当前位置:网站首页>Song list 11111
Song list 11111
2022-07-07 21:40:00 【Boumbo】
On the east side of Beijing
1. Whether non static variables of a class can be referenced in the static method of a class
2. When the class is loaded
3. What have you used or learned I/O Class of flow
3. There are several ways to create threads
4. Understanding of thread pool and corresponding parameters , What are the rejection strategies
5.mysql Know which storage engines
6.innodb and ISAM The difference between
7. Since the primary key ID And manually generate primary keys ID Which is faster , Why?
8. Index failure scenario
9.RestController and Controller The difference between
10.Springboot When modifying the configuration file , How to write a list data in the configuration file
11. The difference between interceptors and filters
12. The way Redis What are the usage scenarios
Byte video infrastructure side
1. Take a new object as Key Pass in a Hashmap in , Then modify the internal value of this object , And from this hashmap Take this object as Key Conduct Get What will be the result of the operation
2.hashmap and hashtable The difference between
3. In what units does the operating system allocate memory
4. How to understand virtual memory
5.TCP be relative to UDP In addition to the need to establish connections and more time-consuming, what are the disadvantages
6. Algorithm problem : Enter an integer array and a positive integer k, Ask if every value in an integer array represents an edge , The size of the value is the length of the edge , Can this array surround a positive k Edge shape
Alibaba cloud side
1. use Redis What functions have you done
2.Redis What are the data structures
3.mysql What is the whole query process of a query statement in ( First establish the connection through the connector , The query cache , Syntax analysis , Analyze which index scans fewer rows and select which index , Go to query )
4.Redis Jump watch in
5.Redis How to realize distributed lock
6.redis Why so fast
7.Redis What are the memory replacement strategies for
8. say something LRU How to realize
9.JDK Which set class in is this idea (LinkedHashMap)
10.springboot The instantiation process
11. Algorithm problem : Judge whether a linked list has links
Two sides of alicloud
1. Implement a requirement , There are two databases One is empty , The other has various watches , How to copy the data in the library to the empty database
2. How to implement any java Serialization and deserialization of objects
Byte flying Book side
1. Parameters of thread pool and their meanings
2.java What locks are there
3.Synchronize and Reentrylock The difference between
4.CountDownLatch and CyclickBarrier
5. Fair and non-fair locks
6. Which collection classes have been used
7.mysql Four levels of isolation , And the default isolation level
8. What is unreal reading
9. How repeatable reading is achieved
10.undolog redolog What is it?
11. In what units does the database store data
12.http And https The difference between
13.tcp Three handshakes, four waves
14. Why would there be waittime
15.reids What kinds of data structures are there
16.redis Jump watch
17.redis What is the threading model of
18.BIO and NIO, The understanding of multiplexing
19. Algorithm problem Recursive implementation of the list inversion
Byte international e-commerce side
1. What are the differences between abstract classes and interfaces
2.
String A = new String(“test”);
String B = new String(“test”);
1)“test”==“test”;
2)“test”==A;
3)A==B; What is the Boolean value obtained
3. Where is the constant pool
4.String StringBuilder StringBuffer The difference between
5. How to understand thread safety and thread insecurity
6. What are the ways to ensure thread safety
7.java What locks are there
8.Synchronize and Reentrylock The difference between
9. The difference between optimistic lock and pessimistic lock
10. Have you ever used locks in practice
11.CAS Principle
12. Specific scenarios using optimistic locks and pessimistic locks
13.exception and error The difference between
14. What have you seen exception and error
15.OOM What is it? , What's the difference with memory leakage
16.hashmap Principle , The principle of capacity expansion , Why is the array length 2 Of n Power
17. Sync IO And asynchronous ID The understanding of the
18. The difference between blocking and synchronization
19.NIO And multiplexing
20.mysql topic
The table structure is Primary key id full name fraction
1) Find the names of the top ten students with the highest scores ( return 10 A student )
2) Find the student names corresponding to the top ten scores with the highest scores ( May be greater than 10 A student )
21. Algorithm , Given an array A[0,1,…,n-1], Please build an array B[0,1,…,n-1], among B[i] Is the value of an array A In addition to subscript i The product of other elements , namely B[i]=A[0]×A[1]×…×A[i-1]×A[i+1]×…×A[n-1]. Division cannot be used .
