当前位置:网站首页>Collection of blockchain theory [31]
Collection of blockchain theory [31]
2020-11-10 08:26:00 【Blockchain tutorial】
Blockchain as a brand new 、 Disruptive technology , It is an active research field at home and abroad . This article lists the latest group of blockchain papers , I hope it can help the students who choose the graduation project of blockchain , This is a Huizhi. Com Edit and organize the number of graduation thesis series of blockchain 31 piece .
Blockchain development tutorial : The etheric fang | The currency | EOS | Tendermint | Hyperledger Fabric | Omni/USDT | Ripple | Tron
This paper collates the latest reference papers that can be used for graduation design of blockchain , If you need to visit the latest articles in the blockchain graduation project required Thesis Series , Can keep an eye on our Blog , Or join QQ Group :532241998.
1、 Storage and prediction framework of battery life of Internet of things devices based on deep learning network and blockchain
With the deepening of digital process , There is a growing need to automate entities .IoT The data generated by Internet of things devices needs to be processed accurately in a safe way . The success of this scenario requires the blockchain as an immutable data store to improve the overall security and trust , This helps to reduce the pressure on the adaptability of the entire automation system .
![[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-3j7Bh5hs-1604956105175)(block-paper-31/iot-battery-life.png)]](/img/53/f34998bfaa33c327b1d7fbc1fce27a.jpg)
This study focuses on a specific use case —— Real time deployment on Chicago park area beach IoT The Internet . Real time data collected by various sensors is used in a deep learning network IoT Sensor battery life prediction model . The model proposed in this paper can help the government to plan for battery replacement in advance , So as to provide uninterrupted service . Because of the sensitivity and security requirements of these data , The predicted battery life value is stored on the blockchain to form an unforgeable record .
The paper PDF download :A Framework for Prediction and Storage of Battery Life in IoT Devices using DNN and Blockchain
2、ACeD: Scalable data validity Oracle
A popular solution for offline computing and on chain storage is to submit the hash of the data off the chain to the chain . This mechanism has been identified as a potential stall attack : The block corresponding to the commit hash may become invalid on any honest node . A straightforward solution is to broadcast all blocks across the network , In order to avoid this data validity attack , But the solution doesn't scale well .
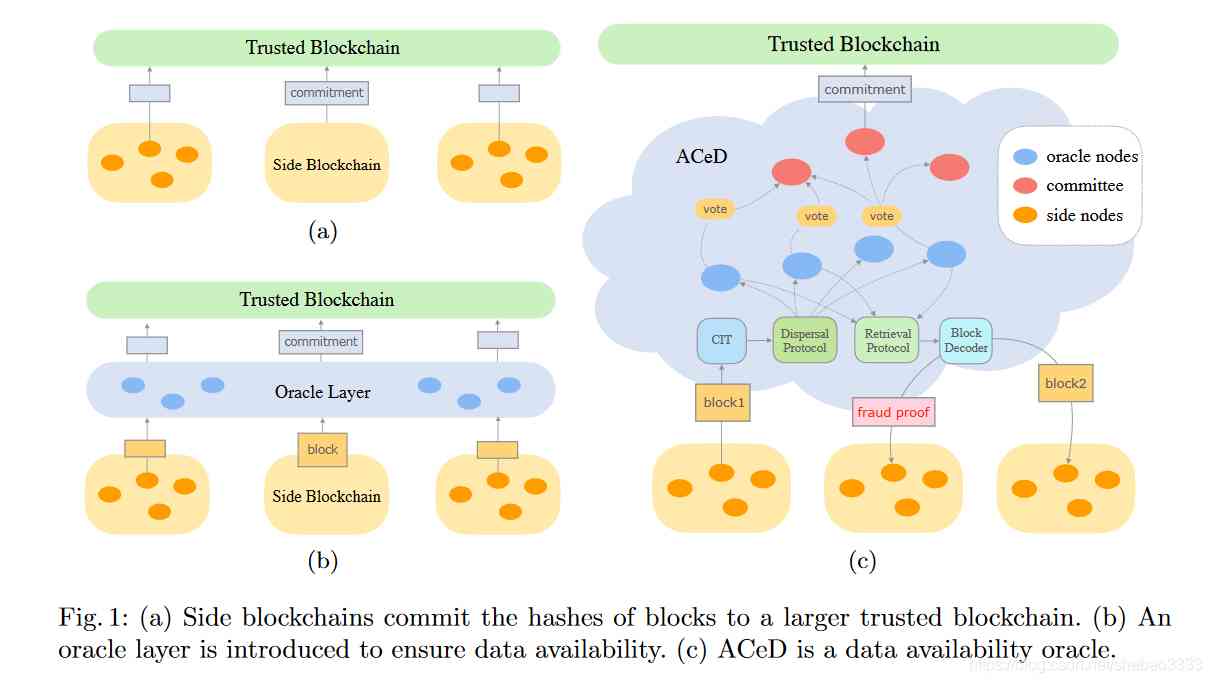
In this paper , We propose a scalable solution to this data validity problem , ACeD, The communication complexity is O(1), As far as we know, this is the first solution to this problem . The key innovation is the new agreement that we're proposing , It only needs N Each node receives O(1/N) Block of , So the data gets a distributed availability guarantee .
