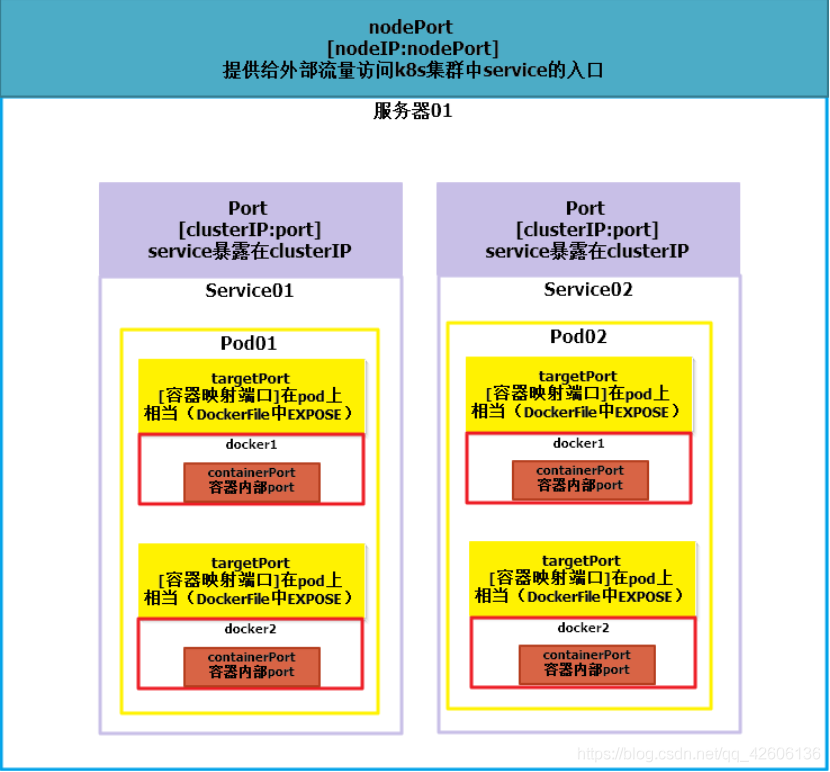
The differences and relationships among port, targetport, nodeport and containerport in kubenetes

刷题---二叉树--2
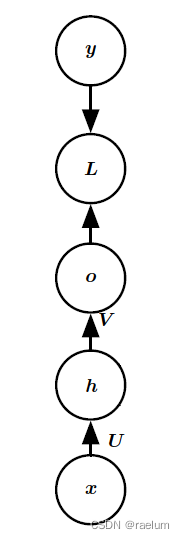
Natural language processing series (I) -- RNN Foundation
随机推荐
This "little routine" is set on the dough cake of instant noodles. No wonder programmers are always hungry
Post request body content cannot be retrieved repeatedly
JZ63 股票的最大利润
String palindrome hash template question o (1) judge whether the string is palindrome
Docker-compose配置Mysql,Redis,MongoDB
drools执行指定的规则
Go learning notes - go based interprocess communication
Thesis translation: 2022_ PACDNN: A phase-aware composite deep neural network for speech enhancement
Programmers can't find jobs after the age of 35? After reading this article, you may be able to find the answer
Anti shake throttle
mysql表的增删改查(进阶)
Leetcode - Sword finger offer 51 Reverse pairs in an array
What is the relationship between NFT and metauniverse? How to view the market? The future market trend of NFT
Anxiety of a 211 programmer: working for 3 years with a monthly salary of less than 30000, worried about being replaced by fresh students
Use sqoop to export ads layer data to MySQL
Fastdateformat why thread safe
Leetcode122 买卖股票的最佳时机 II
The second composition template of postgraduate entrance examination English / chart composition, English chart composition is enough
Sse/avx instruction set and API of SIMD
5g era, learning audio and video development, a super hot audio and video advanced development and learning classic