Kwai machine learning platform development side
1.mysql Cluster index , Nonclustered index , Overlay index
2.redis Implement a distributed lock
3. How to use mysql Implement a distributed lock
4. How to use redis Implement a blocking lock
5.hashmap The implementation of the
6. understand Currenthashmap Well
7. Read about docker,k8s Well
8. Algorithm problem : Two integer arrays , The index is i The user's entry time and exit time , Seek the largest number of online people in history
Kwai machine learning platform development two sides
1. Understanding of threads and processes
The process is cpu The smallest unit of allocation of resources , It is an independent unit of system resource scheduling , It is also the basic unit of the operating system , All resources are in this process , The process doesn't work , It is used to maintain these resources . The thread is working , Thread is cpu The smallest unit that performs a task , But threads don't have their own resources to run programs , Therefore, threads cannot be separated from processes .
Multi process : Listening to music while chatting is a manifestation of multi process , It seems to be going on at the same time , It's actually cpu High speed switching between programs
A single threaded program has only one execution path
Multithreaded programs have multiple threads ( route ) Do the same thing , Multithreaded programs preempt cpu The opportunity of using the right is greater
The thread switching virtual memory space is still the same , But process switching is different
Process context switching involves switching memory address space
Thread switching refers to switching from one thread to another in the same process
Reference resources
2. How processes communicate , The way threads communicate
Each process has a different user address space , The global variables of any process cannot be seen in another process , So to exchange data between processes, you have to go through the kernel , Create a buffer in the kernel , process A Copy data from user space to kernel buffer , process B Then read the data from the kernel buffer , The mechanism provided by the kernel is called interprocess communication .
Anonymous pipeline communication 、 Advanced pipeline communication 、 Well known pipeline communication 、 Message queuing communication 、 Semaphore communication 、 The signal 、 Shared memory communication 、 Socket communication
Reference resources
Thread communication is when multiple threads operate on shared resources , Inform each other of their status to avoid competition for resources .
Shared memory 、 Messaging and pipeline flow
Reference resources
3. Do you understand
4. The difference between user mode and kernel mode
5. Pagination and segmentation , The difference between page request and segment request
6. Page replacement algorithm
7. How to achieve LRU
8. Read about docker,k8s Well
9. Four features of database transaction
10. Four isolation levels and default isolation levels
11. What are the concurrency consistency problems
12. Algorithm problem 1. The longest valid bracket sequence length
2. Concatenate the substrings of all words
边栏推荐
- uva 12230 – Crossing Rivers(概率)「建议收藏」
- Virtual machine network configuration in VMWare
- GridView defines its own time for typesetting "suggestions collection"
- Ubuntu安装mysql8遇到的问题以及详细安装过程
- NVR硬盘录像机通过国标GB28181协议接入EasyCVR,设备通道信息不显示是什么原因?
- Cocos2d-x 游戏存档[通俗易懂]
- Intelligent transportation is full of vitality. What will happen in the future? [easy to understand]
- Wechat official account oauth2.0 authorizes login and displays user information
- [function recursion] do you know all five classic examples of simple recursion?
- Unity3d 4.3.4f1执行项目
猜你喜欢
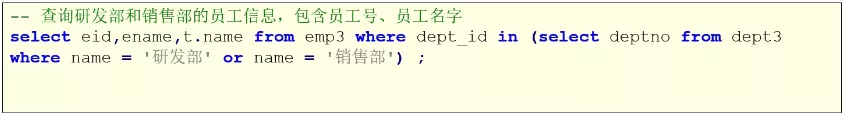
Mysql子查询关键字的使用方式(exists)
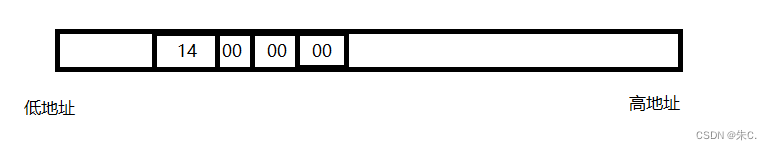
Details of C language integer and floating-point data storage in memory (including details of original code, inverse code, complement, size end storage, etc.)