Our plan will coding-theoretic The design is embedded in the Merkel tree submission , So as to ensure the efficiency and the reconstruction of imitation tampering . This scheme is different from asynchronous verifiable information step by step and encoding Merkel tree . In Ethereum Kovan The implementation on the test network shows excellent performance , It can reach... Per second 10000 Transaction throughput , also gas Reduced costs 6000 times .
The paper PDF download :ACeD: Scalable Data Availability Oracle
3、 be based on Hyperledger Fabric Analysis of information lifetime in real-time monitoring network of blockchain
Information longevity (AoI) It is a recently proposed index for quantifying the freshness of data in real-time condition monitoring system . In this paper , We make use of AoI The index explores based on Hyperledger Fabric Blockchain monitoring network (HeMN) Data freshness of . stay HeMN In the network , Status updates from the data source are sent via an uplink link and recorded in HyperledgerFabric Blockchain network . Asked to ensure the freshness of the data , We calculate based on transmission delay and formula delay AoI The probability of indicator failure , utilize Fabric The analysis results are verified by the network , And the probability of successful transmission is investigated AoI Failure probability affects efficiency .
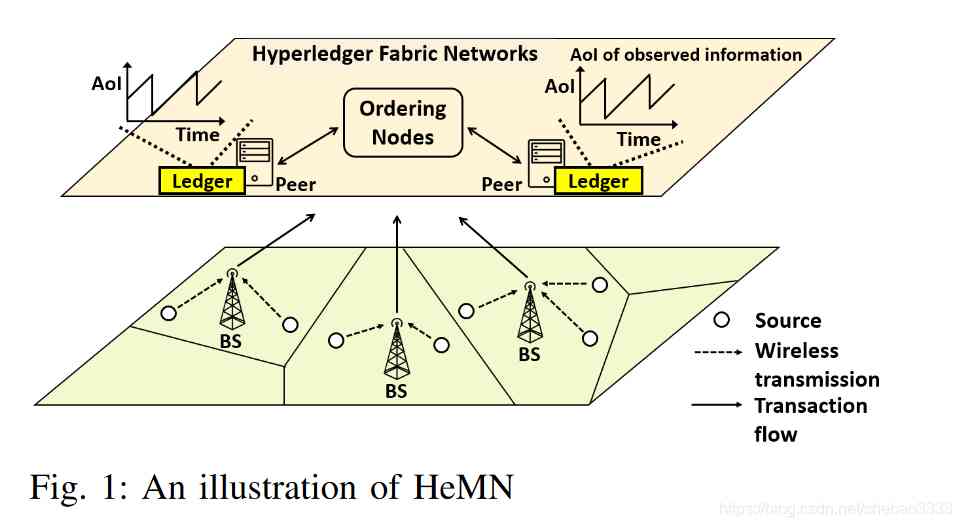
The paper PDF download :Age of Information Analysis in Hyperledger Fabric Blockchain-enabled Monitoring Networks
4、 Ethereum contract smart corpus
Many real-world software engineering studies indicate the availability of source code 、 The need for filtering and sorting warehouses is obvious . In the last few years , Ethereum blockchain Browser service has become used to explore 、 Search for Ethereum blockchain transactions 、 Address 、 Tokens, 、 Smart contract source code 、 A popular item of price and other activity data on the chain . Obtain useful information for software engineering research from the above services , For example, smart contract software metrics , There may be a lot of subtasks to complete , For example, search for specific transactions 、 analysis HTML Format and filter the duplicate code of smart contract .
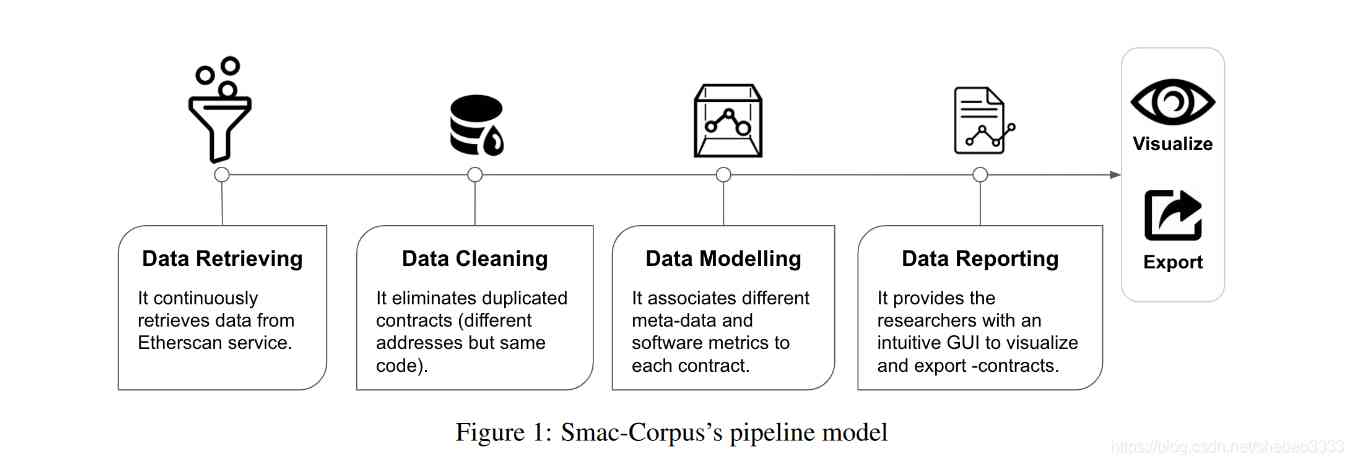
In this paper , We propose the concept of intelligent corpus , The corpus contains the latest smart contracts Solidity Source code and metadata about contracts . This paper presents the design and initial implementation of the intelligent corpus ,
The paper PDF download :Smart-Corpus: an Organized Repository of Ethereum Smart Contracts Source Code and Metrics
5、 Blockchain and decentralized Internet : expectation 、 Trends and challenges
Blockchain has had an impact on current technology , It revolutionized the financial industry through the use of digital cryptocurrencies and decentralized features . With the current pursuit of decentralized Internet , From the infrastructure and protocol layer to the service and application layer, many methods have been proposed to achieve this goal .

This paper focuses on the use of blockchain to provide reliable and secure decentralized computing system , This paper reviews the methods based on blockchain . To achieve decentralization , This paper makes an in-depth study from two aspects . One is consensus algorithm , We think PoP、Paxos and PoAH Enough Internet architecture to enable blockchain . The second aspect is the impact of future Internet technology on blockchain , The combination of the two will help to improve the existing defects and further optimize the decentralization of the Internet .
The paper PDF download :Blockchain for Decentralization of Internet: Prospects, Trends, and Challenges
Link to Huizhi blockchain collection :
One | Two | 3、 ... and | Four | 5、 ... and | 6、 ... and | 7、 ... and | 8、 ... and | Nine | Ten | 11、 ... and | Twelve | 13、 ... and | fourteen | 15、 ... and | sixteen | seventeen | eighteen | nineteen | twenty | The 21st | Twenty-two | 23 | Twenty-four | twenty-five | hexacosa- | twenty-seven | Twenty-eight | Twenty-nine | thirty
Link to the original text : Blockchain graduation project must read thesis 31 — Huizhi. Com
版权声明
本文为[Blockchain tutorial]所创,转载请带上原文链接,感谢
边栏推荐
- Three ways to solve coursera video unable to watch
- JMeter interface test -- a solution with token
- [leetcode] 93 balanced binary tree
- Overview of the most complete anomaly detection algorithm in history
- pytorch训练GAN时的detach()
- csdn bug6:待加
- CUDA_获取指定设备
- 坚持追查7年,近10亿美元比特币终被美国政府没收充公
- 大专学历的我工作六年了,还有机会进大厂吗?
- Yixian e-commerce prospectus of perfect diary parent company: focusing on marketing and ignoring R & D, with a loss of 1.1 billion in the first three quarters
猜你喜欢