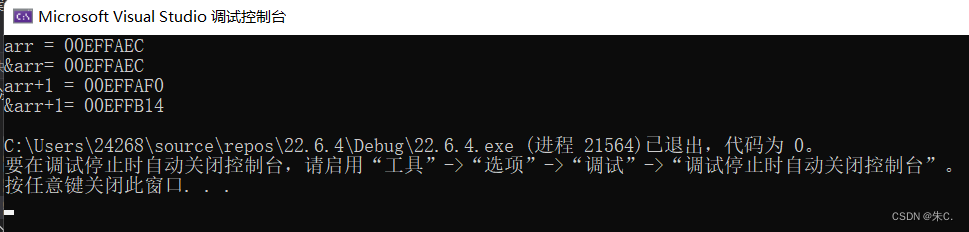
C language helps you understand pointers from multiple perspectives (1. Character pointers 2. Array pointers and pointer arrays, array parameter passing and pointer parameter passing 3. Function point
NVR硬盤錄像機通過國標GB28181協議接入EasyCVR,設備通道信息不顯示是什麼原因?
SQL injection error report injection function graphic explanation
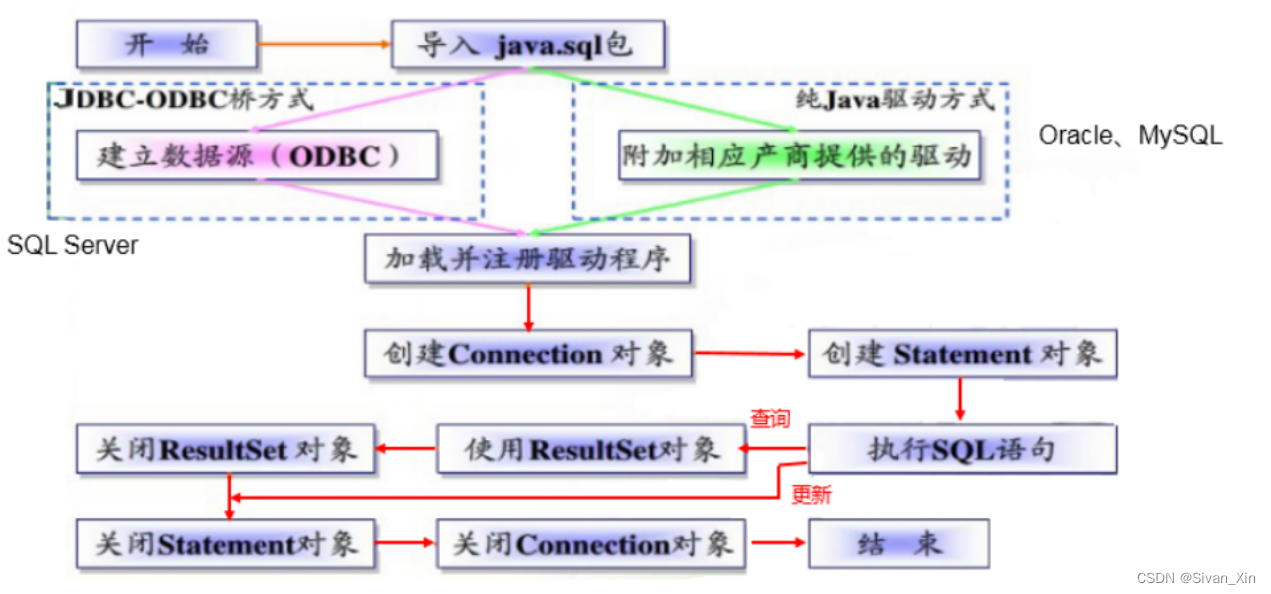
【JDBC Part 1】概述、获取连接、CRUD
![[200 opencv routines] 223 Polygon fitting for feature extraction (cv.approxpolydp)](/img/1e/055df228853d9b464fc4bcbde0a7ee.png)
[200 opencv routines] 223 Polygon fitting for feature extraction (cv.approxpolydp)
Default constraint and zero fill constraint of MySQL constraint

嵌入式开发:如何为项目选择合适的RTOS?