对于程序员,那些既陌生又熟悉的计算机硬件

Overview of the most complete anomaly detection algorithm in history

Error running app: default activity not found solution

史上最全异常检测算法概述
工厂方法模式

【LeetCode】 93 平衡二叉树

假如需要一百万个对象

CSDN bug3: to be added
利用尾巴作为时间序列进行处理来识别鲸鱼
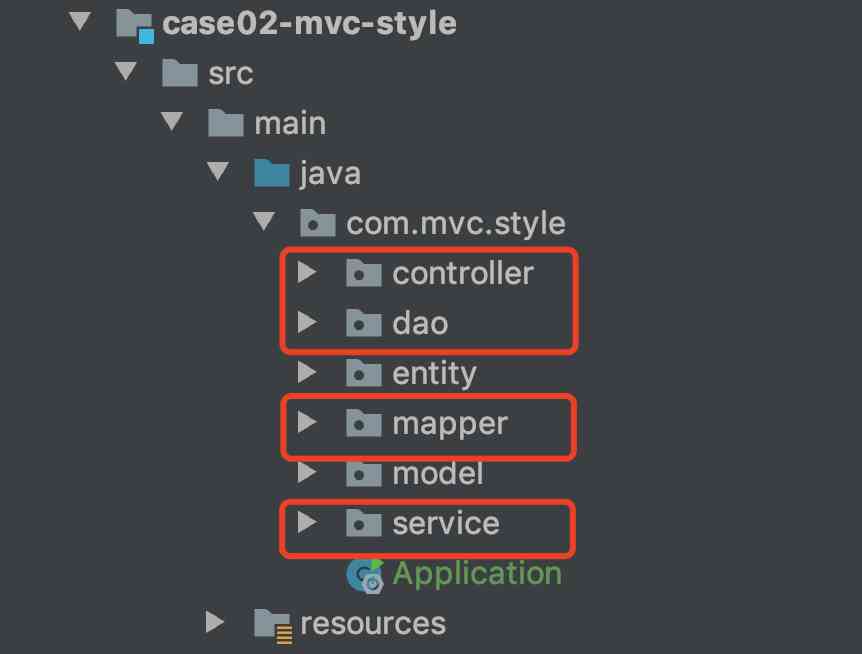
Coding style: SSM environment in MVC mode, code hierarchical management
随机推荐
CUDA_主机内存
CSDN bug10: to be added
树莓派鼓捣记 - 设置 wifi
将Map中对应的key和value赋值到对象中
史上最全异常检测算法概述
[论文阅读笔记] RoSANE, Robust and scalable attributed network embedding for sparse networks
《Python Cookbook 3rd》笔记(2.2):字符串开头或结尾匹配
js label语法跳出多重循环
编码风格:Mvc模式下SSM环境,代码分层管理
day85:luffy:购物车根据有效期不同切换价格&购物车删除操作&价格结算&订单页面前戏
csdn bug6:待加
The length of the last word in leetcode
JS solves the problem of automatic pagination in browser printing
港股上市公司移卡收购创信众42.5%股权 谋划加快营销服务布局
The solution of polar experience insensitive verification
proxy 的不完整polyfill
Centos7 operating system security hardening series (2)
Fire knowledge online answer activity small program
[leetcode] 92 integer inversion
Oschina: my green plants are potatoes, ginger and garlic