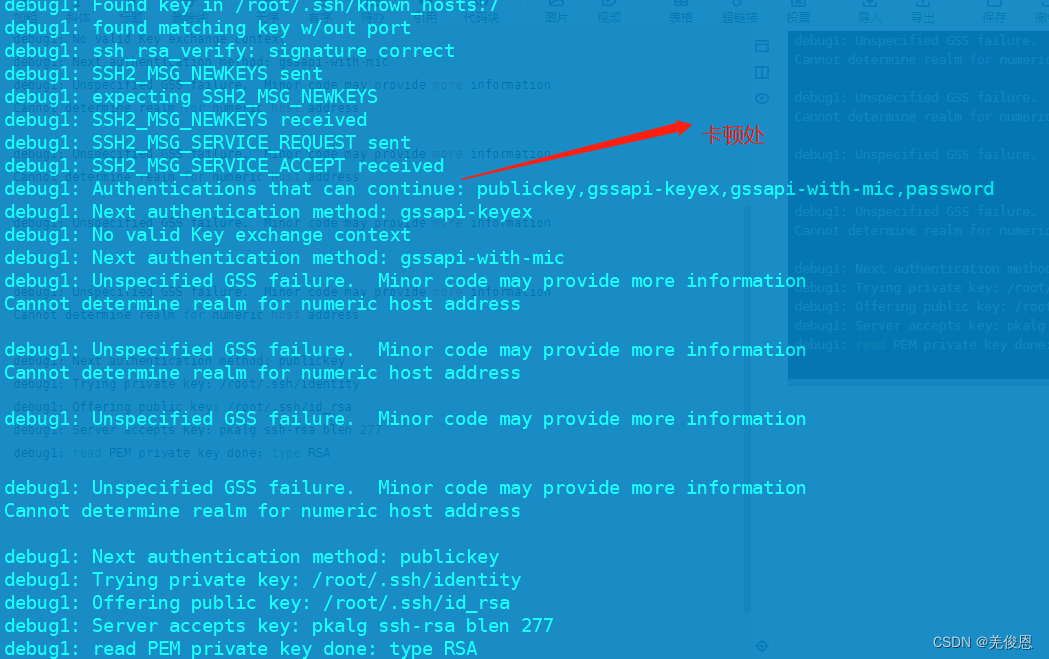
Debugging and handling the problem of jamming for about 30s during SSH login
随机推荐
Take the intersection of two sets
Is it safe to open an account online now? I want to know where I can open an account in Nanning now?
Usage of MySQL subquery keywords (exists)
Implementation of mahout Pearson correlation
开户还得用身份证银行卡安全吗,我是小白不懂
恶魔奶爸 A0 英文零基础的自我提升路
EasyUI date control emptying value
The cyberspace office announced the measures for data exit security assessment, which will come into force on September 1
How to integrate Google APIs with Google's application system (1) -introduction to Google APIs
Cv2.resize function reports an error: error: (-215:assertion failed) func= 0 in function ‘cv::hal::resize‘
Numerical method for solving optimal control problem (0) -- Definition
95年专注安全这一件事 沃尔沃未来聚焦智能驾驶与电气化领域安全
Use br to recover backup data on azure blob storage
私募基金在中国合法吗?安全吗?
Postgresql数据库character varying和character的区别说明
Debugging and handling the problem of jamming for about 30s during SSH login
Redis - basic use (key, string, list, set, Zset, hash, geo, bitmap, hyperloglog, transaction)
Dry goods sharing | devaxpress v22.1 original help document download collection
Develop those things: go plus c.free to free memory, and what are the reasons for compilation errors?
Actual combat: sqlserver 2008 Extended event XML is converted to standard table format [easy to understand]